Maze Ransomware Explained: Attacks, Group Operations, and How to Stay Protected?

Bisma Farrukh
Ransomware attacks have evolved rapidly over the past few years, becoming more targeted, aggressive, and damaging. Among the most notorious threats was Maze ransomware, a strain that reshaped how ransomware campaigns operate. Maze was not just about encrypting files; it introduced data theft and public shaming as part of its attack strategy, pressuring victims into paying ransoms.
This blog provides a detailed analysis of Maze ransomware, including its operational mechanics, the group behind it, and steps individuals and organizations can take to protect themselves and respond effectively.
Table of Contents
What Is Maze Ransomware?
Maze ransomware was a sophisticated strain of ransomware that emerged in late 2019 and quickly gained global attention. It was designed to infiltrate systems, encrypt critical files, and demand a ransom payment in exchange for a decryption key.
What made Maze particularly dangerous was its use of a double extortion tactic. In addition to encrypting files, Maze operators stole sensitive data and threatened to publish it online if victims refused to pay. This approach significantly increased pressure on businesses, especially those handling confidential data.
Maze Ransomware Attack Overview
A Maze ransomware attack typically targets medium to large organizations, including healthcare providers, law firms, government agencies, and enterprises. These attacks frequently resulted in operational shutdowns, financial losses, and long-term reputational damage.
Maze attacks were carefully planned rather than random. Attackers spent time inside victim networks, identifying valuable data and critical systems before launching an encryption. This made recovery more complex and increased the likelihood of ransom payment.
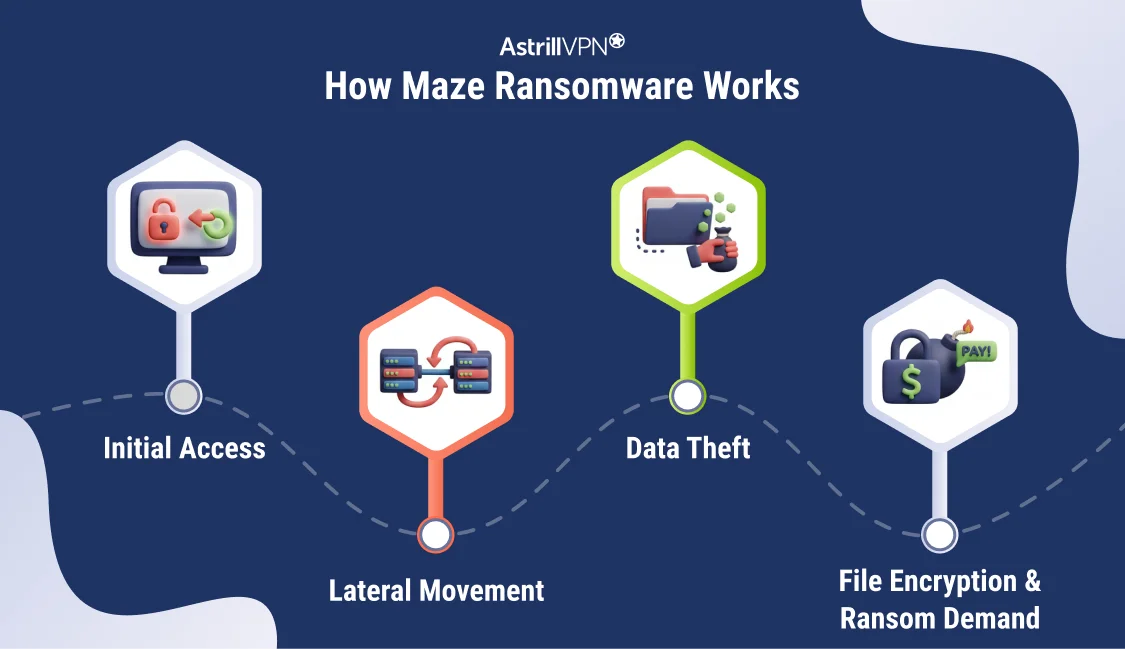
How Does Maze Ransomware Work?
Maze ransomware operates through a multi-stage attack process designed to maximize damage and leverage.
Initial Access
Attackers typically gained entry through phishing emails, malicious attachments, compromised websites, or stolen credentials. In some cases, exposed Remote Desktop Protocol (RDP) services were exploited.
Lateral Movement
Once inside the network, Maze attackers moved laterally to identify valuable systems, backup servers, and sensitive data. They often turned off security tools and backups to prevent recovery.
Data Theft
Before encrypting files, attackers exfiltrated sensitive information, including customer records, financial data, and internal documents.
File Encryption and Ransom Demand
Finally, Maze ransomware encrypted files across the network and left ransom notes demanding payment, usually in cryptocurrency. Victims were warned that stolen data would be published if payment was not made.
Maze Ransomware Analysis
From a technical and operational perspective, Maze ransomware represented a significant shift in ransomware strategy. It combined advanced intrusion techniques with psychological pressure, making it more effective than earlier ransomware variants.
Key characteristics identified during Maze ransomware analysis include:
- Strong encryption algorithms that made file recovery extremely difficult without a key
- Manual deployment rather than automated spreading
- Data exfiltration before encryption
- Public leak sites used to pressure non-paying victims
Key statistics and data points of Maze ransomware attacks
Here are some key statistics related to Maze ransomware attacks and their impact, based on cybersecurity research and incident reports:
Number of Victims and Incidents
- The Maze ransomware group was linked to more than 100 publicly reported victims in its first year of operation, with organizations affected across North America and other regions, spanning various industries, including healthcare, technology, and legal services.
- At its peak, Maze had hundreds of victims worldwide, with reports indicating that the ransomware strain accounted for 273 attacks in 2020 alone, outpacing other prominent ransomware families during that period.
- Group-IB data shows Maze was responsible for a significant share of ransomware exposures in 2025, accounting for roughly 19–20% of listed victims on ransomware leak sites, more than any other single actor that year.
- During 2020, Maze was a dominant actor in the so-called “double extortion” ransomware category, accounting for about 30% of reported ransomware incidents involving data theft and encryption in multiple months.
- While exact numbers for Maze ransom payments are not publicly disclosed in full, major attacks often included multi-million-dollar ransom demands. For example, one attack on an industrial company involved demands as high as 850 Bitcoin (~$6 million at the time).
What Is the Maze Ransomware Group?
The Maze ransomware group was a well-organized cybercriminal operation rather than a single individual. It operated as a Ransomware-as-a-Service (RaaS) model, where developers created the malware and affiliates carried out attacks in exchange for a share of the ransom.
The group maintained a high level of professionalism, including negotiation portals, victim support channels, and detailed ransom instructions. This structure allowed Maze to scale rapidly and target high-value organizations worldwide.
How Did the Maze Ransomware Group Operate?
The Maze ransomware group followed a structured and strategic operating model:
- Affiliate recruitment: Skilled attackers were recruited to deploy Maze ransomware
- Targeted attacks: Victims were carefully selected based on size, revenue, and data sensitivity
- Public pressure: Non-paying victims were named and shamed on data leak websites
- Negotiation tactics: Victims were given deadlines and partial data leaks as warnings
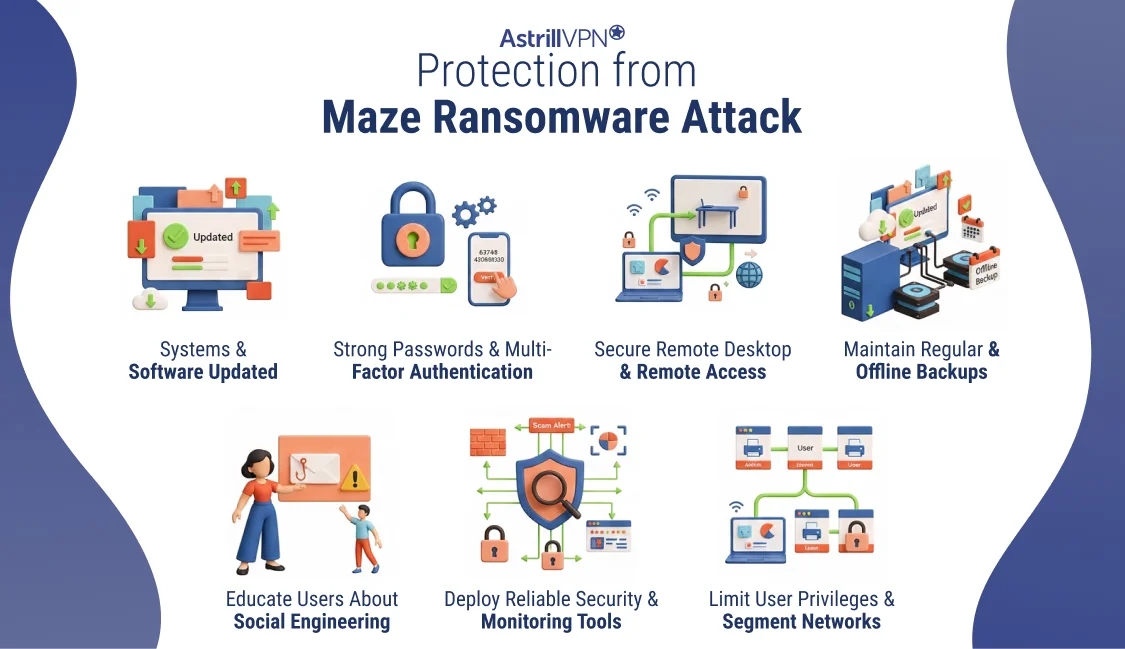
How Can I Protect Myself from a Maze Ransomware Attack?
The following practices can be adopted to protect yourself from a Maze Ransomware attack.
Keep Systems and Software Updated
Keeping your operating systems, applications, and firmware up to date is one of the most effective ways to prevent a Maze ransomware attack. Maze often exploited known vulnerabilities in outdated software to gain initial access. Regular updates and timely security patches close these entry points, reducing the risk of attackers infiltrating your system.
Use Strong Passwords and Multi-Factor Authentication
Weak or reused passwords make it easier for attackers to access systems, primarily through exposed remote services. Using strong, unique passwords for all accounts and enabling multi-factor authentication adds an extra layer of security. If credentials are stolen, MFA helps prevent unauthorized access.
Secure Remote Desktop and Remote Access Services
Maze ransomware commonly targets unsecured Remote Desktop Protocol (RDP) connections. Limiting remote access, changing default ports, using VPNs, and restricting RDP access to trusted IP addresses can significantly reduce the likelihood of a successful attack.
Maintain Regular and Offline Backups
Regular data backups are critical for recovery from ransomware attacks. Backups should be stored offline or in a secure, isolated environment to prevent them from being encrypted by ransomware. This ensures that systems and data can be restored without having to pay the ransom.
Educate Users About Phishing and Social Engineering
Phishing emails and malicious links are standard methods of delivery for Maze ransomware. Training employees and users to recognize suspicious emails, attachments, and websites helps prevent accidental malware downloads and reduces overall risk.
Deploy Reliable Security and Monitoring Tools
Using reputable antivirus, endpoint protection, and network monitoring solutions helps detect and block ransomware activity early. Continuous monitoring enables the identification of suspicious behavior before the ransomware spreads across the network.
Limit User Privileges and Segment Networks
Restricting user privileges reduces the damage ransomware can cause if an account is compromised. Network segmentation further limits lateral movement, preventing Maze ransomware from spreading freely across systems and accessing critical resources.
What Should I Do If My System Is Infected with Maze Ransomware?
If your system is infected with Maze ransomware, follow these steps:
Isolate the Infected System Immediately
As soon as a Maze ransomware infection is detected, disconnect the affected system from the network. This helps prevent the ransomware from spreading to other devices or shared drives. Avoid shutting the system down unless advised by security professionals, as valuable forensic data may be lost.
Assess the Scope of the Infection
Identify which systems, files, and network segments have been affected. Understanding the extent of the infection helps determine the best response strategy and prevents further damage. Check for encrypted files, ransom notes, and signs of data exfiltration.
Notify Your IT Team or Security Professionals
Contact your IT department or a cybersecurity incident response team immediately. Maze ransomware attacks are complex and often involve data theft, so professional guidance is essential for containment, investigation, and recovery.
Preserve Evidence for Investigation
Do not delete ransom notes, logs, or suspicious files. Preserving evidence helps cybersecurity experts analyze how the attack occurred and may assist law enforcement in investigations or future prevention efforts.
Do Not Rush to Pay the Ransom
Paying the ransom does not guarantee that files will be decrypted or that stolen data will not be leaked. It also encourages further criminal activity. Explore all recovery options, including backups and available decryption tools, before considering any payment.
Restore Systems from Clean Backups
If secure backups are available, restore affected systems only after ensuring the malware has been entirely removed. Backups should be scanned and verified to prevent reinfection during the recovery process.
Report the Incident to Authorities
Reporting the attack to relevant law enforcement or cybersecurity authorities can help track ransomware operations and may provide additional guidance. Some industries are also legally required to report data breaches involving sensitive information.
Strengthen Security After Recovery
Once systems are restored, review and improve security controls. Patch vulnerabilities, change compromised credentials, enable multi-factor authentication, and conduct security training to reduce the risk of future ransomware attacks.
Can Maze Ransomware Be Decrypted Without Paying the Ransom?
Maze ransomware cannot be decrypted without paying the ransom because it uses strong, industry-grade encryption algorithms. These encryption methods are designed to make brute-force decryption practically impossible without the unique decryption key held by the attackers.
Paying the ransom is not guaranteed to restore your files or prevent stolen data from being leaked. Many victims have reported partial decryption, corrupted files, or continued extortion even after payment. As a result, law enforcement agencies and cybersecurity experts strongly advise against paying ransoms.
In some limited situations, files may be recovered without paying if secure backups are available or if security researchers release a free decryption tool due to a flaw discovered in the ransomware. Unfortunately, no universal public decryptor exists for Maze ransomware, making prevention and backup strategies the most reliable defense against it.
The safest recovery approach is to completely remove the malware, restore data from clean backups, and strengthen security measures to prevent future ransomware infections.
Conclusion
Maze ransomware marked a turning point in the evolution of ransomware attacks. By combining file encryption with data theft and public exposure, the Maze ransomware group introduced tactics that reshaped the cybercrime landscape.
Understanding how Maze ransomware operates, the group’s modus operandi, and how to respond to an attack is essential for modern cybersecurity preparedness. Although the Maze group itself is no longer active, its legacy endures through similar ransomware threats, underscoring the importance of robust security practices more than ever.


No comments were posted yet