Defense in Depth: A Complete Guide to Layered & Integrated Security

Bisma Farrukh
Cyberattacks today rarely rely on a single weakness. Modern breaches usually unfold in stages. An attacker phishes a user, escalates privileges, moves laterally, and quietly extracts data. This is precisely why single-layer security no longer works.
Defense in depth is built on a simple but powerful idea: no single control should ever be trusted to stop an attack on its own. Instead, organizations deploy multiple, coordinated layers of protection so that if one fails, others are ready to detect, slow, contain, and stop the threat.
In this guide, you will learn what defense in depth really means, how a defense in depth strategy is built, how layered security and integrated security fit into the model, and how modern organizations design and measure effective multi-layer defenses.
Table of Contents
What is Defence in Depth?
Defense in depth is a cybersecurity approach that uses multiple, overlapping security controls across people, processes, and technology to protect systems, networks, and data.
The concept comes from military strategy, where multiple defensive positions are built so that even if one is overrun, others continue to resist. In cybersecurity, the same thinking applies. Systems are designed with the assumption that some controls will eventually fail.
Rather than relying on a single perimeter control, such as a firewall, defense in depth spreads protection across multiple points. The goal is not just to block attacks, but to:
- Reduce the chance of a successful breach
- Limit how far an attacker can move.
- Detect threats early
- Slow down malicious activity.
- Contain damage and support fast recovery.
Core Principles Behind a Strong Defense in Depth Strategy
A defense-in-depth strategy is not about stacking tools. It is about designing security as a coordinated system.
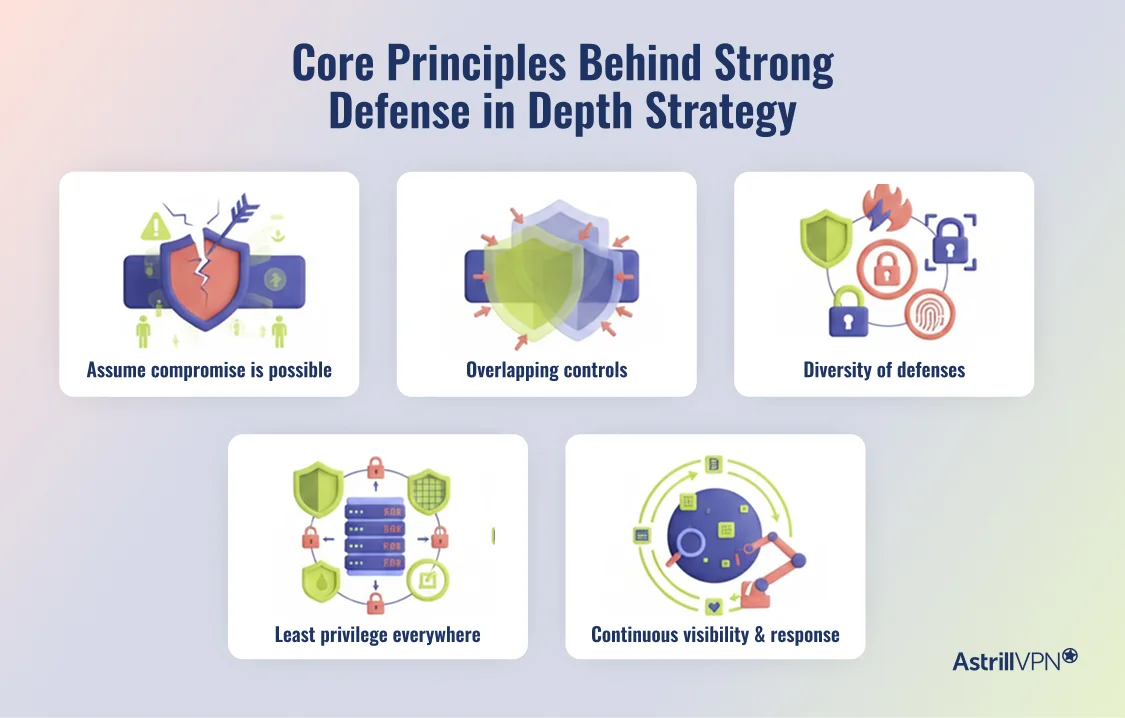
1. Assume compromise is possible
Every strong defense in depth strategy starts with the assumption that attackers will eventually get inside. This mindset drives investment in detection, segmentation, response, and recovery, not only prevention.
2. Overlapping controls
Each layer should reinforce others. When one fails, another should either block the attack or expose it.
3. Diversity of defenses
Using different types of controls reduces the chance that a single exploit or misconfiguration defeats everything.
4. Least privilege everywhere
Access should always be limited to what is necessary. Identity becomes a central pillar, not an afterthought.
5. Continuous visibility and response
Defense in depth is not static. Telemetry, monitoring, and feedback loops are critical for adapting to evolving threats.
Defense in Depth Strategy Explained
A defense in depth strategy defines how security controls are distributed across an environment and how they work together.
At a strategic level, it focuses on three outcomes:
- Prevention: Reducing the attack surface and blocking common threats
- Detection: Identifying suspicious behavior quickly
- Response and containment: Limiting blast radius and restoring operations
A mature strategy maps controls to risks. It aligns defenses with business-critical assets, compliance requirements, and realistic threat models.
Instead of asking “Which tools should we buy?”, strong strategies ask:
- What are our most valuable assets?
- How could they realistically be attacked?
- Where would an attacker move next?
- Which controls interrupt that path?
Layered Security and Its Role in Defense in Depth
Layered security refers to deploying protection mechanisms at multiple points within an environment. It is the structural foundation of defense in depth.
Layered security ensures that:
- Attacks are met with resistance at every stage
- Failures do not result in total compromise
- Security does not depend on one technology
Integrated Security: The Glue Between Layers
Integrated security means security layers do not operate in isolation. Instead, they exchange context, signals, and response actions.
Integrated security enables:
- Centralized visibility across layers
- Automated correlation of weak signals
- Coordinated response across systems
- Faster containment and remediation
For example:
- An endpoint alert can trigger network isolation
- An identity risk score can enforce step-up authentication
- A SIEM can orchestrate firewall and IAM changes
Layers of Defense in Depth
There is no single universal model, but strong defense in depth architectures consistently address the following layers.
1. Physical Security Layer
The physical layer protects the environment in which digital systems operate.
This includes:
- Controlled facility access
- Surveillance and monitoring
- Hardware protection
- Secure disposal of equipment
- Environmental controls
2. Network and Perimeter Security Layer
This layer governs how data moves and how systems communicate.
Key controls include:
- Firewalls and next-generation firewalls
- Intrusion detection and prevention systems
- Network segmentation and microsegmentation
- Secure remote access solutions
- DNS and traffic filtering
3. Identity, Access, and Endpoint Security Layer
Modern defense in depth strategies are identity-centric.
This layer includes:
- Identity and access management
- Multi-factor authentication
- Privileged access management
- Endpoint detection and response
- Device posture enforcement
4. Application and Data Security Layer
This layer protects how software behaves and how information is stored.
It includes:
- Secure application development practices
- Web and API protection
- Vulnerability management
- Encryption in transit and at rest
- Database monitoring and controls
- Data loss prevention
5. Administrative and Policy Layer
Technology alone does not create defense in depth.
This layer governs:
- Security policies and governance
- Risk management frameworks
- Incident response planning
- Compliance programs
- Employee security training
6. Detection, Response, and Resilience Layer
This layer ensures the organization can see and react.
It includes:
- Centralized logging and SIEM
- Security operations centers
- Threat intelligence
- Incident response workflows
- Backup and disaster recovery
- Business continuity planning
7. Modern Extensions of Defense in Depth
Today’s environments demand additional layers:
- Cloud and workload protection platforms
- Zero Trust architectures
- Secure access service edge
- Continuous posture management
- AI-assisted threat detection
How to Build an Effective Defense in Depth Strategy
Building a defense in depth strategy is an architectural exercise, not a procurement project.
Step 1: Identify critical assets
Understand which systems, data, and services are most valuable and most exposed.
Step 2: Map realistic threat paths
Analyze how attackers would likely attempt to reach those assets.
Step 3: Design layered control placement
Assign preventive, detective, and responsive controls to each stage of attack.
Step 4: Prioritize by risk
Not every layer needs equal investment. Focus on high-impact attack paths.
Step 5: Integrate controls
Ensure visibility, telemetry, and response mechanisms are connected.
Step 6: Validate continuously
Test assumptions through simulations, red teaming, and incident reviews.
Implementation OF Defense in Depth
Effective implementation focuses on coordination, not quantity.
Organizations should:
- Establish baseline security architecture
- Consolidate overlapping tooling where possible
- Centralize monitoring and response
- Automate containment where risk allows
- Build operational playbooks
- Train teams regularly
Measuring the Success of a Defense in Depth Strategy
You cannot improve what you cannot measure.
Key indicators include:
- Mean time to detect threats
- Mean time to respond and contain
- Lateral movement success rates
- Privilege misuse incidents
- Patch and exposure closure time
- Incident recurrence patterns
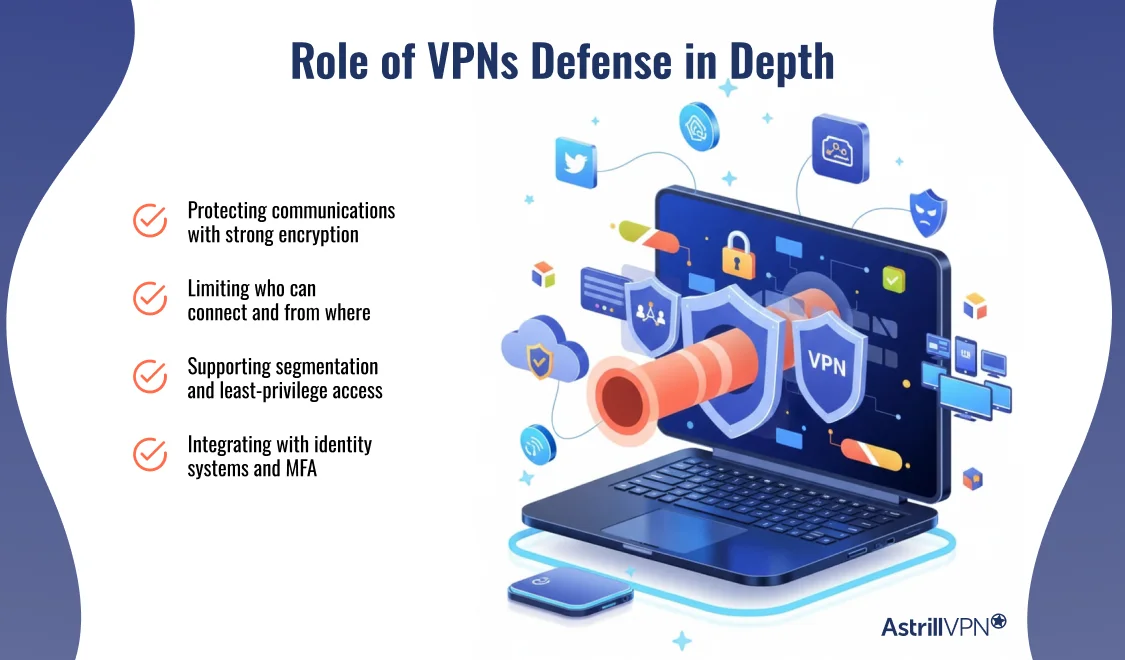
Role of VPNs in Defense in Depth
VPNs support defense in depth by securing data in transit and controlling remote access to internal systems.
They encrypt network traffic, preventing interception on public or untrusted networks, and act as a controlled entry point instead of exposing internal services directly to the internet.
Within a defense-in-depth strategy, VPNs strengthen the network security layer by:
- Protecting communications with strong encryption
- Limiting who can connect and from where
- Supporting segmentation and least-privilege access
- Integrating with identity systems and MFA
For example, business-grade VPN services like AstrillVPN are often used to secure remote connections and protect internal traffic flows as part of a broader layered security model.
AstrillVPN or any other VPNs do not stop malware, phishing, or insider threats on their own. Their role is to reduce exposure and secure connectivity, while other layers handle identity protection, endpoint security, monitoring, and response.
Defense in Depth vs Other Security Approaches
Modern frameworks do not replace Defense in depth. It supports them.
- Zero Trust strengthens defense in depth by enforcing continuous verification.
- Cloud-native security extends layered models into dynamic environments.
- Risk-based security prioritizes where layers are most needed.
Industry-Specific Considerations
Different sectors emphasize different layers.
- Healthcare focuses on data protection and access controls.
- Financial services emphasize segmentation, identity, and monitoring.
- Manufacturing prioritizes physical security and operational technology isolation.
- Cloud-first organizations concentrate on workload, identity, and posture management.
Common Mistakes That Weaken Defense in Depth
- Treating tools as layers without integration
- Overinvesting in perimeter controls while neglecting identity
- Flat networks with unrestricted internal trust
- Excessive complexity without operational clarity
- Lack of testing and feedback loops
Conclusion
Defense in depth is not about stacking defenses. It is about engineering resilience.
By combining layered security with integrated security, organizations create environments where attacks are expected, detected early, constrained quickly, and learned from continuously.
A strong defense-in-depth strategy turns security from a barrier into a living system that adapts as threats evolve.
FAQs
Layered security refers to placing multiple, independent security controls at different points in an environment (for example, firewalls, endpoint protection, identity controls, and data encryption). Its purpose is to ensure that if one layer fails, another can still provide protection.
Integrated security refers to how those layers work together. It focuses on connectivity between security tools so they can share data, correlate threats, and coordinate responses. Layered security provides structure. Integrated security provides intelligence and coordination.
Defense in depth is the overarching architectural strategy of using multiple layers of protection. Zero Trust is a modern model that strengthens defense in depth by enforcing continuous verification of users, devices, and workloads at every layer.
Zero Trust removes implicit trust inside networks, which historically weakened defense in depth. It enhances identity controls, segmentation, and access enforcement, making the layered defenses more adaptive and context-aware.
Multi-factor authentication strengthens defense in depth by adding a second independent verification layer to identity security.
Even if credentials are stolen through phishing or malware, MFA blocks attackers from accessing systems without the additional factor. This prevents a single point of failure at the login stage and significantly reduces the success of lateral movement and privilege escalation.
No. Defense in depth cannot prevent all cyberattacks. Its purpose is not absolute prevention. Its purpose is to reduce the likelihood of success, detect attacks earlier, limit damage, and enable faster containment and recovery.
Defense in depth accepts that some controls will fail. By distributing protection across layers and integrating detection and response, it ensures that no single breach becomes a total compromise.


No comments were posted yet