What Is a UDP Flood DDoS Attack? How to Mitigate Them

Arsalan Rathore

A UDP flood attack is a type of Distributed Denial-of-Service (DDoS) attack that exploits the connectionless nature of the User Datagram Protocol (UDP) to overwhelm a target system, server, or network. By sending a high volume of UDP packets to random or specific ports, attackers consume bandwidth and system resources, causing slowdowns or complete service outages. UDP flood attacks are widely used because they are easy to launch, difficult to trace, and highly effective at disrupting online services.
Table of Contents
What Is UDP Flood?
A UDP flood is a volumetric attack in which an attacker sends massive amounts of UDP packets to a victim’s IP address. These packets are often sent to ports where no application is listening. When the target system receives these packets, it checks for an active application on the destination port. If none exists, the system replies with an ICMP “Destination Unreachable” message, further increasing resource usage and network congestion.
Understanding UDP Flood Attacks
A UDP flood attack focuses on exhausting a target’s bandwidth and processing capacity. Since UDP does not require a handshake like TCP, attackers can send packets continuously without waiting for responses. This makes UDP-based attacks faster, stealthier, and harder to mitigate than some other DDoS techniques.
In a UDP flood DDoS attack, traffic originates from multiple compromised devices, often part of a botnet. These distributed sources amplify the attack’s impact, making it harder to block malicious traffic without affecting legitimate users.
How UDP Flood attack Works?
A UDP flood attack works by overwhelming a target server with a massive number of UDP packets, causing service disruption or complete denial of service. The diagram illustrates this process step by step, from the attacker to server exhaustion.
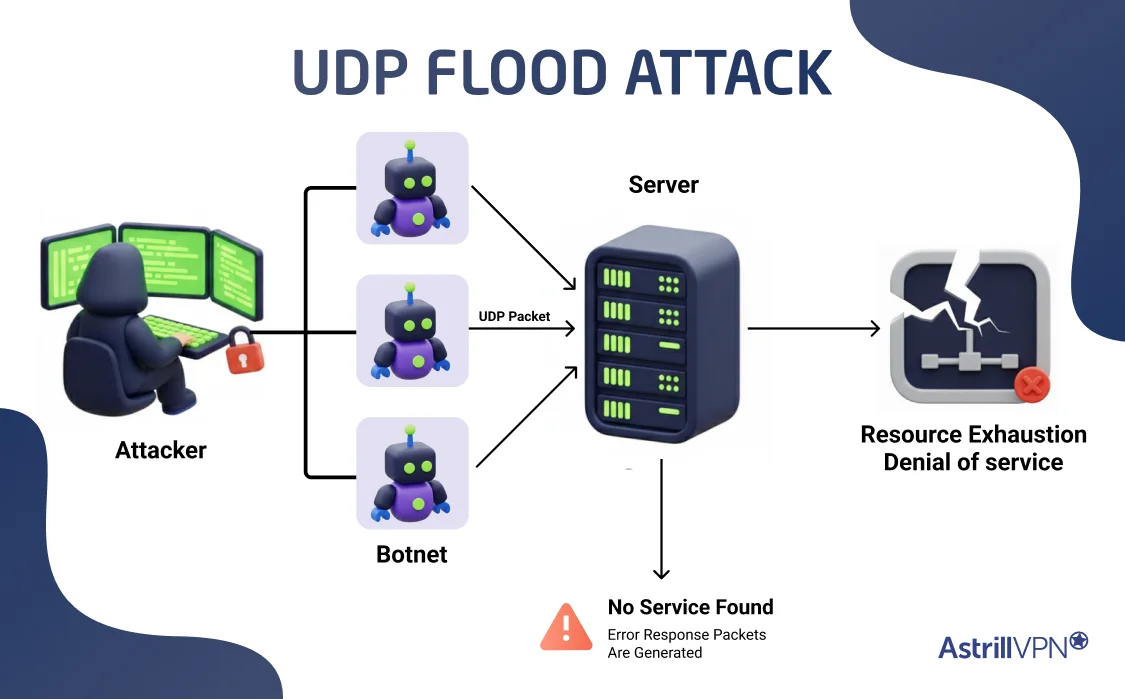
Step 1: Attacker Controls a Botnet
The attack begins with a malicious attacker who controls multiple compromised devices, collectively known as a botnet. These bots can include infected computers, servers, or IoT devices. Each bot is capable of sending large volumes of UDP packets simultaneously.
Step 2: Botnet Sends UDP Packets to the Server
The botnet devices generate and send a flood of UDP packets toward the target server. Because UDP is a connectionless protocol, the bots do not need to establish a session before sending packets. These packets are often sent to:
- Random destination ports, or
- Specific UDP service ports (such as DNS or gaming ports)
Step 3: Server Receives UDP Packets
As shown in the diagram, the server receives continuous UDP packets from multiple botnet sources. For each incoming packet, the server must check whether an application is actively listening on the destination port.
Step 4: No Service Found on Destination Port
In many cases, the targeted ports do not have an active service running. When the server cannot find a corresponding application for the incoming UDP packet, it attempts to handle the request anyway.
Step 5: Error Response Packets Are Generated
If no application is listening on the targeted port, the server sends error response packets, typically ICMP “Destination Unreachable” messages back to the source IP address. These responses consume additional processing power and bandwidth.
Step 6: Resource Exhaustion Occurs
As the volume of UDP packets increases:
- Server CPU usage spikes
- Network bandwidth becomes saturated
- Memory and processing resources are depleted
Step 7: Denial of Service (DoS)
The server becomes overwhelmed and is unable to respond to legitimate user requests. This results in a Denial of Service (DoS) condition, where applications become slow or completely unavailable.
Related Article: How DNS flood Attack Works
UDP Flood Attack Statistics
- UDP-based attacks account for over 40% of volumetric DDoS attacks worldwide.
- Peak UDP flood attacks have exceeded 1 Tbps in traffic volume.
- DNS and NTP-based UDP attacks remain among the top three DDoS vectors
- The gaming and fintech industries experience the highest frequency of UDP floods
- Attack durations have increased, with many lasting over 6 hours.
How does AstrillVPN help in preventing UDP flood attacks?
AstrillVPN helps in preventing UDP flood attacks by acting as a protective layer between the attacker and the target system. By masking the user’s real IP address and replacing it with a VPN server’s IP address, Astrill makes it difficult for attackers to identify and flood the actual network directly. Any malicious UDP traffic is first directed toward Astrill’s servers, which are built to handle large volumes of data and can absorb, filter, or drop excessive packets before they reach the user.
Astrill also applies server-side packet inspection, rate limiting, and firewall rules to detect abnormal UDP traffic patterns and block spoofed or malformed packets commonly used in UDP flood attacks. Additionally, the encrypted VPN tunnel ensures that only valid session-based traffic is allowed through, reducing the effectiveness of IP spoofing techniques. While AstrillVPN is not a dedicated DDoS mitigation service, these combined features significantly reduce exposure to UDP flood attacks and help maintain network stability during attempted floods.
Real World UDP Flood Attacks
UDP flood attacks have been responsible for some of the most disruptive and high-impact DDoS incidents in recent years. Due to UDP’s speed and lack of connection validation, attackers frequently use this method to overwhelm critical online services across multiple industries.
1. DNS Provider UDP Flood Attacks
One of the most common real-world examples of UDP flood attacks targets the DNS infrastructure. DNS relies heavily on UDP (port 53), making it an attractive target. In several large-scale incidents, attackers flooded DNS servers with massive volumes of UDP packets, causing domain name resolution failures. As a result, thousands of websites became inaccessible, despite their servers being operational.
Impact:
- Websites unreachable worldwide
- Disruption to e-commerce and SaaS platforms
- Cascading failures across dependent services
2. Gaming Industry UDP Flood Attacks
Online gaming platforms are frequent victims of UDP flood attacks because real-time gameplay relies on UDP for low latency. Attackers flood game server ports with UDP traffic, resulting in lag, dropped connections, and server crashes. These attacks are often used for competitive sabotage or extortion.
Impact:
- Matchmaking failures
- Severe lag and packet loss
- Player dissatisfaction and revenue loss
3. IoT-Based UDP Flood Attacks
Large botnets made up of compromised IoT devices such as routers, cameras, and smart appliances have been used to launch massive UDP flood attacks. These devices generate enormous volumes of UDP packets, overwhelming network infrastructure and internet service providers.
Impact:
- Network congestion at the ISP level
- Regional service outages
- Complex mitigation due to distributed sources
4. Telecommunications and ISP Attacks
Telecom providers and ISPs have been targeted with UDP floods aimed at saturating backbone links. By flooding UDP traffic toward infrastructure services, attackers cause widespread connectivity issues for residential and enterprise customers.
Impact:
- Internet slowdowns across large regions
- VoIP and mobile service disruptions
- High operational and mitigation costs
5. Financial Services UDP Flood Attacks
Banks and fintech platforms have faced UDP flood attacks aimed at disrupting online banking and payment systems. Even brief outages can result in significant financial losses and damage customer trust.
Impact:
- Temporary unavailability of online services
- Transaction delays
- Reputational damage and regulatory scrutiny
6. UDP Flood Attacks Combined with Amplification
In many real-world cases, UDP flood attacks are combined with amplification techniques such as NTP, DNS, or SSDP reflection. Attackers send small spoofed requests that trigger significantly larger responses toward the victim, thereby dramatically increasing the attack volume.
Impact:
- Traffic amplification by tens or hundreds of times
- Rapid bandwidth exhaustion
- Extended downtime
Why UDP Is Commonly Used in Flood Attacks?
UDP is frequently exploited in DDoS attacks due to its inherent characteristics:
- Connectionless Protocol – No handshake or verification process
- Low Overhead – Faster packet transmission
- Easy IP Spoofing – Source IP addresses can be forged
- Wide Usage – Used by DNS, VoIP, streaming, and gaming services
IP Spoofing in UDP Flood Attacks
IP spoofing plays a significant role in UDP flood attacks. Attackers forge the source IP address of packets, making them appear to come from legitimate or random locations. IP spoofing significantly enhances the scale and anonymity of UDP flood attacks. This technique:
- Makes attack traffic difficult to trace
- Bypasses basic IP-based filtering
- Causes response traffic to be sent to spoofed IPs, increasing network load
Commonly Targeted Ports in UDP Flood Attacks
Attackers often target UDP ports associated with widely used services, including:
- Port 53 – DNS services
- Port 123 – NTP (Network Time Protocol)
- Port 161 – SNMP
- Port 1900 – SSDP
- Gaming and VoIP Ports – Used by real-time applications
Difference Between UDP Flood and TCP Flood Attacks
| Feature | UDP Flood Attack | TCP Flood Attack |
| Protocol Type | Connectionless | Connection-oriented |
| Handshake Required | No | Yes (3-way handshake) |
| Detection Difficulty | Higher | Lower |
| IP Spoofing | Easy | Difficult |
| Resource Target | Bandwidth & CPU | Server connection table |
While TCP floods aim to exhaust connection resources, UDP floods primarily overwhelm bandwidth and processing power.
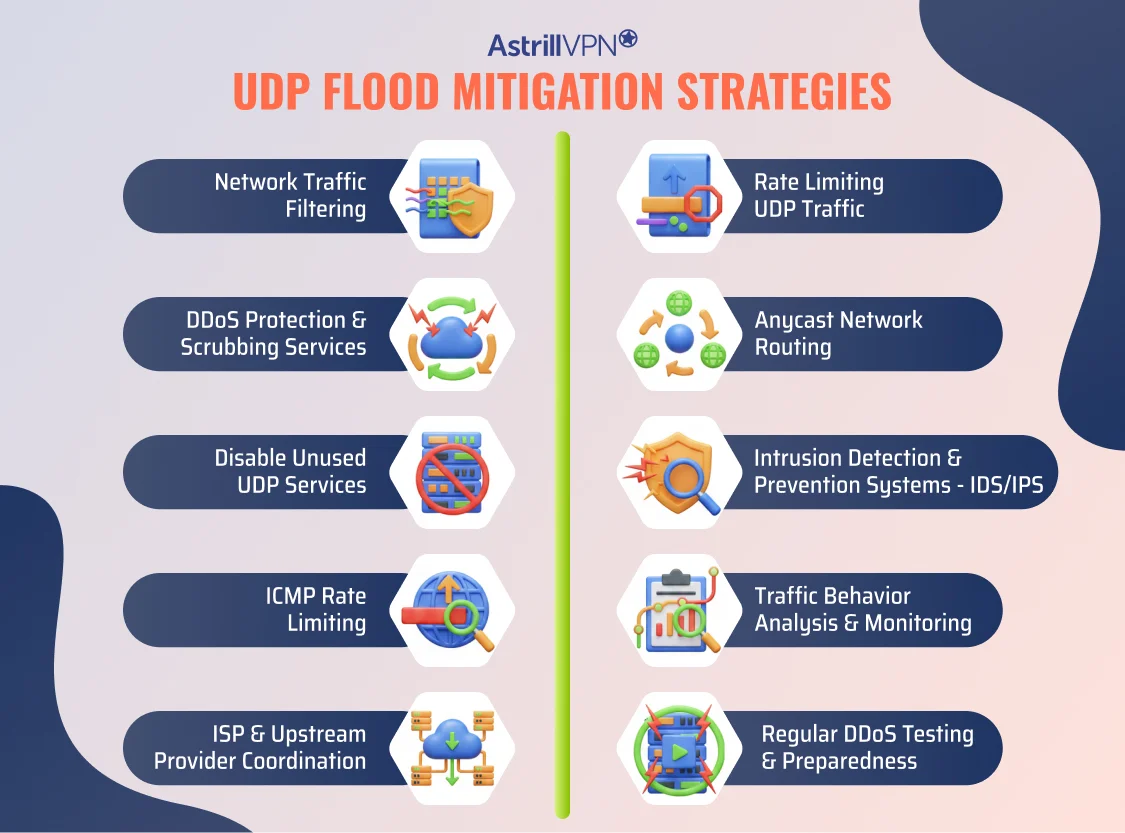
UDP Flood Mitigation Strategies
Mitigating UDP flood attacks requires a multi-layered defense approach because UDP traffic is connectionless, high-volume, and easy to spoof. Effective mitigation focuses on filtering malicious traffic, controlling traffic rates, and ensuring the resilience of infrastructure.
1. Network Traffic Filtering
Firewalls, routers, and access control lists (ACLs) can be configured to filter unwanted UDP traffic. Blocking unused UDP ports and allowing only essential services significantly reduces the attack surface. Filtering rules should be applied as close to the network edge as possible to prevent malicious traffic from consuming internal resources.
2. Rate Limiting UDP Traffic
Rate limiting restricts the number of UDP packets a server or network can process per second. By enforcing thresholds on packet rates, organizations can prevent attackers from overwhelming systems while still allowing legitimate traffic to pass. This technique is particularly effective against high-volume UDP floods.
3. DDoS Protection and Scrubbing Services
Cloud-based DDoS mitigation services absorb and analyze incoming traffic, separating legitimate packets from malicious ones. These services use large-scale infrastructure to handle traffic surges and prevent UDP flood traffic from reaching the target server.
4. Anycast Network Routing
Anycast routing distributes incoming traffic across multiple geographically dispersed servers. Instead of overwhelming a single target, UDP traffic is spread across multiple nodes, reducing the overall impact of the attack and improving service availability.
5. Disable Unused UDP Services
Many systems run UDP services that are not required for daily operations. Disabling unnecessary UDP services and closing unused ports prevents attackers from exploiting them during a UDP flood attack.
6. Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS solutions monitor traffic patterns in real time and can automatically block or throttle suspicious UDP traffic. These systems detect anomalies such as unusually high packet rates or abnormal port usage associated with UDP flood attacks.
7. ICMP Rate Limiting
Since UDP flood attacks often trigger ICMP “Destination Unreachable” responses, limiting ICMP response rates prevents excessive outbound traffic and reduces additional strain on the server during an attack.
8. Traffic Behavior Analysis and Monitoring
Continuous monitoring helps establish normal UDP traffic baselines. When traffic deviates from expected patterns, automated alerts and mitigation actions can be triggered, allowing faster response to UDP flood attacks.
9. ISP and Upstream Provider Coordination
Internet Service Providers (ISPs) can block or rate-limit malicious UDP traffic upstream before it reaches the target network. Early mitigation at the provider level is significant for large-scale volumetric attacks.
10. Regular DDoS Testing and Preparedness
Conducting DDoS simulations and stress tests ensures that mitigation mechanisms work effectively under real attack conditions. Having an incident response plan enables faster recovery and minimizes downtime during a UDP flood attack.
Conclusion
UDP flood attacks remain one of the most prevalent and disruptive forms of DDoS attacks due to the simplicity and efficiency of the UDP protocol. By understanding how UDP floods work, why UDP is vulnerable, and which mitigation techniques are most effective, organizations can significantly reduce their risk of downtime and service disruption. Implementing layered security measures and proactive monitoring is essential to defending against modern UDP flood DDoS attacks.
FAQs
Following are some common FAQs listed below.
UDP is vulnerable because it does not require session establishment or verification, allowing attackers to send massive volumes of packets without restriction.
IP spoofing involves forging the source IP address of UDP packets to hide the attacker’s identity and bypass basic security filters.
Common targets include ports 53 (DNS), 123 (NTP), 161 (SNMP), and 1900 (SSDP), as well as ports used by VoIP and gaming services.
UDP floods overwhelm bandwidth and CPU using connectionless traffic, while TCP floods target server connection resources through handshake abuse.


No comments were posted yet