Application Layer DDoS Attacks: Types, Detection, and Protection

Bisma Farrukh

Distributed Denial-of-Service (DDoS) attacks have evolved far beyond overwhelming networks with sheer volume of traffic. One of the most significant modern threats is the application-layer DDoS attack, also referred to as a Layer 7 DDoS attack. These attacks target the application layer of the OSI model, where web applications, APIs, and services interact directly with users.
Unlike traditional volumetric attacks, application-layer attacks are stealthy, harder to detect, and capable of taking down websites using relatively low traffic volumes. This makes them especially attractive to attackers and particularly challenging for organizations to defend against.
Table of Contents
What Is an Application Layer DDoS Attack?
An application-layer DDoS attack targets the seventh layer (Layer 7) of the OSI model, which handles application-level communication such as HTTP, HTTPS, DNS, and APIs. The goal is to exhaust server resources by sending requests that appear legitimate but are designed to overload application logic.
Instead of flooding bandwidth, attackers exploit how applications process requests, forcing servers to consume CPU, memory, database connections, or backend services until they can no longer respond to real users.
Understanding Application Layer Attacks
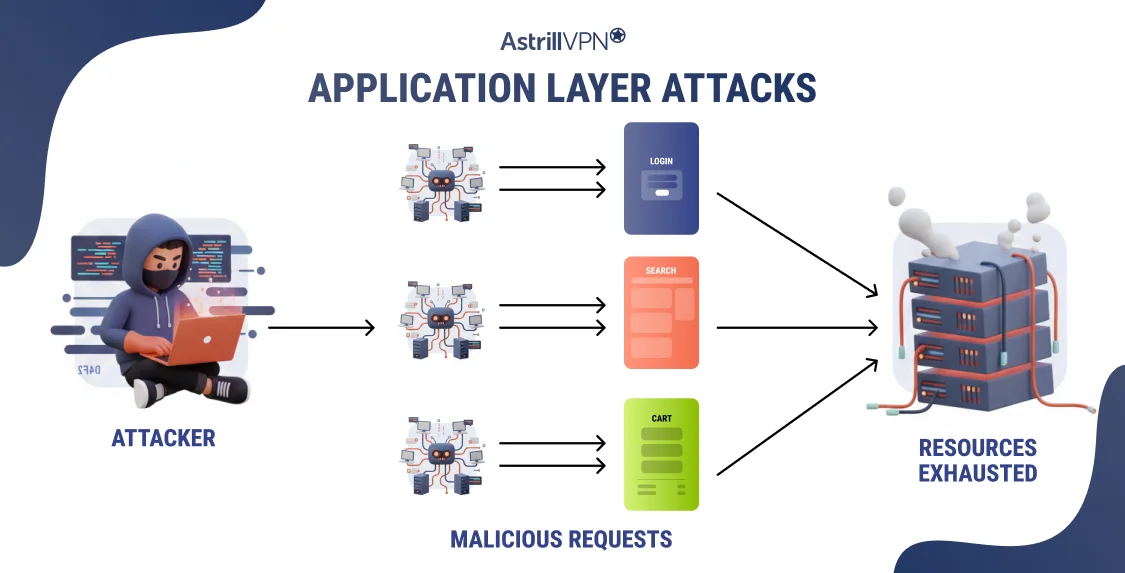
Application layer attacks target Layer 7 of the OSI model, which is the layer responsible for handling direct interactions between users and applications. This includes web browsers, APIs, login systems, search functions, and online transactions. Instead of overwhelming network bandwidth, these attacks exploit how applications process requests, making them more precise, stealthy, and harder to detect.
How Application Layer Attacks Work?
Application layer attacks typically follow this pattern:
- Attackers identify a vulnerable application endpoint
Examples include login pages, search bars, shopping carts, or APIs. - Malicious requests are generated.
These requests are crafted to appear as genuine user actions. - The server performs expensive operations.
Each request may trigger authentication checks, database queries, or the generation of dynamic content. - Resources are exhausted
Over time, the application becomes completely unresponsive.
What Is a Layer 7 DDoS Attack?
A Layer 7 DDoS attack, also known as an application layer DDoS attack, is a type of distributed denial-of-service attack that targets the application layer (Layer 7) of the OSI model. This layer is responsible for handling user-facing services such as websites, web applications, APIs, and online services that rely on protocols like HTTP and HTTPS.
Unlike volumetric DDoS attacks that aim to overwhelm network bandwidth, Layer 7 attacks focus on exhausting application resources by sending large numbers of seemingly legitimate requests. These requests require the server to perform resource-intensive operations, which can eventually lead to slowdowns or complete service outages.
How a Layer 7 DDoS Attack Works?
A Layer 7 DDoS attack typically follows this process:
- Attackers generate legitimate-looking requests
Malicious actors send HTTP or HTTPS requests that closely resemble normal user behavior. - Requests target resource-intensive endpoints.
These may include login pages, search functions, database queries, or APIs that require backend processing. - Server resources become exhausted.
Each request consumes CPU, memory, threads, or database connections. - Legitimate users are denied service.
As resources are depleted, real users experience slow responses or complete website downtime.
How Do Layer 7 DDoS Attacks Differ From Other Types of DDoS Attacks?
| Feature | Layer 7 DDoS | Network/Transport DDoS |
|---|---|---|
| Target | Application logic | Bandwidth or network stack |
| Traffic Volume | Low to moderate | Very high |
| Traffic Appearance | Legitimate | Clearly malicious |
| Detection Difficulty | High | Lower |
| Protocols Used | HTTP, HTTPS | UDP, TCP, ICMP |
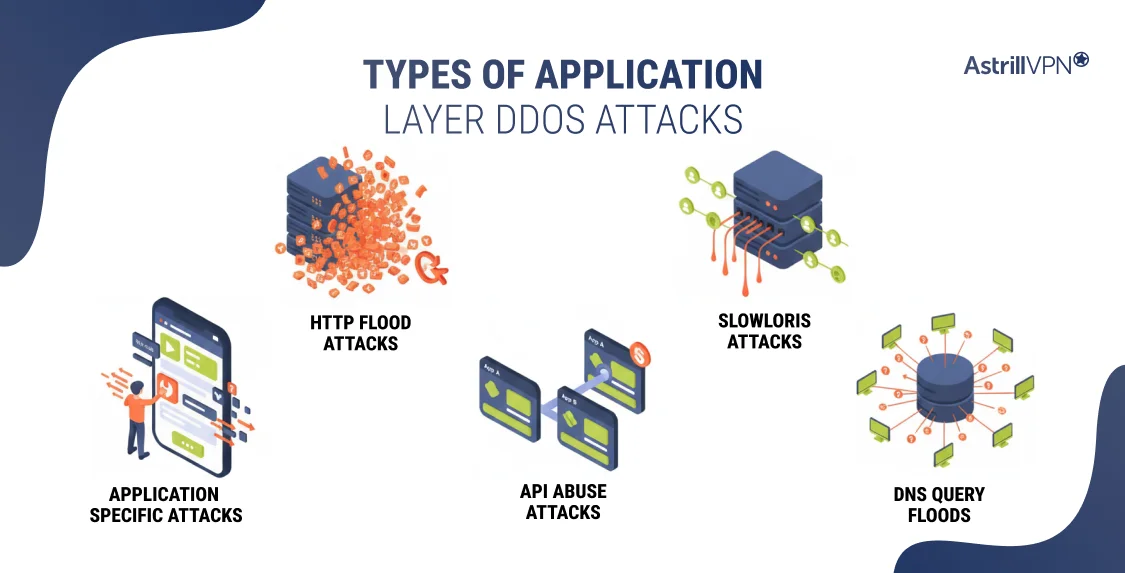
Most Common Types of Application Layer DDoS Attacks
1. HTTP Flood Attacks
Attackers send a large number of HTTP GET or POST requests to web servers. Each request forces the server to process scripts, query databases, or generate responses, resulting in the exhaustion of resources.
2. Slowloris Attacks
This attack keeps many HTTP connections open by sending partial requests slowly. The server waits for completion, tying up available connections and preventing legitimate users from establishing a connection.
3. Application-Specific Attacks
Attackers target resource-intensive functions such as:
- Login pages
- Shopping carts
- Search queries
- Report generation endpoints
4. API Abuse Attacks
APIs are prime targets due to their direct access to the backend. Attackers flood API endpoints with requests, exhausting compute resources and backend services.
5. DNS Query Floods (Layer 7 Context)
When DNS services are hosted at the application layer, attackers overwhelm them with legitimate-looking DNS queries, which can slow or disrupt name resolution.
Role of Hypertext Transfer Protocol (HTTP) in Layer 7 DDoS Attacks
The Hypertext Transfer Protocol (HTTP) plays a central role in Layer 7 DDoS attacks because it is the primary protocol used for web communication between clients and servers. Since most websites, web applications, and APIs rely on HTTP or HTTPS, attackers exploit this protocol to launch application-layer floods that closely mimic legitimate user behavior.
Why HTTP Is a Prime Target in Layer 7 DDoS Attacks?
HTTP is beautiful to attackers because:
- It is universally used by browsers, mobile apps, and APIs
- HTTP requests appear legitimate and human-like
- Each request often triggers server-side processing.
- Encryption (HTTPS) can hide payload details from basic inspection
Can a Layer 7 DDoS Attack Bring Down My Website?
Yes, a Layer 7 DDoS attack can absolutely bring down your website, even if your servers have strong bandwidth capacity and your network appears healthy. Unlike traditional DDoS attacks that flood networks with massive traffic, Layer 7 attacks target the application itself, making them especially dangerous and difficult to defend against.
Layer 7 DDoS attacks focus on exhausting application-level resources, such as:
- CPU and memory
- Web server threads and worker processes
- Database connections
- API rate limits
- Session
How to Detect an Application Layer DDoS Attack?
Detecting application-layer DDoS attacks requires behavioral analysis rather than volume-based monitoring. Advanced monitoring tools and application logs are critical for early detection.
Key Indicators Include:
- Sudden spike in specific URLs or endpoints
- Increase in failed logins or repeated requests
- High server CPU usage with normal bandwidth
- Abnormally long session durations
- Increased HTTP 500 or 503 errors
Key current statistics and trends about application‑layer (Layer 7) DDoS attacks
- Between early 2023 and late 2024, Akamai reported a 94% rise in Layer 7 DDoS attacks against web applications and APIs, growing from ~500 billion to over 1.1 trillion monthly attacks.
- In Q2 2025, application‑layer DDoS attacks increased by ~74 % compared to the prior year, according to industry summaries.
- Global mitigation services like Cloudflare saw millions of attacks per quarter, with reports stating 20.5 million DDoS attacks were blocked in Q1 2025, far exceeding prior annual totals.
- Cloudflare data from 2023‑24 showed HTTP DDoS attacks increasing by ~93 % YoY.
- Financial services were disproportionately affected (e.g., approximately 43.6% of application-layer attacks in one dataset), followed by e-commerce (~22.6%) and ICT services (~18.2%).
Application Layer DDoS Protection Strategies
Protecting against application layer (Layer 7) DDoS attacks requires more than traditional network-level defenses. Because these attacks mimic legitimate user behavior and exploit application logic, adequate protection must focus on traffic behavior, request patterns, and application awareness rather than just traffic volume.
Below are the most effective application-layer DDoS protection strategies used by modern organizations.
1. Deploy a Web Application Firewall (WAF)
A Web Application Firewall (WAF) is one of the most critical defenses against Layer 7 DDoS attacks. Advanced WAFs use behavioral analysis instead of static rules, making them effective against sophisticated attacks.
How it helps:
- Inspects HTTP/HTTPS requests in real time
- Blocks malicious patterns and abnormal request behavior
- Protects specific URLs, forms, and APIs
- Filters traffic before it reaches the origin server
2. Implement Rate Limiting
Rate limiting restricts the number of requests a client can make within a specific time window. Rate limiting helps prevent attackers from overwhelming backend resources with repeated requests.
Best practices:
- Apply limits per IP, session, or user
- Use stricter limits on sensitive endpoints (login, search, APIs)
- Adjust thresholds dynamically during traffic spikes
3. Use Bot Management and Detection
Botnets power most application-layer DDoS attacks. This prevents malicious bots while allowing legitimate users to access the site uninterrupted.
Bot mitigation tools can:
- Identify automated traffic using fingerprints and behavior analysis
- Distinguish bots from real users
- Block, throttle, or challenge suspicious clients
4. Enable CAPTCHA and Challenge-Response Mechanisms
CAPTCHAs and JavaScript challenges help verify whether traffic is coming from humans or automated scripts. These challenges significantly reduce bot-driven attack traffic.
Use cases:
- During active attacks
- On login, signup, or checkout pages
- When abnormal traffic patterns are detected
5. Leverage Content Delivery Networks (CDNs)
A CDN distributes traffic across multiple geographically dispersed servers. CDNs are particularly effective in mitigating HTTP GET flood attacks.
Benefits for Layer 7 protection:
- Absorbs and filters malicious requests
- Serves cached content without hitting origin servers
- Reduces server load during attacks
6. Monitor Application Behavior and Traffic Baselines
Establishing normal traffic baselines helps detect anomalies quickly. Sudden deviations from standard patterns often indicate an application-layer attack.
Monitor metrics such as:
- Request rates per endpoint
- Error rates (4xx, 5xx)
- Response times
- Session duration
7. Optimize and Harden Application Logic
Reducing backend resource consumption makes applications more resilient. Efficient applications are more complex to overwhelm.
Key steps include:
- Optimizing database queries
- Implementing caching for expensive operations
- Limiting unauthenticated requests
- Enforcing timeouts and connection limits
Best Practices to Prevent Application Layer DDoS Attacks
Preventing application layer (Layer 7) DDoS attacks requires a proactive and layered approach. Since these attacks exploit legitimate application behavior and protocols, such as HTTP/HTTPS, organizations must focus on application-aware security, traffic intelligence, and operational readiness, rather than relying solely on traditional network defenses.
Below are the best practices for effectively preventing and mitigating the impact of application-layer DDoS attacks.
1. Deploy an Advanced Web Application Firewall (WAF)
A modern WAF is essential for Layer 7 protection. An advanced WAF can analyze request patterns and block malicious traffic before it reaches your application.
Best practices:
- Enable behavior-based detection instead of only signature-based rules
- Protect high-risk endpoints such as login pages, search functions, and APIs
- Regularly update rules and policies
2. Enforce Intelligent Rate Limiting
Rate limiting prevents attackers from overwhelming your application with repeated requests. This ensures normal users are not affected while abusive traffic is throttled.
Key recommendations:
- Apply different limits per endpoint
- Set stricter limits for unauthenticated users
- Use adaptive rate limits that adjust during traffic spikes
3. Implement Bot Management Solutions
Since most application-layer attacks are automated, bot detection is critical. Separating bots from humans significantly reduces the effectiveness of attacks.
Effective bot management includes:
- Device and browser fingerprinting
- Behavior analysis (mouse movement, request timing)
- Blocking or challenging suspicious bots
4. Use CAPTCHA and Challenge-Based Controls Strategically
CAPTCHAs help validate real users during suspicious activity. Use challenges selectively to avoid harming user experience.
Best use cases:
- Login and authentication pages
- Signup and checkout forms
- During detected attack periods
5. Leverage CDNs and Caching
A Content Delivery Network (CDN) reduces the load on origin servers. CDNs are especially effective against HTTP GET flood attacks.
Benefits include:
- Serving cached content without backend processing
- Absorbing large volumes of HTTP requests
- Filtering malicious traffic at the edge
6. Harden and Optimize Application Logic
Well-optimized applications are harder to overwhelm. Lower resource consumption reduces attack impact.
Optimization techniques:
- Cache frequently accessed data
- Reduce expensive database queries
- Limit resource-heavy operations for unauthenticated users
- Enforce timeouts and connection limits
7. Secure and Monitor APIs Separately
APIs are common Layer 7 DDoS targets. API-specific controls significantly shrink the attack surface.
API protection best practices:
- Require authentication and API keys
- Apply strict per-user and per-key rate limits
- Monitor abnormal API request patterns
- Disable unused endpoints
8. Establish Traffic Baselines and Continuous Monitoring
Knowing what “normal” looks like helps detect attacks early. Sudden deviations from baselines often indicate an ongoing attack.
Monitor:
- Requests per second
- Response times
- Error rates (4xx/5xx)
- Session behavior
9. Use Behavioral and AI-Based Detection
Machine learning–driven solutions can detect subtle and low-rate attacks.
- Identify low-and-slow attacks
- Adapt to new attack patterns.
- Reduce false positives
10. Prepare an Incident Response and Mitigation Plan
Preparation minimizes downtime.
Your plan should include:
- Clear escalation procedures
- Preconfigured mitigation rules
- Communication plans for stakeholders
- Regular testing and drills
Conclusion
Application-layer DDoS attacks represent one of the most serious threats to modern web applications. Their ability to mimic legitimate traffic makes them challenging to detect and highly effective at disrupting services. By understanding how Layer 7 DDoS attacks work and implementing strong application-layer DDoS protection, organizations can significantly reduce the risk of downtime and maintain reliable digital services.
Frequently Asked Questions (FAQs)
Here are some of the most commonly asked questions (FAQs).
Application-layer DDoS attacks can last anywhere from a few minutes to several days or even weeks. Because they use low-and-slow techniques and mimic legitimate users, attackers can sustain them for long periods without triggering traditional defenses.
No. Many Layer 7 attacks generate low to moderate traffic volumes. Their effectiveness stems from forcing the application to perform resource-intensive operations, rather than consuming bandwidth.
Yes, if defenses are poorly configured. Overly aggressive rate limits or CAPTCHA rules can block real users. This is why behavior-based detection and adaptive thresholds are recommended instead of static rules.
Yes. HTTPS encryption hides request payloads, making inspection harder unless security tools terminate SSL/TLS. This increases the importance of advanced WAFs and edge-based security solutions.
Absolutely. Mobile applications rely on backend APIs, which are frequently targeted by Layer 7 DDoS attacks. Attackers often flood API endpoints instead of traditional web pages.


No comments were posted yet