What Is a Watering Hole Attack? Signs & Prevention Guide

Arsalan Rathore
A watering hole attack is a cyberattack strategy in which the attacker targets a specific group of individuals by compromising a website or online service that they are known to frequent. The name “watering hole” is derived from the concept in nature, where predators wait at watering holes to catch their prey. Similarly, in a watering hole attack, the attacker identifies the websites or platforms commonly visited by a particular group such as employees of a company, members of a specific organization, or users with a shared interest and infects those sites with malicious code. When the intended victims visit the compromised site, their devices become infected with malware or are exploited for other malicious purposes.
Table of Contents
What is a Watering Hole Attack?
A watering hole attack is a cyber threat method where attackers identify a group of individuals (often within a specific organization or industry) and compromise websites that they are known to visit regularly. The intention is to infect the users’ devices with malware, allowing hackers access to sensitive data.
Key Characteristics of Water Hole Attacks
- Targeted Approach: Unlike indiscriminate attacks, watering hole attacks are carefully planned with specific targets in mind.
- Malicious Payloads: These attacks often employ sophisticated malware that can steal passwords, harvest sensitive data, or provide the attacker with backdoor access.
- Trust Exploitation: By compromising trusted sites, attackers exploit users’ trust in those sources, increasing the likelihood of successful infection.
How Do Watering Hole Attacks Work?
The mechanics of a watering hole attack typically unfold in several stages:
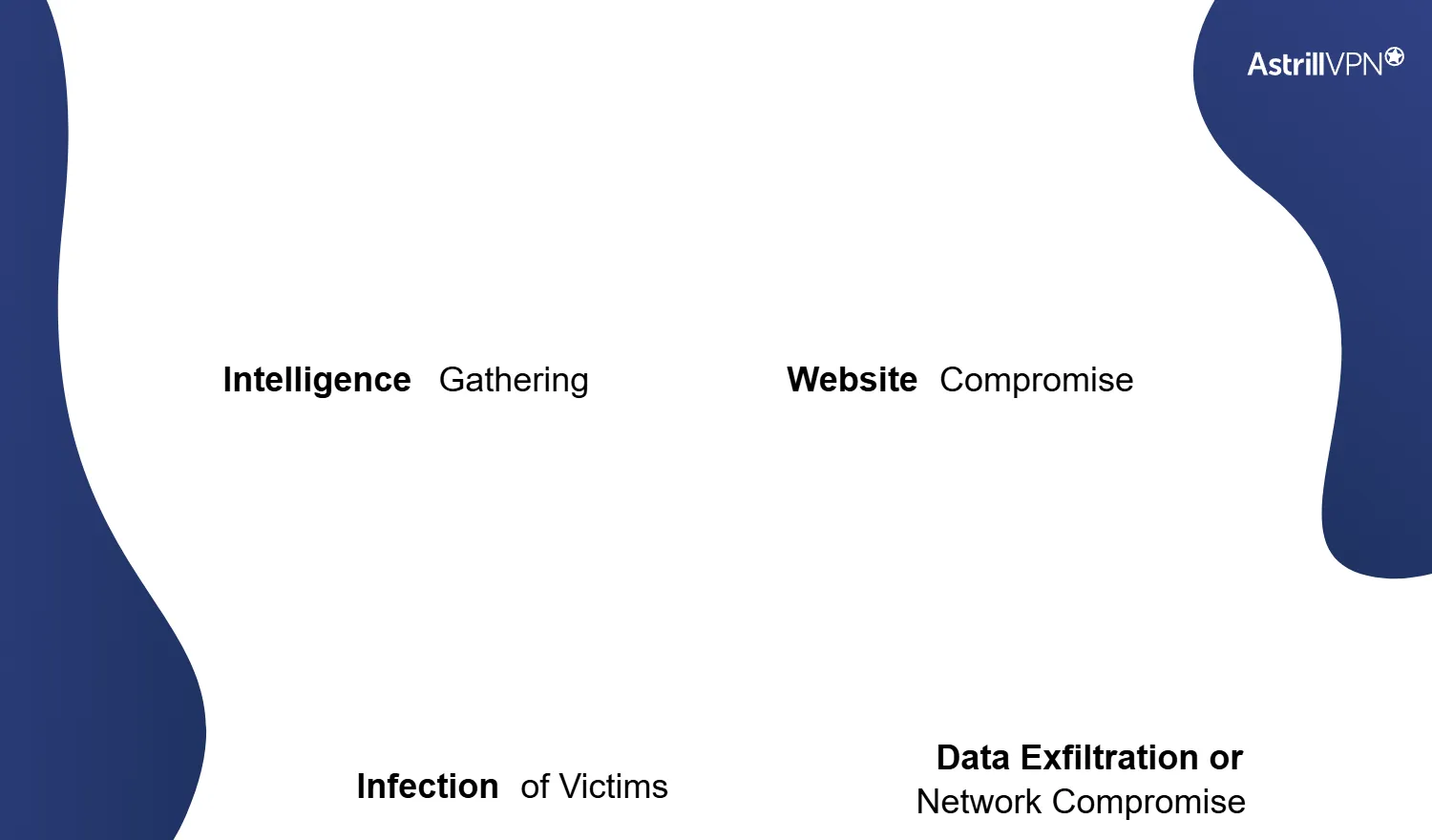
1. Intelligence Gathering
Attackers begin by researching their target to identify the websites that employees frequently visit. This may include industry forums, news sites, or even vendors.
2. Website Compromise
Once targets are identified, attackers will compromise these sites, injecting malicious code into them. This can be achieved through techniques such as SQL injection or exploiting vulnerable plugins.
3. Infection of Victims
When users from the target group visit the compromised website, the malicious code executes, often causing them to download malware onto their devices.
4. Data Exfiltration or Network Compromise
Once the malware is installed, attackers can begin to exfiltrate sensitive information or leverage the compromised devices as entry points into the organization’s network.
Signs of a Watering hole attack
Detecting a watering hole attack can be challenging, as these attacks often unfold subtly. However, there are several signs that may indicate a watering hole attack is in progress or has occurred. Here are some key signs to be aware of:
1. Unusual Website Behavior
- Unexpected Pop-Ups: If a commonly used website begins displaying unusual pop-ups or advertisements, it could be a sign that the site has been compromised.
- Redirects to Unknown Sites: If users are being redirected to unfamiliar or suspicious websites after visiting a trusted site, it may indicate a watering hole attack.
2. Security Software Alerts
- Malware Detection: Alerts from antivirus or endpoint protection software regarding malware detection when visiting specific sites could signal an infection attempt.
- Suspicious Activity Detection: Security software may mark certain website behavior as suspicious, especially if it attempts to download files without user consent.
3. Signs of Compromise on Websites
- Defaced Website Content: If legitimate websites show altered content or unexpected changes, they might be under attack or compromised.
- Code Injection or Injection Attacks: If web developers notice unfamiliar code or significant changes in the website’s backend, it may indicate malicious activity.
4. Unusual User Activity
- Unexpected Login Attempts: Investigating log files for unusual login attempts or access patterns from specific locations can help detect compromised credentials.
- Data Exfiltration: Sudden spikes in data transfer activity from specific devices or users may indicate that sensitive information is being accessed or transmitted by unauthorized users.
5. Network Anomalies
- Increased Internet Traffic: An unexpected rise in internet traffic directed towards certain outgoing connections may indicate data being sent to an attacker’s servers.
- Unusual DNS Requests: Monitoring DNS requests for familiar sites that redirect to unknown malicious IP addresses can signal a watering hole attack.
6. User Reports of Issues
- Employee Complaints: If multiple employees report problems when visiting trusted sites, such as slow load times or unexpected prompts, it may warrant further investigation into potential compromises.
7. Strange Application Behavior
- Malfunctions in Software: Legitimate applications behaving strangely, crashing, or showing signs of compromise may suggest that malware has infiltrated the system.
- Unauthorized Access Requests: Pop-ups requesting permissions that are out of the ordinary could indicate malware at work.
8. Phishing Attempts
- Targeted Phishing: Awareness of increased spear phishing attempts after visiting compromised sites may indicate attackers are attempting to leverage any acquired data.
Prevention and Response
If you suspect a watering hole attack, it’s essential to take immediate action:
- Isolate any devices that may have been compromised.
- Use security software to perform a full malware scan on affected systems.
- To minimize vulnerabilities, ensure that all software, plugins, and antivirus tools are up to date.
- Report the incident to the IT/security department for a comprehensive investigation and response.
Understanding these signs can help individuals and organizations identify possible watering hole attacks early, allowing for timely intervention and mitigation.
Other security exploits similar to watering hole attacks
Here are several security exploits that share similarities with watering hole attacks in terms of targeting users through trusted environments or exploiting vulnerabilities:
1. Phishing Attacks
Phishing involves the deceptive practice of tricking individuals into providing sensitive information, such as usernames and passwords, often through emails or fake websites. Unlike watering hole attacks, which compromise websites to infect users, phishing typically relies on social engineering tactics to lure users into giving up their information directly.
2. Spear Phishing
Spear phishing is a targeted version of phishing where attackers tailor their messages to a specific individual or organization, often using personal information to increase the likelihood of success. This exploit aims to deceive victims into clicking malicious links or downloading harmful attachments.
3. Drive-By Downloads
Drive-by downloads occur when a user visits a compromised website, and malware is automatically downloaded to their device without their consent. This is similar to watering hole attacks but focuses more on the automatic exploitation of vulnerabilities rather than targeting specific user groups.
4. Malvertising
Malvertising involves embedding malicious code into online advertisements that appear on legitimate websites. Users can be infected simply by viewing or clicking on these ads, similar to how watering hole attacks exploit trusted sites but utilizing ads as the vector instead of compromised websites.
5. Credential Stuffing
In a credential stuffing attack, cybercriminals take advantage of users who reuse passwords across multiple sites. By using leaked credentials from a breached site, attackers can attempt to gain unauthorized access to other accounts, capitalizing on the lack of security practices similar to watering hole attacks.
6. Man-in-the-Middle (MitM) Attacks
MitM attacks occur when an attacker secretly intercepts and relays messages between two parties who believe they are communicating directly with each other. This can involve exploiting insecure connections, similar to how attackers may exploit trusted environments in watering hole scenarios.
7. Zero-Day Exploits
Zero-day exploits take advantage of previously unknown vulnerabilities in software or hardware. While these exploits may not directly relate to user behavior as watering hole attacks do, they can be part of the attack lifecycle when combined with social engineering tactics to target specific organizations or individuals.
8. Remote Code Execution (RCE) Attacks
RCE attacks enable an attacker to execute arbitrary code on a remote machine. This can result from vulnerabilities in software that users may interact with regularly, aligning with the concept of manipulating trusted environments to gain unauthorized access.
9. Rogue Software
Rogue software refers to malicious programs that disguise themselves as legitimate software, tricking users into downloading and executing them. These attacks often exploit trust, much like watering hole attacks.
10. Social Engineering Attacks
Social engineering encompasses a broader range of tactics where attackers manipulate individuals into divulging confidential information. These techniques can be deployed in various forms, from impersonating IT staff to creating scenarios where individuals feel compelled to provide sensitive information.
Examples of watering hole attack in real life
- CVE-2012-1723 Attack: A watering hole attack exploited a vulnerability in Java, targeting websites frequented by employees of specific organizations. Users who visited these sites were infected with malware that enabled unauthorized access to their networks.
- Comment Crew Attack: A group of Chinese hackers used watering hole attacks to infiltrate the networks of defense contractors by compromising websites related to defense-related topics.
Statistics on Watering Hole Attacks
- According to a 2020 report by Symantec, watering hole attacks accounted for approximately 8% of all targeted attacks.
- A 2021 Interpol report highlighted that 40% of financial institutions experienced watering hole attacks over a 12-month period, emphasizing cybercriminals’ growing interest in this method.
- Attackers’ likelihood of success increases significantly; studies suggest that a 25% infection rate can be achieved when users visit compromised trusted sites.
How to Prevent Watering hole Attack – 4 Key Strategies
To mitigate the risk of watering hole attacks, organizations should consider implementing several strategies:
1. Regular Vulnerability Assessment
Conducting regular security assessments of websites that employees frequently use to ensure they are not compromised.
2. User Education and Awareness
Training employees to identify phishing attempts and the importance of not visiting suspicious websites can reduce risk significantly.
3. Robust Endpoint Security
The use of up-to-date antivirus software and endpoint protection solutions can help in detecting and mitigating malware infections.
4. Monitoring and Incident Response
Establishing a strong incident response plan can help organizations respond quickly to suspected watering hole attacks, minimizing damage and recovery time.
Conclusion
Watering hole attacks represent a significant risk to organizations, exploiting the trust of targeted individuals and the vulnerabilities of websites they use. By understanding how these attacks work and implementing preventive measures, businesses can protect themselves from potential threats and mitigate the impact of such attacks. Awareness, education, and robust security practices are essential components of an effective defense strategy against watering hole attacks.
FAQs
Answer: Look for abnormal behavior on frequently visited websites or receive warnings from your security software regarding potential threats.
Answer: Yes, industries such as finance, healthcare, and technology are often targeted due to the sensitive nature of their data.
Answer: While it’s difficult to prevent every attack, implementing strong security measures and user training can significantly reduce the chances of a successful watering hole attack.
Answer: Immediately disconnect from the network, run a full malware scan on your device, and report the incident to your IT/security team for further investigation.


No comments were posted yet