What Is a Smurf Attack? How It Works and How to Prevent it

Bisma Farrukh
Despite modern network defenses and best practices, Smurf attacks continue to surface in real-world DDoS traffic mixes and can still pose a threat when network configurations are weak or outdated. In simulated environments and real-world attack analyses in 2025, security researchers observed that a single Smurf-style packet sent to a misconfigured broadcast network could trigger as many as 1,000 response packets directed at a victim, resulting in crippling spikes in traffic and leading to the network infrastructure struggling or failing.
This guide takes you inside the mechanics of a Smurf attack and explains why it still matters today. You will learn exactly how these attacks work, see a clear example, and get straightforward guidance for preventing and mitigating them. By the end, you will have a solid, practical understanding of the threat and how to secure your systems against it.
Table of Contents
What Is a Smurf Attack?
A Smurf attack is a type of attack that overwhelms a target with a massive amount of traffic. Unlike other attacks that utilize numerous hacked devices from various locations, a Smurf attack leverages ordinary devices on a single network to generate a flood of responses that can crash a system.
This technique utilizes a protocol known as ICMP, or Internet Control Message Protocol. This is the same protocol that tools like ping use to check if a host is online. In a Smurf attack, the attacker sends an ICMP echo request to the broadcast address of a network. This request causes every device on the network to respond. The attacker tricks the devices by changing the original address to the victim’s, so all responses go to that victim. When multiple devices respond simultaneously, it can overload the victim’s network with excessive traffic.
The name “Smurf attack” comes from an old hacking tool from the 1990s. It describes how many small responses can overpower one larger system. Today, many networks have protections against Smurf attacks. However, outdated or poorly set up systems can still be vulnerable.
Smurf DDoS Attack Explained
A Smurf DDoS attack is a volumetric DDoS technique that relies on traffic amplification rather than brute force. The attacker does not need to control thousands of infected devices. Instead, they manipulate normal network behavior so that legitimate systems unknowingly generate the flood of traffic on their behalf.
What makes a Smurf attack distinct is the combination of IP spoofing and broadcast exploitation.
The attacker sends a crafted ICMP echo request to a network’s broadcast address, using a falsified source IP that appears to be the victim’s. When the packet reaches the broadcast network, all devices respond directly to the victim. This amplifies the attack, potentially triggering hundreds or thousands of replies that overwhelm the victim’s system, consuming bandwidth and exhausting resources, which prevents legitimate users from accessing the service.
From a technical standpoint, a Smurf DDoS attack falls into two overlapping categories:
• Reflection attacks, because third-party systems reflect traffic toward the victim
• Amplification attacks, because the volume of responses far exceeds the size of the original request
The danger lies not only in the number of packets but also in their simultaneous arrival from legitimate systems, which makes the traffic appear normal and complicates filtering.
Despite modern routers blocking directed broadcasts by default, Smurf DDoS attacks remain relevant due to existing misconfigurations in enterprise networks and poorly secured infrastructure. These weaknesses can allow Smurf attacks to create disruptive traffic levels with minimal effort.
How Does a Smurf Attack Work?
Understanding how a Smurf attack works is easiest when you look at it as a simple chain reaction. The attacker does not directly flood the victim. Instead, they set up the conditions for many other devices to do it for them.
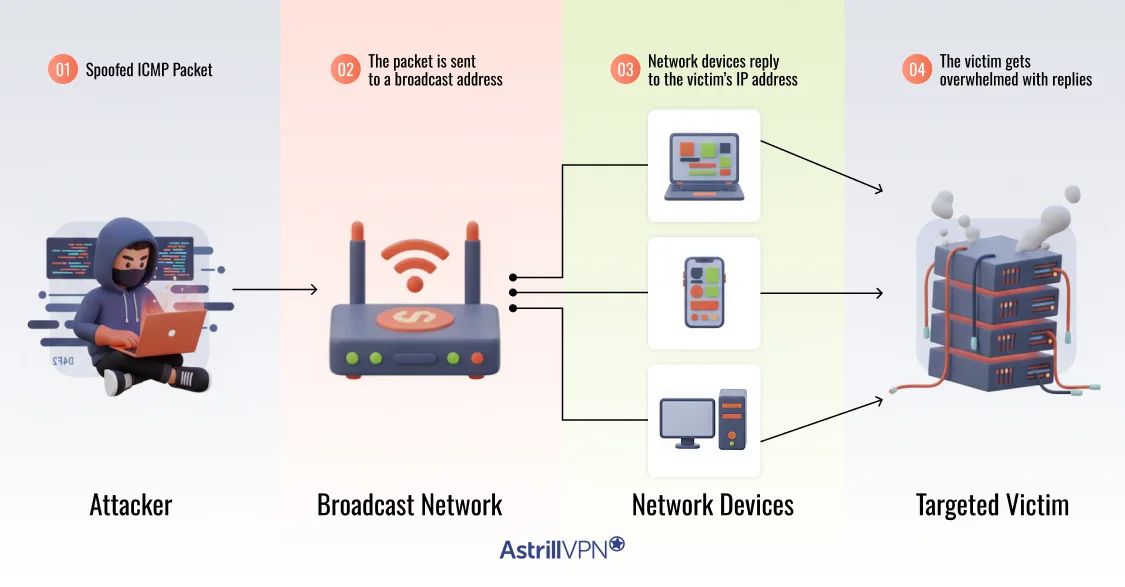
Here is the step-by-step flow of a Smurf attack.
Step 1: The attacker crafts a spoofed ICMP packet
The attack begins with the creation of an ICMP echo request. This is the same type of message used by the ping command to test connectivity.
However, there is one critical manipulation.
The attacker forges the source IP address inside the packet so that it appears to come from the intended victim. This technique is known as IP spoofing. From the perspective of any system that receives this packet, it looks like the victim is the one who sent it.
At this point, the attacker is laying the foundation for traffic to be redirected.
Step 2: The packet is sent to a broadcast address
Instead of sending the packet to a single device, the attacker sends it to a network’s broadcast address.
A broadcast address is designed to deliver a message to every active device within a network segment. That means servers, workstations, printers, and networked devices can all receive the same request at once.
This is where the amplification begins.
One packet now reaches many systems simultaneously.
Step 3: Network devices reply to the victim’s IP address
Each device that receives the broadcast ICMP request responds automatically with an ICMP echo reply.
Because the source address was spoofed, every one of these replies is sent to the victim’s IP address, not to the attacker.
None of these systems are malicious on their own. They are simply behaving as the protocol instructs them to. But together, they generate a surge of traffic aimed at a single target.
Step 4: The victim gets overwhelmed with replies
As the replies arrive simultaneously, the victim’s bandwidth, firewall, or server resources begin to saturate.
The system is forced to process thousands of unsolicited responses. Legitimate traffic is delayed or dropped. Services slow down or become completely unavailable. In severe cases, network equipment itself can become unstable.
The result is a denial-of-service attack caused not by one powerful attacker, but by the combined responses of many normal devices.
Technical Components of a Smurf Attack
A Smurf attack may look simple on the surface, but it relies on several technical elements working together. Understanding these components helps clarify why the attack can be so effective and where defenses should be applied.
Below are the core technical building blocks that make a Smurf attack possible.
1. Internet Control Message Protocol (ICMP)
ICMP is a foundational network protocol used for diagnostics and error reporting. Tools like ping depend on it to check whether a system is reachable and how quickly it responds.
In a Smurf attack, ICMP is not exploited because it is weak, but because it is widely trusted and automatically processed. When a system receives an ICMP echo request, it typically replies without authentication or verification. That predictable behavior is what attackers abuse.
The attack specifically uses:
• ICMP Echo Request
• ICMP Echo Reply
2. IP Spoofing
IP spoofing is the technique of falsifying the source address in a network packet.
Instead of inserting their real IP address, the attacker places the victim’s IP address in the source field of the ICMP request. This makes every responding device believe the victim initiated the communication.
IP spoofing serves two purposes:
• It redirects all replies to the victim
• It conceals the true origin of the attacker
3. Broadcast Addresses
A broadcast address is designed to deliver a packet to every device on a network segment.
In a normal environment, broadcasts are used for legitimate purposes such as device discovery and network announcements. In a Smurf attack, the broadcast address becomes an amplifier.
When the spoofed ICMP request is sent to a broadcast address:
• Every reachable device receives it
• Every device generates a reply
• All replies are sent to the victim
4. Vulnerable or Misconfigured Networks
Modern routers and operating systems typically block directed broadcasts by default. Smurf attacks become possible only when networks are misconfigured, outdated, or improperly secured.
Examples of enabling conditions include:
• Routers that forward directed broadcast traffic
• Devices that respond to ICMP requests sent to broadcast addresses
• Poorly segmented enterprise or hosting networks
5. Traffic Amplification Mechanism
The defining technical feature of a Smurf attack is amplification.
One small ICMP request can generate hundreds or thousands of replies. The victim receives far more data than the attacker ever transmitted.
This creates a severe imbalance between the attacker’s effort and the victim’s impact. Even low-bandwidth attackers can cause significant disruption if amplification conditions exist.
6. Target Resource Exhaustion
The final technical component is not a protocol, but an outcome.
As ICMP replies arrive simultaneously, the victim system experiences:
• Bandwidth saturation
• CPU and memory pressure
• Firewall and router overload
• Service unavailability
Impact and Risks of Smurf Attacks
The immediate goal of a Smurf attack is simple: overwhelm a system until it can no longer function normally. However, the real impact often extends far beyond slow connections or temporarily unreachable service:
- Severe bandwidth saturation that slows or completely blocks legitimate traffic.
- Service outages that make websites, applications, and online platforms inaccessible.
- An overload of network devices, such as routers, firewalls, and load balancers, can potentially cause instability across the entire infrastructure.
- Degraded performance for internal systems, including VPN gateways, email servers, and cloud workloads.
- Financial losses due to downtime, missed transactions, SLA penalties, and emergency response costs.
- Reputational damage occurs when customers experience repeated service disruptions or unreliable access.
- Operational disruption for employees who lose access to critical tools and systems.
- Increased risk of secondary attacks, as Smurf traffic floods can distract security teams and mask other malicious activity.
- Long recovery times if network equipment becomes unstable or requires reconfiguration.
How to Prevent Smurf Attacks
Preventing Smurf attacks is less about complex tools and more about removing the technical conditions that allow them to work. Strong network hygiene and layered defenses make this type of attack extremely difficult to execute.
Disable Directed Broadcasts on Network Devices
Routers and Layer 3 switches should be configured to block directed broadcast traffic. This prevents external systems from sending packets to broadcast addresses within your network.
Blocking directed broadcasts prevents the attacker from reaching multiple devices with a single packet. This single step eliminates the amplification effect that Smurf attacks depend on.
Configure Systems to Ignore Broadcast ICMP Requests
Endpoints and servers should not respond to ICMP echo requests sent to broadcast addresses.
Disabling this behavior ensures that even if a broadcast packet enters the network, devices will not generate mass replies. This significantly reduces the risk that your infrastructure will be used as an attack amplifier against others.
Implement Ingress and Egress Filtering
Ingress filtering blocks packets with spoofed source addresses from entering the network. Egress filtering prevents forged packets from leaving it.
Together, these controls reduce the effectiveness of IP spoofing, which is a core requirement for Smurf attacks. They also improve traceability and strengthen overall network security.
Use Network Level Monitoring and Anomaly Detection
Continuous monitoring enables the detection of abnormal ICMP traffic patterns before they escalate.
Unusual spikes in echo requests or replies, unexpected broadcast traffic, or sudden saturation of links should trigger alerts and automated responses. Early detection allows security teams to contain potential attacks before services are disrupted.
Apply Rate Limiting and Traffic Filtering Policies
Rate limiting on ICMP traffic prevents any single source or traffic type from overwhelming network resources.
Firewalls and security gateways can be configured to restrict unnecessary ICMP traffic, block suspicious patterns, and prioritize legitimate connections during high load conditions.
Maintain Regular Network Audits and Hardening
Smurf attacks often succeed because of forgotten devices, legacy systems, or default configurations.
Routine audits help identify exposed broadcast settings, outdated firmware, and improperly configured equipment. Hardening practices ensure new systems do not reintroduce vulnerabilities over time.
Can a VPN Prevent Smurf Attacks?
A VPN is not a direct defense against Smurf attacks, but it can still play an important supporting role within a broader security strategy.
Smurf attacks primarily target network infrastructure and publicly reachable systems. They exploit how routers and hosts respond to broadcast ICMP traffic. A VPN does not change how broadcast amplification works across the internet, and it cannot stop an attacker from abusing third-party networks to flood a target.
However, a reliable VPN like AstrillVPN can contribute to Smurf attack resilience in several meaningful ways.
First, a VPN helps reduce direct exposure of internal systems. By placing services behind encrypted tunnels and restricting access to authenticated users, organizations limit which assets are visible and reachable from the public internet. Fewer exposed systems mean fewer potential high-value targets.
Second, enterprise-grade VPN deployments are often paired with strong firewall policies, traffic filtering, and access controls. This layered approach enhances overall network hygiene and reduces the likelihood of misconfigurations within protected environments.
Third, VPNs play a defensive role in protecting users, not just servers. During large-scale denial-of-service events, VPNs can help employees maintain secure access paths, protect their traffic from interception, and avoid unstable or hostile network segments.
Smurf Attack vs. Similar DDoS Attacks
| Attack Type | How It Works | Key Technique | Primary Target Impact | How It Differs From a Smurf Attack |
| Smurf Attack | Spoofed ICMP requests are sent to a broadcast address, causing many devices to reply to the victim. | Reflection and amplification using ICMP and broadcast networks. | Bandwidth exhaustion, network device overload, service unavailability. | Relies on broadcast amplification and misconfigured networks rather than direct flooding. |
| ICMP Flood | Large volumes of ICMP packets are sent directly to the victim from one or more sources. | Direct packet flooding without broadcast amplification. | Server overload, network congestion. | Does not use third-party systems to multiply traffic. |
| Fraggle Attack | Similar to Smurf but uses UDP services instead of ICMP. | Reflection and amplification through UDP broadcast services. | Bandwidth saturation and service disruption. | Exploits UDP services rather than ICMP echo replies. |
| SYN Flood | Attackers send many TCP connection requests without completing handshakes. | Exhaustion of server connection tables. | Application unavailability and server instability. | Targets server resources rather than raw network bandwidth. |
| DNS Amplification | Small DNS queries trigger large DNS responses sent to the victim. | Reflection and high amplification via open DNS resolvers. | Massive traffic surges and network saturation. | Uses internet exposed services instead of local broadcast networks. |
Conclusion
Smurf attacks are a powerful reminder that some of the most disruptive cyber threats do not come from complex malware, but from the misuse of ordinary network behavior. By exploiting ICMP responses, broadcast addressing, and IP spoofing, attackers can turn legitimate systems into unwitting participants in denial-of-service campaigns.
Although modern network standards have reduced the prevalence of Smurf attacks, they have not eliminated the risk. Misconfigured routers, outdated equipment, and overlooked broadcast settings can still expose organizations to this form of amplification. When that happens, even low-effort attackers can generate traffic volumes capable of destabilizing networks and disrupting services.
The most effective defense is built on fundamentals. Proper router configuration, controlled ICMP handling, spoofing prevention, and continuous network monitoring eliminate the conditions that enable Smurf attacks. When these controls are in place, Smurf attacks lose their power. For organizations and individuals alike, understanding threats like the Smurf attack is part of building long-term digital resilience.
FAQs
The core difference lies in the protocol being abused. A Smurf attack utilizes ICMP echo requests to trigger a mass reply from devices on a broadcast network. A Fraggle attack follows the same amplification concept but uses UDP services instead of ICMP, typically targeting services like echo or chargen.
Smurf attacks are not as common today as they were in the early days of the internet, but they can still occur. Most modern routers block directed broadcasts by default, which helps prevent traditional Smurf attacks. However, some networks are misconfigured or use outdated hardware, and some environments are not properly separated. When these situations occur, Smurf-style amplification can still be misused.
The most effective prevention measure is blocking directed broadcasts on routers and network gateways.
When broadcast traffic from external sources is not allowed into a network, attackers cannot reach multiple devices with a single packet. This removes the amplification mechanism that Smurf attacks rely on. Without broadcast reachability, the attack collapses.
There are several warning signs that a network may be unintentionally participating in a Smurf attack:
• Large volumes of outgoing ICMP echo replies without corresponding internal requests
• Unexpected spikes in ICMP traffic leaving the network
• Alerts from upstream providers about abnormal traffic patterns
• Increased load on network devices even when internal usage is low
The financial impact depends on the organization’s size, industry, and its dependency on online services; even short outages can be costly. Losses often include immediate revenue disruption, incident response expenses, infrastructure recovery costs, and contractual penalties tied to service level agreements.
Beyond direct costs, repeated service interruptions can damage customer trust, increase churn, and weaken brand credibility. For digital businesses, financial harm from denial-of-service attacks often extends well beyond the duration of the attack itself.


No comments were posted yet