Spam vs. Phishing: Understand the Difference

Bisma Farrukh

Have you ever opened your inbox to find a message claiming you’ve won a million dollars in some lottery you never entered? Or maybe an urgent alert that your account has been hacked and needs to be verified immediately? If so, chances are you’ve been the target of spam or phishing emails. While the two terms are often used interchangeably, there are some key differences between spam and phishing you should understand. Knowing how to spot the difference between phishing and spam can help you avoid becoming the victim of fraud or identity theft. Read on to find out exactly what these shady practices are and how you can protect yourself.
Table of Contents
Defining Spam:
Spam is an unsolicited bulk email sent for commercial purposes. Usually, it’s trying to sell you something shady like knock-off handbags or pharmaceuticals.
Spam emails often have a few telltale signs:
- They have an urgent or exciting subject line, like “You’ve won a prize!” or “Act now, limited time offer!”
- The sender’s name and email address don’t match. “Totally Legit Company” sender@shadysite.com is a red flag.
- There are lots of exclamation points, spelling or grammar mistakes.
- There’s a link or download attachment from someone you don’t know.
Defining Phishing:
Phishing occurs when criminals impersonate a trusted source, such as your bank or credit card company, to trick you into giving them your personal information. They often send emails that look legitimate but contain malicious links or attachments.
Key Differences Between Spam and Phishing
Spamming and phishing are two common cyber threats, but they differ in some important ways:
1. Types
Spam refers to unsolicited bulk messages, usually commercial in nature, sent indiscriminately to many recipients. Phishing messages are crafted to target specific individuals or groups by impersonating a legitimate company or website to trick people into providing sensitive data like account numbers, passwords, or credit card numbers.
2. Nature of attack
Spam is annoying but typically harmless. Phishing, on the other hand, aims to steal personal information or install malware, so it can lead to identity theft, financial fraud, or other cybercrimes.
3. Identification
Spam is easy to spot because it often contains poor grammar, exaggerated claims, or urgent language trying to sell you something. Phishing emails are more sophisticated, closely imitating official communications from a reputable company to appear authentic and bait unsuspecting users into clicking malicious links or downloading attachments.
4. End goal
The sender of spam messages is usually trying to sell a dubious product or service to make money. The phisher’s goal is to access your sensitive data and accounts for criminal purposes like fraud or theft.
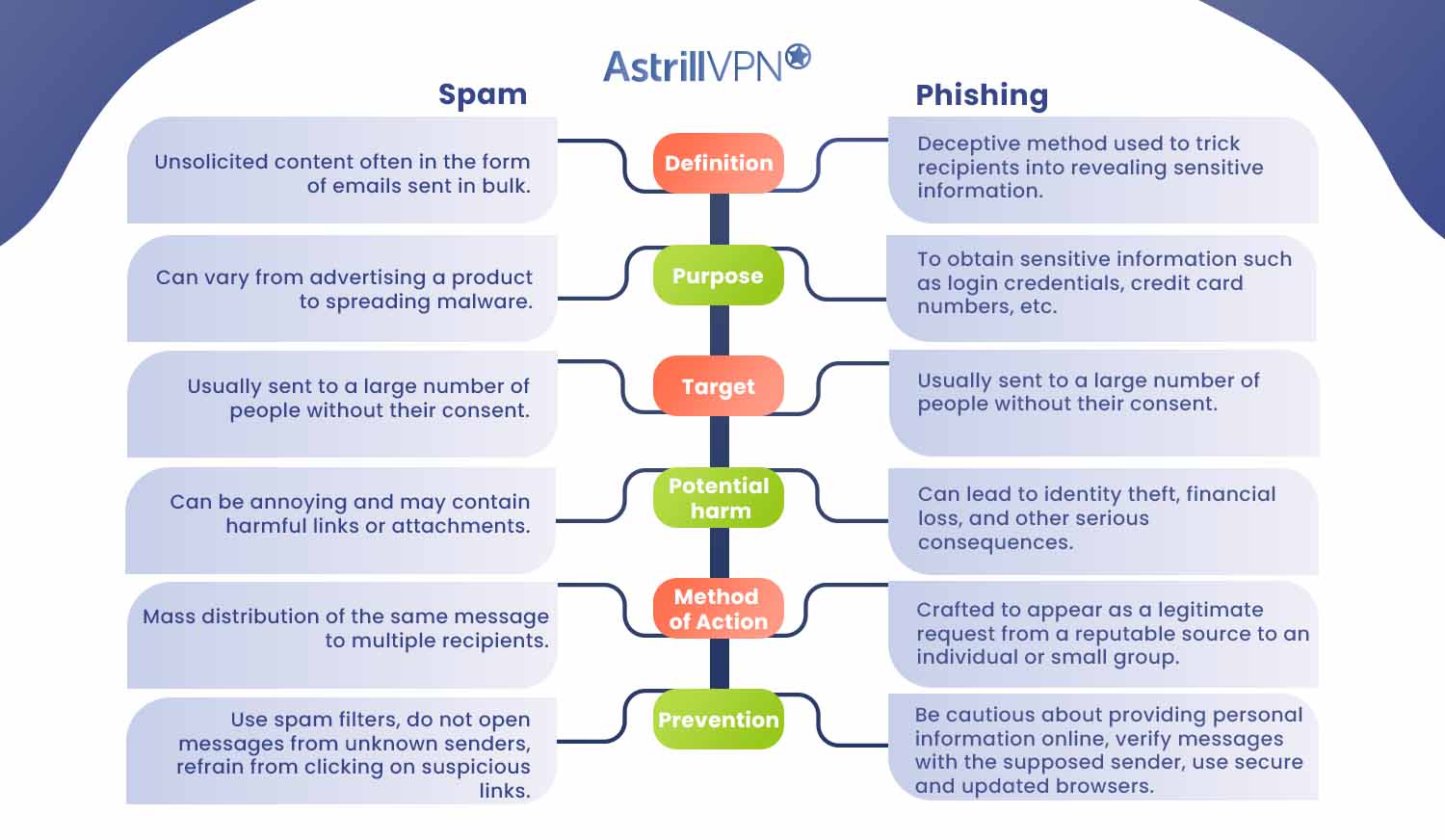
Detailed Difference of Spam vs Phishing
| Spam | Phishing | |
| Definition | Unsolicited content often in the form of emails sent in bulk. | Deceptive method used to trick recipients into revealing sensitive information. |
| Purpose | Can vary from advertising a product to spreading malware. | To obtain sensitive information such as login credentials, credit card numbers, etc. |
| Target | Usually sent to a large number of people without their consent. | Usually sent to a large number of people without their consent. |
| Potential harm | Can be annoying and may contain harmful links or attachments. | Can lead to identity theft, financial loss, and other serious consequences. |
| Method of Action | Mass distribution of the same message to multiple recipients. | Crafted to appear as a legitimate request from a reputable source to an individual or small group. |
| Prevention | Use spam filters, do not open messages from unknown senders, refrain from clicking on suspicious links. | Be cautious about providing personal information online, verify messages with the supposed sender, use secure and updated browsers. |
Does AstrillVPN Protect Against Spam and Phishing?
A VPN provides an encrypted tunnel for your Internet traffic, hiding your online activity and location. This does offer some protection against spam and phishing.
AstrillVPN helps protect you from spam and phishing in a few ways:
Filters and Blocks
AstrillVPN uses advanced spam filters to detect and block unwanted messages before they even reach your inbox. It analyzes incoming emails for common signs of spam like strange sender addresses or suspicious links and attachments. Anything suspicious gets marked as spam and sent to your spam folder.
AstrillVPN also actively blocks known phishing sites and malware hosts. If you accidentally click a phishing link or download a malicious file, AstrillVPN prevents your device from connecting to those threats. This adds an extra layer of protection when spam and phishing messages slip through.
Encryption
AstrillVPN uses strong encryption to secure all your online activity and communications. Even if spammers or phishers could see your internet traffic, they wouldn’t be ablfe to read it. Your emails, messages, passwords, and other sensitive data are hidden behind a veil of encryption.
In summary, AstrillVPN helps shield you from the dangers of spam, phishing, and online fraud through proactive blocking, strong encryption, and account security features like Kill Switch and Website filter. With AstrillVPN by your side, you can feel confident clicking, sharing, and communicating online.
FAQs
Many people confuse spam and phishing emails. Let’s clear up some common questions:
No, phishing emails themselves are not viruses. They are fraudulent messages designed to trick you into providing sensitive data or downloading malicious software. Phishing emails often contain links or attachments with viruses, but the email itself is not a virus.
Yes, phishing refers to scam emails that attempt to steal your personal information. Phishing emails are crafted to look like legitimate messages from companies you know, like your bank, credit card issuer or email provider. They try to trick you into entering account numbers, passwords, or clicking links that download malware.
Not exactly. Phishing emails are sent by cybercriminals to illegally obtain access to people’s accounts and personal data. The criminals who orchestrate phishing campaigns are hackers, but phishing itself refers to the scam messages they distribute, not the individuals.
Conclusion
Now you know the difference between spam and phishing and can spot each one before falling victim to their tricks. While technology has made communication more convenient, it’s also enabled new forms of deception. But forewarned is forearmed, right? Keep your guard up, trust your instincts, and don’t become another statistic. Outsmart the scammers and stay safe online. The spam and phishes of the world don’t stand a chance against an eagle-eyed, savvy person like yourself.

No comments were posted yet