What Is OT Cybersecurity? Ultimate Guide on Protecting Industrial Systems

Bisma Farrukh
In an age of digital transformation, Operational Technology (OT) systems, once isolated and safe from outside threats, are increasingly connected to modern networks for efficiency, analytics, and automation. This connectivity, while beneficial, has radically shifted the cybersecurity landscape for industrial environments. Today’s OT infrastructure is a prime target for sophisticated threat actors, and organizations bear the consequences in the form of production stoppages, financial losses, and safety risks.
This blog explores the essentials of OT cybersecurity, the growing threat landscape, deep-dive vulnerabilities, best practices to defend industrial environments, and real statistics that show just how urgent this issue has become.
Table of Contents
What Is OT Cybersecurity?
Operational Technology (OT) refers to hardware and software systems that monitor and control physical devices, processes, and infrastructure in industrial environments. Examples include:
- Industrial Control Systems (ICS)
- Supervisory Control and Data Acquisition (SCADA)
- Distributed Control Systems (DCS)
- Programmable Logic Controllers (PLCs)
- Human-Machine Interfaces (HMIs)
OT cybersecurity is the practice of protecting OT systems from cyber risks, including unauthorized access, manipulation, and damage. Unlike traditional Information Technology (IT), which primarily protects data privacy and integrity, OT cybersecurity prioritizes the safety, availability, and reliability of physical operations.
Why OT Matters More Than Ever?
Industrial environments control crucial infrastructure, including power grids and water utilities, manufacturing floors, and oil pipelines. Because of these high-impact consequences, OT cybersecurity is not just an IT problem; it’s a business continuity and national security priority. A successful cyberattack on OT systems isn’t just about stolen data; it can cause:
- Production line shutdowns
- Damage to equipment
- Safety incidents
- Environmental harm
- Utility outages affecting millions of people
The Growing OT Threat Landscape
Industrial systems are under increasing attack as threat actors become more capable and motivated. Recent studies and industry reports reveal a rapid rise in cyber incidents targeting OT environments.
1. Rising Attack Rates
- A 2024 report found that nearly 70% of industrial organizations experienced at least one cyberattack in the past year, with 26% reporting attacks weekly.
- A survey showed that 73% of OT environments were impacted by intrusions, up sharply from prior years.
2. Impactful Incidents
- One report found that 1 in 4 industrial operations were forced to temporarily shut down due to attacks, a staggering statistic that illustrates how these threats affect operations.
- Another study found 1,700 ransomware attacks against industrial organizations in one year, an 87% increase over the year prior.
3. Persistent Vulnerabilities
Industrial automation device scanning has shown that about 12% of OT devices contain known exploited vulnerabilities (KEVs), with many insecurely connected to the internet.
4. Security Challenges in Digital Transformation
As companies digitize OT, nearly 40% of industrial enterprises view cybersecurity as a top challenge, especially when connecting isolated systems to broader networks. Together, these numbers paint a clear picture: the OT threat landscape is real and has a real operational impact.
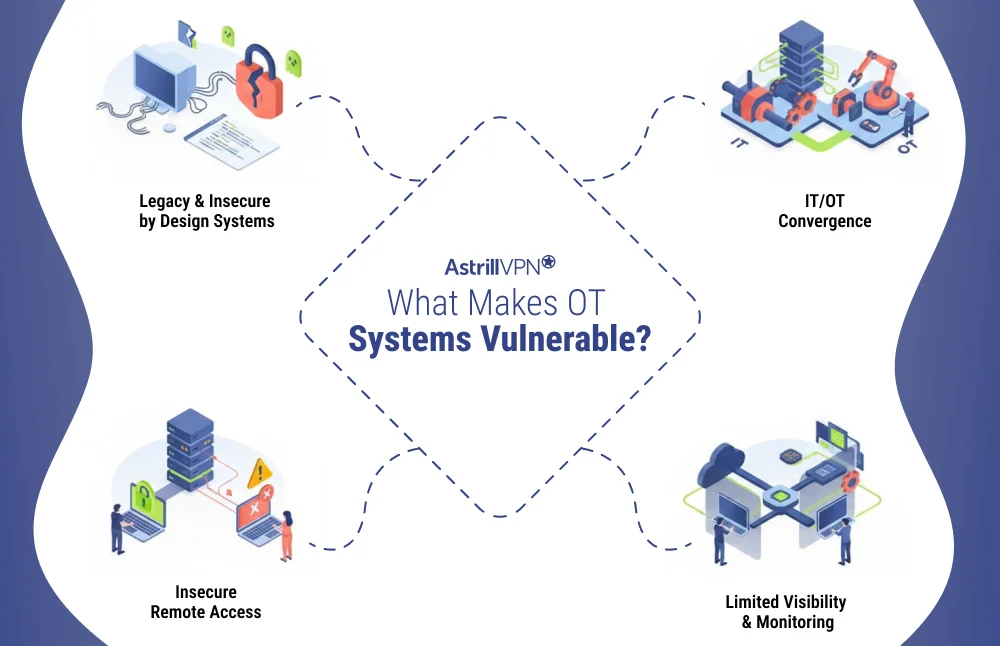
What Makes OT Systems Vulnerable?
The following issues make OT systems vulnerable.
1. Legacy and Insecure-by-Design Systems
Many OT systems were designed decades ago with functionality and uptime prioritized over security. These systems often lack modern cybersecurity features such as encryption, secure authentication, or update mechanisms, making them inherently vulnerable to attack.
In academic studies examining OT devices, every analyzed product family contained at least one trivial but exploitable vulnerability, underscoring inherent design weaknesses.
2. IT/OT Convergence
While necessary for digital transformation, the merger of IT and OT networks exposes OT systems to more traditional cyber risks:
3. Limited Visibility and Monitoring
Unlike IT environments, many OT systems lack centralized monitoring, intrusion detection, or even basic logging. This reduces the likelihood of detecting malicious activity early, which allows attackers to dwell in networks undetected.
4. Insecure Remote Access
OT engineers and third-party vendors use remote access tools for maintenance and monitoring. Without strong security controls, this introduces additional attack vectors.
OT Cybersecurity Threats: What Are Organizations Facing?
The following are the OT Cybersecurity threats organizations face daily:
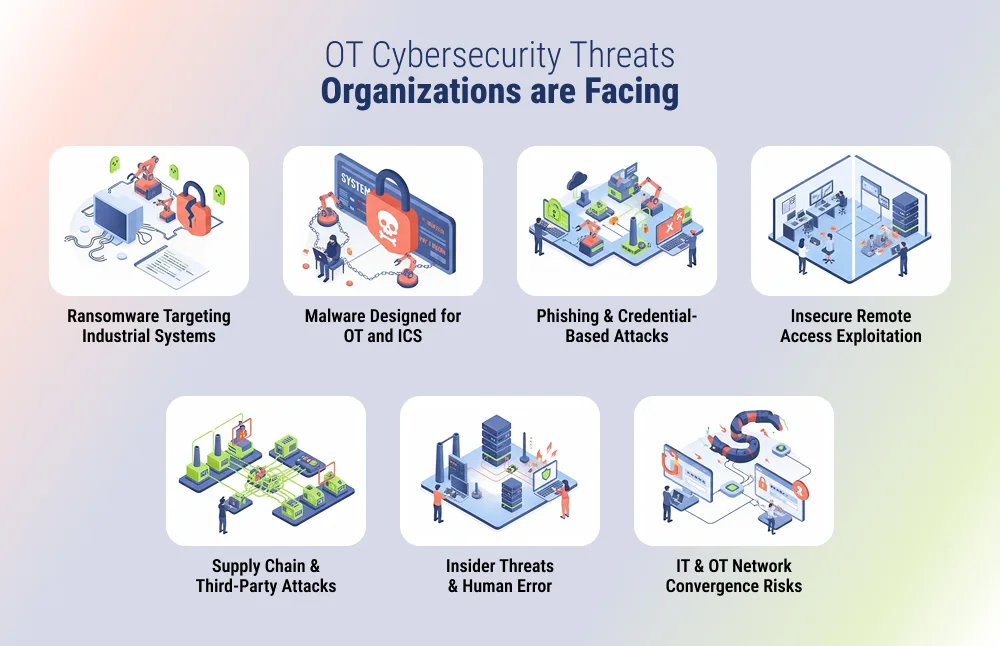
Ransomware Targeting Industrial Systems
Ransomware has emerged as one of the most disruptive threats to OT environments. Unlike traditional IT ransomware that encrypts data, OT-focused ransomware is designed to halt industrial processes by locking operators out of control systems or forcing shutdowns to prevent physical damage.
Attackers know that downtime in manufacturing plants, power grids, or oil and gas facilities can cost millions per hour, which increases pressure on organizations to pay ransoms quickly. These attacks often enter through IT networks and later move into OT systems due to weak segmentation.
Malware Designed for OT and ICS
Specialized malware targeting industrial control systems poses a serious risk to operational environments. Such malware is built to manipulate PLCs, SCADA systems, and other control components, potentially altering process logic or damaging physical equipment. Unlike generic malware, OT-specific malware can remain undetected for long periods, silently impacting operations and leading to unsafe conditions or sudden system failures.
Phishing and Credential-Based Attacks
Phishing remains a primary entry point for attackers targeting OT environments. By tricking employees or contractors into revealing login credentials, attackers gain unauthorized access to corporate IT networks and then pivot toward OT systems.
Once inside, compromised credentials allow attackers to operate with legitimate access, making detection difficult and increasing the likelihood of prolonged system compromise.
Insecure Remote Access Exploitation
Remote access technologies are widely used in OT environments for maintenance, monitoring, and vendor support. However, poorly secured remote connections, such as exposed VPNs, weak passwords, or outdated remote desktop tools, are frequently exploited by attackers. These weaknesses provide direct pathways into critical operational systems, bypassing traditional perimeter defenses.
Supply Chain and Third-Party Attacks
OT systems rely heavily on third-party vendors for software updates, firmware, and system integration. Attackers increasingly target these suppliers to infiltrate multiple organizations at once. Compromised updates or malicious components introduced through the supply chain can embed threats deep within OT environments, often going unnoticed until significant damage has occurred.
Insider Threats and Human Error
Insider threats remain a significant challenge for OT security. Employees or contractors with privileged access may unintentionally misconfigure systems, fall victim to phishing attacks, or bypass security controls for convenience. In some cases, disgruntled insiders may intentionally disrupt operations, making insider risk a persistent concern for organizations managing critical infrastructure.
IT and OT Network Convergence Risks
As organizations integrate IT and OT networks to support digital transformation, the attack surface expands significantly. Threats that were once confined to IT systems, such as malware, worms, and advanced persistent threats, can now reach OT environments. Without proper segmentation and monitoring, a single compromised endpoint can serve as a gateway to safety-critical industrial systems.
OT Security Vulnerabilities: What Are the Weak Points?
Here is a closer look at specific vulnerabilities common in industrial technology:
Legacy and Outdated Systems
One of the most critical weaknesses in OT environments is the widespread use of legacy systems. Many industrial control systems were deployed decades ago and were never designed to withstand modern cyber threats. These systems often run on unsupported operating systems and firmware that no longer receive security updates, leaving known vulnerabilities unpatched for years. Because replacing or upgrading OT equipment can be costly and disruptive, organizations frequently continue operating vulnerable systems.
Lack of Network Segmentation
Poor network segmentation is a significant vulnerability in OT security. In many environments, IT and OT systems share flat networks, allowing attackers to move laterally once access is gained. A breach that begins in a corporate IT system can quickly spread to critical operational assets if adequate separation, firewalls, and demilitarized zones (DMZs) are not in place. This lack of isolation significantly increases the potential impact of cyber incidents.
Insecure Industrial Protocols
Many industrial communication protocols used in OT environments were designed for reliability and speed, not security. These protocols often lack encryption, authentication, and integrity checks, making them vulnerable to interception, spoofing, and manipulation. Attackers can exploit these weaknesses to monitor traffic, alter commands, or disrupt physical processes without being easily detected.
Limited Asset Visibility and Monitoring
Organizations often lack complete visibility into their OT environments. Unknown or unmanaged devices, outdated documentation, and limited real-time monitoring make it difficult to detect abnormal behavior or unauthorized access. Without clear visibility, security teams may not recognize an attack until operational disruptions or equipment failures occur.
Weak Access Controls
In many OT environments, access controls are overly permissive. Shared accounts, hard-coded credentials, and minimal authentication remain standard practices. These weaknesses make it easier for attackers to gain and maintain access to critical systems, especially when credentials are stolen through phishing or exposed via remote access tools.
Insecure Remote Access Points
Remote connectivity is essential for modern OT operations, but it also introduces significant risk. Poorly configured VPNs, exposed remote desktop services, and outdated remote management tools can serve as entry points for attackers. Without strong authentication and strict access policies, remote access becomes one of the most exploited vulnerabilities in OT environments.
Long System Lifecycles
OT systems are designed to operate continuously for long periods, often spanning 20 to 30 years. While this longevity supports operational stability, it also means security measures quickly become outdated. Over time, systems accumulate vulnerabilities that are difficult to remediate without full replacements, increasing long-term cyber risk.
Limited Security Resources and Expertise
Many organizations lack dedicated OT cybersecurity personnel and rely on IT teams that may not fully understand industrial systems. This skills gap can lead to misconfigured defenses, delayed incident response, and ineffective risk management. Limited budgets and competing operational priorities further exacerbate these challenges.
OT Cybersecurity Best Practices
Protecting OT systems requires a multi-layered approach combining people, processes, and technology. Here are the key best practices that organizations should implement:
Network Segmentation and Isolation
One of the most effective OT cybersecurity best practices is strong network segmentation. Separating OT networks from IT systems and external networks reduces the risk of attackers moving laterally into critical operational assets. Using firewalls, secure gateways, and demilitarized zones (DMZs) helps limit access to sensitive control systems while still allowing necessary data flow for monitoring and analytics.
Comprehensive Asset Inventory and Visibility
Maintaining an accurate, up-to-date inventory of all OT assets is essential to adequate security. Organizations must know what devices, software, and communication protocols are in use to identify potential vulnerabilities. Continuous visibility into network traffic and device behavior enables security teams to detect anomalies, unauthorized devices, and suspicious activity before they cause operational disruption.
Continuous Monitoring and Threat Detection
OT environments require specialized monitoring tools designed to understand industrial protocols and normal operational behavior. Continuous monitoring enables early detection of abnormal activity, such as unexpected configuration changes or unauthorized command execution. Early detection is critical in OT environments, where delayed response can result in safety incidents or equipment damage.
Strong Access Control and Authentication
Limiting access to OT systems through role-based access control (RBAC) helps ensure that users only have the permissions necessary for their job functions. Organizations should implement strong authentication mechanisms, including multi-factor authentication for remote access. Reducing the number of shared accounts and enforcing strict credential management significantly reduces the risk of unauthorized access.
Secure Remote Access Management
Remote access is often necessary for maintenance and vendor support, but it must be tightly controlled. Secure remote access solutions should include encryption, strong authentication, session monitoring, and time-limited access. By restricting remote connectivity to approved users and devices, organizations can reduce one of the most commonly exploited attack vectors in OT environments.
Patch and Vulnerability Management
Although patching OT systems can be challenging due to uptime requirements, it remains a critical best practice. Organizations should establish controlled patch management processes that align with maintenance windows and operational constraints. When direct patching is not possible, compensating controls such as virtual patching or network-based protections can help reduce risk.
Incident Response and Recovery Planning
Developing an OT-specific incident response plan is essential for minimizing the impact of cyber incidents. These plans should define clear roles, communication procedures, and recovery steps tailored to industrial environments. Regular testing through tabletop exercises or simulations ensures that teams can respond effectively under real-world conditions.
Employee Training and Security Awareness
Human error is a significant factor in OT cybersecurity incidents. Providing regular training for engineers, operators, and contractors helps build awareness of phishing attacks, unsafe practices, and cybersecurity responsibilities. Educated personnel are better equipped to recognize early warning signs and follow secure operational procedures.
Risk Assessment and Compliance Alignment
Regular risk assessments help organizations identify weaknesses and prioritize security investments. Aligning OT cybersecurity efforts with recognized standards such as IEC 62443 or NIST guidelines provides a structured framework for improving security maturity. Compliance-driven assessments also support regulatory requirements and industry best practices.
Backup, Resilience, and Business Continuity
Reliable backups and recovery mechanisms are critical for maintaining operational resilience. Organizations should ensure that OT system configurations and necessary data are securely backed up and regularly tested. Strong resilience planning enables faster recovery from cyber incidents and reduces the likelihood of prolonged downtime.
Conclusion
Operational Technology systems form the backbone of modern industrial environments. As connectivity increases and digital transformation accelerates, OT cybersecurity has transformed from a niche concern to an enterprise-level priority. With major studies revealing that nearly 70% of industrial organizations have suffered cyberattacks and that shutting down operations due to an attack is increasingly common, it’s clear that robust OT cybersecurity isn’t optional; it’s essential.
Adequate OT security demands a risk-based, comprehensive approach that addresses people, processes, and technologies. By embracing best practices like network segmentation, Zero Trust, continuous monitoring, and employee training, organizations can protect their systems and the people and societies that depend on them from an increasingly hostile threat landscape.
FAQs
Here are some of the most frequently asked questions.
IT cybersecurity focuses on protecting data confidentiality, integrity, and availability. Its primary goal is to safeguard information. OT cybersecurity, however, emphasizes system availability, safety, and operational continuity. A failure in IT might result in lost data, a failure in OT could cause physical damage, safety incidents, and service disruptions.
Common threats include ransomware specifically targeting OT environments, phishing and credential theft, malware designed for industrial systems, supply chain risks, and insider threats. These attacks can result in system downtime, financial losses, or physical consequences.
Industries heavily dependent on OT systems face the most significant risks. These sectors provide essential services that are attractive targets due to their high value and potential for disruption.
Energy and utilities
Manufacturing
Oil and gas
Transportation
Water and wastewater treatment
Chemical and pharmaceutical
OT security solutions often differ from traditional IT products. Commonly used tools include:
Industrial firewalls and ICS-aware intrusion detection systems
OT-focused network monitoring tools with behavioral analytics
Secure remote access gateways.
Asset visibility and management platforms
Security information and event management (SIEM) solutions customized for OT
Zero Trust and identity governance systems


No comments were posted yet