What is PUP? Understanding Risks, Detection & Removal Tips

Bisma Farrukh

The growing cybersecurity threats come in various forms, not all of them as overt as a full-blown virus. One prevalent and often insidious category is the Potentially Unwanted Program (PUP). These programs, while not always malicious in the traditional sense, can significantly degrade user experience, compromise privacy, and even create vulnerabilities. Recent reports indicate a substantial rise in PUP detections, with one study showing a increase n PUP encounters over the past year affecting a broad range of users worldwide.
Recent reports indicate a substantial rise in PUP detections, with research showing that 79% of all malware infections removed by major security providers are now classified as PUPs, which is a dramatic increase from just 25% in 2012.
Furthermore, another report highlights that PUPs are often bundled with legitimate software, leading to an estimated of all software installations potentially including an unwanted extra. Understanding PUPs is crucial for maintaining a clean and secure digital environment.
Table of Contents
What is PUP?
A Potentially Unwanted Program (PUP) in cybersecurity is a software application that performs actions that are generally considered undesirable or against the user’s explicit consent. These programs often exhibit behaviors such as displaying excessive advertisements, changing browser settings without permission, collecting user data, or consuming system resources unnecessarily. Unlike traditional malware, PUPs often operate in a grey area, sometimes being included in end-user license agreements (EULAs) that users may quickly accept without reading.
PuP vs Malware : Key Differences
While both PUPs and malware can negatively impact a user’s system, there are key distinctions:
| Feature | PUP (Potentially Unwanted Program) | Malware |
|---|---|---|
| Intent | Often designed for profit (ads, data collection) rather than direct harm. | Designed for malicious purposes (data theft, system damage, control). |
| Legality | Often included in EULAs, making their presence technically “consented” to. | Typically operates without any consent or legal justification. |
| Detection | May be flagged by security software as “potentially unwanted” rather than outright malicious. | Explicitly detected and blocked as a direct threat by security software. |
| Removal Difficulty | Can sometimes be removed through standard uninstallation processes, though often persistent. | Often requires specialized tools and advanced techniques for removal. |
| System Impact | Annoying ads, slow performance, browser hijacking, privacy concerns. | Data theft, system corruption, unauthorized access, ransomware, espionage. |
Types of potentially unwanted Programs
PUPs manifest in various forms, each with its own set of undesirable behaviors:
- Adware: Displays unwanted advertisements, often pop-ups, banners, or in-text ads, sometimes redirecting to malicious sites.
- Browser Hijackers: Modify web browser settings (homepage, search engine) without user permission, often redirecting traffic to specific sites for advertising revenue.
- Toolbars: Install unnecessary toolbars in web browsers that consume screen space and often include intrusive search functionalities or data collection features.
- System Optimizers: Falsely claim to improve system performance or detect numerous errors, then demand payment to “fix” non-existent or minor issues.
- Spyware (Light): Collects user browsing habits or personal information for marketing purposes, often less intrusive than malicious spyware but still a privacy concern.
- Bundled Software: Unwanted programs that are installed alongside legitimate software, often hidden in “express” installation options.
Most Common PUP Categories (2024–2025)
- Adware and Browser Hijackers: Around 45–50% of all PUP detections involved intrusive adware or unwanted browser extensions.
- Fake System Optimizers and Driver Updaters: Approximately 25% of PUPs were disguised as performance boosters or “cleaner” apps.
- Cryptomining and Hidden Resource Drainers: About 10–15% of detected PUPs engaged in background crypto mining or resource abuse.
- Data-Tracking Utilities: A growing category in 2025, these collect user data for targeted ads or analytics without proper consent.
Global Overview
- In 2025, PUPs accounted for 18–22% of all threat detections globally, according to aggregate data from security firms such as Malwarebytes and ESET.
- The number of PUP detections increased by about 12% from 2024 to 2025, largely due to the rise in bundled software installations and fake system optimization tools.
How Do PUPs Get Installed?
PUPs primarily rely on deceptive tactics to gain access to a device:
- Software Bundling: This is the most common method. PUPs are packaged with legitimate, free software that users download from unofficial sources. During installation, the user might unknowingly agree to install the PUP by clicking “Next” without reviewing custom installation options.
- Deceptive Advertising: Malicious ads or pop-ups may trick users into downloading and installing PUPs by claiming to be essential updates, security alerts, or free software offers.
- Drive-by Downloads: In some cases, visiting a compromised website can lead to an automatic download and installation of a PUP without explicit user action, though this is more typical of traditional malware.
- Fake Updates: Prompts to update Flash Player, Java, or other common software can sometimes be disguised attempts to install PUPs.
Common Examples of PUPs
While specific PUP names change frequently, some common categories include:
- Search engines that alter your default browser settings (e.g., certain “search protect” programs).
- “Free” video converters or download managers that come with a host of extra, unwanted programs.
- Fake antivirus or system optimization tools that constantly show alarming pop-ups about your system’s health.
- Browser extensions or add-ons that claim to offer useful features but secretly track your browsing or inject ads.
Signs Your Device Has PUPs
Identifying PUPs can be subtle, but several signs indicate their presence:
- Excessive Pop-up Ads: A noticeable increase in pop-up ads, especially on websites where they don’t usually appear.
- Browser Redirects: Your browser’s homepage or search engine changes without your consent, or you are redirected to unfamiliar websites.
- Slow System Performance: Your computer or device becomes noticeably slower, applications take longer to load, or the system frequently freezes.
- Unwanted Toolbars or Extensions: New toolbars or browser extensions appear that you don’t remember installing.
- New Icons on Desktop: Unfamiliar program icons appear on your desktop or in your Start Menu.
- Difficult to Uninstall Programs: Attempts to uninstall suspicious programs via standard methods are met with errors or the program reappears.
How to Detect PUPs?
Detecting PUPs often requires a combination of vigilance and specialized tools:
Common Symptoms of PUP Infections
Detecting a PUP begins with recognizing the signs of its presence. Some common symptoms include unexpected browser toolbars, frequent pop-up ads, or sudden redirects to unfamiliar websites. Your computer may slow down significantly, and you might notice unknown programs in your installed applications list.
Other warning signs include changes to your browser’s homepage or search engine without your permission, as well as unexplained network or CPU activity. If you observe any of these issues, it’s a good indication that a PUP might be installed on your system.
Manual Detection Methods on Windows and macOS
You can start detecting PUPs manually by checking your installed programs. On Windows, go to Control Panel → Programs and Features and review the list for any recently installed or suspicious applications. In addition, inspect browser extensions by navigating to your browser’s extension management page such as chrome://extensions for Chrome or about:addons for Firefox and remove anything you do not recognize.
Checking the Task Manager for unknown processes and reviewing your Startup Programs can also help uncover hidden PUPs.
On macOS, open the Applications folder to look for unwanted apps, then check System Preferences → Users & Groups → Login Items for startup entries you don’t recognize. You can also use Activity Monitor to identify any suspicious background processes that may be running without your knowledge.
Using Security Tools for PUP Detection
While manual inspection is helpful, using security tools ensures a more thorough detection process. Windows users can rely on Windows Defender for a full or offline system scan. However, dedicated anti-malware tools such as Malwarebytes, AdwCleaner, HitmanPro, and ESET Online Scanner are particularly effective at identifying and removing PUPs. These tools specialize in detecting software that traditional antivirus programs might overlook, especially adware, browser hijackers, and hidden system optimizers.
Resetting Your Browser Settings
Sometimes, even after removing a PUP, your browser may continue to behave abnormally. In such cases, resetting your browser can help restore normal operation. Most browsers, including Chrome, Edge, and Firefox, offer a reset option that reverts settings to their defaults. After resetting, clear your cache and cookies, and manually remove any remaining suspicious extensions. This ensures that the PUP cannot reinstate its unwanted changes.
Preventing Future PUP Infections
Prevention is the best defense against PUPs. Always choose Custom or Advanced installation options when installing software, as this allows you to deselect any bundled offers. Download applications only from official websites or reputable sources, and avoid clicking on ads that promise free utilities or updates. Keeping your operating system, browsers, and security tools up to date helps close vulnerabilities that PUPs may exploit. Additionally, using a trusted ad-blocker or browser security extension, such as uBlock Origin or Malwarebytes Browser Guard, adds an extra layer of protection against unwanted software.
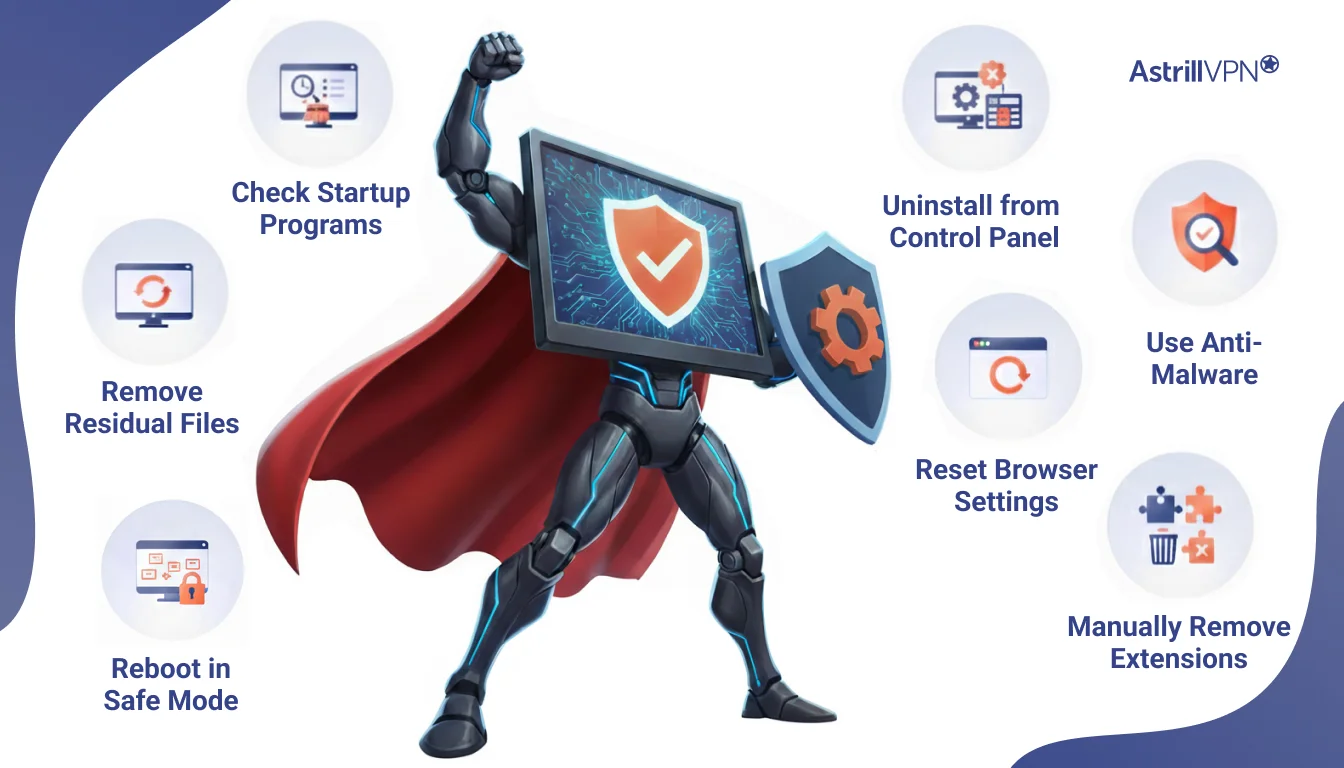
How to Remove Potentially Unwanted Programs?
Removing PUPs can vary in difficulty, but these steps are generally effective:
- Uninstall from Control Panel/Settings: The first step is to attempt uninstallation through your operating system’s built-in tools. For Windows, go to “Add or Remove Programs”. For macOS, drag the application to the Trash.
- Use Anti-Malware: Run a full scan with a reputable security program. These tools can often identify and remove persistent PUPs.
- Reset Browser Settings: Resetting your web browser to its default settings can remove unwanted toolbars, extensions, and homepage hijackers.
- Manually Remove Extensions: Go into your browser’s extension manager and remove any suspicious add-ons.
- Check Startup Programs: Some PUPs configure themselves to launch at startup. Disable or remove them from your system’s startup programs.
- Remove Residual Files: After uninstallation, there might be leftover files or registry entries. Advanced users can manually clean these, or a dedicated cleaner tool can assist.
- Reboot in Safe Mode: For stubborn PUPs, booting your device into Safe Mode can sometimes allow for easier removal.
How to Prevent PUPs?
Prevention is key to avoiding the headaches caused by PUPs:
- Download Software from Official Sources: Always download programs directly from the developer’s official website or trusted app stores. Avoid third-party download sites that often bundle unwanted software.
- Read EULAs and Installation Prompts Carefully: During software installation, always choose “Custom” or “Advanced” installation options. Deselect any bundled software or optional installations that you don’t recognize or want.
- Use a Reputable Antivirus: Keep your security software updated and perform regular scans.
- Keep Operating System and Software Updated: Updates often include security patches that can protect against vulnerabilities exploited by PUPs.
- Be Wary of Free Offers: If something seems too good to be true like free system cleaners that promise miracle fixes, it probably is.
- Use a Browser with Strong Security Features: Modern browsers often have built-in protections against malicious sites and unwanted downloads.
- Educate Yourself: Understanding common social engineering tactics used to trick users into installing PUPs is a powerful defense.
Are PUPs Dangerous?
While PUPs are generally less destructive than full-fledged malware, they can still pose significant risks:
- Privacy Concerns: Many PUPs collect user data, browsing habits, and even personal information, which can then be sold to third parties or used for targeted advertising.
- Performance Degradation: PUPs often consume system resources (CPU, RAM, network bandwidth), leading to a slower and less responsive device.
- Security Vulnerabilities: Some PUPs can weaken a system’s security, making it more susceptible to other, more dangerous forms of malware. They might open backdoors or disable legitimate security features.
- Annoyance and Frustration: Constant pop-ups, browser redirects, and unwanted changes to settings can severely degrade the user experience.
- Financial Impact: Rogue system optimizers might trick users into paying for unnecessary or ineffective services.
Conclusion
Potentially Unwanted Programs represent a significant and often underestimated threat in the cybersecurity landscape. While they may not always cause immediate and obvious damage like viruses or ransomware, their ability to erode privacy, degrade system performance, and introduce security vulnerabilities makes them a serious concern for any digital user. By understanding what PUPs are, how they propagate, and implementing robust preventive measures, users can significantly enhance their digital hygiene and protect their devices from these insidious programs. Exercising caution when downloading software, and utilizing reliable security tools are paramount in the ongoing battle against PUPs.
FAQs
Here are some frequently asked questions.
No, PUPs are generally not classified as traditional malware. While they exhibit undesirable behaviors and can be harmful, they often operate in a legal grey area, sometimes with user “consent” obtained through tricky EULAs. Malware, on the other hand, is unequivocally malicious with harmful intent.
While most PUPs are not designed for direct theft of passwords or financial information, some highly intrusive forms of spyware-like PUPs might collect sensitive data. More importantly, PUPs can weaken your system’s security, making it easier for actual malware to gain access and steal such information.
The reason for this is often the “potentially unwanted” nature of PUPs. Since they sometimes operate under the guise of legitimate software, security programs may flag them as a potential threat but leave the decision to remove them up to the user. This is to avoid accidentally uninstalling a program that a user might genuinely want, despite its questionable characteristics.
Yes, PUPs can and do infect smartphones and tablets, particularly on Android devices. They often come bundled with free apps downloaded from unofficial app stores or through deceptive advertising.
No, a PUP is not a virus. A virus is a type of malware that replicates itself and spreads to other computers. PUPs do not typically have self-replicating capabilities.


No comments were posted yet