Ever wonder how often botnet attacks happen and just how vulnerable you really are? The truth may shock you. Botnets, networks of infected computers controlled by hackers, are one of the biggest threats in cybersecurity today. And the scary part is, your computer could be part of one right now without you even knowing it.
Table of Contents
What Is a Botnet?
A botnet is a network of infected computers, known as bots, that are under the control of a hacker. These bots are usually regular PCs and devices that have been compromised by malware and are now remotely controlled. The hacker uses the collective power and resources of the botnet to carry out cybercrimes like:
- Distributing spam and malware
- Launching DDoS attacks to take down websites
- Stealing personal data and account information
Once your device is infected with botnet malware, it can be difficult to remove. The hacker works hard to keep their botnet secret so they can utilize your resources without you even realizing it.
The truth is botnet attacks have become incredibly common. Some estimates show over 30% of all PCs connected to the internet are part of a botnet. These malicious networks are responsible for over 80% of all spam and a large portion of DDoS assaults.
What is a Botnet attack and how it works?

A botnet attack is a network of compromised computers that can be remotely controlled by an attacker. Once infected with malware, each device becomes a “bot” that can be manipulated without the owner’s knowledge. These bots are often used to launch coordinated cyber attacks.
The “bot herder,” also known as the “bot master,” controls the botnet using command and control (C&C) software. The bot herder sends commands to the bots, instructing them to carry out malicious activities like distributed denial-of-service (DDoS) attacks, spam email campaigns, bitcoin mining, and data theft.
Because botnets are made up of many devices scattered around the world, they can be difficult to detect and disrupt. The bot herder will often use anonymizing techniques to hide their identity and location. As technology and security practices evolve, bot herders are constantly adapting their methods to avoid detection and continue manipulating their botnets.
The scary truth is botnet attacks have become extremely common. Once infected, your device can become a pawn used to harm others at any time.
Types of Botnet
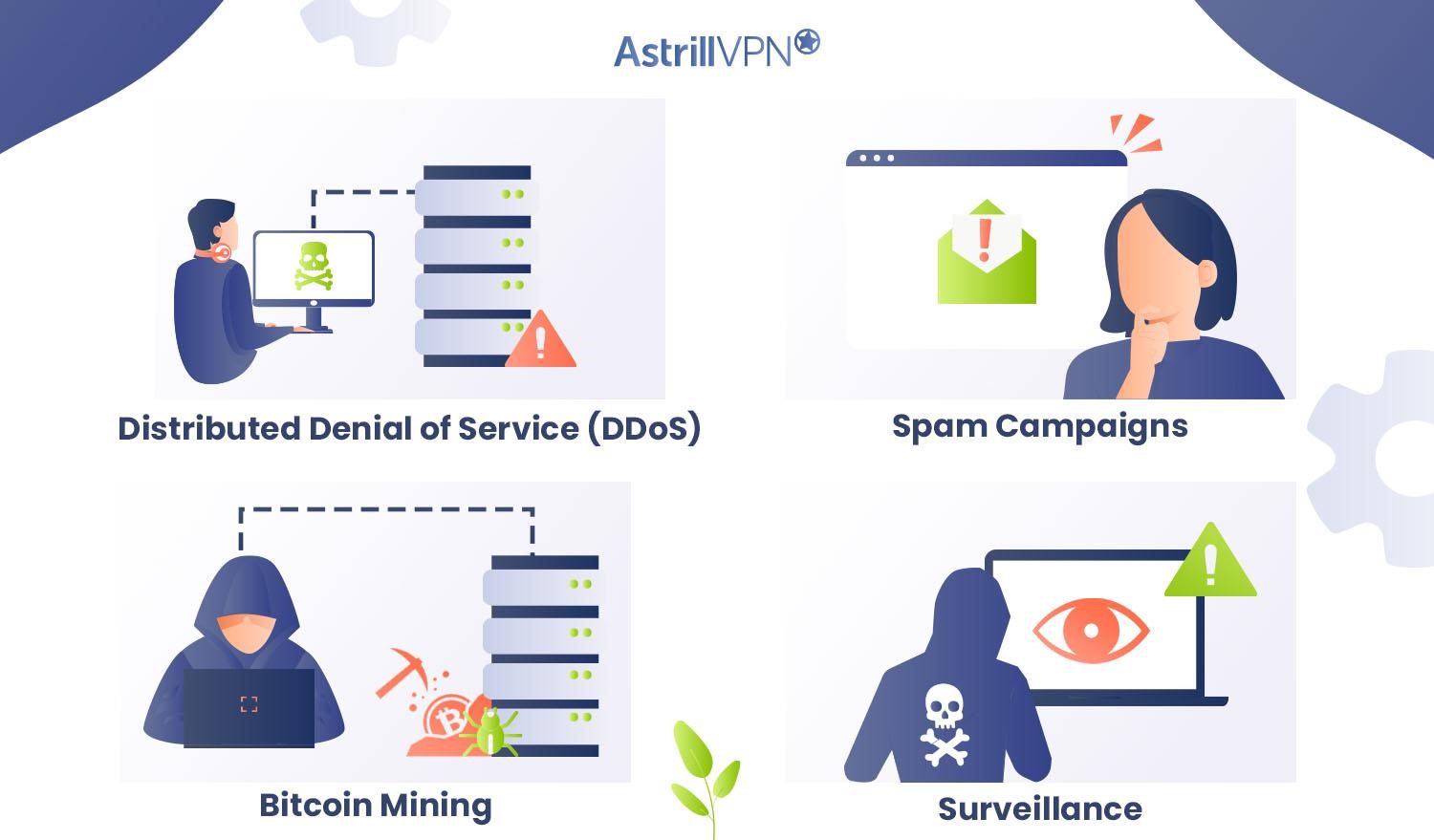
Botnet attacks come in a few common forms. Each uses a network of infected computers under the control of the attacker:
Distributed Denial of Service (DDoS)
A DDoS attack floods a target website with traffic from the botnet, overloading it and taking it offline. The attacker controls the botnet to direct a massive amount of requests at the site simultaneously, more than it can handle.
Spam Campaigns
The botnet can also be used to send massive amounts of unsolicited spam emails. The spam is generated on the infected computers in the botnet and sent through their internet connections, hiding the true source.
Bitcoin Mining
Some botnets are used to mine Bitcoin and other cryptocurrencies. The combined computing power of the botnet is harnessed to solve the complex equations required for mining digital coins. The profits go to the botnet operator rather than the computers’ owners.
Surveillance
In some cases, botnets are used to gather information on the people using the infected devices. Everything from keylogging to accessing webcams and microphones is possible, allowing the botnet operator to spy on victims.
As you can see, botnets pose a serious threat with a variety of malicious uses. The fact that attackers can gain control of thousands or even millions of devices should be alarming and highlights the importance of cybersecurity. With vigilance and proper precautions, you can reduce your risk of becoming part of a botnet.
The Rising Botnet Threat: How common are Botnet Attacks?
Botnet attacks are on the rise for several reasons. As more devices become connected to the Internet of Things (IoT), cybercriminals have more targets to infect and form into botnets. It’s estimated that by 2020, over 20 billion devices will be connected to the IoT, ranging from smart TVs and security cameras to routers and DVRs. Many of these devices have poor default security, making them easy prey for hackers.
Growth of Ransomware and Cryptojacking
Two of the most common payloads distributed by botnets are ransomware and cryptojacking code. Ransomware encrypts files and holds them for ransom, while cryptojackers secretly use your device’s computing power to mine cryptocurrency. As these types of cybercrime have become more lucrative, criminal organizations have invested heavily in developing stealthy botnets to spread them.
Some of the largest known botnets, like Mirai and Trickbot, now have millions of infected devices under their control. They are rented out or sold to the highest bidder, enabling massive attacks that are difficult to mitigate. A single Mirai attack in 2016 took down major websites like Twitter, Netflix, and PayPal.
With botnets only continuing to expand in size and sophistication, individuals and organizations must take proactive steps to secure their connected devices. Using strong, unique passwords, enabling two-factor authentication when available, and keeping software up to date are some of the best ways you can help reduce the threat of becoming part of a botnet. Together, we can work to curb the growth of these dangerous cyber weapons and make the Internet a safer place.
Real-World Examples of Devastating Botnet Attacks
Botnet attacks are more common than you might realize. Here are a few well-known examples of the damage they can cause:
Mirai (2016)
The Mirai botnet infected Internet of Things (IoT) devices like routers, webcams, and DVRs. At its peak, it compromised over 600,000 IoT devices. The botnet was used to conduct massive distributed denial-of-service (DDoS) attacks, including one against DNS provider Dyn that disrupted major websites like Twitter, Reddit, and Spotify.
Conficker (2008)
This worm targeted vulnerabilities in Windows to spread to millions of computers worldwide. It allowed cybercriminals to steal personal data, distribute malware, and conduct DDoS attacks. At the height of the infection, Conficker had compromised over 9 million Windows PCs.
Srizbi (2007)
The Srizbi botnet infected millions of PCs running outdated antivirus software and security patches. It was designed to send huge volumes of spam emails to unsuspecting users. At its peak, Srizbi could send out over 60 billion spam emails per day, accounting for roughly half of all spam on the internet at the time.
As these examples show, botnet attacks pose a serious threat. They are often used to steal data, spread malware, send spam, or disrupt internet services. The massive scale of some botnets means that when they activate, the results can be catastrophic.
How to protect yourself and your Business from Botnet Attacks?

To protect yourself and your business from botnet attacks, there are a few key steps you should take:
Use strong, unique passwords
Use complex passwords that are different for each account. Long, random passwords with a minimum of 12 characters are best. Enable two-factor authentication whenever possible.
Be cautious of phishing emails
Never click links or download attachments from unsolicited emails. Phishing emails are a common way for botnets to infect devices. Delete suspicious emails right away.
Keep your software up to date
Install updates for your operating systems and software as soon as they become available. Updates often contain security patches to prevent vulnerabilities that botnets target.
Use reputable antivirus software
Antivirus software, especially those with built-in firewalls and malware detection, can help prevent botnet infections. Run regular scans to check for any infections.
Educate your employees
Train employees on cybersecurity best practices like spotting phishing emails, using strong passwords, and keeping systems up to date. Employees are frequently targeted, so education is key.
Monitor network activity
Watch for signs of botnet activity like unusual traffic, blocked IP addresses, or sudden spikes in bandwidth usage. These could indicate an active infection.
Backup critical data
Back up important files regularly in case of infection. Some botnets can lock access to files and demand ransom payment. Backups ensure you have unencrypted copies of your data.
Staying vigilant and taking proactive steps to strengthen your cyber defenses will reduce the risk of botnet attacks. But even with the best safeguards, infections can still happen. Monitor systems closely and take action quickly if an attack occurs.
How to tell if your computer is a part of a botnet?
If your computer seems to be running slower than usual or you notice strange activity, it could be part of a botnet. Here are a few signs to watch out for:
Increased Spam or Pop-Ups
Botnets are often used to send spam, phishing emails, or launch popup ads. If you’re seeing a spike in unsolicited messages or annoying pop-ups, your device may have been compromised.
Higher Data Usage
Botnets frequently send and receive data to communicate with the command and control server. Check your internet data usage and see if there are any unexplained spikes. This could indicate your computer has been co-opted into a botnet.
Unexplained Processes Running
Botnets run hidden processes to carry out attacks without the user’s knowledge. Look for unfamiliar background processes running on your computer that are using CPU resources. End these processes immediately.
Connection to Unknown IP Addresses
Botnets connect to the control server to receive commands. Review your router or firewall logs to check for connections to unknown IP addresses. This is a telltale sign your computer has been roped into a botnet.
If any of these sound familiar, your computer could be part of a botnet. Run a reputable antivirus scan right away to check for infections. You should also change all passwords, enable two-factor authentication when available, and be on high alert for further signs of compromise. The sooner you take action, the less damage can be done. Staying vigilant and keeping your guard up is key to avoiding becoming prey for botnet operators.
How can AstrillVPN help in combating Botnet attacks?

AstrillVPN can help protect you from botnet attacks in several ways:
Encrypted Connection
AstrillVPN creates an encrypted tunnel between your device and the VPN server, hiding your online activity and location. This makes it much harder for botnet operators to infiltrate your system or steal your data. Even if their malware has infected your device, it will have a hard time communicating back to the botnet controller.
Hiding Your IP Address
AstrillVPN assigns you a new IP address, masking your real one. This hides your actual location and identity, making you a less obvious target. Botnets often scan for vulnerable devices by IP address, so using a VPN helps you blend into the crowd.
Secure Wi-Fi Protection
Public Wi-Fi networks are a prime target for botnet operators. AstrillVPN encrypts your connection even on unsecured networks by giving you access to perform VPN leak test, preventing hackers from accessing your data or planting malware on your device. You can connect with peace of mind from any hotspot.
Added Security Features
AstrillVPN includes additional features like an Internet kill switch, which cuts off all internet traffic if your VPN connection drops. This prevents your real IP and data from being exposed. AstrillVPN also offers malware and ad blocking for an added layer of protection.
Using a reputable VPN service like AstrillVPN, with strong encryption and security features, is one of the best ways to defend against the threat of botnet attacks. Combined with good digital hygiene like strong passwords, updated software, and caution around unsolicited links or downloads, you can significantly reduce your risk of becoming part of a botnet.
FAQs
Botnets are malicious networks of infected devices controlled by hackers. Here are some common questions about these cyber threats:
Botnets can persist for years, as long as the command and control servers remain active and infected devices stay connected. Hackers frequently update botnet code to evade detection, allowing them to keep botnets operational indefinitely.
A botnet IP address refers to the internet protocol address of a device that has been infected and assimilated into a botnet. These IP addresses are often blacklisted by cybersecurity firms once detected as part of a botnet. However, hackers will frequently change IP addresses used by a botnet to avoid blacklisting.
Performing a factory reset of an infected device may remove the botnet malware, depending on the sophistication of the infection. As botnets become more advanced, the malware can embed itself deeper into the device’s software and survive a reset. The only sure way to remove a botnet is to perform a hard reset of the device, wiping it completely clean to factory settings. You should then update all software and change account passwords to fully remediate the device.
Conclusion
These were the cold hard facts about botnet attacks. They’re more common than you probably realized and becoming more sophisticated each day. While the cybercriminals behind these attacks get smarter, the good news is you can outsmart them by taking some basic precautions. Staying vigilant and proactively protecting yourself online is the best defense against becoming part of a botnet. Take control of your cybersecurity and don’t become another pawn in their game.



No comments were posted yet