What is CyberSecurity: Types, Measures and Best Practices

Arsalan Rathore

Just like how our security matters in the real world, our digital safety is of paramount importance. Cybersecurity is the practice of staying safe when connected to the internet and when protecting internet-reliant devices, such as databases, hardware, and even software.
This protection is against hackers and malicious actors. In this day and age, we use the internet on a daily basis, and we do all sorts of things online. We work from home via an internet connection, we shop online, and we even share personal moments with our loved ones. All of this comes under our Personally Identifiable Information (PII).
There’s a cyberattack every 39 seconds, and the victim can be anyone. In 2021, around 1,862 data breach cases were reported, which was the highest ever number of data breaches ever. This is a clear indication that cyberthreats are growing at an exponential pace. Every day millions of cyberattacks are carried out globally and the ones that aren’t prepared for it face a great loss.
Hackers, malicious third parties, and even general trackers on certain websites may collect user information for a variety of reasons. Most unwanted third parties may sell this information to advertisers. Some hackers may also sell it on the dark web for nefarious reasons.
Government-sponsored hackers may also collect some of this data for political reasons, aiming to further impose embargos and censorship on activists or whistleblowers.
Table of Contents
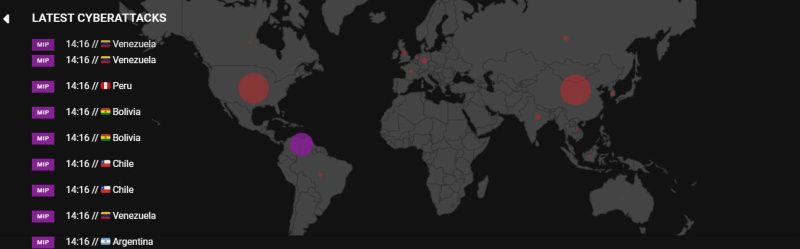
Global Cyber-Attacks Stats at a Glance
- In 2024, Over 40% of businesses in the United Kingdom reported experiencing a cyber attack or security breach in the previous 12 months, according to the UK Government Cyber Security Breaches Survey 2024. This marks a significant increase from 39% in 2022
- As of January 2023, Greece tops the National Cyber Security Index (NCSI) with an impressive score of 96.10. The countries with the highest NCSI scores are Greece (96.10), Lithuania (93.51), Belgium (93.51), Estonia (93.51), and the Czech Republic (92.21).
- The retail sector is anticipated to face a staggering global cost of $48 billion in 2023 due to eCommerce fraud.
- From 2023 to 2027, businesses will incur a massive financial loss of $343 billion due to online payment fraud.
Some Key Cybersecurity Facts
- Cybercrime is projected to cost the global economy $10.5 trillion annually by 2025, up from $9.5 trillion in 2024 and a dramatic rise from $3 trillion in 2015
- Ransomware accounts for 70% of all malware-related breaches.
- The average cost of a ransomware attack has risen to $4.54 million.
- Only 8% of businesses that pay a ransom recover all their data.
- 94% of all malware is delivered via phishing emails, making it the most common attack vector.
- Phishing attacks continue to grow, with nearly 1.9 million incidents worldwide.
- Nearly 50% of all cyberattacks target small businesses, which are seen as easier targets due to limited cybersecurity resources.
- Over 450,000 new malicious programs are detected daily in 2024.
- Global cybersecurity spending is projected to reach $215 billion in 2024, growing at a rate of 14.3% annually.
- In the first half of 2023 alone, ransomware extortion totaled $176 million more than the previous year.
Why is cybersecurity important?
Personally Identifiable Information (PII) includes your phone number, email address, financial details, and other personal information that should remain private.
Because most banking and personal apps require two-factor authentication, losing control of your phone number can lead to significant problems. Hackers can hijack your phone, steal your 2FA codes, and gain direct access to any account or device linked to your number. This could, then, lead to further problems, since our smartphones have a large amount of personal data.
Also, configuring your online data storage properly is also important. Check Point reported that in 2021, personal data of more than 100 million Android users were leaked online due to misconfigured cloud services.
Additionally, if a cybercriminal or a hacker is able to gain access to your baking credentials, they can not only collect data on your transactions but can also make transactions for themselves. This can usually be done through phishing and malware applications, or even devices that make use of card-skimming software.
All of this, together, can allow a hacker to gain access to not only your personal data but also interfere in your offline life. They can commit identity theft, sell your personal information on the dark web, or even create clone cards which can cause greater loss of your financial assets.
According to PurpleSec, the most reported 5 cyber crimes in 2023 were:
- Extortion
- Identity theft
- Personal data breach
- Non-payment
- Phishing attacks
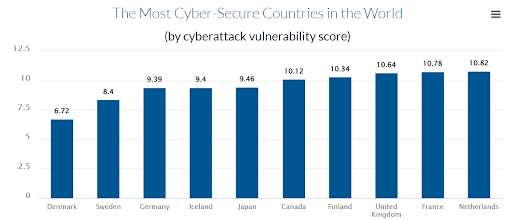
According to a study by Comparitech, Netherlands was the most Cyber-secure country in the world.
Types of cyberattacks
We already know that cybersecurity measures are always developing, but we must also be mindful of how cyberattacks are also becoming more sophisticated. Here are some types of cyberattacks to keep in mind so that you may best protect yourself against them.
Malware
Malware is short for Malicious Software, which refers to software or applications that have unwanted features. This may include access to personal or proprietary information, such as user details or passwords, and excessive control permissions, such as those pertaining to internal systems. This may also include invasive advertisements in the form of pop-ups or spam.
According to a report by Terranova Security, Over 450,000 new malicious programs and potentially unwanted applications (PUAs) are detected daily in 2024. Also, Malware attacks surged by 30% in the first half of 2024 compared to the same period in 2023, with a 92% spike recorded in May.
In short, this is software on your device that performs actions you have not consented to. This can include spyware or adware, but also keyloggers which keep track of which keys you’ve pressed on your keyboard to track your data inputs, and also ransomware, which holds your data hostage until you meet the hackers demands. This method is extremely popular for extortion and tracking user activities, which is a serious breach of privacy and safety.
Zero-Day Exploits
A zero-day exploit occurs when a vulnerability in software, hardware, or firmware remains unknown to the vendor or developer of the affected product. This lack of awareness leaves the vendor with no time to develop and release a patch or fix, so it’s a “zero-day” exploit. These exploits pose a challenge because attackers can exploit the flaw before the vendor fixes it.
Key Elements of a Zero-Day Exploit
- Vulnerability Discovery: A zero-day exploit starts with the discovery of a security flaw in software or hardware. This flaw could be due to a coding error, a design flaw, or unforeseen interactions between components. The vulnerability exists but is unknown to the vendor, meaning that no fix or patch is available.
- Exploitation: After discovering the vulnerability, attackers develop a method (an exploit) to exploit it. This exploit could allow attackers to perform malicious activities such as unauthorized access, data theft, or control of a compromised system.
- Attack Window: The critical aspect of a zero-day exploit lies in the time between the attackers discovering the vulnerability and its public disclosure or patching by the vendor. The vulnerability is considered “zero-day” during this window because no known fixes exist. Attackers often use this period to target vulnerable systems before they can be secured.
- Disclosure and Patching: Once the vendor becomes aware of the vulnerability, whether through responsible disclosure, public discovery, or a security breach, they typically begin working on a patch. After releasing the patch, the vulnerability is no longer considered a zero-day, as it becomes known and fixable.
Cybercriminals often use zero-day exploits in targeted attacks against high-profile organizations or individuals. For example, attackers may use a zero-day exploit to gain access to a government network or to steal trade secrets from a competitor.
Some attackers may attempt to exploit zero-day vulnerabilities on a mass scale, affecting as many systems as possible. Ransomware attacks, botnets, and other widespread cyber threats can be delivered via zero-day exploits.
Zero-day exploits can be sold on dark web marketplaces or used in cybercrime-for-hire schemes. Malicious actors may pay for access to zero-day vulnerabilities to conduct specific attacks for financial gain.
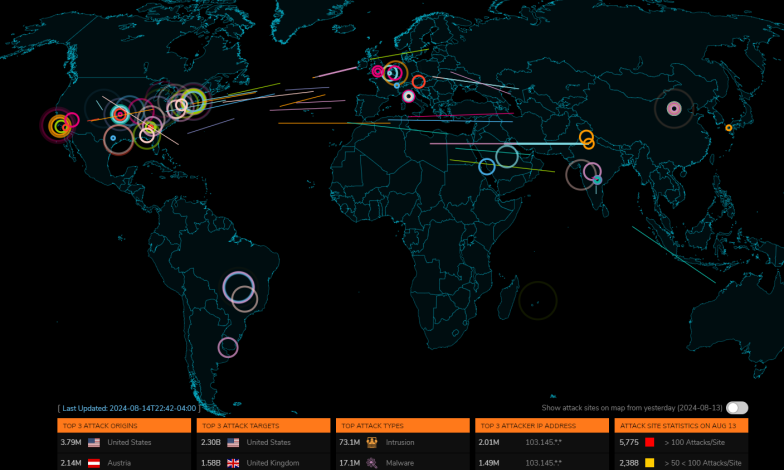
Phishing attacks
A screenshot of live Phishing attacks happening globally. [15th August 2024]
Phishing attacks are a little different from malware as they involve trickery that loops the users into revealing confidential information. A hacker or malicious third party may impersonate a bank and contact the user to gain details about their financial log-ins, such as their username or password, 2FA passwords, and other such information.
These types of threats can cause trouble even in the most impressive cybersecurity details are set up, which is why it’s important for users to also remain vigilant about their own personal safety.
According to the Cobalt.io guide, Phishing was the primary infection vector in 41% of cybersecurity incidents. Also, 6% of phishing incidents involved Business Email Compromise (BEC), with spear phishing links being used in half of these cases.
Advanced persistent threats
These types of cyberattacks are the most sophisticated ones. Advanced persistent threats (APT) may first present as a type of malware or virus to get inside a network, but once they have gained access to the inside of the network, they become undetected. This allows them to steal the largest amount of data possible, which it does so quietly and without much disruption so that the cybersecurity defense isn’t alerted to the theft.
During this time, it also tracks the growth of the cybersecurity software so that it can change itself to remain undetected. Due to how detailed and complex these attacks are, they are often conducted on a very large scale, such as by national organizations or by large criminal syndicates who have the financial means to resource this type of technical work.
In contrast to malware, which targets a wide range of devices and users, APTs are often targeted at a specific, usually singular high-value target. It is for this very reason that they are constantly developing themselves so that they can get past the defenses of a particular, specific organization.
Denial-of-Service (DoS) Attacks
DoS attacks aim to overwhelm a targeted system or network, rendering it unavailable to legitimate users. Attackers flood the target with an overwhelming traffic volume or exploit vulnerabilities to consume system resources, causing a service disruption.
Distributed Denial-of-Service (DDoS) attacks involve multiple compromised systems attacking a target simultaneously. Organizations can implement network traffic monitoring and filtering to mitigate DoS attacks, use load-balancing techniques, and employ firewalls and intrusion prevention systems.
Insider Threats
Insider threats refer to security risks posed by individuals with authorized access to an organization’s systems or data. These threats can be accidental or intentional and may arise from employees, contractors, or partners. Insider threats can lead to data breaches, intellectual property theft, or sabotage.
Organizations can mitigate insider threats by implementing access controls, monitoring user activities, conducting regular security awareness training, and maintaining a culture of security and accountability.
Ransomware
Ransomware is malware that encrypts files or restricts access to a victim’s system until a ransom is paid. It is typically delivered through malicious email attachments, compromised websites, or software vulnerabilities. Ransomware attacks can have severe consequences, causing data loss, financial losses, and operational disruptions.
Prevention measures include regularly backing up critical data, updating software and operating systems, implementing strong security practices, and educating users about potential threats.
Man-in-the-Middle (MitM) Attacks
MitM attacks occur when an attacker intercepts communication between two parties without their knowledge. The attacker can eavesdrop, alter, or inject malicious content into the communication flow. MitM attacks commonly target unsecured public Wi-Fi networks or compromised routers.
These attacks can lead to the theft of sensitive information like login credentials or financial data. Implementing encryption protocols, using trusted networks, and employing secure communication channels (e.g., HTTPS) can help prevent MitM attacks.
SQL Injection Attacks
SQL Injection attacks target web applications that rely on a database backend. Attackers exploit vulnerabilities in the application’s input fields to inject malicious SQL code, allowing them to manipulate the database or gain unauthorized access.
SQL Injection attacks can result in unauthorized data disclosure, data manipulation, or even complete system compromise. To prevent SQL Injection attacks, developers should follow secure coding practices, use parameterized queries or prepared statements, and perform regular security testing and code reviews.
Related Article: What is Cyberstalking? Recognizing the signs of prevention
Cyber-Attack Statistics
The following cybercrimes are most faced by the US companies in 2023:
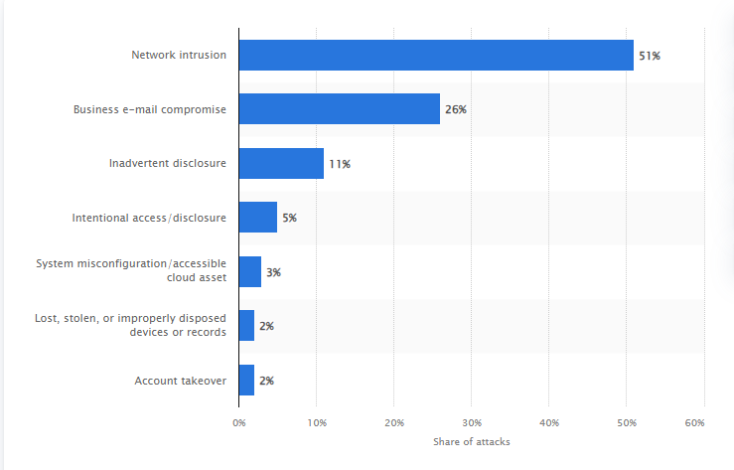
Source: Statista
According to Global Threat Report 2024, in 2023, the technology sector remained the most frequently targeted industry for interactive intrusion activity, as observed by CrowdStrike CAO. This trend continued from 2022. The following charts illustrate the relative frequency of intrusions across the top 10 industry sectors and various geographic regions.
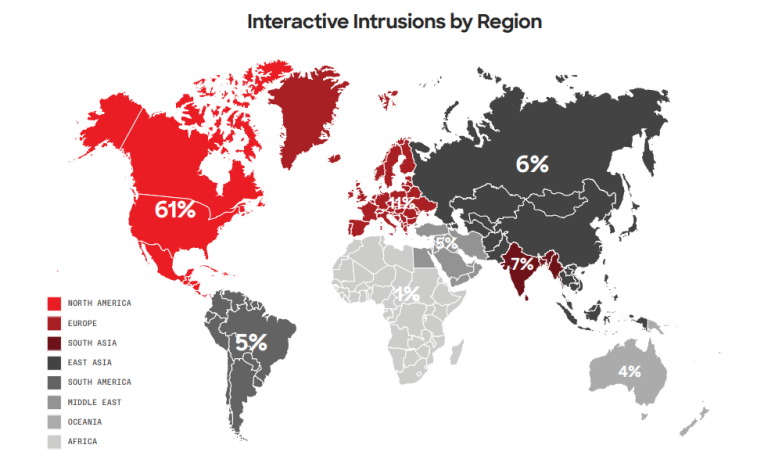
This shows that North America continues to be the most affected region. Following are the industries that were affected the most as per the report:
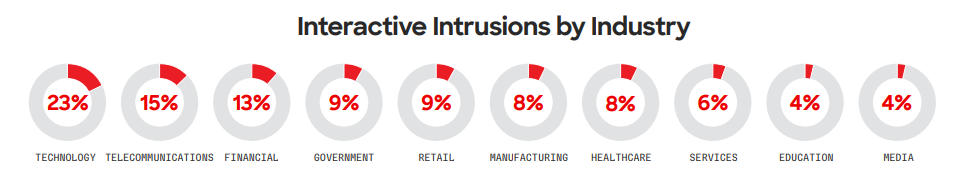
According to Verizon’s 2024 Data Breach Investigations Report, around one-third of all data breaches now involve ransomware or some form of extortion. Pure extortion attacks have risen significantly, making up 9% of all breaches.
This shift has caused a slight drop in traditional ransomware, which accounts for 23% of breaches. However, when combined, ransomware and extortion represent 32% of breaches. Ransomware remains a top threat, impacting 92% of industry sectors.
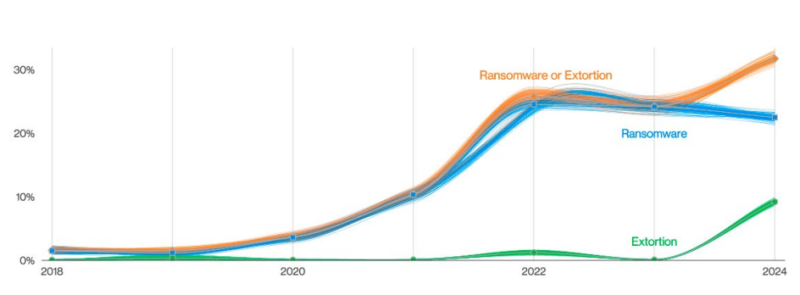
The report also indicated that Phishing report rates have steadily improved over the past few years. In 2023, security awareness exercises revealed that 20% of users successfully identified and reported phishing attempts during simulations, and 11% of those who initially clicked on a phishing email also reported it afterward. While this progress is encouraging, there’s a concerning statistic: the median time it takes for a user to click on a malicious link after opening a phishing email is just 21 seconds.
Furthermore, within an additional 28 seconds, many users enter their sensitive data, leading to the alarming finding that the median time for users to fall victim to a phishing email is less than a minute. This highlights the urgent need for enhanced training and quicker detection mechanisms to prevent these rapid phishing attacks.
Another alarming set of statistics is provided in the Data Breaches and Cyber Attacks. The following graph shows the number of known records breached per month:
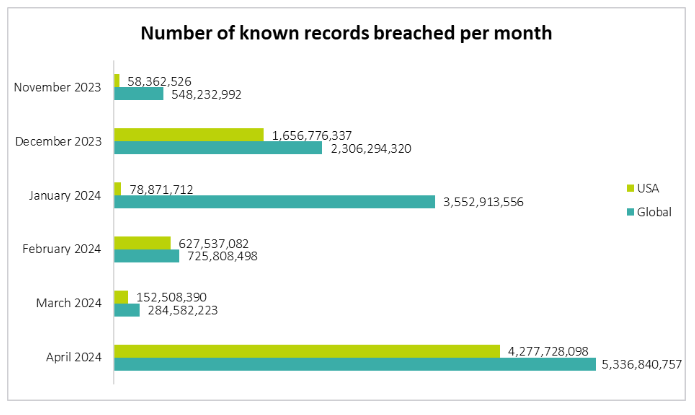
As you can see, by April 2024, the number of breaches has increased significantly. While the breaches have increased, here’s an overview of the % of organizations that took remedial actions:
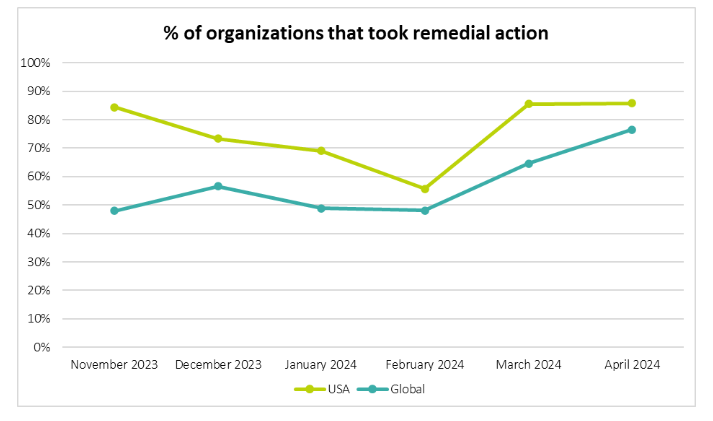
It shows that the organizations are going with the flow and are taking these breaches seriously.
Most Recent Privacy Breaches
Here are some of the most recent and significant privacy breaches in 2024:
National Public Data Breach
In August 2024, a massive data breach at National Public Data exposed 2.7 billion records on the dark web. The breach included sensitive information such as Social Security numbers, highlighting the ongoing risks associated with data brokers who collect and sell vast amounts of personal information (TechRepublic).
Evolve Bank Ransomware Attack
In July 2024, Evolve Bank suffered a ransomware attack that led to the theft of personal information from over 7.6 million people. This attack targeted fintech and startup customers, exposing highly sensitive financial data (TechRepublic).
Trello Breach
In January 2024, over 15 million Trello users were impacted by a breach that exposed private email addresses and other linked data. The compromised data heightened the risk of identity theft and phishing attacks (Security Boulevard).
Change Healthcare Attack
A ransomware attack in early 2024 severely impacted Change Healthcare, a critical player in the U.S. healthcare system. The attack led to weeks of disruption, affecting the ability of pharmacies and hospitals to process claims. Sensitive patient data, including diagnoses and treatment details, were compromised, impacting potentially a third of all Americans (CRN).
Types of Cybersecurity
As the types of threats to our security grows, so do our defenses. It’s important to know about the different measures of cybersecurity so you can remain vigilant about what best fits your needs.
Application security
This method of security is geared at strengthening an app’s internal defenses in order to minimise and prevent attacks. Most of this is established when the app itself is being built, such as in the initial stages of development.
However, as technology advances and our apps grow with our needs, these security updates may be distributed to users through patches and updates to give pre-existing defenses a boost.
Because of this, the apps are never 100% perfect or secure, unless the users are keeping up-to-date with all new patches. Cyberthreats tend to evolve and advance quickly so, realistically, it’s never possible to have a foolproof defense mechanism built into the app itself.
Intrusion detection
Intrusion detection systems (IDS) are built to scan and identify the activities running on a network, just to single out unusual activities which can turn hostile or malicious. This type of software mainly monitors behaviour that seems uncommon from users, and keeps logs of suspicious activities.
Each system has its own special method of functioning to cover all ends. Some raise alarms and some directly respond to attacks, either by isolating or trapping them or by launching a counter-attack. Generally, there are two types of tools that an IDS can use to single out and trap threats: one based on signatures, and another based on anomalies.
Systems that analyse incoming traffic for suspicious activities are network intrusion detections systems (NIDS), and system that monitor confidential files to see if there’s any incoming attack are known as Host-based intrusion detection systems (HIDS). There are also some types of IDS which can do monitor for threats and also come up with a counter-attack if needed, which are called Intrusion prevention systems (IPS).
Data loss prevention
Some methods are geared for limited losses, such as Data loss prevention (DLP) systems which ensure that data can’t be accessed by unauthorised parties. DLP systems also ensure that the data is uploaded in a secure, encrypted manner outside of the company’s servers as well.
Due to how it most frequently deals with sensitive information, this type of software is highly regulated. It maintains the security of all information whilst acting in compliance with regulatory mandates, such as HIPAA, GDPR, and others. As such, it also serves multiple purposes at the same time: monitoring, controlling, and reporting.
For instance, a healthcare provider is in need of DLP to protect patient records (including SSNs and medical histories), while a VoIP phone service implements such methods to safeguard customer data (like call recordings and personal information) from breaches.
It monitors and controls data streams, incoming and outgoing, to ensure all data is being dealt with security and there aren’t any irregularities in the flow. As it does this, it allso gives reports to confirm compliance with the rules and obligations set up by regulatory bodies.
Cloud Security
Cloud security protects data, applications, and infrastructure deployed in cloud environments. It involves securing cloud-based services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Cloud security measures include access controls, encryption, data segregation, vulnerability management, and cloud service provider security standards compliance. Properly configuring and monitoring cloud resources is essential for optimizing cloud based expenses as well as maintaining security and privacy.
Identity and Access Management (IAM)
IAM focuses on managing and controlling user access to an organization’s systems, applications, and data. It includes processes for user authentication, authorization, and access control.
IAM solutions encompass technologies like multi-factor authentication (MFA), single sign-on (SSO), role-based access control (RBAC), and privileged access management (PAM). Effective IAM practices help prevent unauthorized access, mitigate insider threats, and enforce least privilege principles.
Incident Response and Recovery
Incident response and recovery involves establishing effective plans and processes to handle cybersecurity incidents. It includes identifying, responding to, and recovering from security breaches, data breaches, and other cyber incidents. Incident response plans outline incident detection, containment, eradication, and recovery procedures.
Regular testing, interactive training, and post-incident analysis are crucial for refining incident response capabilities and minimizing the impact of cyber incidents.
Cybersecurity Tools and Techniques
Following are some key cybersecurity tools and techniques used to defend against a wide range of cyber threats:
1. Firewalls: The First Line of Defense
Firewalls are among the most fundamental cybersecurity tools. They function as a barrier between a trusted internal network and untrusted external networks, such as the Internet. Firewalls filter incoming and outgoing network traffic based on predetermined security rules.
They block unauthorized access while allowing legitimate communication to flow through. Modern firewalls are much more advanced, offering deep packet inspection, intrusion prevention, and application-level filtering features.
2. Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are crucial tools for monitoring network traffic and detecting suspicious activity. While an IDS is designed to monitor and alert security teams about potential threats, an IPS takes this further by actively blocking these threats in real time. These systems scan for known attack signatures, unusual traffic patterns, and other indicators of compromise.
3. Encryption: Protecting Data in Transit and at Rest
Encryption is a vital cybersecurity technique used to protect the confidentiality of sensitive data. Whether it’s stored on a server or transmitted across a network, encryption ensures that unauthorized parties cannot access the information without the proper decryption keys.
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption uses the same key to encrypt and decrypt data, while asymmetric encryption involves a pair of keys—one public and one private. Organizations use encryption to secure financial transactions, email communications, and even entire databases against unauthorized access.
4. Virtual Private Networks (VPNs): Securing Remote Access
A Virtual Private Network (VPN) is another essential tool in cybersecurity, particularly for organizations with remote workers. VPNs create secure, encrypted connections over the Internet, allowing users to safely access internal systems and resources from remote locations. VPNs also help hide users’ IP addresses, making it difficult for attackers to track their online activity or steal sensitive data.
AstrillVPN is one of the most commonly used VPN by both individuals and businesses to ensure secure access to private networks. VPNs are especially important for employees accessing corporate networks from public Wi-Fi, as they prevent potential hackers from intercepting the connection.
5. Multi-Factor Authentication (MFA): Enhancing Access Control
Multi-Factor Authentication (MFA) is a technique that adds an extra layer of security when users log into a system. Instead of relying solely on a password, MFA requires a second form of authentication, such as a code sent to a mobile device or a biometric scan (fingerprint or facial recognition).
This additional layer of verification significantly reduces the chances of unauthorized access, even if the password has been compromised.
6. Vulnerability Scanning: Identifying Weaknesses Before Attackers Do
Vulnerability scanning is a proactive cybersecurity technique used to detect weaknesses in a system that could be exploited by attackers. Vulnerability scanners like Nessus, Qualys, and OpenVAS scan networks, operating systems, and applications for known security flaws.
These tools generate reports that provide a detailed analysis of vulnerabilities, helping IT teams to prioritize and patch them before they can be exploited.
7. Endpoint Detection and Response (EDR): Monitoring Devices for Threats
As cyber threats continue to evolve, protecting individual devices (endpoints) is critical. Endpoint Detection and Response (EDR) tools continuously monitor endpoints such as laptops, smartphones, and servers for malicious activity. If a potential threat is detected, the EDR system alerts security teams and takes immediate action, such as isolating the device from the network to prevent further damage.
8. Penetration Testing: Simulating Attacks to Improve Security
Penetration testing, often referred to as ethical hacking, is a technique where security professionals simulate real-world attacks on a system to identify vulnerabilities.
Regular penetration testing helps ensure that an organization’s defenses are strong enough to withstand actual cyberattacks. Organizations can significantly reduce the risk of data breaches by identifying and fixing vulnerabilities before malicious hackers can exploit them.
9. Security Information and Event Management (SIEM)
SIEM systems are critical in monitoring and managing security across an organization. These tools collect and analyze logs and security data from different sources, such as servers, firewalls, and network devices.
SIEM systems can centralize and automate threat detection, making them an essential component of any cybersecurity strategy. They provide a comprehensive view of an organization’s security posture.
10. Data Loss Prevention (DLP): Safeguarding Sensitive Data
Data Loss Prevention (DLP) tools are designed to prevent sensitive data from being exposed, leaked, or stolen by unauthorized users. These tools monitor, detect, and block the transfer of sensitive information such as customer data, financial records, or intellectual property outside of the corporate network. DLP solutions typically work by classifying data and enforcing policies that dictate how data should be handled.
11. Patch Management: Keeping Systems Up to Date
Patch management is a crucial cybersecurity practice that involves regularly updating software, operating systems, and applications to fix vulnerabilities. Software vendors often release patches to address newly discovered security flaws. Failure to apply these patches can leave systems open to cyberattacks, as attackers often exploit outdated software to gain access to systems.
12. Hashing: Ensuring Data Integrity
Hashing is a technique used to ensure the integrity of data by converting it into a fixed-size string of characters, which is typically a hash value. Unlike encryption, hashing is a one-way process and cannot be reversed. Hashing is commonly used in cybersecurity to verify that data has not been altered during transmission. For example, password storage often relies on hashing to ensure that passwords are protected even if the database is compromised.
Popular hashing algorithms include SHA-256 and MD5. While hashing is a simple yet powerful tool for ensuring data integrity, it is important to use strong, modern algorithms to avoid vulnerabilities associated with weaker hashes.
13. Zero Trust Architecture: Never Trust, Always Verify
Zero Trust is a modern security model that assumes no user, device, or network—internal or external—can be trusted by default. This principle requires continuous verification of users and devices attempting to access systems, regardless of whether they are within the network perimeter. Zero Trust Architecture incorporates multiple layers of defense, such as multi-factor authentication, micro-segmentation, and strict access controls, to protect data and resources.
Organizations can reduce the risk of insider threats and unauthorized access by adopting a zero-trust model, even when traditional network perimeters have been breached. Zero Trust is a proactive approach that emphasizes ongoing vigilance and monitoring.
14. Security Awareness Training: Empowering Employees
One of the most important techniques in cybersecurity is educating employees about potential threats. Security awareness training equips employees with the knowledge and skills needed to recognize phishing attacks, social engineering, and other common cyber threats.
Since human error is often the weakest link in cybersecurity defenses, training employees helps to reduce the likelihood of security breaches caused by accidental or intentional actions.
15. Network Segmentation: Limiting the Spread of Attacks
Network segmentation is a technique that divides a network into smaller, isolated segments or zones. Each segment operates independently and has its security controls. This isolation limits an attacker’s ability to move laterally across the network once they gain access. Only the compromised segment is affected if a breach occurs, while other segments remain secure.
By implementing network segmentation, organizations can create additional layers of defense. It’s especially useful in protecting critical infrastructure, sensitive data, and high-value assets. Network segmentation works with tools like firewalls and access control mechanisms to enhance overall security.
Cybersecurity Frameworks
- NIST Cybersecurity Framework
The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology (NIST) in the United States, provides a set of guidelines, best practices, and standards for managing and improving cybersecurity risk. It offers a flexible framework that organizations can use to assess, develop, and strengthen their cybersecurity posture. The framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. It serves as a roadmap for organizations to manage cybersecurity risks and enhance their resilience against cyber threats.
- ISO/IEC 27001:2013
ISO/IEC 27001:2013 is an international standard for information security management systems (ISMS). It provides a systematic approach for establishing, implementing, maintaining, and continually improving an organization’s information security practices. The standard focuses on risk management, security controls, and establishing a robust information security governance framework. ISO/IEC 27001:2013 is widely recognized and helps organizations demonstrate their commitment to protecting sensitive information and managing security risks effectively.
- CIS Controls
The Center for Internet Security (CIS) Controls a set of best practices and guidelines to help organizations safeguard their systems and data against cyber threats. The CIS Controls provide a prioritized approach to cybersecurity by outlining specific actions organizations should take to mitigate common attack vectors. The controls are divided into three implementation levels, allowing organizations to adopt them according to their risk profile and available resources. The CIS Controls cover asset management, vulnerability management, secure configurations, access controls, and incident response.
- PCI DSS (Payment Card Industry Data Security Standard)
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security requirements established by major credit card companies to protect cardholder data and ensure secure payment transactions. PCI DSS applies to organizations that handle, store, or transmit payment card data.
It outlines specific security controls and practices organizations must implement to protect cardholder data, including network security, access controls, encryption, and regular security testing. Compliance with PCI DSS is mandatory for organizations involved in payment card processing.
- GDPR (General Data Protection Regulation)
The General Data Protection Regulation (GDPR) is a comprehensive data protection regulation enforced in the European Union (EU) and European Economic Area (EEA). It sets out rules and requirements for the processing, storage, and protection of personal data of EU residents.
GDPR emphasizes principles such as consent, data minimization, transparency, and individual rights regarding their data. Organizations that collect or process the personal data of EU residents must comply with GDPR, implement appropriate technical and organizational measures, and ensure the lawful and secure handling of personal data.
- HIPAA (Health Insurance Portability and Accountability Act)
HIPAA is a U.S. federal law that sets privacy and security standards for protected health information (PHI) held by covered entities such as healthcare providers, health plans, and healthcare clearinghouses. The law requires organizations to implement safeguards to protect PHI’s confidentiality, integrity, and availability.
HIPAA mandates security measures such as risk assessments, access controls, encryption, audit controls, and employee training to ensure the privacy and security of sensitive health information.
- FISMA (Federal Information Security Management Act)
FISMA is a U.S. federal law that establishes requirements for securing federal government information systems. It outlines standards and guidelines for federal agencies to develop and maintain comprehensive information security programs.
FISMA requires federal agencies to implement risk-based approaches to cybersecurity, conduct regular security assessments, develop and maintain system security plans, and establish incident response capabilities. The law ensures federal information and systems’ confidentiality, integrity, and availability.
Safety Tips and Recommendations
Even as cybersecurity measures are constantly being developed by our favourite softwares and applications, internet users must continue to remain vigilant. Here are our recommendations and tips to maintain your personal bubble of cybersecurity:
1. Use a VPN
Public networks, such as those in cafes or in the office, may seem generally secure but they are very prone to attacks by malicious third parties. Always connect to a premium VPN, such as Astrill, to ensure that all of your data remains safe under layers of encryption.
A VPN encrypts your traffic and passes it through a secure tunnel, making you safe and secure over the web. Also, it changes your IP and DNS, so that you can enjoy true privacy by staying anonymous over the web, stay safe from being tracked and have your online privacy intact and secure.
There are certain pros and cons of VPN, but in general, a VPN is the best option you have for protecting your digital privacy and securing your online data. You can install a VPN on any device and secure your information easily.
2. Remain updated with all devices
Make sure all of your devices are kept up-to-date with the latest security patches and updates to its operating software. It is also good practice to update all applications and software as well, to minimize vulnerabilities.
It has been reported that In 2018, one out of every 36 smartphones contained high-risk applications. This number would have definitely increased by now and this means that it can happen to any of us, if we do not take the necessary measures.
3. Don’t click on suspicious links
Most phishing attacks, such as Whale Phishing and URL Phishing, are conducted through direct means of contact, such as emails and messages. It’s best to use antivirus software or to personally check the authenticity of the content being sent to you. It’s always in your best interest not to directly click any random link that you find in your inbox.
4. Create strong, unique passwords
Along with using Two-Factor Authentication, it’s best to make complicated passwords. The strongest passwords contain no references to your personal life, such as your name or your birthday, and are often long with many special characters. Make sure that your password is something that is not only secure but also hard to guess for someone who may know you personally.
Consider using a password manager to store all of your passwords. Some types also come with password generators, which take away all of the work of coming up with a clever password.
Along with all of these tips, it’s best to keep a safety-conscious point of view when surfing online. Cyberattacks are growing more advanced with each day, and when cybersecurity protocols may appear to be lacking, the users themselves can take charge and protect themselves.
Make sure to always be mindful of the content you post, and ensure that you don’t share anything that is personally identifiable on a public platform, or over an unencrypted connection.
5. Secure Your Home Network
Change the default passwords on your router and enable WPA3 encryption for your Wi-Fi network. Use a strong, unique password for your Wi-Fi network and consider setting up a guest network for visitors. Also, disable remote management features on your router if not needed, and ensure that your router’s firmware is regularly updated to protect against known vulnerabilities.
6. Educate Yourself and Your Team
Cybersecurity is not just about technology; it’s about awareness and behavior. Regular training is essential to stay updated on the latest cyber threats, from phishing and social engineering to new malware strains.
Educate employees on recognizing suspicious emails, safeguarding sensitive information, and maintaining secure online practices. Encourage vigilance and report suspicious activities immediately to create a security culture within your organization.
7. Limit Sharing of Personal Information Online
Cybercriminals often use social media to gather information about potential victims, such as their names, addresses, work details, and even their pets’ names (common password choices). Review the privacy settings of your social media accounts and limit who can see your personal information. Avoid oversharing personal details that could be used in security questions or targeted phishing attacks.
Emerging Trends in Cybersecurity
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are increasingly used in cybersecurity to enhance threat detection, analysis, and response capabilities. AI and ML algorithms can quickly analyze vast amounts of data, identify patterns, and detect anomalies indicating cyber attacks or suspicious activities.
These technologies enable proactive threat hunting, automated incident response, and adaptive defense mechanisms. However, it’s important to note that as AI and ML evolve, so do the techniques used by cybercriminals to bypass detection systems, necessitating ongoing research and development to stay ahead.
Internet of Things (IoT) Security
The proliferation of IoT devices, such as smart home devices, industrial sensors, and medical devices, has introduced new security challenges in IoT development, particularly in designing secure and resilient systems. IoT devices often have limited computational resources and lack robust security measures, making them vulnerable to exploitation.
Securing the IoT ecosystem involves addressing device vulnerabilities, implementing strong authentication and encryption, ensuring secure communication protocols, and establishing centralized management and monitoring systems. As IoT expands, the security of connected devices and the protection of sensitive data become critical focus areas.
Cloud Security
With the widespread adoption of cloud computing, ensuring robust cloud security has become imperative. Cloud security encompasses measures to protect data, applications, and infrastructure deployed in cloud environments. It involves implementing strong access controls, encryption, secure data storage and transfer, continuous monitoring, and incident response capabilities.
As organizations increasingly rely on cloud services, the shared responsibility model between cloud service providers and customers must be clearly defined and understood to address potential security risks effectively.
Mobile Device Security
Mobile devices like smartphones and tablets have become integral to personal and professional life. This makes mobile devices attractive targets for cyber attacks. Mobile device security focuses on protecting devices from malware, data breaches, and unauthorized access.
This includes implementing secure device configurations, enabling encryption, enforcing strong authentication, managing app permissions, and educating users about mobile security best practices. Mobile security will remain a significant concern as mobile devices continue to store sensitive data and access critical systems.
Blockchain Technology and Security
Blockchain technology, known for its decentralized and immutable nature, has potential applications in enhancing cybersecurity. It can provide secure and transparent transaction records, identity management, and data integrity verification.
Blockchain-based solutions can help prevent data tampering, enhance supply chain security, and facilitate secure peer-to-peer transactions. However, as blockchain technology evolves, it presents unique security challenges, such as smart contract vulnerabilities and the potential for 51% attacks.
Exploring robust security measures and standards for blockchain implementations is crucial to ensure its effectiveness in enhancing cybersecurity.
Conclusion
Businesses need to improve their cybersecurity structures to avoid being compromised as the cyber-threats and thefts of personal information are on the rise. A comprehensive cybersecurity strategy that addresses coverage of data, systems, network, and information security rules, including social engineering considerations, is essential.
Understanding the threats to which you are most vulnerable as an individual or company is equally crucial. You will be able to concentrate your preventative efforts on the most crucial aspects and better equip yourself if you do this.
FAQs
The 5Cs of cyber security include Change, Cost, Continuity, Compliance and Coverage.
Many people, including governments, organizations, and educational institutes, need cybersecurity to protect their sensitive and confidential data. All of these entities are at risk of cyberattacks.
AI can help enhance and improve cybersecurity practices like threat detection and vulnerability management, but it is not a replacement for cybersecurity. AI can present some errors, so human intervention is always needed.
In the next five to ten years, preventative measures will be needed to combat cyber threats. With technology advancing rapidly, there will be more cyber threats than ever, and cybersecurity practices will be required to combat these threats.
Coding skills are not a requirement for entry-level cybersecurity jobs. However, if you want to keep progressing and advance to a senior-level role, you will need some coding skills.
Deep Packet Inspection (DPI) is a sophisticated method used in cybersecurity to analyze the data being transmitted over a network. Unlike basic packet filtering, which only looks at the header information of packets, DPI examines the entire content of the data packets, including the payload

No comments were posted yet