Zero Day Attack Explained: How Hackers Exploit the Unknown

Arsalan Rathore

Zero day attacks are among the most critical threats in cybersecurity. These attacks occur when malicious actors exploit a software vulnerability unknown to the vendor or security community. Because no patch or fix is available during the exploit, the vulnerability is called a “zero-day,” indicating that developers have had zero days to address the flaw.
What makes zero day attack especially dangerous is their unpredictability and potential for widespread impact. Since traditional security tools rely heavily on known signatures and threat intelligence, zero day exploits often bypass detection entirely. Attackers can leverage these vulnerabilities to gain unauthorized access, execute arbitrary code, or exfiltrate sensitive data all without triggering alarms.
According to Google’s Threat Intelligence Group, 75 zero day vulnerabilities were actively exploited in the wild in 2024, a rise from 63 in 2022 and a slight decrease from 98 in 2023.
These exploits are typically used in targeted operations by advanced persistent threat (APT) groups, cybercriminal syndicates, and even nation-state actors. Zero day vulnerabilities are often traded on underground markets, fetching high prices due to their offensive capabilities and stealth.
Understanding how zero day vulnerabilities work, how they are exploited, and how to mitigate the associated risks is essential for individuals and organizations aiming to maintain a robust security posture in a constantly evolving threat environment. In this guide, we have explained everything related to zero-day attacks and how you can prevent them.
Table of Contents
What Is a Zero Day Vulnerability?
A zero-day vulnerability is a security flaw in software or hardware that is unknown to the vendor or developer when discovered and potentially exploited. The term “zero-day” refers to developers having zero days to fix the issue before attackers can actively exploit it.
These vulnerabilities often arise from coding errors, design oversights, or misconfigurations. Because they are not yet publicly known or documented, there are no available patches, updates, or defensive mechanisms to protect against them when they are discovered. This makes zero day vulnerabilities especially dangerous, offering attackers a temporary but decisive advantage.
What Is a Zero Day Exploit?
A zero day exploit is a specific method or code designed to exploit a zero-day vulnerability. While a zero day vulnerability refers to the security flaw itself, the exploit is the weapon that turns the flaw into a functioning tool for attack.
In simple terms, the vulnerability is the unlocked door; the exploit is the method used to walk through it, silently and without resistance.
How Zero Day Exploits Work
Zero day exploits are developed to manipulate a flaw in a system, software, firmware, or hardware component that has not yet been patched or made public. These exploits often allow attackers to:
- Execute unauthorized commands or code
- Escalate privileges within a system
- Install malware or spyware
- Bypass authentication mechanisms
- Exfiltrate sensitive data
Zero Day Exploit vs. Zero Day Attack
In simpler terms, the exploit is the tool; the attack is the act. The terms zero day exploit and zero day attack are closely related but serve different roles in the broader context of cybersecurity threats. Understanding the distinction between the two is essential for analyzing how attackers operate and how defenders should respond.
- A zero-day exploit refers to the technical mechanism i.e. a script, sequence of commands, or piece of malware, crafted to take advantage of a previously unknown vulnerability.
- A zero-day attack is the actual use of that exploit in the wild to compromise a system, application, or network.
How They Work Together
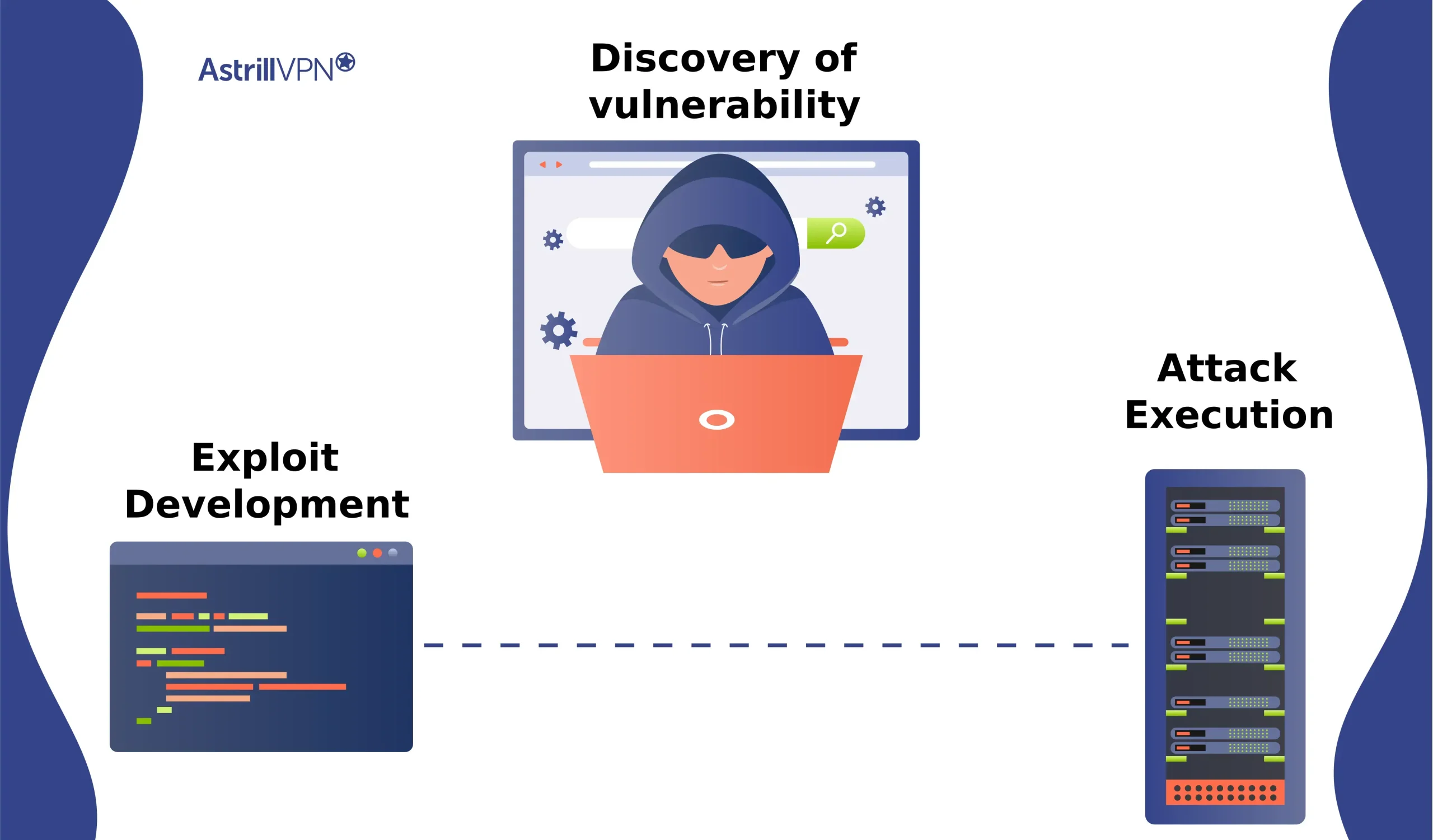
A zero day attack typically unfolds in the following sequence:
- Discovery of a zero day vulnerability (flaw unknown to the vendor).
- Development of a zero day exploit targeting that flaw.
- Execution of the zero day attack using the exploit often before the vendor or the public is aware of the issue.
Why Zero Day Attacks Are So Dangerous
- Bypass traditional defenses: Antivirus, firewalls, and EDR solutions often fail to detect new exploits without signatures or prior threat intelligence.
- Highly targeted: Zero-day attacks are frequently used in espionage, state-sponsored operations, and financially motivated campaigns, focusing on high-value targets.
- Silent and long-lasting: In many cases, attackers maintain persistence on compromised systems for weeks or months before detection.
The Role of Threat Actors
Zero day threats are not commonly used by low-level hackers. Developing or acquiring a working exploit for an unknown vulnerability requires advanced technical skills, significant resources, or access to black-market vendors. As a result, these tools are often found in the arsenals of:
- Nation-state groups
- Advanced Persistent Threat (APT) actors
- Cybercriminal organizations with well-funded operations
Real-World Impact
Zero day attacks have been behind some of the most serious cyber incidents in history. For example:
- The Stuxnet worm used multiple zero-day exploits to target Iranian nuclear facilities.
- The 2023 MOVEit Transfer breach exploited a zero-day flaw to exfiltrate data from hundreds of organizations globally.
- Several mobile spyware platforms, such as Pegasus, have relied on zero-day exploits to silently compromise smartphones.
How Zero Day Vulnerabilities Are Discovered
Zero-day vulnerabilities are among the most elusive flaws in the cybersecurity landscape. By definition, they are unknown to the vendor and security community at the time of discovery. This makes their detection both rare and highly valuable, whether discovered by ethical researchers or malicious threat actors.
Understanding how these vulnerabilities are uncovered offers insight into the dynamics of modern cybersecurity and the constant race between attackers and defenders.
1. Independent Security Research
Many zero-day vulnerabilities are found by professional security researchers or ethical hackers through:
- Reverse engineering: Deconstructing software binaries to identify undocumented flaws or unsafe code execution paths.
- Fuzzing: A method of automatically inputting random or malformed data into a program to uncover unexpected behavior or crashes that could indicate a vulnerability.
- Code audits: Manual or automated examination of source code (when available) to identify logic errors, buffer overflows, or improper input handling.
2. Internal Discovery by Developers or QA Teams
In some cases, vendors themselves identify security issues during routine software testing, quality assurance (QA), or product hardening. While these aren’t “zero-day” flaws in the traditional sense, since they’re discovered internally, they can be critical and would have otherwise remained undiscovered in production environments.
3. Malicious Discovery by Threat Actors
Cybercriminals and state-sponsored hacking groups also actively search for zero-day vulnerabilities, often using the same techniques as researchers but with different intent:
- Black-box testing: Interacting with software without access to source code to trigger unexpected behavior.
- Network sniffing and protocol analysis: Observing traffic patterns to identify weak points or unprotected interfaces.
- Insider access: Leveraging internal knowledge or unauthorized access to uncover hidden flaws in enterprise systems or proprietary software.
4. Bug Bounty Platforms and Security Communities
Organizations like Google, Microsoft, and Apple run bug bounty programs, where vetted researchers are rewarded for responsibly disclosing vulnerabilities. These platforms serve as a constructive outlet for talent that could otherwise be leveraged in underground exploit markets.
Additionally, organizations like MITRE and the Zero Day Initiative (ZDI) contribute to responsible vulnerability coordination and publish known vulnerabilities once patches are available.
5. Zero-Day Brokers and Exploit Marketplaces
Some zero day vulnerabilities are discovered and traded by exploit brokers, entities that purchase vulnerabilities and sell them to governments, law enforcement agencies, or other clients. These brokers operate in a legal gray area and typically do not disclose the vulnerabilities to vendors, increasing the risk of prolonged, undetected exploitation.
Life Cycle of a Zero Day Attack
The life cycle of a zero day attack illustrates how a vulnerability transitions from an unknown flaw to an active threat capable of breaching systems. This process involves multiple stages, from discovery, weaponization, exploitation, and eventual remediation. Understanding this cycle is essential for identifying where defensive strategies can be most effective.
1. Discovery of the Vulnerability
The life cycle begins when software, hardware, or firmware identifies a previously unknown vulnerability. This discovery can happen through:
- Independent research
- Malicious reconnaissance
- Insider access
- Reverse engineering
2. Development of a Zero Day Exploit
Once the vulnerability is confirmed, attackers, or in some cases, researchers, begin developing an exploit to leverage the flaw. This often involves:
- Crafting custom code that triggers the vulnerability
- Testing the exploit against target systems
- Packaging it into a payload (e.g., malware, scripts, phishing kits)
3. Weaponization and Packaging
The exploit is now weaponized for delivery. Attackers may embed it in:
- Malicious email attachments (e.g., Office docs or PDFs)
- Compromised websites (drive-by downloads)
- Fake software updates
- Messaging platforms or even USB drives
4. Deployment and Execution
The exploit is deployed, and the attack is executed. This is the moment the zero-day attack becomes active. Depending on the goal, attackers may:
- Gain remote access
- Escalate privileges
- Install spyware or ransomware
- Exfiltrate sensitive data
5. Persistence and Lateral Movement
Advanced attackers may use the zero day exploit to gain a foothold and expand their reach:
- Establishing persistence on the network
- Moving laterally between systems
- Avoiding detection through stealth tactics
6. Detection and Disclosure
Eventually, signs of the exploit may be uncovered through incident response, behavioral anomaly detection, or third-party research. Once detected, the vulnerability is:
- Reported to the vendor
- Assigned a CVE (Common Vulnerabilities and Exposures) ID
- Publicly disclosed, often alongside proof-of-concept code
7. Patch Development and Remediation
The vendor works to develop and distribute a patch to fix the flaw. This process may vary in speed depending on the software’s complexity and the exploit’s severity. Once patched:
- Users must apply the fix to be protected
- Security tools update their signatures.
- Threat actors shift focus to unpatched systems.
8. Post-Attack Phase
Even after a patch is released, unpatched systems remain vulnerable, turning the zero-day into an n-day exploit. It is still dangerous but now detectable. Attackers often scan for systems that are late to patch, continuing to exploit the vulnerability for weeks or months.
Assessing Zero Day Threats
Zero day threats represent one of the most severe and unpredictable challenges in cybersecurity. Because they exploit previously unknown vulnerabilities, zero-day threats bypass conventional defenses and operate silently until discovered, often only after damage has been done. Assessing their risk accurately requires understanding their intent, scope, and the actors who use them.
1. Understanding the Nature of the Threat
A zero day threat encompasses the unknown vulnerability and the potential exploit that leverages it. What makes this type of threat so dangerous is the complete lack of prior knowledge, no detection signatures, patches, or historical indicators of compromise (IOCs) to rely on. This element of surprise leaves a critical blind spot in security infrastructures.
Zero day threats:
- Often remain active in the wild for extended periods before discovery.
- Can bypass endpoint protection, intrusion detection systems (IDS), and firewalls.
- They are typically part of highly targeted campaigns but can also be used in mass attacks.
2. Threat Actor Profiles
The value and rarity of zero-day exploits mean they are primarily used by:
- Nation-state actors: For espionage, sabotage, or geopolitical advantage.
- Advanced Persistent Threat (APT) groups: For long-term infiltration of high-value networks.
- Cybercriminal organizations: To steal financial data, deploy ransomware, or compromise business systems.
- Hack-for-hire groups: Engaged in corporate espionage or targeted surveillance.
3. Targets of Zero Day Threats
Zero-day threats are not limited to any single sector. Common targets include:
- Operating systems: Windows, Linux, macOS, Android, and iOS.
- Web browsers and plugins: Chrome, Firefox, Safari, Adobe Flash (historically).
- Enterprise software: Email servers, content management systems (CMS), VPNs, file transfer platforms.
- IoT and embedded systems: Smart devices and routers often lack robust patching mechanisms, making them ideal long-term targets.
4. Intent Behind Zero-Day Attacks
Not all zero-day threats are created equal. The attacker’s intent plays a significant role in determining the level of risk:
- Espionage: Silent exfiltration of sensitive data without system disruption.
- Disruption: Causing downtime or chaos (e.g., Stuxnet).
- Financial gain: Ransomware delivery, fraud, or theft.
- Surveillance: Gaining persistent access to monitor users or organizations covertly.
5. Risk Factors to Consider
When assessing the threat level posed by a zero-day, organizations should evaluate:
- Attack surface: How exposed are your systems to potentially vulnerable software?
- Patching culture: Do you have processes in place for fast remediation once vulnerabilities are disclosed?
- Visibility and detection: Can your security tools detect abnormal behavior even without known signatures?
- Incident response readiness: Do you have a plan for containing and investigating zero-day incidents?
Zero Day Attack Prevention & Defense
Preventing and defending against zero-day attacks requires a proactive, multi-layered security strategy. Since these threats exploit unknown vulnerabilities, traditional defenses like signature-based antivirus solutions are often ineffective. Instead, organizations and individuals must focus on reducing their attack surface, improving threat visibility, and adopting tools that enhance privacy and resilience, such as a reliable VPN.
1. Patch Management & Software Hygiene
While zero-day vulnerabilities are, by definition, unpatched at the time of discovery, attackers often continue to exploit them long after fixes are released. That’s why it’s critical to:
- Apply security updates promptly across all operating systems, applications, and network devices.
- Remove unsupported or legacy software, which is less likely to receive security patches.
- Limit third-party software and browser plugins that expand the potential attack surface..
2. Use of a Trusted VPN
A trusted VPN, like AstrillVPN, adds a valuable layer of defense, especially when you’re on unsecured or public networks. While a VPN cannot prevent a zero day exploit within your operating system or browser, it can:
- Encrypt all internet traffic, making it unreadable to attackers monitoring insecure networks.
- Mask your IP address, reducing your exposure to reconnaissance efforts often preceding targeted attacks.
- Prevent man-in-the-middle attacks, which are commonly used to deliver exploits over compromised networks.
3. Behavior-Based Threat Detection
Zero-day attacks often bypass static defenses, but they still generate unusual behavior. Implement:
- Endpoint Detection and Response (EDR) tools that monitor for suspicious activity, like privilege escalation or code injection.
- Anomaly-based intrusion detection systems (IDS) that analyze network traffic for outliers.
- Security Information and Event Management (SIEM) platforms that correlate logs for early warning signals.
4. Least Privilege Access & Network Segmentation
Restricting access within your system or organization minimizes the impact of a successful attack:
- Apply least privilege policies, ensuring users and applications access what they truly need.
- Use network segmentation to isolate sensitive systems, preventing lateral movement in case of a breach.
- Implement multi-factor authentication (MFA) to reduce the risk of compromised credentials being used with an exploit.
5. Zero Trust Architecture
Adopting a Zero Trust model—“never trust, always verify”, can significantly reduce exposure:
- Authenticate and validate every request, regardless of whether it originates inside or outside the network.
- Continuously monitor device health, user behavior, and access patterns.
- Limit implicit trust in internal networks, where zero-day exploits may spread unnoticed.
6. User Awareness & Threat Intelligence
Human error remains a primary vector for zero-day delivery. To mitigate risk:
- Train users to recognize phishing and social engineering tactics often used to deliver exploits.
- Subscribe to real-time threat intelligence feeds that provide early warnings of emerging zero-day campaigns and tactics.
- Monitor vendor advisories and vulnerability databases to stay ahead of potential risks.
Tools & Strategies for Zero-Day Attack Prevention
Since zero-day attacks exploit unknown and unpatched vulnerabilities, prevention depends on anticipating and mitigating threats before they materialize. This requires a blend of advanced security tools, intelligent infrastructure, and proactive risk management. While no tool can guarantee complete protection from zero-day threats, the following strategies significantly reduce the likelihood and impact of an attack.
1. Vulnerability Scanning & Attack Surface Management
Even though zero-day vulnerabilities are unknown, organizations must minimize overall risk by reducing their attack surface:
- Continuous vulnerability scanning helps detect misconfigurations, outdated components, and weaknesses that could be combined with unknown exploits.
- Attack surface management (ASM) tools offer visibility into exposed services, ports, and devices, which is especially critical for cloud-native and hybrid environments.
- Shadow IT discovery ensures unauthorized apps or systems aren’t silently introducing risk.
2. Threat Intelligence Platforms
Threat intelligence is essential for identifying zero-day exploit trends and attacker tactics before they reach your environment:
- Monitor dark web forums, exploit marketplaces, and APT campaigns for signs of emerging zero-day threats.
- Integrate threat intelligence feeds with your SIEM or EDR systems for automated alerts.
- Use Indicators of Attack (IOAs) rather than static Indicators of Compromise (IOCs), which may not exist for zero-day exploits.
3. Endpoint Detection & Response (EDR)
Because zero-day attacks often bypass perimeter defenses, EDR solutions are critical for real-time detection and remediation at the endpoint level:
- Monitor system behavior for anomalies like suspicious file execution, memory injection, or privilege escalation.
- Provide forensic data to understand attack vectors and limit the spread.
- Enable rapid isolation of compromised devices from the rest of the network.
4. Application Whitelisting & Sandboxing
- Application whitelisting ensures that only approved software can execute, reducing the chances of a malicious payload running successfully.
- Sandboxing allows organizations to test attachments, links, and executables in isolated environments to observe behavior without risking the host system.
5. Security Patch Automation
Once a zero-day becomes a known vulnerability, speed is everything:
- Implement automated patch management solutions to deploy critical fixes as soon as they are released.
- Prioritize patching of systems with public exposure (e.g., VPNs, web servers, remote access portals).
- Use tools that assess patch coverage and vulnerability risk scoring across your infrastructure.
6. Network Segmentation & Microsegmentation
Containing a zero-day exploit becomes easier with a controlled network architecture:
- Segment critical assets (e.g., financial systems, databases) from general user networks.
- Use microsegmentation in data centers and cloud environments to enforce granular policies down to the workload level.
- Limit east-west traffic, preventing lateral movement once a system is compromised.
7. Zero Trust Architecture
Implementing a Zero Trust model shifts the security paradigm from perimeter-focused to identity- and context-based access control:
- Continuously verify users, devices, and applications.
- Implement least-privilege access, and revoke permissions dynamically when risk is detected.
- Use identity federation, device health checks, and context-aware access rules to prevent exploitation even if a system is compromised.
8. Backup, Isolation, and Recovery
When all else fails, rapid recovery becomes the last line of defense:
- Maintain frequent, versioned backups of critical systems and data, stored on-prem and in secure cloud environments.
- Ensure backups are isolated from the primary network to prevent compromise.
- Test disaster recovery plans regularly to minimize downtime after an incident.
9. Leverage Privacy Tools Like VPNs
VPNs play an indirect but essential role in defending against zero-day delivery vectors:
- A secure VPN like AstrillVPN encrypts all internet traffic, protecting against network-based attacks such as man-in-the-middle (MitM) that can deliver zero-day payloads.
- VPNs also reduce digital exposure by masking IP addresses and location data, making it harder for attackers to perform reconnaissance or target high-value endpoints.
Examples of Zero‑Day Attacks
1. Apple Core Media Framework (iOS/macOS, January 2025)
CVE‑2025‑24085 was a zero-day privilege escalation flaw in Apple’s Core Media framework. Exploited in the wild, it affected iPhones, Macs, Apple TVs, and more via malicious media files. Apple issued patches in early 2025.
2. Google Chrome Exploits (CVE‑2025‑2783, CVE‑2025‑5419, CVE‑2025‑6554)
Throughout 2025, Google patched multiple Chrome zero-day vulnerabilities used in active espionage campaigns.
- CVE‑2025‑2783, for instance, was exploited in Operation ForumTroll, a cyber-espionage campaign targeting Russian educational and media institutions. The attackers sent phishing emails containing specially crafted links that triggered remote code execution in Chrome’s rendering engine.
- These exploits bypassed Chrome’s sandboxing and site isolation features, enabling attackers to install backdoors and steal credentials.
- Google’s emergency updates in March and April 2025 addressed these flaws, but security experts warned that attackers were exploiting them within days of discovery, indicating a highly organized operation with access to internal browser mechanics.
3. Zip Utility Exploit (CVE‑2025‑0411)
In February 2025, a zero day vulnerability in the open-source 7-Zip file compression utility was exploited in espionage operations against Ukrainian targets.
- Russian-linked actors embedded malicious payloads into archive files that, when opened with 7-Zip, triggered a flaw enabling remote code execution.
- Victims unknowingly installed SmokeLoader malware, a known info-stealer and downloader used to exfiltrate sensitive documents and monitor communications.
- The vulnerability was believed to have been exploited as early as late 2024, with a coordinated patching effort completed by March 2025 after coordinated disclosure from CERT-UA.
4. U.S. Telecom Infrastructure Hack via Versa Director & Cisco Gear (2024)
A major breach in mid-2024 saw China-linked threat actors exploit zero-days in Versa Networks’ Director software, Fortinet firewalls, and Cisco routers.
- The attack targeted U.S. telecom infrastructure, especially AT&T, where over 100,000 routers were silently compromised.
- The attackers gained remote shell access to core network devices, enabling deep packet inspection and covert data exfiltration.
- This sophisticated attack went undetected for nearly a year, and experts noted that the attackers used multiple zero-days chained with misconfigurations to retain access.
5. Kaseya VSA Supply Chain Ransomware (REvil, July 2021)
In mid‑2021, the REvil group exploited a previously unknown vulnerability in Kaseya’s VSA remote management software, gaining executive control over Kaseya client environments. The exploit enabled propagation of ransomware across managed service provider (MSP) ecosystems, affecting over 1,000 downstream organizations and causing massive disruption.
6. Zoom Remote Code Execution (Early 2020)
As remote work surged, Zoom suffered a zero‑day flaw permitting arbitrary remote code execution on Windows systems, mainly when high-privilege users engaged with outdated client versions. Attackers achieved full system access covertly, prompting Zoom to implement emergency patches and accelerate bug bounty expansion.
FAQs
Zero-day attacks exploit unknown and unpatched vulnerabilities, making them stealthier and harder to detect. Unlike traditional cyber attacks that target known flaws with existing defenses, zero-day strike before any fix or signature is available.
They’re dangerous because they exploit unknown weaknesses, often allowing attackers to bypass all security layers undetected. With no available patch or prior warning, defenders have little to no time to react, making these attacks highly effective and damaging.
It can take anywhere from a few days to several weeks, depending on the complexity of the vulnerability, the vendor’s response time, and potential risks associated with the fix. In some cases, interim mitigations are deployed before a full patch is released.
Attackers often uncover zero-days through reverse engineering, fuzzing (automated testing), code auditing, or by purchasing them from exploit brokers or the dark web. Advanced threat actors may also invest heavily in R&D to identify them independently.
Demand has surged due to their high value in cyber espionage, ransomware campaigns, and nation-state operations. As security technologies improve, finding exploitable flaws becomes harder, driving up both the cost and market competition for zero-day exploits.


No comments were posted yet