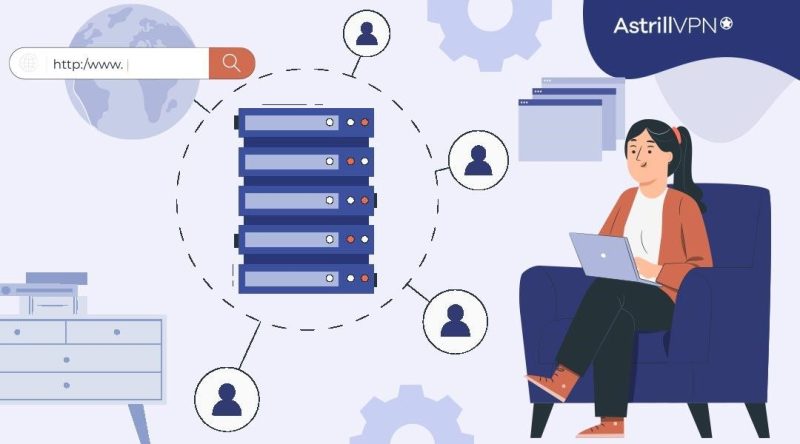
What Do ISPs See On My Internet History?
Internet Service Providers, or ISPs, provide internet access to homes, businesses, and other entities. They act as intermediaries, bridging the gap between users and the vast Internet infrastructure. Since ISPs provide internet service, it’s obvious that they have access to certain things we do over the internet. But the question is, what do ISPs see? […]
Bitcoin is pseudonymous, not anonymous, meaning your transactions can be traced back to you with some work. If you want to stay under the radar and buy Bitcoin anonymously, you’ve come to the right place. This guide will show you the best ways to hide your identity when buying crypto. Whether you want to invest […]
The Restrict Act (S.686) is a proposed bill introduced in the United States Senate on March 7th, 2023. Introduced by Senator Mark Warner, the Act proposes that the Secretary of Commerce be given the authority to review business transactions by foreign entities offering Information & Communications Technologies (ICTS) Products & Services, especially when these are […]
Introduction Someone spying on your iPhone sounds scary, and unfortunately, sometimes you may not even be aware that you’re getting spied on. Spyware is a type of Malware or app that sneaks into your phone and tracks and monitors your online activities through your phone. Just last month, it was reported that a well-known cybersecurity […]
Just like how we need different hardware essentials to be able to play certain games, we also need different internet speeds. If you’re playing games with other players in a competitive environment, such as PlayerUnknown’s: BattleGrounds, or Valorant, you want high download and upload speeds to prevent delays or lags. If you prefer to game […]
If you’ve decided to clear your router’s browsing history. Whether you share your network with others, want to free up space on the router, or value your privacy, deleting the router’s logs and history is essential. The good news is, clearing your router’s history is simple enough. The bad news is that the steps can […]
Are you having trouble accessing the web interface of your Xfinity router because you can’t find the IP address? Don’t worry, we’re here to help! Most Xfinity routers come with a default IP address of 10.0.0.1. However, if you’ve made any changes to the default settings, locating the correct IP address becomes crucial for accessing […]
Encryption is how we keep data private in an increasingly digital world. Whether you’re trying to protect your personal files, communications, or business data, understanding encryption methods is key. The two main types are symmetric encryption, where the same key is used to encrypt and decrypt data, and asymmetric encryption, which uses a public key […]
Just like how our security matters in the real world, our digital safety is of paramount importance. Cybersecurity is the practice of staying safe when connected to the internet and when protecting internet-reliant devices, such as databases, hardware, and even software. This protection is against hackers and malicious actors. In this day and age, we […]
Introduction When QR codes got introduced in the early nineties, they seemed like a great idea. You can access information just by scanning a QR code. It was convenient for a lot of people. Fast forward to now, and QR codes get used very commonly. You can find QR codes on billboards, restaurant menus, magazines, […]
Encryption serves as a powerful tool to safeguard sensitive information from unauthorized access and maintain confidentiality. In this guide, we have explained VPN encryption in detail and discussed the types of protocols you may come across. So without further ado, let’s dive right into VPN encryption and understand what it is and what it is […]
Are your online accounts and sensitive information truly secure? You might think so; after all, you diligently password-protect all your accounts and are careful who you share them with. But there’s a growing threat lurking in the shadows of the digital world. Dictionary attacks are an emerging cyber menace that is on the rise. They’re […]
If you’ve ever wondered how to optimize your Mac’s performance, free up storage space, or resolve compatibility issues, clearing the cache is crucial. Cache files can accumulate over time, impacting your system’s speed and efficiency. In this guide, we will walk you through clearing different types of cache on a Mac, including browser cache, system […]
Introduction Changing the location on your iPhone doesn’t have to be complicated. All you need is a VPN to get things sorted. Location spoofing isn’t just for cybercriminals or fraudsters; it can also provide a range of benefits to the average user. From enhancing your Privacy to unblocking censored content, there are many reasons why […]
Ever stumbled upon AliExpress and wondered if it was safe and legit? You’re not alone. This mega-site based in China has gained a reputation for offering crazy cheap prices on just about anything under the sun. But it’s only natural to question whether it’s too good at those prices. Before you whip out your credit […]
Have you ever wanted to transport yourself to an exotic locale using nothing but your phone? With Snapchat, you can make your friends believe you’ve escaped to a tropical beach or the Eiffel Tower while lounging on your couch. The social media app allows you to change your location to anywhere in the world. Whether […]
Pokémon Go has captured the hearts of millions of players worldwide, offering a unique augmented reality experience that combines the real world with the virtual world of Pokémon. The average number of active Pokemon Go players is 79,669,226, which proves its popularity well. While the game encourages exploration and adventure, there may be times when […]
Wide area networks (WANs) connect geographically dispersed locations, enabling organizations to communicate and share data across different sites. As businesses expand and adopt cloud-based applications, the demand for efficient and reliable WAN technologies has increased significantly. Two prominent WAN technologies exist Software-Defined Wide Area Networking (SD-WAN) and Multi-Protocol Label Switching (MPLS). SD-WAN and MPLS have […]
Instagram is one of the most popular websites in the world, and according to SEMRush, it is one of the top ten sites that people visit from all across the globe. Instagram is the fourth most used social media platform behind Facebook, YouTube, and WhatsApp. It also has 1.35 billion active users per month as […]
YouTube has become a powerful platform offering vast educational content, revolutionizing how students learn and teachers instruct. However, accessing YouTube at school can be challenging due to blocking or restrictions imposed by educational institutions. By leveraging the potential of YouTube while maintaining a safe and controlled online space, schools can enhance learning experiences and provide […]
Hey there, ever had the feeling someone was looking over your shoulder while you entered your password or PIN? That uncomfortable sense of being watched can be a sign your personal information is at risk from shoulder surfing. Shoulder surfing definition is when someone spies on you to steal your data or account access. They […]