What Is a Replay Attack? How It Works & How to Prevent It

Bisma Farrukh
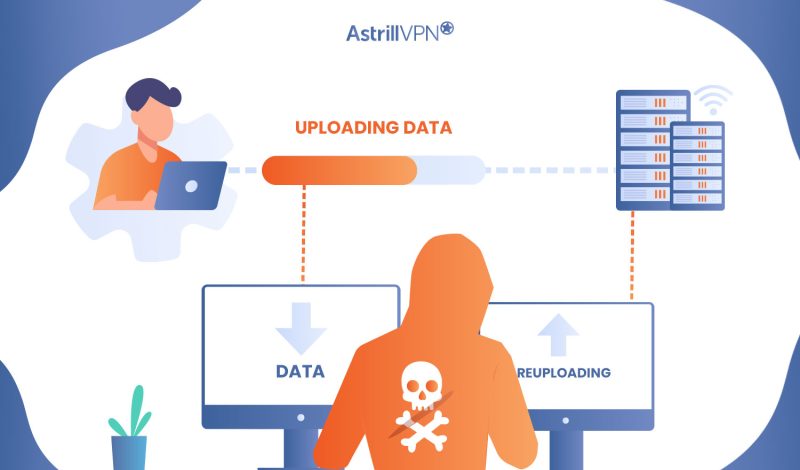
In the world of cybersecurity today, there are many different attack vectors to be aware of. One relatively common type is the replay attack. It sounds like something out of a sci-fi movie, but essentially, it’s when someone tries to “replay” a valid request or transaction on the web in order to gain access to sensitive data or resources. But what makes this type of attack so difficult to defend against,, and how can you avoid these kinds of threats?
In the study, researchers discovered that 51% of the tested devices lacked local connectivity, making them fall short of essential reliability and safety standards. Among the remaining devices, a concerning 75% were found to be vulnerable to replay attacks. A notable case involved a popular garage door opener that failed to implement adequate local security protections, leaving it open to unauthorized access.
We’re here to answer all your questions and provide a technical overview of what you need to know about replay attacks so that you can keep your systems secure. In this article, we’ll discuss what a replay attack is, how they work, and what steps you should take to prevent them.
Table of Contents
What is a Replay Attack?
A replay attack in cybersecurity is a type of cyberattack in which malicious actors intercept and re-transmit valid data to gain access to systems or networks. It’s a way for bad actors to use legitimate data from one session and replay it during another session when the user should not have access.
Replay attacks are especially dangerous, as they can go undetected for long periods as the attacker uses valid credentials. By replaying the valid data many times, the attacker can access valuable information and resources.
Replay attacks are becoming more and more difficult to defend against due to the sophistication of attackers. Relying solely on manual detection methods is no longer viable, as attackers are able to bypass these systems by sending data in random patterns that do not conform to known patterns of attack.
How Do Replay Attacks Work?
Replay attacks exploit the trust that systems place in previously validated data transmissions. Essentially, an attacker intercepts a legitimate transaction like a login session, financial exchange, or IoT command and resends it to impersonate the original request and gain unauthorized access.
Here is the typical flow:
- Initial Eavesdropping: The attacker captures valid network packets during a normal communication.
- Replaying the Data: These captured packets authentication tokens, session requests, IoT commands are resent, unmodified or slightly tweaked, tricking the recipient into performing the same action again.
- Unauthorized Access: This method allows attackers to bypass authentication, escalate privileges, or replay commands to systems without needing credentials.
- Exploitation Phase: With elevated privileges, they can install malware, exfiltrate data, create backdoors, or manipulate system behavior.
- Covering Their Tracks: Many attackers delete logs or deploy rootkits to evade detection after successful exploitation.
Types of Replay Attacks: Session Replay, Wireless Replay & More
Now let’s talk about the different types of reply attacks.
1. Session Replay Attack
A session replay attack (also known as a man in the middle attack) is when an attacker intercepts a data transmission between two computers, records the information, and then uses it to access the target’s system without stealing the data. For example, If you were to make a purchase online, someone with access to your data could “replay” it and make another purchase without you knowing.

2. Wireless Replay Attack
A wireless replay attack occurs when someone intercepts wireless signals and replays them in order to gain access to a system or network. This type of attack is particularly dangerous because it’s almost impossible to detect.

3. ARP Reply Attack
An ARP reply attack is when an attacker sends fake ARP messages over a network in order to redirect traffic from one computer to another. This means that any data sent from one system can be intercepted by another before it reaches its intended destination.

Real World Examples of Replay Attacks
Replay attacks can and do happen in the real world. One replay attack example that comes to mind is during the 2016 US Presidential Elections. A Canadian security firm, Citizen Lab, observed a massive replay attack campaign targeting Georgian voters and the Georgian government’s pro-Western stance.
Citizen Lab published a report on the attack which showed that malicious actors sent email phishing messages to 3,000 individual targets in Georgia. The attackers used malicious links sent in those emails to launch a replay attack on the targeted individuals and their organizations.
The attackers also engaged in an elaborate ‘watering hole’ strategy; a technique used to infect unsuspecting users by redirecting them to infected URLs or websites containing malware. The attackers crafted baited content that would attract Georgian voters, thereby increasing the potential damage of their campaign as more victims would become exposed to their threats from fake news stories, political pamplets, and other forms of propaganda that they spread via social media channels like Facebook and Twitter.
What is replay resistant authentication?
It’s an authentication process that makes sure that a request, message or data package can’t be reused. Basically, if someone were to intercept the data and try to resubmit it or use it again, they wouldn’t be able to do so and that helps protect your system from malicious actors.
Replay resistant authentication is essential for keeping your systems safe from malicious actors trying to take advantage of vulnerabilities so if you want help beefing up your security protocols, implementing this could be an important step.
How can a VPN prevent replay attack?
You may be wondering how you can prevent a replay attack. One way is to use a virtual private network (VPN). A VPN can protect you by adding two levels of encryption to your data so it’s less likely to be intercepted and misused. AstrillVPN has features that can provide an even greater level of protection.
For example, the Port forwarding feature can help protect you from a replay attack by encrypting all incoming and outgoing traffic with separate port numbers on the VPN server, reducing the risk of interception. Additionally, Astrill’s logging policy ensures that none of your personal information or usage data is stored helping to reduce the likelihood of your connection being monitored or intercepted.
Last but not least, Astrill offers different protocols for different encryption methods that are constantly updated so attackers have difficulty breaking through them. These protocols are also combined with application-level security measures that further increase safety from hackers and attackers trying to execute a replay attack on your device.
How to Prevent Replay Attacks? Replay Resistant Authentication Methods
Replay attack prevention is a serious issue as these attacks can cause damage to companies and their customers, so it’s essential that businesses take appropriate measures to protect against them. Here are some methods of authentication that are particularly resilient against such attacks.
Nonce
A nonce (number used once) can be used to make sure that each authentication message is unique every time it’s sent. This prevents the attacker from re-sending a captured message, as they can’t know the value of the nonce, and the verification will fail.
Time-based one-time password (TOTP)
TOTP is a form of two-factor authentication. It requires two pieces of information: a one-time password generated using a cryptographic hash function, as well as an ever-changing piece of information like the current date and time or an incrementing counter. The server must verify both pieces of information within a predefined time window to ensure that any messages sent are not replays.
Random Challenge-Response Protocols
Random challenge-response protocols drastically reduce the risk of replay attacks due to their multi-level challenge process. The server sends a random challenge to the client which it must respond to correctly in order for the authentication process to succeed. Because the challenge is always random, it prevents attackers from copying and replaying requests they have intercepted.
Single Use Secure Tokens
Single use secure tokens are a form of authentication where a one-time token is generated by the server and sent to the user as part of an authentication request. When received by the user, they enter this token in order to gain access. Since single use tokens are only valid for one session, they cannot be reused or replayed by attackers making this an effective way of protecting against replay attacks.
Time Stamps
Using timestamping with hash values prevents attackers from replaying previously intercepted requests because each request must include a time stamp with a unique hash value. When combined with other methods like digital signatures and public key encryption, time stamps provide an additional layer of security that can help stop replay attacks in their tracks.
Tools Used to Carry Out Replay Attacks
Generally, these tools include packet sniffers and traffic generation tools, along with other tools that can be used for capturing and resending data.
Packet Sniffers
A packet sniffer is a tool used to capture network packets flowing on an available network. These packets are essentially transmitted data in their raw form, and the packet sniffer can capture them, read them and analyze them. Packet sniffers are often used by hackers to identify vulnerability related to the transmission of sensitive information over the network.
Traffic Generation Tools
Traffic generation tools are essentially programs which generate random amounts of unrelated traffic to interfere with the flow of legitimate packets being sent over the network. This makes it difficult for any reactive security measures in place to block illegitimate traffic.
Other Tools
Other than packet sniffers and traffic generation tools, hackers may also make use of various other tools such as automated clickers or form fillers which can be used for automatic capture or injection of targeted data into forms on websites with malicious intent.
Conclusion
In sum, replay attacks are a form of attack in which an attacker captures and re-transmits data previously sent by a legitimate user in hopes of deceiving a system into believing it is a valid request. These attacks can be conducted in both wired and wireless networks and can have serious consequences, including fraud and data theft.
Organizations should make sure they have sufficient security measures in place to prevent replay attacks. This includes ensuring that authentication systems are secure and using technologies such as alarm systems, replay-resistant authentication protocols and network traffic monitoring tools. By understanding replay attacks and putting the right security controls in place, organizations can protect themselves from this type of attack.
FAQs
You may still have many questions about what a replay attack is, which we’ll try to answer here.
A man-in-the-middle attack is the interception of the exchanged data, where an attacker can change the values in real time and alter it however they wish. The main difference with a replay attack is that it works by simply replaying the previously intercepted data without further manipulation; meaning that no malicious alterations are made to the data.
No, while they both rely on sending high volumes of traffic to overwhelm resources, a Replay Attack is focused on resending valid requests even if those requests were originally sent unbeknownst to other users while DoS (denial of service) overloads resources by sending invalid requests.
Yes. Replay attacks are usually routed through automated scripts, or simple manual copies/pastes of previously sent requests that are then executed multiple times.


No comments were posted yet