Famous DDoS Attacks Explained | Real-World Examples

Arsalan Rathore
When organizations review DDoS attack examples, they examine the events that have caused widespread outages, financial losses, and reputational damage. These cases help security teams understand how large DDoS attacks are constructed, how quickly they can escalate, and why each new wave often surpasses the one before it.
The DDOS attacks force businesses to reassess their defenses and highlight the importance of proactive protection. A secure network environment, supported by tools like a reliable VPN, helps limit exposure and makes online activity harder for attackers to identify.
This guide focuses on the most significant attacks that influenced cybersecurity strategies worldwide and explains what each event revealed about the evolving threat landscape.
Table of Contents
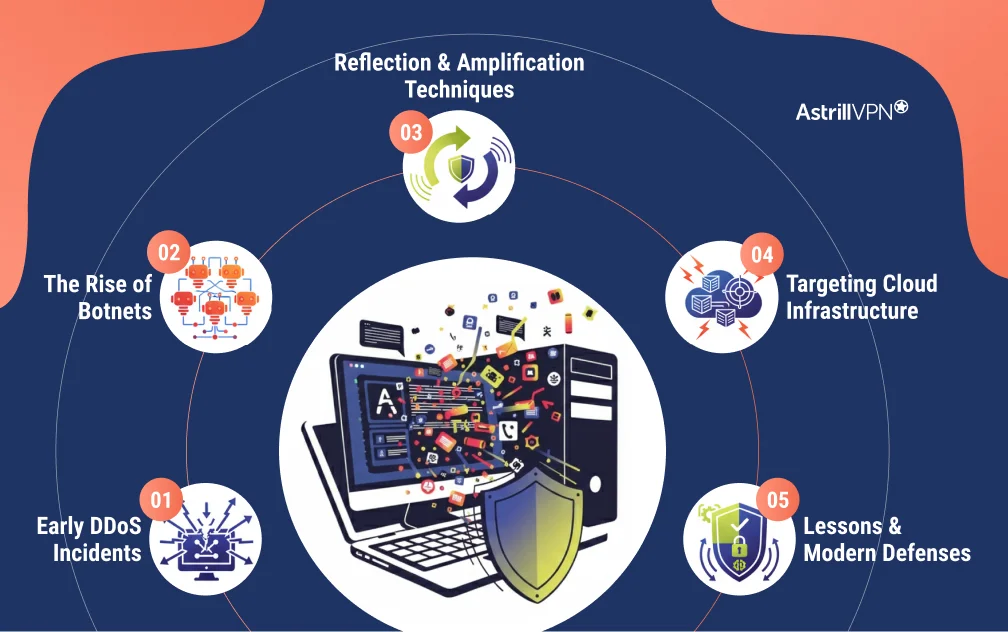
The Evolution of Big DDoS Attacks Over Time
Early DDoS Incidents
In the late 1990s and early 2000s, DDoS attacks were relatively small and straightforward. Attackers relied on a limited number of compromised computers, often causing temporary outages that were noticeable but rarely catastrophic in nature. These early attacks set the foundation for understanding network vulnerabilities.
The Rise of Botnets
As the internet expanded, the number of connected devices skyrocketed. Unsecured routers, webcams, and other smart devices became prime targets for attackers. By compromising these devices, attackers can build botnets with thousands or even millions of machines, enabling some of the first large-scale DDoS attacks that force organizations to rethink their network security.
Reflection and Amplification Techniques
Attackers soon discovered methods to multiply the impact of their campaigns. By exploiting open servers and public protocols, they could amplify traffic and overwhelm networks with far greater force. These innovations allowed DDoS campaigns to reach unprecedented levels, laying the groundwork for record-breaking attacks that would capture global attention.
Targeting Cloud Infrastructure
As more businesses rely on cloud platforms, attackers have shifted their focus to these environments. Large-scale campaigns targeting cloud services became common, resulting in several of the most notable DDoS attack examples. Each event often sets new benchmarks for the most significant DDOS attack ever, highlighting the scale of modern threats.
Lessons and Modern Defenses
The evolution of DDoS attacks shows a constant escalation between attackers and defenders. Security teams have responded with real-time monitoring, automated mitigation, and distributed filtering, while users must maintain digital hygiene to avoid contributing to botnets. A secure connection, such as a trusted VPN, adds an extra layer of protection, making it harder for attackers to target devices or intercept network activity.
Prominent Examples of DDoS Attacks
DDoS attacks have left an undeniable mark on the internet. Some incidents were so significant or innovative that they changed how organizations approach cybersecurity. Exploring these events provides insight into how attackers operate and how big DDoS attacks have evolved.
Mafiaboy and the Early High-Profile Attacks (2000)
One of the first attacks to capture global attention was carried out by a teenager known as Mafiaboy. Using relatively simple tools and a limited network of compromised computers, he targeted major websites including Yahoo, eBay, Amazon, Dell, and CNN.
These attacks caused widespread outages and disrupted online services for several days, highlighting the vulnerability of even the most prominent platforms. This event is often cited as an early example of a DDoS attack because it demonstrated that even small resources can have an outsized impact when used strategically.
The Mirai Botnet and the Dyn Attack (2016)
The Mirai botnet represented a significant turning point in DDoS history. It leveraged unsecured Internet of Things (IoT) devices, such as webcams and routers, to launch large-scale attacks. Mirai first gained attention with the attack on Brian Krebs’ security blog, which overwhelmed his site with hundreds of gigabits of traffic.
Later in the same year, Mirai powered the Dyn DNS attack, briefly taking down major websites including Twitter, Netflix, and PayPal. This incident illustrates the shift toward using massive, distributed networks of everyday devices to execute big DDoS attacks that could impact millions of users simultaneously.
GitHub and the Memcached Attack (2018)
In 2018, GitHub experienced one of the largest DDoS attacks ever recorded. The attack, using misconfigured memcached servers, reached an astonishing 1.35 terabits per second. It lasted only a few minutes but demonstrated how amplification techniques could dramatically increase the scale of an attack.
GitHub’s mitigation efforts, in collaboration with its traffic scrubbing partner, showcased how modern organizations defend against extremely high-volume incidents. This attack remains a key example of a DDoS attack due to its technical sophistication and record-setting scale.
Microsoft Azure and Cloud-Level Attacks (2021)
Cloud infrastructure became a target as businesses increasingly relied on remote services. Microsoft Azure reported mitigating multiple attacks exceeding three terabits per second, exploiting reflection vectors across UDP-based protocols.
These attacks underscore the need for cloud providers to maintain robust defenses against the growing threat of cloud networks. They serve as examples of big DDoS attacks that push the limits of modern infrastructure.
The Largest Recorded DDoS Attack (2025)
The continuous escalation in attack size culminated in 2025 when Cloudflare mitigated an attack that peaked at 7.3 terabits per second. This remains the most significant DDOS attack ever recorded. Thousands of IP addresses and multiple attack vectors were used in a coordinated effort that lasted under a minute, yet delivered more than 37 terabytes of data. The scale of this attack highlights how modern DDoS incidents are no longer just a threat to individual organizations but a challenge to the internet’s resilience.
Each of these incidents highlights different aspects of DDoS evolution, from early exploits to modern, cloud-scale operations. Studying these attacks provides critical lessons in preparation, mitigation, and understanding how attackers innovate. These famous DDoS attack examples continue to influence the development of cybersecurity strategies today.
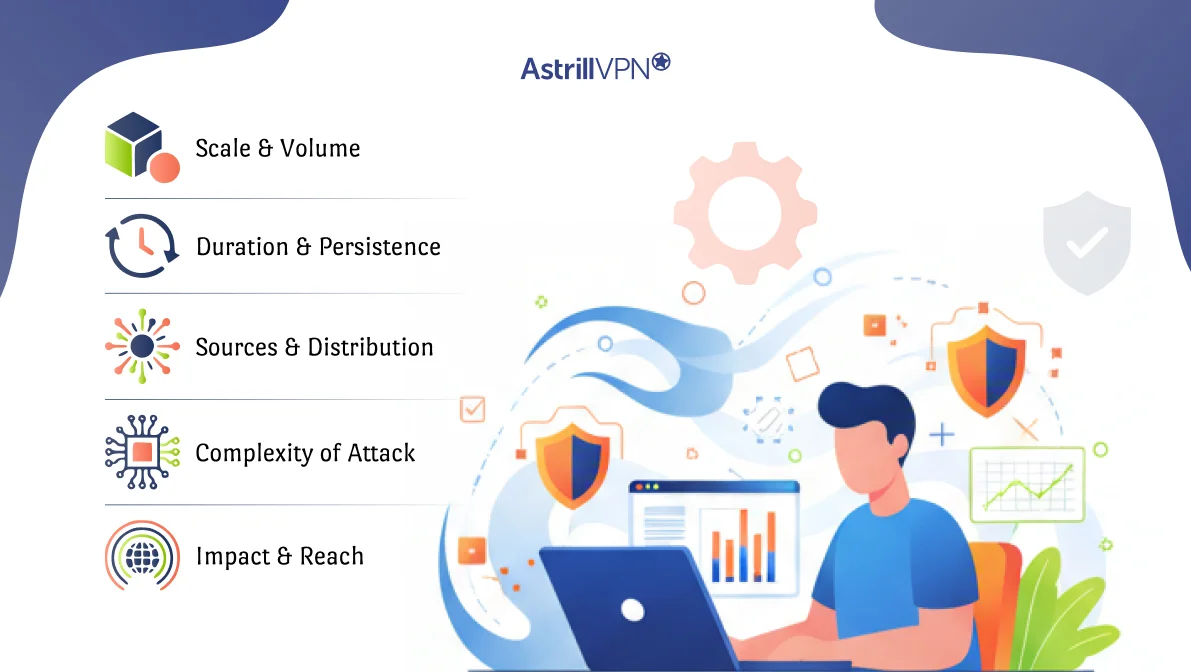
Comparative Analysis: What Makes These the “Biggest” DDoS Attacks Ever
Understanding why specific incidents are considered the biggest requires examining several key factors beyond simple traffic volume. Comparing historic cases helps reveal patterns in attacker strategies and the scale of modern threats.
Scale and Volume
One of the most obvious measures is sheer size. Attacks are often evaluated by the total traffic directed at the target, measured in gigabits or terabits per second. The most significant DDOS attack ever, recorded in 2025 at 7.3 terabits per second, illustrates the extremes attackers can reach today. Earlier incidents, such as the 2018 GitHub memcached attack, reached 1.35 terabits per second, demonstrating how amplification techniques can magnify traffic far beyond the capacity of individual machines.
Duration and Persistence
Size alone does not define impact. The length of an attack and its ability to maintain pressure are equally important. Some attacks, such as the early Mafiaboy campaigns, lasted hours or days, resulting in extended service disruptions. Others, like modern cloud-level attacks, may last only minutes but deliver massive volumes of traffic, testing the limits of mitigation strategies.
Number of Sources and Distribution
Another defining factor is the number of devices or IP addresses involved. Large botnets, often composed of unsecured IoT devices, enable attacks to come from thousands or even millions of sources simultaneously. The Mirai botnet, for example, demonstrated how distributed networks of everyday devices could be harnessed to carry out some of the first big DDoS attacks with real global impact.
Complexity of Attack Vectors
Modern attacks rarely rely on a single method. Reflection, amplification, multi-vector assaults, and exploitation of cloud infrastructure have all contributed to record-setting incidents. The combination of multiple techniques increases difficulty for defenders and amplifies the scale, making these events stand out among other DDoS attack examples.
Impact and Reach
Ultimately, the significance of an attack is determined by its real-world impact. Outages affecting millions of users, disruption to critical services, or financial loss elevate an attack’s prominence. Some of the most famous DDoS attacks not only caused downtime but also forced companies and security teams to rethink infrastructure, implement stronger protections, and develop global response strategies.
| Attack | Year | Peak Traffic | Duration | Number of Sources | Key Impact |
| Mafiaboy Campaign | 2000 | Hundreds of Mbps | Hours to Days | Limited | Temporarily took down Yahoo, eBay, Amazon, CNN, and Dell, exposing vulnerability of major websites |
| Mirai Botnet / Dyn Attack | 2016 | ~1.1 Tbps | Minutes to Hours | Thousands of IoT devices | Took down major websites including Twitter, Netflix, and PayPal, demonstrating IoT botnet power |
| GitHub Memcached Attack | 2018 | 1.35 Tbps | Minutes | Misconfigured memcached servers | Largest recorded attack at the time, tested GitHub’s mitigation strategies, highlighted amplification techniques |
| Microsoft Azure Cloud Attacks | 2021 | ~3.47 Tbps | Minutes | Thousands of IPs across multiple reflection vectors | Targeted cloud infrastructure, showcasing the growing threat to enterprise cloud services |
| Cloudflare Record Attack | 2025 | 7.3 Tbps | Under a Minute | Thousands of IP addresses, multi-vector | The biggest DDOS attack ever recorded, delivered over 37 terabytes in under a minute, stressing global defenses |
Impact and Consequences of Big DDoS Attacks
Big DDoS attacks do more than disrupt services. Their effects can ripple across businesses, users, and entire networks, making them a critical cybersecurity concern.
Key Consequences
- Downtime caused by large-scale attacks can halt transactions, reduce revenue, and damage customer trust. Even brief outages can have lasting reputational consequences.
- Massive traffic overwhelms servers and networks, sometimes causing hardware stress or failures. Modern attacks reaching terabits per second test even the most resilient infrastructures.
- DDoS attacks can be used as a distraction to cover up breaches. Personal devices may be recruited into botnets, exposing sensitive data. A reliable VPN helps mask connections and reduce risk.
- High-profile outages can trigger regulatory scrutiny. Organizations are expected to maintain defenses and report incidents promptly, reinforcing the need for proactive security strategies.
- Attacks drive investment in redundancy, traffic scrubbing, and monitoring systems. They highlight the importance of securing networks, IoT devices, and cloud infrastructure against future threats.
Conclusion
Famous DDoS attacks reveal just how quickly the internet can be disrupted when attackers harness vast networks of compromised devices. From early campaigns, such as Mafiaboy’s attacks, to modern record-setting incidents, these events have shaped cybersecurity practices and highlighted the vulnerabilities inherent in connected systems.
Studying DDoS attack examples helps organizations understand the scale, sophistication, and persistence of these threats. Big DDoS attacks are no longer isolated events; they demonstrate the potential for widespread disruption, financial loss, and privacy risks. Each record-setting incident, including the most significant DDoS attack ever, sets new benchmarks and forces both businesses and users to rethink their security strategies.
For individuals and organizations, preparation is essential. Maintaining strong digital hygiene, securing devices, and utilizing tools like a trusted VPN can help reduce exposure, protect online activity, and make it more difficult for attackers to exploit networks.
FAQs
The Mirai botnet is a network of compromised IoT devices like cameras and routers. It coordinated these devices to send massive traffic to targets, powering high-profile attacks such as the 2016 Dyn DNS attack and the attack on Brian Krebs’ blog.
Yes, OVH offers built-in DDoS protection with traffic filtering and monitoring to keep websites and servers online during attacks.
It targeted Dyn’s DNS servers, which direct internet traffic, making major websites like Twitter, Netflix, and PayPal inaccessible. The attack’s scale and impact on critical infrastructure made it particularly disruptive.
Yes, it reached 1.35 terabits per second using memcached amplification. Despite lasting minutes, it set a record at the time and is widely cited as a major DDoS incident.
Recent attacks use multi-vector strategies, exploiting amplification through UDP-based protocols and targeting cloud infrastructure and unsecured IoT devices, allowing record-breaking traffic bursts in very short time frames.


No comments were posted yet