What is Whaling Phishing? Threats and Prevention Methods [Updated]
![What is Whaling Phishing? Threats and Prevention Methods [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/07/What-is-Whale-Phishing-Threats-and-Prevention-Methods-800x444.jpg)
Table of Contents
What is Whaling Phishing?
A whale phishing attack is a specific type of phishing attack aimed at senior Managers and Executives of a company. The cybercriminal pretends to be a trusted and legitimate entity, all to lure the victim into sharing sensitive information or transferring funds to a fraudulent account.
It is also known as CEO fraud, a spear phishing email attack. The attacker masquerades as a CEO and tricks people into transferring money or sharing confidential information. They trick people into transferring money into the attacker’s account.
While phishing scams target individuals randomly, and spear phishing scams target specific individuals, whaling attacks take it one step further by targeting the critical people of an organization and doing it in a way that seems as if their mode of communication is legitimate.
The victim could receive an email from the attacker thinking it’s legitimate and from the higher-ups, but it’s not. In whaling attacks, hackers utilize social engineering techniques to trick users into providing bank details, confidential HR information, employee information, and credit card details and trick people into sending vast sums of money, believing the hackers to be the company’s CEO.
How Do Whaling Attacks Work?
Whaling Attacks work using this step by step process:
Research on the Targets

The attacker first conducts thorough research on the key players of the targeted organization and their executives. They collect information from various sources, including social media and the company’s website, to better understand the company culture and the targeted person’s roles and responsibilities.
Writing a Convincing Message

Attackers then craft a convincing email that appears to come from a legitimate source and someone that the victim trusts. They use social engineering methods to create a sense of urgency regarding their demand. They do this by using persuasive language and convincing the attacker to do things needing immediate action.
Spoofing

To ensure they look credible, hackers spoof emails and phone addresses to make it seem like they are communicating from a legitimate source. They can impersonate the characteristics of the company’s CEO or Executive to deceive the target.
Manipulating the Target

The attackers can exploit the vulnerability of the attacker by playing on their trust. Once the victim falls into the trap, they can ask the victim to share personal information or install Malware on their device to steal confidential data.
The Fallout of a Whaling Attack

If the phishing attempt is successful, the attacker gains access to confidential information, can hack into the target’s account, and even steal the financial assets of an organization. Not only does the victim experience financial loss, but the company’s reputation also gets damaged.
Types of Whaling Attacks
Here are the most common types of Whaling Attacks:
- Spear phishing: Spear phishing is a personalized form of phishing where the attacker pretends to be a CEO or a Senior Executive and crafts a message or personal email to the attacker, making it seem like they’re communicating from a trusted source. The attacker aims to get the target to reveal sensitive information or financial details.
- Social Engineering: Whaling with Social Engineering involves the attackers using manipulation and psychological tactics to build a relationship with the attacker and gain their trust, collect information about their activities, and then use that information to plan their convincing phishing attempts.
- Malware Attacks: The attacker can send an email that contains a malicious link. Once the target clicks on it, thinking it’s legitimate, it infects their device with Malware. It can enable the attacker to access sensitive and confidential data.
- CEO Fraud: CEO fraud is a type of Whale phishing that only targets the company’s higher-ups or senior executives. The attackers masquerade as the CEO or Senior Management Personnel and send fake emails to employees, asking them to disclose sensitive information or make Wire transfers.
Whale phishing attacks require a great deal of planning and research to make them convincing and for it to be successful. Individuals and companies must work together to stay vigilant, be aware of such attacks, and take the necessary security measures to protect themselves against phishing attempts.
What Do Attackers Target the Higher Ups and Executives of the Company?
According to the 2023 Verizon DBIR, social engineering tactics, like phishing and whaling, have increased compared to the previous year because of pretexting, commonly used in Business Email Compromise (BEC). There are various reasons why attackers choose to target the executives of a company. Some of the main reasons include:
- They Hold A Position of Power: The executives and the board of directors of a company hold the key to all of the essential documents of a company, and they’re the only ones who have the privilege of editing, deleting, and moving vast amounts of data that the company deems to be sensitive and confidential. Executives also have the higher authority to authorize different actions, like choosing different vendors and transferring money.
- Financial Gain: Executives often have a wealth of financial resources, making them the ideal targets for attackers who are looking for ransom payments or financial fraud. High-ranking personnel have access to company accounts which are used for fraudulent transactions.
- Corporate Espionage: Competitors, foreign entities, and attackers can target executives so that they can gain insights about the company’s strategy, product developments, and other deals. This information can help attackers and competitors undermine the company’s position in the market.
- Network Access: Executives often have privileged access to the company’s internal networks and systems. Compromising all their accounts allows attackers to gain a foothold inside the corporate network, allowing them to move laterally and access other sensitive assets.
Examples of Whale Phishing Attacks
- In 2016, the social media company Snapchat fell victim to a Whale Phishing scam when an employee from the Payroll team got an email from an attacker pretending to be the CEO of Snapchat, Evan Spiegel. The employee mistakenly sent over some employees’ payroll information, thinking the CEO was asking for them. Unfortunately, the employee fell for the scam, leading to the hacker exposing the information for the entire world to see.
- In 2016, an employee of Seagate Technology, a data storage company, also became a victim of a Whaling attack. The attacker masqueraded as the company’s CEO and requested to transfer current and past employees’ confidential and sensitive W-2 tax documents. The employee complied with the demand, and as a result, the personal data of over 10,000 employees had gotten exposed.
- Mattel, a multinational toy manufacturing company, was also a target of the Whaling attacks in 2015. The attacker posed as the company’s CEO and tricked a finance executive through phishing emails into sending him 3 million dollars on a fraudulent account. The attack highlighted that even large and well-established companies could fall prey to such targeted attacks.
How Can You Detect A Whaling Attack?
- The email is sent from an unusual sender or email address. Although the email addresses are very similar to the ones of the original sender, they still have slight variations and misspellings. Be on the lookout for those.
- Whaling attacks create a sense of urgency and require immediate action. Be careful if the email asks you to take quick action or asks you to do something within a specific time frame.
- Whaling attacks typically ask for login credentials, sensitive information, or other confidential data, such as financial details. If you get such requests, verify the email before giving away such information.
- Whaling attack emails may have poor grammar or spelling mistakes. These errors can indicate that it’s a fake email. It could be possible that the attacker isn’t a native speaker of the language they’re using in their email.
- If you are sent links and attachments and find them suspicious, do not click on them until you’ve verified that it’s coming from a legitimate source. Clicking on these suspicious links can lead to your computer devices getting infected with Malware which is the attacker’s goal.
What Are The Consequences of Whaling Attacks?
Whaling attacks cause harm to organizations and individuals alike. Whaling attacks can lead to the theft of your personal and financial information. The attackers can use your private information to commit credit card fraud or create accounts under your name.
If you’re a victim of a phishing scam where your device gets infected with Malware, you could lose access to your device and your files. If your business is a victim of Whaling attacks, it would be a costly endeavor to recover from that, and it would also lead to a loss of productivity for your business. Whaling attacks have resulted in businesses losing millions of dollars.
It can also negatively impact the image of businesses and organizations because it would raise concerns over their ability to protect their data and the privacy and security of their customers. It can also lead to legal repercussions for companies since Data Protection laws require that companies safeguard personal information. Data breaches lead to fines, investigations as well as legal consequences.
Another negative consequence for businesses is that it results in a loss of trust and loyalty of their customers. If the customer’s personal information gets compromised due to a data breach, they would be unwilling to be associated with the company again. Having a bad rapport with customers can lead to enormous fallouts for a business.
How Is a Whaling Attack Different from Spear Phishing?
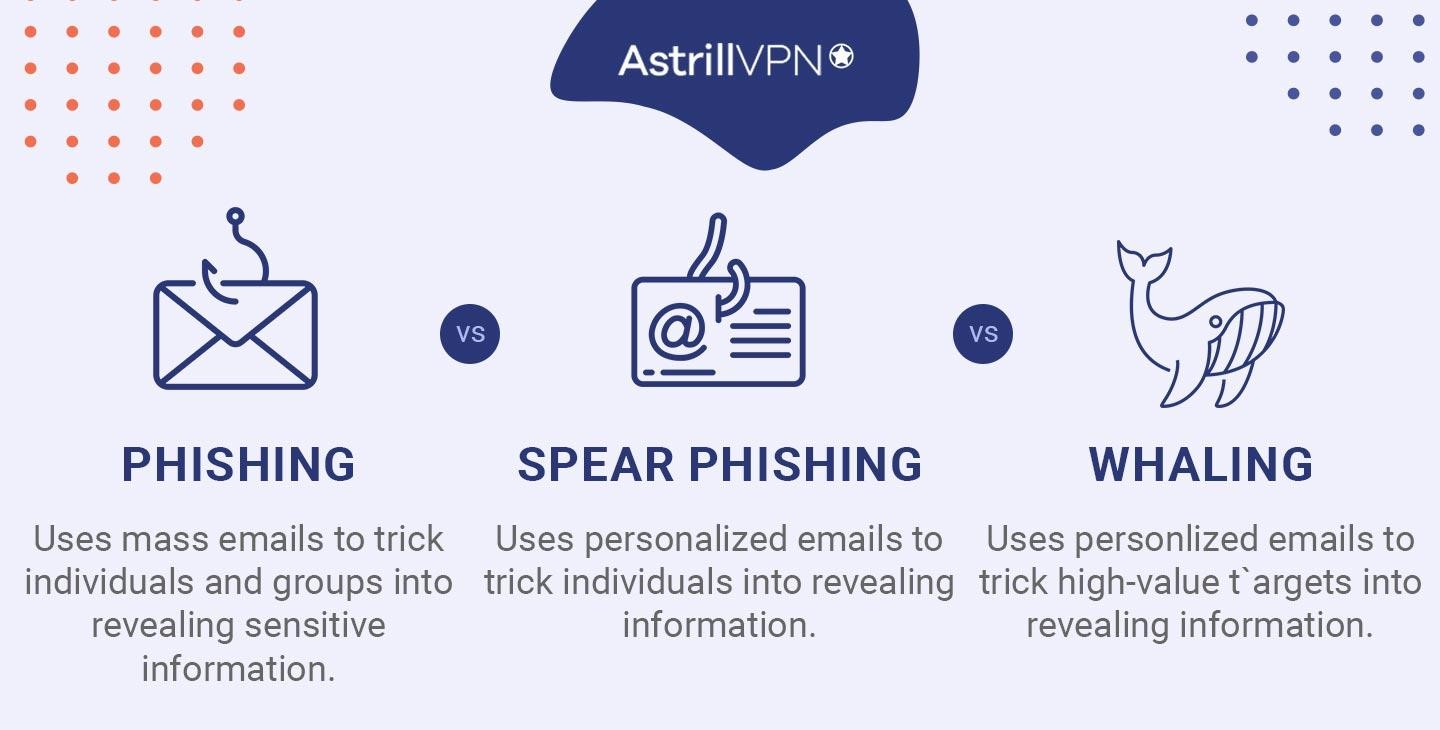
Whaling attacks and Spear Phishing are similar in that they are both targeted phishing attacks. However, the difference is in the people they plan to attack. Whaling attacks target high-profile people such as CEOs, government officials, and senior executives. Spear phishing, on the other hand, targets individuals not strictly limited to high-profile individuals and can include employees of a specific organization or members from a particular community.
Whaling attacks are much more personalized since much time and effort gets spent researching and collecting the target’s information and their activities and relationships. There is also a level of personalization in spear phishing, but it is not as intense as Whaling. A spear-phishing attempt would be crafting a convincing email to a target that shares some of their details to make it look more authentic.
Whaling attacks are mainly carried out for financial gains. The attacker can deceive the targets into making fraudulent payments or sharing confidential financial information. Spear phishing attempts get made for a wide variety of purposes. It can get used to gain access to someone’s login credentials, spread Malware or collect sensitive information. The goals may differ depending on the intentions of the attacker.
How To Prevent Whaling Attacks
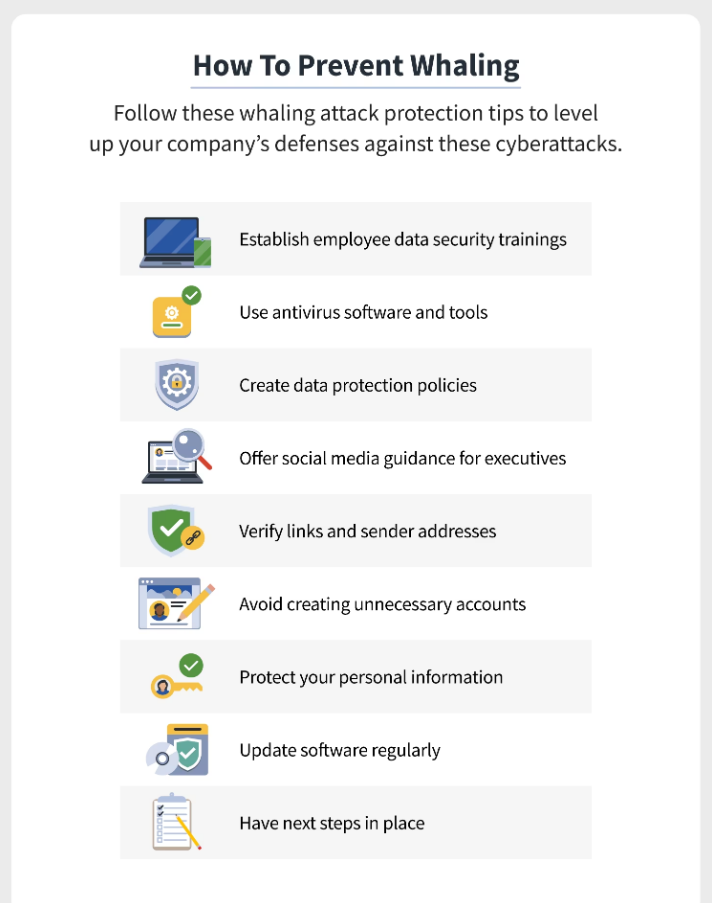
Preventing Whaling Attacks is all about implementing robust security measures, educating employees, and for the organization to remain vigilant and aware of these attacks. Let’s go over the prevention methods in detail.
Educating Your Employees
Provide detailed training to employees, especially those in high-profile or managerial positions and those with access to sensitive data. Companies should train them to identify phishing attempts quickly, as well as identify social engineering techniques that many attackers use. Lastly, employees should get trained to verify the reliability of emails and messages from attackers before taking action.
Enhance Email Security
Employ the most effective email security features like spam filters and email authentication protocols like (SPF, DKIM, and DMARC). These protective measures can help block and detect phishing emails which would make whaling attacks ineffective. They should also quickly verify urgent emails with the person who supposedly sent them. Attackers create a sense of urgency to get what they want, so any email of that nature should get verified immediately.
Safe Social Media Practices
Since CEOs and other executives are often the targets of Whaling Attacks, they should keep their social media profiles private. The attackers always go to social media to find personal information about their targets and use this information to trick and deceive people. If their social media profiles remain private, the attackers cannot find much information on their targets.
Implement Multi-factor Authentication
Make it mandatory to use Multi-factor Authentication (MFA) when accessing email accounts, sensitive data, or any critical systems. MFA provides an extra layer of security and requires users to provide multiple verification methods, such as sending an OTP (one-time password) to their mobile device. It prevents attackers from gaining unauthorized access.
Flag External Emails
Another way to spot a spoofed or fake email is to check if the email was sent from outside the company’s network. Companies should make it a policy to flag any email from outside their network. Suppose an email requires you to send over sensitive information or open an attachment you find fishy or need you to take immediate action. In that case, you should flag the email for further investigation.
Staying Informed & Regularly Updating Your Systems
Companies and individuals should stay informed about the latest phishing trends and techniques and keep a lookout for any recent whaling attacks. It will help them remain vigilant and address any emerging threats promptly. They should keep themselves updated with the best security practices.
You should also ensure that your software, hardware, and applications are updated frequently and have the latest security patches. You should regularly update anti-virus and anti-malware software to protect yourself against phishing attempts.
How AstrillVPN Can Help You Protect Against Whaling Attacks
AstrillVPN encrypts your internet traffic and masks your IP address, keeping your data safe and secure and maintaining anonymity. It would make it difficult for cybercriminals to intercept your data. It will prevent them from accessing sensitive data such as passwords, bank details, or credit card information.
Although VPNs aren’t an immediate solution to protect against Whaling attacks, you can install AstrillVPN to protect yourself from cyberattacks and phishing attempts, making it difficult for any third party to intercept your data.
Wrapping Up
Whaling Attacks can cause a lot of damage to individuals and organizations. Once you fall for a Whaling Attack, you can compromise your confidential data, and businesses can lose millions of dollars, leading to legal repercussions.
By identifying and training yourself to identify the signs of a Whaling attack early on and implementing security measures, you can thwart a Whaling attack attempt from the onset.
Frequently Asked Questions (FAQs)
There are various types of whaling attacks, and the three significant types include CEO fraud, Spear phishing, and using Social Engineering techniques.
A cyber-criminal can craft a well-written and convincing email asking you to click on a popular website link. However, the website looks like the original, so the attacker can steal the data when the user adds in their login details or other personal information.
It is a phishing attempt on an individual by someone pretending to be the CEO of a company or any other authoritative entity to scam someone.
It is a type of cyberattack where the attacker clones or copies a legitimate email to spread Malware. Hackers intercept the message and modify it before sending it to the victim.
It is a social engineering attack where the attacker tricks the victim by making an offer or reward or giving false promises. Still, once the victim falls for the trap, they use it to spread Malware to their device to steal sensitive and confidential information.
They target high-profile individuals since they can access financial resources and other sensitive data. The attackers will use a whaling attack to masquerade the CEO or senior executive, then craft a compelling email asking the employees to share sensitive information with them. The employee will comply since they believe the CEO demands them to share confidential details or transfer money to their fraudulent accounts.


No comments were posted yet