What Is an SSL Stripping Attack and How to Prevent It

Bisma Farrukh
As internet users increasingly depend on secure websites for activities such as banking, shopping, and communication, encrypted connections have become essential to cybersecurity. The Secure Sockets Layer (SSL), known as Transport Layer Security (TLS), is crucial for protecting sensitive data as it travels between users and websites.
Attackers have developed methods to bypass this protection without triggering significant warnings. One such method is SSL stripping, a stealthy cyberattack that downgrades secure HTTPS connections to unencrypted HTTP, exposing user data to interception. This blog will explore what SSL stripping is, how these attacks work, why they remain a threat, and how organizations and users can defend against them.
Table of Contents
What Is SSL Stripping in Cybersecurity?
In cybersecurity, SSL stripping is considered a downgrade attack that targets weaknesses in how browsers and websites handle secure connections. Instead of breaking encryption directly, the attacker removes it altogether. This makes SSL stripping particularly dangerous because it does not rely on cracking cryptographic algorithms, but on manipulating the connection process itself.
SSL stripping is often used in public Wi-Fi environments such as cafes, airports, and hotels, where attackers can more easily position themselves between users and legitimate networks. Because the attack can occur silently, many victims remain unaware that their data has been compromised.
What Is an SSL Stripping Attack?
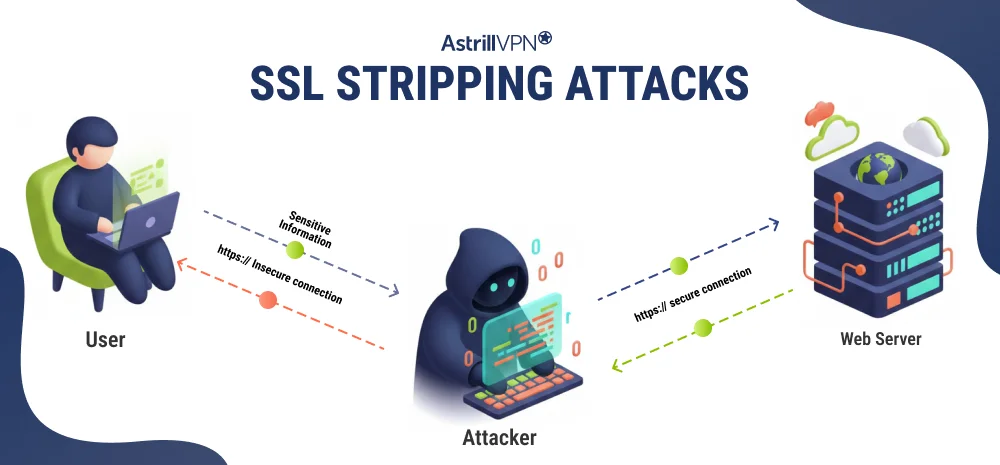
An SSL stripping attack occurs when an attacker intercepts traffic between a user and a web server and alters it in real time. The attacker acts as a proxy, maintaining an HTTPS connection with the legitimate website while presenting an HTTP version of the site to the victim.
This allows the attacker to:
- Read all data sent by the user
- Modify content before it reaches the user.
- Steal credentials without triggering certificate warnings.
Unlike traditional SSL attacks that attempt to forge or break certificates, SSL stripping avoids detection by making the user believe the site was never secure in the first place.
How do SSL Stripping Attacks Work?
SSL stripping attacks exploit the moment when a user’s browser transitions from an unsecured to a secure connection. Instead of breaking encryption, the attacker prevents it from being established in the first place. The attack typically unfolds in several stages.
Positioning Between the User and the Network
The attacker places themselves between the victim and the internet. This is commonly done on unsecured or public Wi-Fi networks using techniques such as ARP spoofing, DNS spoofing, or by setting up a rogue access point. At this stage, all of the victim’s web traffic passes through the attacker’s system.
Intercepting the Initial HTTP Request
When a user types a website address without explicitly including “https://”, the browser initially sends an HTTP request. The website then redirects the browser to the HTTPS version. In an SSL stripping attack, the attacker intercepts this request before it reaches the legitimate server.
Blocking the HTTPS Redirect
Instead of allowing the secure redirect, the attacker blocks or alters it. The victim’s browser remains on an unencrypted HTTP connection, while the attacker establishes a separate HTTPS connection to the real website. This creates two parallel connections: one secure and one insecure.
Acting as a Man-in-the-Middle
The attacker now acts as a proxy between the user and the website. Data entered by the victim, such as usernames or form fields, is sent to the attacker in plain text. The attacker can read or modify this data before forwarding it securely to the legitimate website.
Stealing Sensitive Information
Because the victim’s connection is not encrypted, the attacker can capture sensitive information, including login credentials, session cookies, and personal data. The website continues to function normally, which makes the attack difficult for users to detect.
Maintaining the Illusion of a Normal Session
Throughout the session, the attacker forwards responses from the website back to the victim over HTTP. As long as the user does not notice the missing HTTPS padlock or security indicators, the attack can continue uninterrupted.
Types of SSL Stripping Attacks
SSL stripping attacks can take several forms depending on how attackers position themselves and manipulate web traffic. While the core objective remains the same, downgrading HTTPS connections to HTTP, the methods used can vary based on the network environment and the attacker’s level of access.
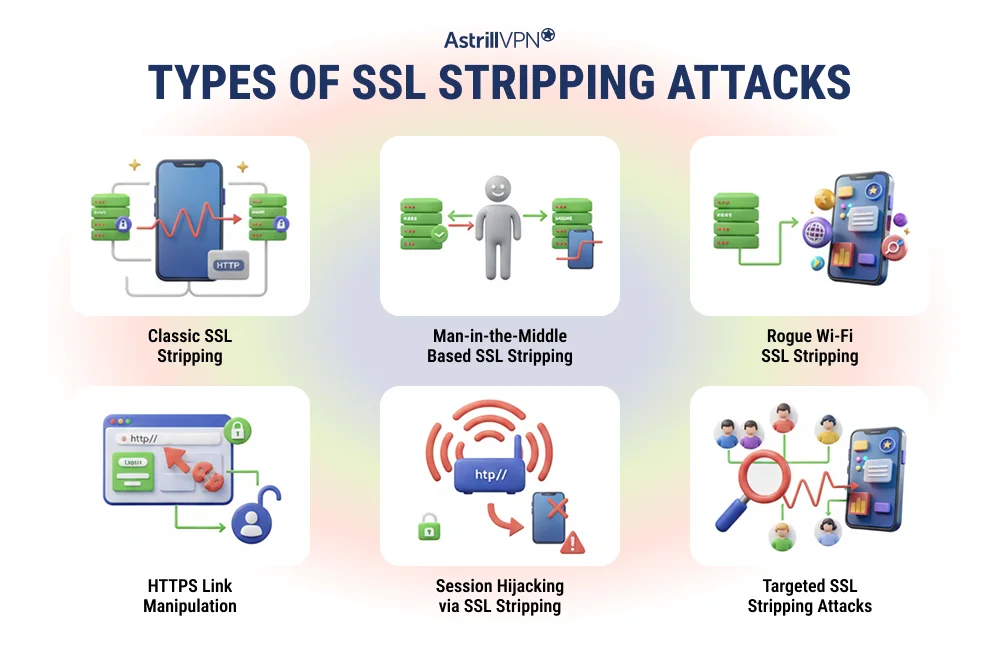
Classic SSL Stripping (HTTP Downgrade Attack)
This is the most common form of SSL stripping. The attacker intercepts the victim’s initial HTTP request and blocks the redirect to HTTPS. The user unknowingly continues the session over HTTP, while the attacker maintains a secure HTTPS connection with the legitimate website. This classic downgrade attack is especially effective on public Wi-Fi networks.
Man-in-the-Middle Based SSL Stripping
The attacker deliberately positions themselves between the user and the server using man-in-the-middle techniques such as ARP spoofing or DNS poisoning. Once in control of the traffic flow, the attacker strips HTTPS links and replaces them with HTTP versions, ensuring all communication from the victim remains unencrypted.
Rogue Wi-Fi SSL Stripping
Attackers create malicious Wi-Fi hotspots that appear legitimate, such as free public internet access points. When victims connect, all traffic is routed through the attacker’s system. The attacker then performs SSL stripping by preventing secure connections and monitoring sensitive data transmitted over HTTP.
HTTPS Link Manipulation
Instead of intercepting redirects, attackers modify web content in transit by changing HTTPS links to HTTP. This forces users to click on insecure links even when navigating within a site. Over time, the user remains on unencrypted pages without realizing that a secure option was available.
Session Hijacking via SSL Stripping
In this variation, the primary goal is not just to steal login credentials but to capture session cookies transmitted over HTTP. By intercepting these cookies, attackers can impersonate the user and gain unauthorized access to accounts without needing a password.
Targeted SSL Stripping Attacks
Some attackers use SSL stripping in a targeted manner against specific individuals. These attacks often involve prior reconnaissance and may be combined with phishing or social engineering tactics to increase success rates. Targeted attacks are more complex to detect and can result in more severe data breaches.
What are the Potential Risks of SSL Stripping Attacks?
SSL stripping attacks pose serious security risks because they silently remove encryption from web communications. Since users often remain unaware that their connection is no longer secure, attackers can exploit this vulnerability to cause significant harm.
Theft of Login Credentials
One of the most immediate risks of SSL stripping is the exposure of usernames and passwords. When a secure HTTPS connection is downgraded to HTTP, login details are transmitted in plain text, allowing attackers to capture credentials for email accounts, social media platforms, and corporate systems.
Session Hijacking and Account Takeover
If passwords are not directly stolen, attackers can intercept session cookies sent over unsecured connections. These cookies can be reused to hijack active sessions, granting attackers unauthorized access to user accounts without requiring them to log in again.
Exposure of Sensitive Personal Data
SSL stripping can lead to the leakage of personal information such as names, addresses, phone numbers, and email details. If users fill out forms or interact with web applications over an insecure connection, all submitted data becomes visible to the attacker.
Financial Fraud and Identity Theft
When SSL stripping occurs on banking, shopping, or payment-related websites, attackers may steal credit card details or financial credentials. This information can be used to commit fraudulent transactions, resulting in significant economic losses for victims.
Data Manipulation and Content Injection
Beyond stealing data, attackers can alter information as it passes between the user and the website. This can include injecting malicious scripts, modifying displayed content, or redirecting users to phishing pages, increasing the risk of malware infections and further compromise.
Corporate Data Breaches
In organizational environments, SSL stripping can expose confidential business information, internal credentials, or proprietary data. Compromised employee sessions may allow attackers to move laterally within corporate networks, increasing the scale and impact of a breach.
Erosion of Trust and Reputational Damage
For businesses, successful SSL stripping attacks can damage customer trust. Users expect secure communication, and data breaches resulting from downgraded connections can lead to reputational harm, legal consequences, and regulatory penalties.
Key SSL Stripping & Related Security Stats
- Man-in-the-Middle (MITM) attacks targeting HTTP-only sites have increased by ~36%, driven by poor SSL configurations and unsecured networks.
- MITM attacks over public Wi-Fi rose by about 41%, underscoring how common downgrade and interception opportunities remain on open networks.
- APIs vulnerable to forced HTTPS downgrade remain prevalent (~14%), providing attackers with potential entry points for SSL stripping variants.
- About 68% of mobile users reported connecting to open Wi-Fi in the past year, and nearly one-third conducted financial transactions while connected, making SSL stripping and similar MITM attacks far more dangerous.
- Only about 27% of users regularly use a VPN, leaving most traffic unprotected over insecure networks.
Why are SSL Stripping Attacks so dangerous?
SSL stripping attacks are considered especially dangerous because they undermine one of the most fundamental protections on the internet, i.e., encrypted communication without drawing attention to the attack. Their stealth, simplicity, and effectiveness make them a serious cybersecurity threat.
They Bypass Encryption Without Breaking It
Unlike many cyberattacks that attempt to crack or exploit encryption algorithms, SSL stripping simply removes encryption from the connection. By forcing users to use HTTP instead of HTTPS, attackers can access data in plain text. This makes the attack efficient and difficult to defend against if HTTPS is not strictly enforced.
Minimal or No Security Warnings
One of the biggest dangers of SSL stripping is that it often produces no browser alerts. Since no invalid certificate is used, users are not warned about insecure connections. Many people do not notice the missing HTTPS padlock, allowing the attack to continue undetected.
High Success Rate on Public Networks
SSL stripping is particularly effective on public or unsecured Wi-Fi networks, where attackers can easily position themselves as a man-in-the-middle. Cafes, airports, hotels, and shared workspaces are common locations where these attacks succeed, putting a large number of users at risk.
Complete Visibility of User Data
Once encryption is stripped, attackers can see everything transmitted during the session. This includes login credentials, session cookies, personal messages, and financial information. The scope of data exposure is often broader than in other SSL-related attacks.
Enables Further Attacks
SSL stripping is often just the first step in a larger attack chain. Stolen credentials and session data can be used for account takeovers, identity theft, or lateral movement within corporate networks, increasing the overall impact of the attack.
Exploits User Behavior and Trust
Many users assume that websites are secure by default and do not verify URL schemes or security indicators. SSL stripping exploits this trust and lack of vigilance, making even security-aware users vulnerable under the right conditions.
Hard to Detect After the Fact
Because SSL stripping leaves no evident traces and requires no malware installation, victims may never realize they were attacked. This delayed detection allows attackers to exploit stolen data long after the initial compromise.
SSL Strip Attack vs Other SSL Attacks
Approach to Encryption
An SSL stripping attack works by removing encryption from a web session entirely. Instead of attempting to break or weaken SSL/TLS encryption, the attacker forces the connection to remain on HTTP rather than HTTPS. This downgrade happens during the initial connection phase, allowing the attacker to read all transmitted data in plain text. In contrast, most other SSL attacks attempt to exploit weaknesses within the encryption protocol itself rather than eliminating it.
Visibility and User Awareness
One of the most dangerous aspects of an SSL strip attack is its stealth. Because no fake or invalid certificate is presented to the user, browsers typically do not display security warnings. Users may overlook the absence of the HTTPS padlock. Other SSL attacks, such as certificate spoofing or man-in-the-middle attacks using forged certificates, trigger browser alerts that warn users of potential security risks.
Technical Complexity
SSL stripping relies more on network positioning and traffic manipulation than on advanced cryptographic techniques. Attackers commonly use methods like ARP spoofing or rogue Wi-Fi access points. On the other hand, traditional SSL attacks such as BEAST, POODLE, or Heartbleed require a deeper understanding of cryptographic flaws or protocol vulnerabilities and often depend on outdated software or configurations.
Type of Data Exposure
In an SSL strip attack, all data transmitted between the user and the website can be intercepted in clear text, including login credentials and session cookies. Other SSL attacks may expose only partial information or require additional steps to decrypt captured traffic. The scope of exposure in SSL stripping is often broader because the data is never encrypted in the first place.
Detection and Mitigation
Detecting SSL stripping is difficult without careful monitoring of URLs and security indicators. Prevention depends heavily on enforcing HTTPS and on using technologies such as HTTP Strict Transport Security (HSTS). Other SSL attacks are often mitigated through software patches, protocol upgrades, and turning off vulnerable cipher suites. While updates can neutralize many SSL vulnerabilities, SSL stripping requires strict connection enforcement to be entirely prevented.
Overall Risk Comparison
While both attack types pose serious security risks, SSL stripping is particularly effective against inattentive users and unsecured networks. Other SSL attacks tend to be more situational and technically constrained. As a result, SSL stripping remains a persistent threat where HTTPS is not strictly enforced, highlighting the importance of modern web security best practices.
Secure Socket Layer Stripping Explained
Secure Socket Layer stripping is simply another term for SSL stripping, emphasizing the removal of SSL protection from a connection. Even though TLS has largely replaced SSL, the term remains widely used in cybersecurity discussions.
By stripping away the secure layer, attackers gain access to the raw data stream between the user and the website. This makes Secure Sockets Layer stripping particularly effective against users who are unaware of how HTTPS works or who do not regularly check browser security indicators.
SSL Stripping Prevention
Preventing SSL stripping attacks requires a combination of secure website configuration, modern browser protections, and user awareness. Since SSL stripping exploits the transition from HTTP to HTTPS, the most effective defenses focus on eliminating unsecured connections.
Enforce HTTPS Everywhere
Websites should enforce HTTPS across all pages and services, not just login or payment sections. Redirecting HTTP traffic to HTTPS is helpful, but relying solely on redirects still leaves a brief window for attackers to interfere. Configuring servers to refuse HTTP connections entirely significantly reduces the risk of SSL stripping.
Implement HTTP Strict Transport Security (HSTS)
HTTP Strict Transport Security (HSTS) is one of the strongest defenses against SSL stripping. When a website enables HSTS, it instructs browsers to communicate with the site only over HTTPS. Any attempt to load the site over HTTP is automatically blocked, preventing attackers from downgrading the connection. Using HSTS preload lists ensures protection even on a user’s first visit.
Use Secure Cookies and Proper Flags
Setting cookies with the Secure and HttpOnly flags ensures they are only transmitted over encrypted connections and are inaccessible to client-side scripts. This limits the impact of SSL stripping by protecting session data, even if an attacker attempts to intercept traffic.
Keep SSL/TLS Configurations Updated
Web servers should be configured to use modern TLS versions and strong cipher suites. Turning off outdated protocols such as SSLv2, SSLv3, and weak TLS versions reduces the overall attack surface. Regular audits and updates help prevent attackers from exploiting configuration weaknesses.
Avoid Unsecured Public Networks
From a user perspective, public Wi-Fi networks are familiar environments for SSL stripping attacks. Avoid accessing sensitive accounts on unsecured networks whenever possible. If access is necessary, using AstrillVPN adds an encryption layer that protects data from interception.
Monitor and Educate Users
Organizations should monitor network traffic for suspicious behavior, such as unexpected HTTP connections to domains that should be HTTPS-only. Educating users to recognize missing HTTPS indicators, such as the absence of a padlock icon, is crucial to prevention.
Use Modern Browsers and Security Tools
Modern browsers include built-in protections that warn users about insecure connections and mixed content. Keeping browsers and operating systems up to date ensures these protections remain effective. Security extensions and endpoint protection tools can further help detect and block downgrade attacks.
By combining strict HTTPS enforcement, HSTS implementation, secure configurations, and informed user behavior, organizations and individuals can effectively defend against SSL stripping and maintain the confidentiality of online communications.
Conclusion
SSL stripping is a subtle but dangerous cyberattack that exploits the transition between unsecured and secured web connections. By downgrading HTTPS to HTTP, attackers can silently intercept sensitive data without triggering alarms. Although modern security measures have reduced its prevalence, SSL stripping remains a threat in poorly secured environments and on public networks. Understanding how SSL stripping works, recognizing its warning signs, and implementing strong prevention measures such as HSTS and encrypted connections are essential steps to protecting data and maintaining online security.
FAQs
Here are some frequently asked questions.
An SSL stripping attack typically follows a structured process. First, the attacker positions themselves between the victim and the internet, often through ARP spoofing or a rogue Wi-Fi access point. When the victim attempts to access a website, the attacker intercepts the initial HTTP request.
Next, the attacker prevents the server’s HTTPS redirect from reaching the user. Instead, the attacker maintains an encrypted HTTPS connection with the server while serving an unencrypted HTTP version to the victim. All data entered by the user, including usernames and passwords, is transmitted in plain text to the attacker, who then forwards it securely to the real website.
SSL stripping can expose a wide range of sensitive information. Attackers can capture login credentials for websites, including usernames and passwords. Session cookies may also be intercepted, allowing attackers to hijack authenticated sessions without knowing the password.
In addition, personal data such as email addresses, contact information, and even financial details can be compromised. If the victim enters payment information or interacts with unsecured forms, this data can be read and reused for identity theft or financial fraud.
Detecting SSL stripping can be challenging, but there are warning signs users can watch for. A website that uses HTTPS may suddenly load over HTTP without explanation. The absence of the padlock icon or security indicators in the browser address bar is a common clue.
Other signs include repeated logouts, unexpected redirects, or pages that appear slightly altered. On unsecured networks, these signs should raise immediate suspicion, especially when accessing sensitive accounts.
Despite improvements in browser security and widespread HTTPS adoption, SSL stripping remains a relevant threat. Many websites still allow initial HTTP connections before redirecting to HTTPS, creating an opportunity for attackers. Public Wi-Fi networks remain high-risk environments where man-in-the-middle attacks are easier to execute.
While modern protections have reduced the effectiveness of SSL stripping, outdated systems, misconfigured servers, and inattentive users keep the attack viable in specific scenarios.
HTTP Strict Transport Security (HSTS) is a web security policy that instructs browsers to connect to a website only over HTTPS. Once a browser receives an HSTS header, it will automatically reject any attempt to load the site over HTTP, even if an attacker tries to force a downgrade.
By eliminating the initial unsecured connection, HSTS effectively neutralizes SSL stripping attacks. Many major websites and browsers also support HSTS preload lists, which ensure secure connections from the very first visit.


No comments were posted yet