What Is Hacking? A Beginner’s Guide to Cyber Intrusions

Arsalan Rathore

Unlike regular phishing, which targets random users, and spear phishing, which focuses on specific individuals, whaling phishing targets top executives, such as CEOs and CFOs. These attacks are highly personalized and often appear as legitimate internal communications, making them much more challenging to detect.
Recent data shows that whaling incidents are increasing in frequency and sophistication. In 2025, cybersecurity researchers observed a sharp increase in executive-targeted phishing emails, with AI-generated messages and voice impersonations being used to deceive decision-makers. One notable incident occurred in early 2025 when attackers used a deepfake video call to impersonate a company’s CFO, successfully tricking an employee into transferring over 25 million dollars to fraudulent accounts.
Whaling phishing is no longer a rare threat. It is a growing risk that can lead to severe financial and reputational damage if not adequately addressed. In this guide, we thoroughly explain what Whaling Phishing is and how to prevent it.
Table of Contents
What Is Hacking?
At its core, hacking refers to gaining unauthorized access to computer systems, networks, or digital devices. While the term often carries a negative connotation, it’s essential to recognize that not all hacking is malicious. The intent behind the intrusion and the methods employed play a significant role in categorizing hacking activities.
However, hacking isn’t always illegal or unethical. While black-hat hackers (the “bad guys”) break into systems for personal gain or to cause damage, white-hat hackers (the “good guys”) are ethical hackers who help strengthen cybersecurity by identifying and fixing weaknesses.
So, hacking, in its purest form, is simply problem-solving using unconventional digital methods. Whether it is good or bad depends entirely on the intent behind it.
How Does Hacking Work?
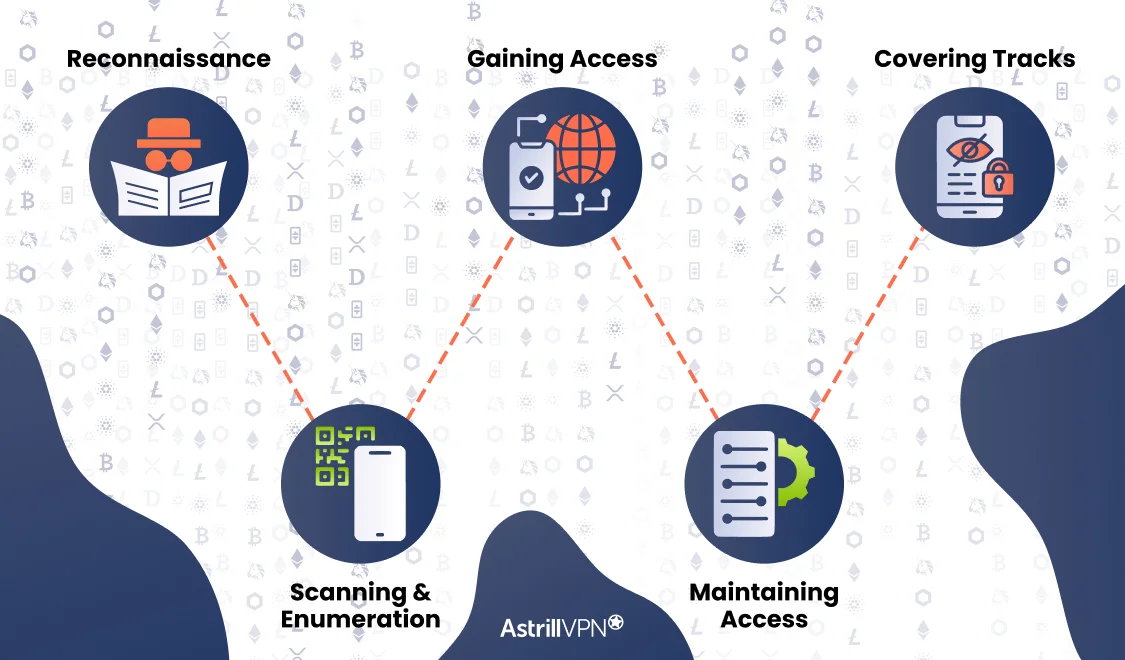
Hacking typically involves several stages:
1 Reconnaissance
Before an attack, hackers collect information about their target. This includes scanning IP addresses, ports, and services, or even social engineering tactics to gather personal data.
2. Scanning and Enumeration
Next, hackers probe the system for vulnerabilities. They may use tools like Nmap or Wireshark to map out network details and find potential entry points.
3. Gaining Access
Using discovered vulnerabilities, hackers try to infiltrate the system. Common techniques include exploiting software bugs, brute-force attacks, or phishing emails with malicious links.
4. Maintaining Access
Once inside, hackers often install backdoors or malware to ensure they can return later. This allows long-term control over the system or continuous data exfiltration.
5. Covering Tracks
To avoid detection, hackers may delete logs, alter timestamps, or install rootkits to stay hidden from system administrators or security software.
Types of Hackers
Not all hackers are bad. In fact, some are the very people helping companies stay safe from cyber attacks. Hackers are often categorized by “hat color” based on their intent:
1. White Hat Hackers (Ethical Hackers)
These are the good guys. They hack legally to find vulnerabilities in systems and fix them before malicious hackers can exploit them. Many work in cybersecurity or as penetration testers.
2. Black Hat Hackers (Crackers)
These are the malicious hackers. They break into systems illegally, often to steal data, plant viruses, or extort money. Think of cybercriminals or hackers behind ransomware attacks.
3. Gray Hat Hackers
They live in the gray area, sometimes acting without permission but without malicious intent. For example, a gray hat might hack into a system to expose a vulnerability, then notify the company about it.
Common Hacking Techniques
Here are some of the most common ways hackers operate:
- Phishing: Tricking people into revealing passwords or sensitive data by pretending to be someone they trust (often via fake emails or websites).
- Malware: Injecting malicious software such as viruses, worms, or ransomware into systems.
- SQL Injection: Exploiting vulnerabilities in databases through input fields (e.g., login forms) to extract or manipulate data.
- Denial of Service (DoS): Overloading a system or website with traffic to make it crash.
- Man-in-the-Middle Attacks: Intercepting data between two parties, often during online transactions.
Why Do Hackers Hack?
Various motivations drive hackers:
- Financial Gain: Many cyberattacks aim for monetary profit, such as stealing credit card information or deploying ransomware.
- Political or Social Activism: Hacktivists target organizations to promote political agendas or social causes.
- Corporate Espionage: Competing businesses may hack to steal trade secrets or proprietary information.
- Personal Vendettas: Disgruntled employees or individuals may hack to exact revenge.
- Intellectual Challenge: Some hackers are motivated by the thrill of overcoming security systems and solving complex problems.
What Do Hackers Do?
Once hackers infiltrate a system, their actions can vary:
- Data Theft: Stealing sensitive information like personal data, financial records, or intellectual property.
- System Disruption: Launching attacks that cause system outages or degrade performance.
- Ransomware Deployment: Encrypting data and demanding payment for its release.
- Botnet Creation: Using compromised systems to form networks that can be used for further attacks.
- Selling Information: Trading stolen data on the dark web to other criminals.
Emerging Hacking Trends in 2025
The threat landscape in 2025 is undergoing significant shifts. Cyber‑attackers are adapting with new techniques, tools, and targets. Understanding these changes is critical to staying ahead. Here are the key trends:
1. AI and Automation in Cyber Offense
Attackers are turning to generative AI and other automation tools to scale up their operations, craft more convincing social engineering attacks, and reduce the need for deep technical skills. Research indicates that by 2025, “anyone with access” to these tools may launch sophisticated malware or phishing campaigns.
2. Credential Theft and Identity‑Based Attacks
The value of stolen credentials continues to rise. Large‑scale harvesting of logins, access tokens, and machine identities fuels identity‑based intrusions. Cloud-environment statistics indicate that credential and identity compromise are the leading entry points.
3. Ransomware‑as‑a‑Service (RaaS) and Data Extortion
Rather than just encrypting systems, many attackers now also threaten to publish stolen data. The RaaS market has matured, making high‑impact ransomware accessible to less‑skilled threat actors. Smaller organisations with weaker defences are becoming prime targets.
4. Cloud, SaaS, and Supply‑Chain Exploits
As enterprises rely more on cloud services, SaaS platforms, and third-party supply chains become high-value targets for cyberattacks. Misconfigurations, excessive permissions, and unmanaged machine identities are significant weaknesses.
5. Nation‑State and Hybrid Threats Targeting Infrastructure
State-backed groups and criminal alliances are moving beyond espionage, increasingly targeting critical infrastructure, physical processes, and hybrid warfare scenarios. These threats are systemic, long‑term, and often less visible.
How to Tell If You’ve Been Hacked
1. Unusual Account Activity
Look for logins from unknown locations, unexpected password reset emails, or multi-factor authentication prompts you did not initiate. These are often the first signs that your credentials may have been compromised.
2. Strange Device Behavior
Check for unfamiliar software, applications, or processes running on your devices. Sudden slowdowns, crashes, or frequent pop-ups can indicate malware or unauthorized access.
3. Suspicious Messages or Social Media Activity
If your contacts receive emails or messages from you that you did not send, or if unusual posts appear on your social media accounts, your accounts may have been hacked.
4. Compromised Files
Encrypted, renamed, missing, or corrupted files can signal ransomware or other malicious activity. Ransom notes or demands for payment are a clear red flag.
5. Network and DNS Irregularities
Unexpected changes to your DNS settings, network configurations, or unusual outbound network traffic may indicate a breach at the network level.
6. Immediate Actions to Take
If you suspect a hack, disconnect from the internet immediately, change passwords from a secure device, enable multi-factor authentication, and run a thorough malware scan. For businesses, professional incident response is recommended.
Hacking Examples
To truly understand hacking, it helps to look at some real-world examples from recent years:
1. Colonial Pipeline Attack (2021)
A ransomware group called DarkSide shut down one of the largest fuel pipelines in the U.S., causing widespread panic and fuel shortages.
2. CyberAv3ngers (2023–2024)
This Iranian-linked group launched cyberattacks targeting water and power infrastructure in the U.S. and Israel using default login credentials and weak passwords.
3. TraderTraitor Attacks (2025)
North Korean hackers used phishing and malware to steal over $1.5 billion in cryptocurrency from major trading platforms, such as Bybit.
4. SolarWinds Breach (2020)
A highly sophisticated Russian-led cyber-espionage campaign infiltrated U.S. federal agencies through compromised software updates, exposing thousands of networks.
Recent Hacking Statistics (2024–2025)
- $10.5 trillion: Projected global cost of cybercrime by 2025 (Cybersecurity Ventures)
- 2,200 cyberattacks occur daily worldwide, on average (University of Maryland)
- 95% of data breaches are caused by human error (IBM)
- 68% of hackers say they hack for fun or challenge, while 53% do it for financial gain (HackerOne Survey)
These numbers reveal just how prevalent and impactful hacking has become in the digital age.
How to Prevent Hacking?
Protecting against hacking involves a combination of technical measures and user awareness:
- Use Strong Passwords: Employ complex, unique passwords for each account.
- Use a VPN: With a VPN, neither hackers nor your internet service provider can track what you’re doing online, so you can browse, shop, and stream with peace of mind-no matter where you connect.
- Enable Multi-Factor Authentication (MFA): This adds an extra layer of security by requiring additional verification.
- Regular Software Updates: Ensure systems and applications are up-to-date to patch known vulnerabilities.
- Educate Users: Training individuals to recognize phishing attempts and other social engineering tactics.
- Implement Firewalls and Antivirus Software: Use security tools to detect and block malicious activities.
- Backup Data: Regularly back up critical information to recover from potential attacks.
Conclusion
As our dependence on technology continues to grow, so does the importance of understanding the risks associated with it. Hacking is no longer a distant concept reserved for movies or tech forums, it’s a real, evolving threat that affects individuals, businesses, and governments alike. From simple phishing emails to complex state-sponsored cyberattacks, hackers are becoming more sophisticated, and their motivations more varied.
In today’s digital world, awareness is your first line of defense. Stay informed, stay alert, and take action to protect your personal and professional data. Hacking may be a part of our digital reality, but with the right knowledge and tools, you can stay one step ahead.
FAQs
Hacking becomes illegal when it involves unauthorized access to systems, theft of data, or causing harm. However, ethical hacking, conducted with permission to identify vulnerabilities, is legal and beneficial.
While achieving complete prevention is challenging, implementing robust security measures significantly reduces the risk of successful hacks.
Ethical hacking involves authorized systems testing to identify and fix vulnerabilities, often performed by cybersecurity professionals.
Use strong, unique passwords, enable MFA, be cautious with personal information online, and keep your devices updated with the latest security patches.


No comments were posted yet