What is DNS Flood Attack: DNS flood DDoS attack

Bisma Farrukh
Modern internet infrastructure depends heavily on the Domain Name System (DNS) to function smoothly. Every time a user types a website address into a browser, DNS translates that domain name into an IP address. Due to their critical role, DNS servers are a prime target for cybercriminals. One of the most common attacks aimed at these servers is the DNS flood attack. This attack can disrupt websites, applications, and even entire networks by overwhelming DNS resources with massive volumes of requests.
Table of Contents
What Is a DNS Flood Attack?
A DNS flood attack is a type of distributed denial-of-service (DDoS) attack that targets DNS servers by sending an excessive number of DNS requests within a short period of time. The goal is to exhaust server resources such as CPU, memory, or network bandwidth, making the DNS service slow or entirely unavailable for legitimate users.
Unlike more complex DDoS attacks, DNS floods rely on sheer volume. Attackers often use botnets composed of compromised devices to generate thousands or millions of DNS queries simultaneously, creating traffic levels that exceed the capacity of standard DNS infrastructure.
What is DNS Query Flood?
A DNS query flood is a specific variation of a DNS flood attack where attackers bombard a DNS server with continuous lookup requests. These queries may be valid in format, but are intentionally generated at a rate far beyond standard traffic patterns.
In many cases, the requests are sent for non-existent or random subdomains. This forces the DNS server to perform repeated recursive lookups, consuming additional processing power. Over time, this leads to slower response times, dropped queries, and complete service outages.
How Does a DNS Flood Attack Work?
A DNS flood attack typically follows a structured process designed to overwhelm DNS infrastructure efficiently.
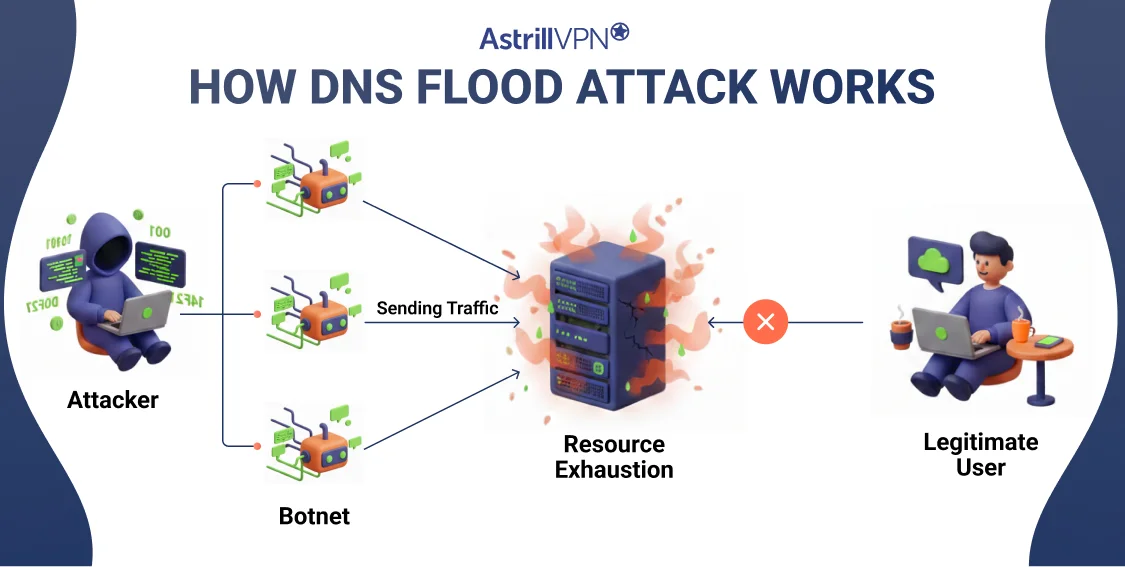
1. Botnet Preparation
Attackers compromise thousands of devices, including PCs, routers, and IoT devices. These infected systems become part of a botnet capable of sending coordinated traffic.
2. Traffic Generation
Each bot sends a continuous stream of DNS queries to the target DNS server. These requests may appear legitimate, making them difficult to filter.
3. Resource Exhaustion
The DNS server attempts to process every incoming request. As traffic increases, CPU usage, memory consumption, and bandwidth utilization spike rapidly.
4. Service Disruption
Once the server reaches its limits, legitimate DNS queries are dropped. Websites relying on that DNS service become unreachable, even if their web servers are still operational.
Types of DNS flood attacks
DNS flood attacks come in several forms, each using a different method to overwhelm the DNS infrastructure. While the end goal is the same: disrupting DNS resolution, the techniques vary in how traffic is generated and how brutal the attack is to detect and mitigate.
Direct DNS Query Flood
A direct DNS query flood is the most straightforward type of DNS flood attack. In this method, attackers send an extremely high volume of DNS queries directly to the target DNS server. These requests are usually valid in structure, which makes them harder to block without affecting legitimate users. The attack focuses on exhausting server resources, such as CPU, memory, and bandwidth, ultimately causing a complete DNS failure.
Random Subdomain Attack
In a random subdomain attack, the attacker continuously generates DNS queries for randomly created subdomains under a legitimate domain. Because these subdomains are not cached, the DNS server is forced to process each request individually and often forward it to authoritative servers. This increases computational load and significantly slows down DNS resolution, making it an effective method for resource exhaustion.
NXDOMAIN Flood Attack
An NXDOMAIN flood attack targets DNS servers by sending queries for non-existent domains. Each query results in an NXDOMAIN response, which still consumes processing power and bandwidth, even though it is not a valid domain. Over time, a flood of such requests can overwhelm DNS infrastructure, leading to service degradation and denial of access for legitimate users.
Reflection-Based DNS Flood
In a reflection-based DNS flood, attackers use third-party DNS resolvers to send traffic to the victim indirectly. By spoofing the victim’s IP address, attackers cause DNS resolvers to send responses to the target instead of the source. While not always amplified in size, the sheer volume of reflected traffic can still overwhelm the target’s network and DNS services.
DNS Amplification Flood
DNS amplification floods are a more advanced and damaging variant of DNS-based attacks. Attackers send minor DNS queries with spoofed source IP addresses to open resolvers, which then reply with much larger responses to the victim. This amplification effect multiplies the attack traffic, allowing attackers to generate massive volumes of data with minimal effort, often crippling DNS servers and network infrastructure.
TCP-Based DNS Flood
Although DNS primarily uses UDP, some DNS flood attacks also exploit TCP connections. In a TCP-based DNS flood, attackers initiate numerous TCP-based DNS requests, forcing the server to maintain and manage multiple connections. This consumes additional memory and processing resources, making it easier to exhaust server capacity compared to UDP-based floods.
Botnet-Driven Distributed DNS Flood
This type of DNS flood relies on large botnets composed of compromised devices distributed across different regions. Each bot sends DNS queries at a moderate rate, but collectively the traffic becomes overwhelming. As the requests originate from diverse IP addresses and locations, distinguishing attack traffic from legitimate traffic becomes especially challenging.
Effects of a DNS flood attack
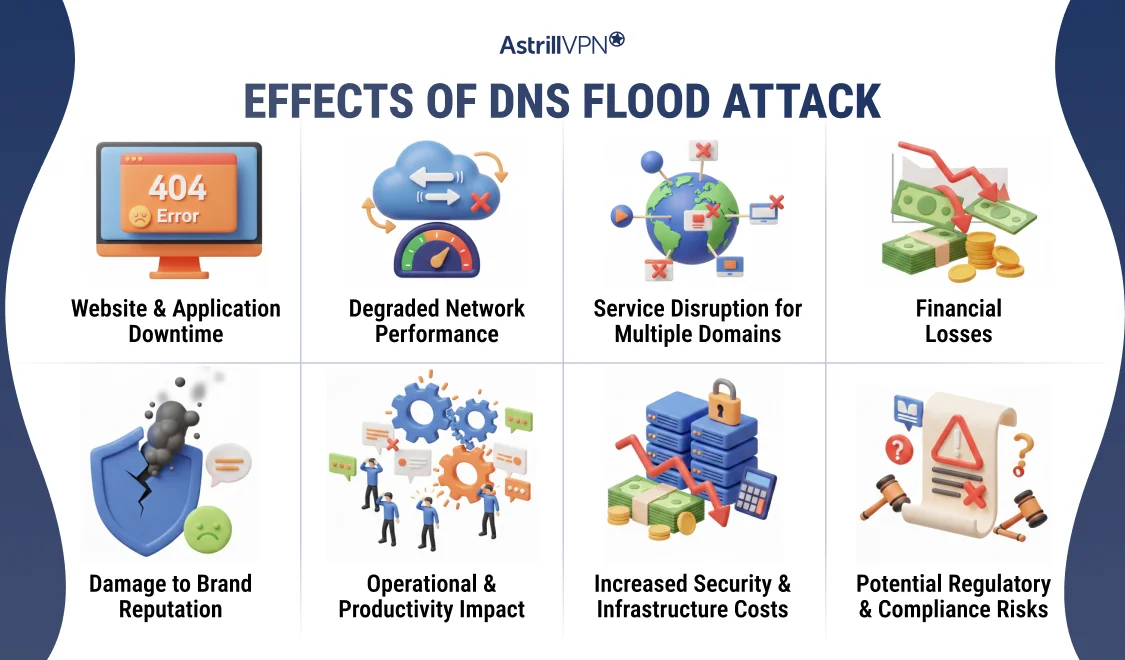
A DNS flood attack can have wide-ranging consequences because DNS is a foundational service for almost every online activity. When DNS availability or performance is disrupted, the impact extends beyond a single website and can affect entire networks and business operations.
Website and Application Downtime
One of the most immediate effects of a DNS flood attack is the downtime of websites and applications. When DNS servers cannot resolve domain names to IP addresses, users are unable to access websites or online services, even if the underlying servers are functioning normally. This often results in error messages, failed connections, or extremely slow page loading.
Degraded Network Performance
DNS floods consume a significant amount of bandwidth and processing power. As DNS traffic overwhelms the network, other critical services may experience latency, packet loss, or instability. Internal systems that rely on DNS for communication can also experience slowdowns, which can impact overall network efficiency.
Service Disruption for Multiple Domains
If multiple domains rely on the same DNS provider or infrastructure, a single DNS flood attack can simultaneously disrupt all of them. This shared dependency can lead to widespread outages, especially for hosting providers, cloud platforms, or managed DNS services.
Financial Losses
Prolonged DNS outages can lead to direct financial losses. E-commerce platforms may lose sales, subscription services may experience churn, and organizations may incur costs related to incident response, mitigation services, and infrastructure upgrades. For some businesses, even a short outage can have a significant economic impact.
Damage to Brand Reputation
Repeated or prolonged service disruptions can harm an organization’s reputation. Users may lose trust in a brand if they experience frequent downtime or unreliable access, which can potentially lead them to switch to competitors. Reputation damage often lasts longer than the attack itself.
Operational and Productivity Impact
A DNS flood attack can disrupt internal operations by preventing employees from accessing email, internal applications, or cloud-based tools. This results in reduced productivity, delayed workflows, and increased strain on IT teams as they work to restore services.
Increased Security and Infrastructure Costs
Following a DNS flood attack, organizations typically need to invest in more robust DDoS mitigation tools, upgraded DNS infrastructure, and enhanced monitoring systems. While these improvements are necessary, they add to long-term operational expenses.
Potential Regulatory and Compliance Risks
For industries that require high availability or data protection compliance, DNS-related outages can trigger regulatory scrutiny. Failure to maintain service availability may result in penalties, audits, or contractual violations, particularly for service providers with uptime guarantees in place.
Key Statistics for DNS Flood Attack
DNS-based attacks are among the most common DDoS attack vectors, frequently ranking in the top three methods used by attackers worldwide.
- Security reports show that DNS flood and amplification attacks account for over 40–50% of all network-layer DDoS attacks in many recent reporting periods.
- Large-scale DNS flood attacks can generate over 1 million DNS queries per second, overwhelming even well-configured DNS servers.
- DNS amplification attacks can increase traffic volume by 30 to 70 times, turning small requests into massive response floods.
- Some of the largest DNS-related attacks have exceeded hundreds of gigabits per second, targeting DNS infrastructure and upstream networks.
- DNS floods commonly utilize UDP-based traffic, which accounts for more than 90% of DNS attack traffic due to its connectionless nature.
How to Detect a DNS Flood Attack?
Detecting a DNS flood attack early is critical to minimizing downtime and preventing widespread service disruption. Because many DNS flood attacks use legitimate-looking requests, detection often relies on identifying abnormal patterns rather than obvious malicious signatures.
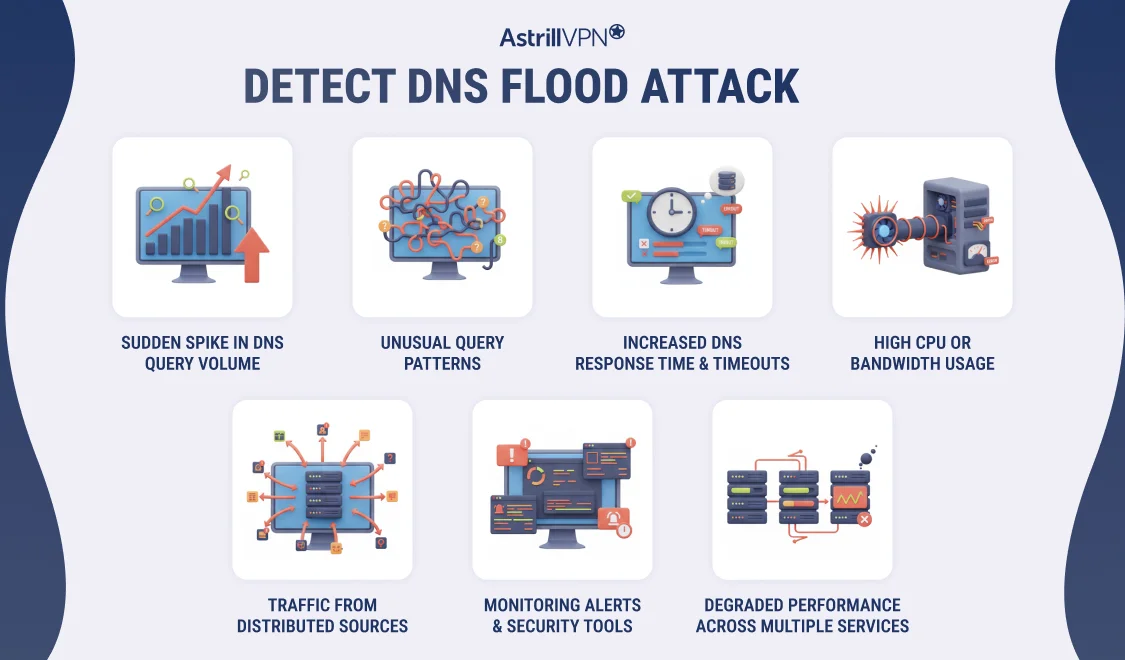
Sudden Spike in DNS Query Volume
One of the clearest indicators of a DNS flood attack is a rapid and sustained increase in DNS queries. Regular DNS traffic follows predictable patterns based on time of day and user behavior. When query rates suddenly surge far beyond typical baselines without a corresponding increase in legitimate user activity, it is often a sign of an ongoing DNS flood.
Unusual Query Patterns
DNS flood attacks frequently generate repetitive or suspicious query behavior. This may include repeated requests for the same domain, queries for random or non-existent subdomains, or a sharp rise in NXDOMAIN responses. These patterns suggest that traffic is being artificially generated to exhaust DNS server resources.
Increased DNS Response Time and Timeouts
As DNS servers become overwhelmed, response times increase noticeably. Users may experience slow website loading, delayed application access, or complete DNS resolution failures. Frequent timeouts in DNS logs are a strong indicator that the server is having difficulty processing incoming requests.
High CPU or Bandwidth Usage
A DNS flood attack places heavy strain on server and network resources. Monitoring tools may show unusually high CPU utilization, memory consumption, or outbound and inbound bandwidth usage on DNS servers. These resource spikes often occur even when application traffic remains normal.
Traffic from Distributed Sources
DNS flood attacks commonly originate from botnets spread across multiple geographic regions. Logs may show DNS queries originating from a large number of unfamiliar IP addresses or countries that do not align with the typical user distribution. This wide dispersion makes the traffic harder to block but easier to identify as abnormal.
Alerts from Monitoring and Security Tools
Advanced DNS monitoring, intrusion detection systems, and DDoS protection platforms can automatically flag anomalies associated with DNS floods. Alerts triggered by abnormal query rates, protocol misuse, or traffic anomalies often provide the earliest warning of an ongoing attack.
Degraded Performance Across Multiple Services
Because DNS is a shared dependency, a DNS flood attack may cause performance issues across multiple websites, applications, or internal services simultaneously. When numerous systems experience resolution failures simultaneously, the DNS infrastructure is often the underlying cause.
How to Prevent DNS Flood Attacks?
Preventing DNS flood attacks requires a proactive and layered defense strategy. Since DNS is a critical and always-on service, security controls must be designed to absorb high traffic volumes while filtering malicious requests without disrupting legitimate users.
Implement Rate Limiting
Rate limiting restricts the number of DNS queries that a single IP address or network can send within a defined time period. By enforcing query thresholds, DNS servers can block abusive traffic before it consumes excessive resources, significantly reducing the impact of DNS floods.
Use Anycast DNS Architecture
Anycast DNS distributes incoming DNS requests across multiple geographically dispersed servers using the same IP address. This approach distributes the traffic load, making it far more difficult for attackers to overwhelm a single DNS server and enhancing resilience during large-scale flood attacks.
Deploy Dedicated DDoS Protection Services
Managed DDoS protection solutions are designed to detect and mitigate DNS flood attacks in real time. These services analyze traffic patterns, identify anomalies, and automatically absorb or filter malicious DNS queries before they reach critical infrastructure.
Enable DNS Response Caching
Effective DNS caching reduces the need for repeated query processing. When frequently requested records are served from cache, DNS servers can handle higher traffic volumes while minimizing computational overhead, limiting the effectiveness of query-based floods.
Harden DNS Server Configuration
Properly configuring DNS servers helps reduce attack surfaces. This includes turning off unnecessary recursion, limiting zone transfers, applying access control lists (ACLs), and ensuring servers respond only to authorized requests.
Monitor DNS Traffic Continuously
Continuous monitoring allows early detection of abnormal query behavior. By establishing baselines for regular DNS traffic, organizations can quickly identify unusual spikes, suspicious query types, or geographic anomalies that may signal an attack.
Use Firewalls and Traffic Filtering
Firewalls can filter malicious traffic based on IP reputation, geolocation, or abnormal request behavior. Integrating DNS-aware firewalls or intrusion prevention systems adds an extra layer of protection against DDoS (Distributed Denial of Service) attempts.
Increase Redundancy and Capacity
Maintaining redundant DNS servers and sufficient bandwidth increases tolerance to traffic surges. Redundancy ensures that if one server is affected, others can continue providing DNS resolution without interruption.
Regularly Test Incident Response Plans
Conducting simulated DNS flood scenarios helps ensure that response teams and mitigation tools are ready. Regular testing reduces response time, improves coordination, and minimizes the potential impact of real-world attacks.
Conclusion
DNS flood attacks target one of the most fundamental components of the Internet. By overwhelming DNS servers with excessive queries, attackers can cause widespread outages and service disruptions. Understanding how these attacks work, recognizing early warning signs, and implementing strong prevention measures are essential for maintaining availability and reliability. With proactive monitoring and modern DDoS mitigation strategies, organizations can significantly reduce the impact of DNS flood attacks and protect their digital presence.
Frequently Asked Questions (FAQs)
Here are some frequently asked questions.
DNS amplification attacks exploit misconfigured open DNS resolvers to amplify traffic. Instead of directly flooding the target, attackers send small spoofed requests that generate much larger responses toward the victim. Regular DNS floods rely on high volumes of direct queries without amplification.
Common warning signs include sudden surges in DNS traffic, slow domain resolution, increased server CPU usage, frequent timeouts, and a spike in failed DNS lookups.
DNS amplification attacks can generate traffic volumes several dozen times larger than the original request size. In large-scale attacks, traffic can reach hundreds of gigabits per second, overwhelming even well-provisioned networks.
Yes, DNS flood attacks can impact multiple websites simultaneously if they rely on the same DNS provider or share a common DNS infrastructure. A single attack on a central DNS service can simultaneously disrupt various domains.
DNS flood attacks continue to pose a significant threat today. As internet usage grows and botnets become more powerful, attackers continue to exploit DNS due to its essential role in online communication.


No comments were posted yet