What is Keystroke Logging? How It Works, Detection Solutions

Bisma Farrukh

Ever get the feeling you’re being watched while typing away on your computer? Unfortunately, it could be more than just paranoia. Keystroke logging, also known as keylogging, is a sneaky way for others to spy on what you’re typing by recording your keystrokes. As you go about answering emails, shopping online, and chatting with friends, a keylogger can capture your every letter and number, seeing everything from passwords to credit card numbers to personal messages.
The scariest part is that you may not know it’s even installed on your device. But don’t panic just yet – there are a few ways you can outsmart these digital spies and protect your privacy. We’ll tell you exactly about the keylogging definition, what is a keystroke logger or what is keystroke monitoring, how to spot the signs you may be compromised, and the steps you can take to better defend yourself against these covert monitoring attacks.
Table of Contents
What Is Keystroke Logging and How Does It Work?
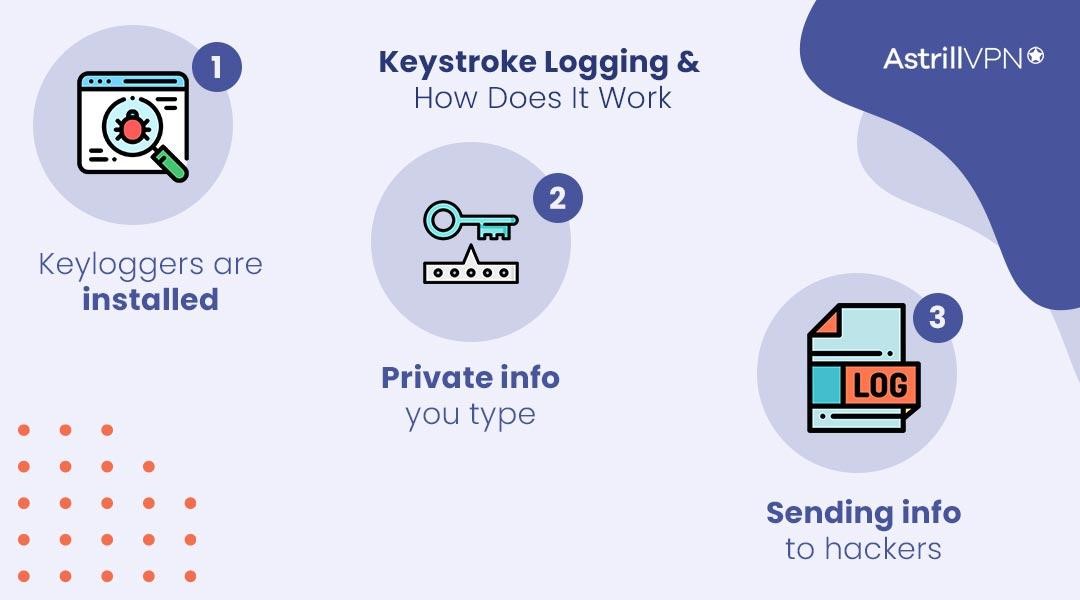
Keystroke logging, also known as keylogging or keystroke monitoring, is when someone secretly records the keys you press on your keyboard. Keyloggers capture your keystrokes and send that sensitive data to hackers.
How it works:
Keyloggers are installed on your computer, usually through malware, to track the keys you press. The keylogger records your keystrokes in the background and sends that info to hackers.
What they capture:
Keyloggers log your usernames, passwords, credit card numbers, and other private info you type. They capture everything from your emails and messages to your online banking passwords.
How to detect them:
Look for unknown programs running in the background on your computer. Run an up-to-date antivirus scan to check for malware. Be alert for signs like lagging keyboards, unfamiliar USB drives, or random keyboard clicks. If detected, remove the keylogger immediately and change all your passwords.
Staying vigilant and practicing good online security habits are the best ways to avoid becoming a victim of keylogging. Be cautious of unsolicited messages and downloads, use strong and unique passwords, and keep your antivirus software up to date. Keyloggers are a serious threat, so be on guard and immediately act if you suspect malicious activity on your computer. Knowledge is power, so learn the signs and outsmart the hackers.
Why Is KeyLogging attack Harmful and Unethical?
Keylogging attack is harmful and unethical for several reasons:
- It violates your privacy. Everything you type on your keyboard, including passwords, credit card numbers, and personal messages, is recorded without your consent. This sensitive data can then be accessed by anyone with access to the keylogger.
- It enables identity theft and fraud. Once cybercriminals have your passwords, social security number, and other personal information, they can steal your identity, open credit cards in your name, and gain access to your online accounts.
- It allows stalking and harassment. Unfortunately, keyloggers are sometimes used by jealous spouses, exes, or stalkers to monitor what you do online and see private messages. This can enable stalking, harassment, and even physical harm.
- Your information may be sold. The data keyloggers collect is valuable and often sold to other cybercriminals on the dark web. Your personal information could end up in the hands of anyone willing to pay for it.
- It undermines security. Keyloggers record everything you enter, including passwords to your email, bank, and work accounts. This compromises the security of those systems and allows unauthorized access.
Common Signs Your Device Has Been Compromised by a Keystroke Logger
Unusual System Behavior

If your computer is acting strangely, it could indicate a keylogger infection. Things like programs opening or closing themselves, the mouse moving on its own, or the keyboard typing when you’re not using it are major red flags. The keylogger may run in the background, recording your keystrokes and manipulating your system.
Antivirus Alerts

Most antivirus software scans for known keyloggers and will alert you if one is detected. Pay close attention to any warnings from your antivirus about suspicious programs running on your system. Quarantine or delete anything it flags as potentially unwanted software.
Unusual Hard Drive Activity
Keyloggers frequently access your hard drive to store the information they log, which can lead to noticeable hard drive activity when the keylogger is running. Listen for loud or excessive hard drive sounds like constant whirring or clicking. This could be a sign your keylogger is actively logging your keystrokes and accessing your storage.
Wi-Fi and Bluetooth Connections

Some keyloggers use your Wi-Fi or Bluetooth connectivity to transmit the data they capture to a remote location. Look for any unknown or unlabeled Wi-Fi or Bluetooth connections on your devices, especially any actively connected. These rogue connections could be how your keylogger is sending your information to hackers and cybercriminals.
Staying vigilant and monitoring for these common signs of keylogger viruses is one of the best ways to detect if you’ve been compromised. If anything seems off with your technology, it’s best to take action immediately.
How to Detect if Keystroke Software Is Installed on Your Computer?
Check for Unknown Processes Running
Open your computer’s Task Manager (Ctrl+Alt+Del) and look for any unfamiliar processes running. Keystroke logging malware will often run as a background process to avoid detection. If you see a process, you don’t recognize, research to determine if it’s legitimate or malware. Some common keylogging process names include:
- Keylogger
- KeyStroke
- iSpy
- Spyware
Inspect Browser Extensions
Keystroke logging software is sometimes installed as a browser extension. Open your browser’s extension manager and review the list of installed extensions. Remove any extensions you did not install yourself. Keyloggers are often given innocent-sounding names to avoid raising suspicion, so if anything looks out of the ordinary, it’s best to disable it.
Scan for Malware
Run a full system scan using reputable anti-malware software like Malwarebytes or McAfee. These programs will scan your computer for keylogging malware and other viruses. If malware is detected, follow the prompts to remove it. You may need to reboot your computer to fully eliminate the infection.
Be on Alert for Warning Signs
Watch out for common signs of keylogging like unknown processes running, typing lag, keyboard keys acting strangely, loss of keyboard or mouse control, or your online accounts being accessed without your knowledge. If you notice anything suspicious, run a malware scan immediately and change all account passwords as a precaution. Staying vigilant is key to detecting keylogging and other malware.
How to Protect Yourself Against Keystroke Logging?
Use an Antivirus Program
An antivirus program can help detect keylogging malware on your computer. Ensure you have a reputable antivirus installed and keep it up to date with the latest virus definitions. Antivirus software scans for known keyloggers and other malware, so updating frequently is important. Run regular system scans with your antivirus to check for any keylogging infections.
Be Cautious of Public Wi-Fi Networks
Public Wi-Fi networks are a prime target for keyloggers and hackers. Never enter sensitive information like passwords, credit card numbers, or social security numbers on public Wi-Fi. If you must use public Wi-Fi, use a VPN to encrypt your internet connection and help prevent keylogging.
Use a Password Manager
A password manager generates and stores complex, unique passwords for all your accounts so you don’t have to remember them. This makes it much harder for keyloggers to capture your passwords. Popular password managers like LastPass, Dashlane, and 1Password can generate secure passwords and store them in an encrypted vault. Use a password manager on all your devices for the best protection.
Be Vigilant For Warning Signs
Watch out for signs that a keylogger may be installed on your computer, like lagging performance, random reboots or freezes, and unfamiliar programs running in the background. If you notice any suspicious activity, run a virus scan immediately. It’s also a good idea to do regular maintenance like disk cleanup and defragmentation to keep your computer running efficiently so you can more easily detect if there are any issues. Staying vigilant and acting quickly if you suspect a keylogger is the best way to limit the damage.
Be Careful What You Download
Only download software from trusted sources. Keyloggers are often hidden in free downloads, torrents, and other places.
Use Two-Factor Authentication When Possible
Two-factor authentication, like text message codes or biometric scans, adds an extra layer of security for online accounts. Even if a keylogger steals your password, they would need the second authentication factor to log in.
Watch Out for Phishing Emails
Be wary of unsolicited messages and links, especially those asking for personal information or account access. Phishing emails are a common way for keyloggers and malware to infect computers.
Use an On-Screen Keyboard
An on-screen keyboard allows you to click letters with your mouse instead of typing on the physical keyboard. Since keyloggers track physical keystrokes, an on-screen keyboard can foil many basic keylogging programs.
Be vigilant and trust your instincts.
If something feels off about your computer’s behavior, it’s best to be safe. Run an antivirus scan and consider consulting an IT professional. An ounce of prevention is worth a pound of cure when it comes to keylogging.
How AstrillVPN can prevent keystroke logging?
AstrillVPN encrypts all of your internet traffic and hides your online activities. Here are a few ways AstrillVPN helps:
- Keep no logs:
With AstrillVPN enabled, no logs are kept of user activity. It also provides protection from online tracking.
- Hides your online destinations:
AstrillVPN masks the websites you visit by hiding your real IP address and encrypting your traffic. It also provides threat protection.
Is a keylogger a virus?
Keyloggers aren’t technically viruses, but they are often considered malware. A keylogger is a type of software or hardware that secretly records the keys struck on a keyboard, typically in order to gain sensitive information such as passwords, credit card numbers, or other secret information. Most keyloggers work by installing themselves secretly on a device, though some can also be installed physically.
While not technically a virus, since keyloggers don’t self-replicate and spread like a virus does, they are often grouped together with malware due to their nefarious purposes. Most keyloggers are installed without the owner’s knowledge or consent and are used for illicit purposes like identity theft or fraud. Once installed, a keylogger can record everything a user types, including usernames, passwords, credit card numbers, messages, and other sensitive data.
Many keyloggers are installed through social engineering tricks, where a user is tricked into installing the software themselves. However, some keyloggers may also arrive through email attachments, malicious websites, or software vulnerabilities. Once installed, a keylogger can be very difficult for the average user to detect due to how secretly they operate. Specialized anti-keylogger software and hardware may be required to remove keyloggers once installed.
Do mobile devices get keyloggers?
Mobile devices like smartphones and tablets can certainly get keyloggers installed on them. Keyloggers are pieces of software that record every keystroke a user types into their device. This can include passwords, credit card numbers, messages, and other sensitive information.
Keyloggers can be installed on mobile devices in several ways:
1. Malicious apps
Some apps that claim to offer useful features may actually contain keylogger software. The app may ask for unnecessary permissions to access device functions in order to secretly install the keylogger.
2. Hacking
Hackers can gain remote access to a device and install keyloggers without the user’s knowledge. This often happens when public WiFi networks are used or insecure apps are installed.
3. Pre-installed
In rare cases, keyloggers may already be installed on a device when purchased from some shady sellers. The keylogger would activate once the device is set up.
Once installed, a keylogger on a mobile device can function similarly to a keylogger on a computer. The keylogger software silently runs in the background, recording everything typed and transmitting that data to the attacker. The user typically has no indication a keylogger is active.
To protect mobile devices from keyloggers, users should only install apps from official app stores, avoid insecure public WiFi, use strong passwords, and keep the device’s software up-to-date with the latest security patches. In some cases, a full factory reset may be the only way to remove an already installed keylogger.
Types of Keyloggers
There are various types of keyloggers, each with their own strengths and weaknesses. Here are some of the main categories:
Hardware keyloggers:
These are physical devices that connect directly to a computer’s keyboard or USB port. They can be difficult to detect since they do not install any software. However, they require physical access to install.
Software keyloggers:
These install as programs on a target computer. Some come pre-installed as malware, while others can be installed remotely. They are easier to install but can sometimes be detected by antivirus software.
Browser keyloggers:
These install within web browsers like Chrome, Firefox or Internet Explorer. They monitor and record all keystrokes within the browser. They are effective for monitoring internet activity but won’t catch activity in other programs.
Cloud keyloggers:
These store all logged keystrokes in the cloud, allowing access from any device. They are often used by parents to monitor children’s internet activity. Cloud storage also makes the data difficult for the target to find and delete.
Keylogging malware:
Many malware strains come with built-in keylogging capabilities. Once installed, they can record everything typed and transmit the data to the attacker. They are stealthy but also easy for antivirus to detect and remove.
In general, the most effective keyloggers combine stealth, remote access and the ability to capture all keystrokes across a target’s device. With so many options, it’s important to consider your specific monitoring needs and the level of detectability you want before choosing a keylogger.
What is keystroke tracking?
Keystroke tracking is the practice of tracking the keys pressed on a keyboard, usually without the user’s knowledge. Keyloggers are hardware or software tools that capture your keystrokes and record them for later retrieval.
Cybercriminals use keylogging to steal passwords, credit card numbers, social security numbers, and other sensitive data. Keyloggers can be installed physically or remotely (as malware). They capture your keystrokes in the background and send the information to the attacker.
What is Keystroke Spyware?
Keystroke spyware, a type of keylogger, is malicious software installed on a computer to secretly monitor keystrokes and steal sensitive data like passwords, credit card numbers, and more. It records each key pressed on the keyboard, takes screenshots, and sends the information to hackers. Keystroke spyware is often distributed through phishing emails, malicious websites, and software downloads.
Once installed, keystroke spyware runs in the background without your knowledge. A serious privacy threat can put your accounts and identity at risk. The only way to fully remove keystroke spyware is to wipe your computer and reinstall the operating system. As cyber threats become more advanced, keystroke spyware will likely become stealthier and harder to detect. Staying vigilant about online security is the best way to minimize your risk.
Conclusion
So there you have it. Keystroke logging is a real threat that you need to be aware of if you want to protect your privacy and security. But don’t panic – with some vigilance and the right tools. You can detect keylogging and stop it in its tracks. And if you do find evidence of keylogging, take action immediately to remove the threat and change all your passwords. Staying safe online requires effort, but with knowledge and the right precautions, you can browse easily, knowing you’ve outsmarted the keyloggers.
FAQs About Keystroke Logging
Keyloggers monitor keyboard input and store the information for the person operating the keylogger to access. Software keyloggers are installed on your computer to capture keystrokes. Hardware keyloggers are physical devices that plug in between your keyboard and computer to record keystrokes. The captured data is then sent to the attacker.
There are a few ways to detect potential keyloggers on your system:
Look for unknown processes or services running in the background. Keyloggers often run as hidden processes. Inspect browser extensions, plugins, or toolbars you don’t recognize. Some keyloggers install as browser add-ons. Check for unfamiliar files on your system, especially in temporary folders. Keyloggers often store captured data in temp files.
The best way to protect against keyloggers is through vigilance and proactive defense. Use a reputable antivirus or anti-malware program and keep it up to date. Be cautious of unsolicited links, attachments, and downloads. Use strong, unique passwords for accounts and enable two-factor authentication when available.

No comments were posted yet