Blogs Posted by Bisma
Cyber threats are evolving faster than ever, and one of the most challenging forms of malware security teams face today is polymorphic malware. Unlike traditional malware that uses a fixed code structure, polymorphic malware continuously changes its appearance, making detection extremely difficult. This ability to mutate allows it to bypass signature-based antivirus tools and remain […]
Digital payments are everywhere, from buying coffee to shopping online, and Apple Pay has become one of the most popular options. But with rising cybercrime, scams, and data breaches, a common question keeps popping up: Is Apple Pay safe? The short answer is yes, Apple Pay is considered one of the most secure payment methods […]
In an era where online privacy and data security are top concerns for users worldwide, the choice of web browser matters more than ever. With major browsers like Chrome, Firefox, and Safari dominating the market, Brave Browser has emerged as a privacy-focused alternative. But is it really safe? Does it protect your data better than […]
As artificial intelligence systems, huge language models (LLMs), become deeply integrated into applications, chatbots, and enterprise workflows, new security threats are emerging alongside their rapid adoption. One of the most concerning and least understood of these threats is prompt injection. Unlike traditional cyberattacks that target code or infrastructure, prompt injection attacks exploit how AI models […]
PBS has long been a trusted source for thoughtful documentaries, investigative journalism, and educational programming. But if you travel abroad or live outside the United States, access can disappear overnight. Episodes that streamed without issue at home suddenly become unavailable, even though PBS content is free to watch and supported by public funding. This happens […]
Instagram has introduced Vanish Mode to address privacy concerns among social media users. This feature gives individuals greater control over their messaging by enabling temporary, disappearing chats that mirror the ephemeral nature of in-person conversations. This guide will delve into the functionality and purpose of Instagram’s Vanish Mode, answering frequently asked questions about this privacy-oriented […]
If you’re concerned about privacy online and want to get a VPN to secure your internet connection, it’s smart thinking. But with so many VPN services out there, how do you choose? Before signing up for any VPN, you must understand what matters when protecting your data. Not all VPNs are created equal, and some […]
As internet users increasingly depend on secure websites for activities such as banking, shopping, and communication, encrypted connections have become essential to cybersecurity. The Secure Sockets Layer (SSL), known as Transport Layer Security (TLS), is crucial for protecting sensitive data as it travels between users and websites. Attackers have developed methods to bypass this protection […]
In an age of digital transformation, Operational Technology (OT) systems, once isolated and safe from outside threats, are increasingly connected to modern networks for efficiency, analytics, and automation. This connectivity, while beneficial, has radically shifted the cybersecurity landscape for industrial environments. Today’s OT infrastructure is a prime target for sophisticated threat actors, and organizations bear […]
Sky Go, the UK’s premium streaming service offering live sports, movies, and on-demand content, is strictly geo-blocked outside the United Kingdom and Ireland due to broadcasting licensing restrictions. Since Brexit in January 2021, EU portability regulations no longer apply to Sky Go, meaning UK subscribers traveling to Europe cannot access the service without a VPN. […]
Cyberattacks today rarely rely on a single weakness. Modern breaches usually unfold in stages. An attacker phishes a user, escalates privileges, moves laterally, and quietly extracts data. This is precisely why single-layer security no longer works. Defense in depth is built on a simple but powerful idea: no single control should ever be trusted to […]
Artificial intelligence systems rely heavily on large volumes of data to learn patterns, make decisions, and generate accurate outputs. While this dependency enables powerful capabilities, it also creates a critical vulnerability known as data poisoning. Data poisoning attacks manipulate training or input data to compromise AI behavior, leading to biased predictions, incorrect decisions, or even […]
Many Windows users encounter unexpected pop-ups, slow system performance, or unfamiliar software called PC App Store, which is installed on their computers. While the name sounds similar to official app marketplaces, it often raises concerns about security and privacy. Users frequently ask whether PC App Store is a virus, how it entered their system, and […]
Modern internet infrastructure depends heavily on the Domain Name System (DNS) to function smoothly. Every time a user types a website address into a browser, DNS translates that domain name into an IP address. Due to their critical role, DNS servers are a prime target for cybercriminals. One of the most common attacks aimed at […]
Despite modern network defenses and best practices, Smurf attacks continue to surface in real-world DDoS traffic mixes and can still pose a threat when network configurations are weak or outdated. In simulated environments and real-world attack analyses in 2025, security researchers observed that a single Smurf-style packet sent to a misconfigured broadcast network could trigger […]
As a dedicated Packers fan, you know the thrill of game day. The anticipation builds as you prepare to cheer on the green and gold. But in 2026, how can you ensure you don’t miss a single play? Whether you’re a longtime season ticket holder or a fan watching from afar, staying connected to your […]
As a Dallas Cowboys fan, you know the importance of catching every game, even when you can’t be at AT&T Stadium. In 2026, streaming options for NFL games continue to evolve, giving you more ways than ever to watch America’s Team in action. Whether you’re looking for a season-long subscription or just need to catch […]
Ransomware attacks have evolved rapidly over the past few years, becoming more targeted, aggressive, and damaging. Among the most notorious threats was Maze ransomware, a strain that reshaped how ransomware campaigns operate. Maze was not just about encrypting files; it introduced data theft and public shaming as part of its attack strategy, pressuring victims into […]
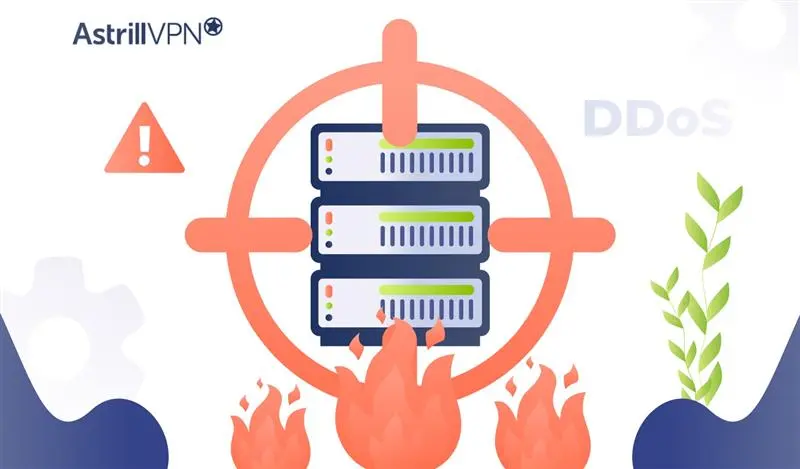
Distributed Denial-of-Service (DDoS) attacks have evolved far beyond overwhelming networks with sheer volume of traffic. One of the most significant modern threats is the application-layer DDoS attack, also referred to as a Layer 7 DDoS attack. These attacks target the application layer of the OSI model, where web applications, APIs, and services interact directly with […]
Are you eager to catch the latest UFC action? With multiple official streaming platforms available worldwide, watching your favourite fighters has never been more accessible. In this comprehensive guide, you’ll discover the best legitimate platforms to stream UFC events, understand pricing options, and learn how to access your subscription while traveling abroad. Whether you’re at […]
Smart speakers, such as Amazon Alexa, have become increasingly common in homes worldwide, offering convenience through voice commands, smart home control, and instant access to information. However, their always-on microphones have raised serious privacy concerns. Many users ask questions such as “Does Alexa spy on you?” “Is Alexa a spying device?”, and “Does Alexa listen […]
Web browsers have become one of the most common entry points for cyberattacks. From phishing websites and malicious ads to drive-by downloads and zero-day exploits, attackers increasingly target browsers because they sit directly between users and the open internet. Traditional security tools such as antivirus software and URL filtering help, but they often fail against […]
Zelle is a popular payment platform with a staggering $806 billion transaction volume, a 28% increase from last year. It is also set to expand at a growth rate of 20% in the next five years. Zelle allows free instant transfers from the app. As companies strive to enhance the customer experience and make things […]
Pay-per-click (PPC) advertising is one of the most effective digital marketing channels, enabling businesses to drive targeted traffic and achieve measurable results. However, as online advertising continues to grow, so does one of its biggest threats: click fraud. This malicious activity drains ad budgets, distorts performance analytics, and weakens the effectiveness of paid campaigns. Whether […]
Email remains one of the most widely used communication channels in the world, but it’s also a significant target for cybercriminals. From phishing scams to malware-laden attachments, spam emails pose serious risks to individuals and businesses alike. Industry estimates indicate that between 45% and 55% of global email traffic is spam, underscoring the importance of […]
The growing cybersecurity threats come in various forms, not all of them as overt as a full-blown virus. One prevalent and often insidious category is the Potentially Unwanted Program (PUP). These programs, while not always malicious in the traditional sense, can significantly degrade user experience, compromise privacy, and even create vulnerabilities. Recent reports indicate a […]
Is someone secretly listening to your phone calls, reading your messages, or tracking your location? In 2024, 2,297 legal wiretaps were authorized in the United States alone which is a 9% increase from the previous year and that’s just what’s officially reported. Unauthorized phone tapping by cybercriminals, suspicious partners, and corporate spies happens far more frequently, […]
As the remote work revolution continues to shape the modern workforce, ensuring online privacy and data security has never been more important. One of the most essential tools for remote professionals is a VPN (Virtual Private Network). Whether working from a coffee shop, a coworking space, or your living room, a VPN is necessary for […]
In an era where data is arguably an organisation’s most valuable asset, ensuring that sensitive information remains secure and does not fall into the wrong hands has become a strategic necessity. The concept of Data Loss Prevention (DLP) is no longer just a buzzword; it is a cornerstone of modern data security programs. From protecting […]
Adware is one of the most common forms of unwanted software. It clutters your screen with pop-up ads, slows down your device, and can even track your online behavior. In the first quarter of 2025 alone, over 12.18 million mobile device attacks involving malware, adware, or unwanted apps were blocked by a major security vendor. […]
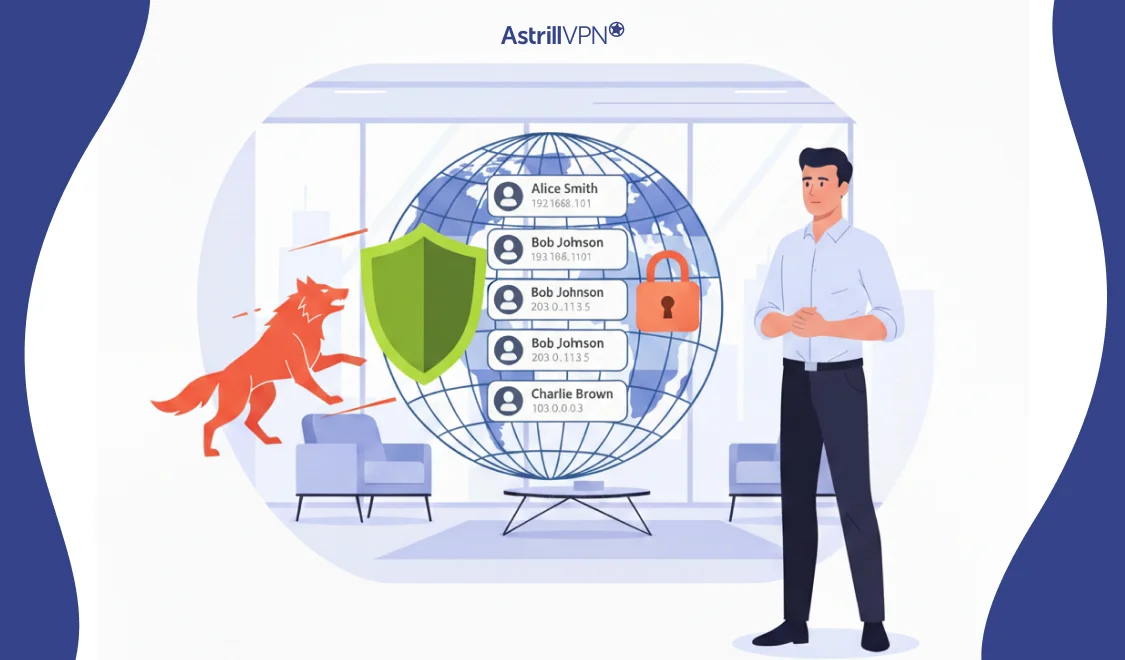
As your organization operates online, it is constantly under siege from cyber threats, many of which evade detection until irreversible damage is done. Among the stealthiest is DNS hijacking, a technique by which attackers redirect your traffic to malicious sites, intercept sensitive data, or inject malware without raising alarms. According to DNSFilter’s 2025 Annual Security […]
There’s a famous saying that says, “all that glitters isn’t gold”. That’s truly the case when it comes to Social Media. While Social Media has provided people a platform to connect with others and build an audience to earn a decent livelihood, there’s also a dark side. Cyberattacks are on the rise. Social Media has […]
In an era where cyber threats are becoming more sophisticated and data breaches more costly, traditional password-based security is no longer enough. Multi-Factor Authentication (MFA) has emerged as a critical defense mechanism for individuals and organizations seeking to protect sensitive information. MFA drastically reduces the likelihood of unauthorized access by requiring multiple verification forms, such […]
If you love nothing more than settling in for a marathon gaming session of your favorite first-person shooter or MMO and if you’re gaming online, your connection and data are exposed for anyone to snoop on. Using a VPN is the best way to reduce isp throttling, protect your privacy, and access geo-blocked games. This […]
Cyber threats have grown more sophisticated and damaging in today’s rapidly evolving digital landscape. One of the most dangerous categories is the Advanced Persistent Threat (APT), a stealthy, targeted, and highly destructive cyberattack. Unlike opportunistic hackers, APT attackers are methodical, patient, and often well-funded, making them a significant concern for governments, large corporations, and critical […]
Cybersecurity is a trendy topic these days, with hackers finding ever-more sophisticated ways to access our data and make off with it. As technology marches, the risk to our personal data is ever increasing. Taking a few basic steps can help protect you and keep your information safe. One of the important steps you can […]
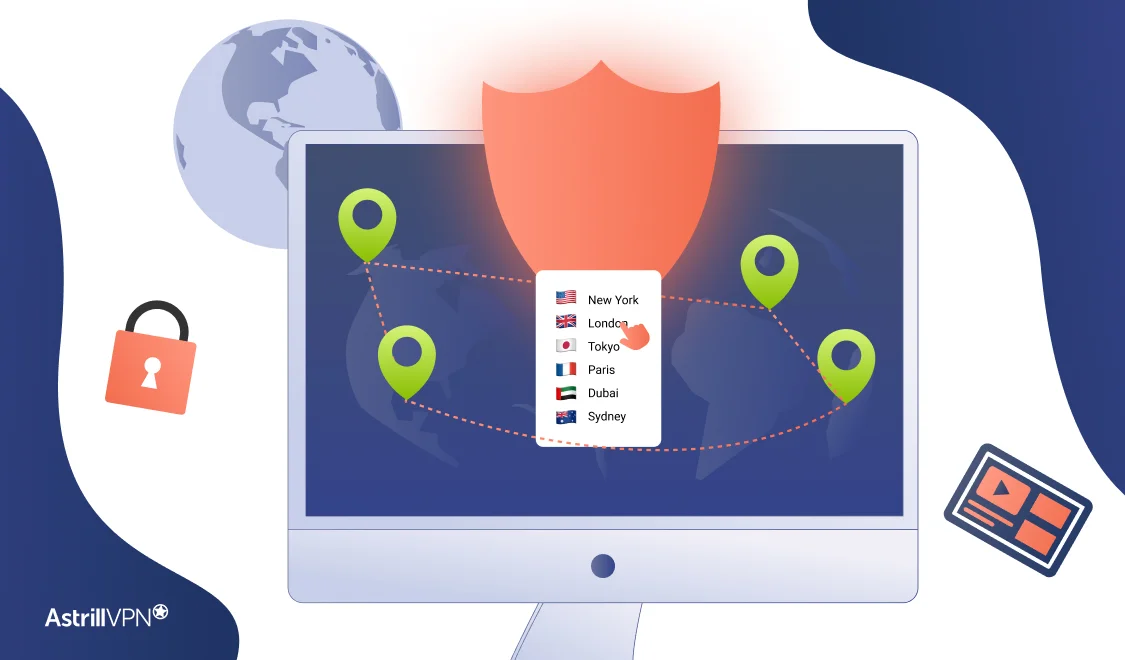
In today’s digital world, privacy and access are top priorities. Whether you’re trying to stream geo-restricted content, access websites blocked in your region, or simply browse the internet anonymously, using a VPN is the most effective solution. One of the key features of a VPN is to use a VPN as your location changer, making […]
If you have heard people talking about using a VPN to protect their data, a friend may have recommended it, or maybe you’ve seen ads for different VPN services. There are several benefits of VPNs. We must discuss what a VPN can do for your digital security and privacy. A Virtual Private Network (VPN) keeps […]
Have you been wondering how to disable IPv6 on your Mac? You’re not alone. While IPv6 was designed to replace IPv4 and provide more IP addresses, many people find it can cause connectivity or other unintended network problems. If you’ve tried various network troubleshooting steps but still suspect IPv6 might be the culprit, disabling it […]
In an increasingly digital world, protecting our data has become even more critical. It’s important that you can trust your VPN to keep your data safe and secure. But how to tell if is my VPN working? The short answer is that it’s tricky but can be done. In this article, we’ll look at some […]
Have you ever tried watching your favorite show while traveling only to get error saying that content isn’t available in your current region? Using a virtual private network or VPN is an easy fix to access streaming content no matter where you are. In this article, we’ll explain what a VPN is, recommend the best […]
All of us know that the internet would not function without bots. From search engines indexing billions of web pages to chatbots providing instant customer support, bots automate tasks, improve efficiency, and enhance user experiences. However, not all bots serve beneficial purposes; malicious bots silently infiltrate systems, steal sensitive data, manipulate traffic, and even crash […]
In our hyperconnected world, billions of devices access the Internet every second. The Domain Name System (DNS) is a silent yet crucial component often called the “phonebook of the Internet.” It translates human-readable domain names into machine-readable IP addresses. While this process seems simple on the surface, DNS is a high-value target for cybercriminals. This […]
Distributed denial-of-service (DDoS) attacks remain one of the most common and disruptive cyber threats today. In 2024, industry telemetry shows that large-scale DDoS events continue to occur frequently and that peak attack volumes in recent years have reached hundreds of gigabits per second. Among DDoS techniques, the SYN flood (sometimes called SYN flooding) is a […]
You’re traveling abroad and suddenly realize you can’t access TextNow, your favorite messaging app. Whether you’re trying to unblock TextNow from a restricted country or dealing with TextNow not working issues due to geographic limitations, this comprehensive guide will show you exactly how to regain access from anywhere in the world. What Is TextNow and Why You Might Want […]
If you’re on the lookout for a perfect mobile app that allows you to call and message people over the internet for free, then Talkatone is the app that needs to pique your interest. Talkatone used voice-over-internet protocol (VoIP technology), allowing you to to communicate with your friends and loved ones without incurring high roaming […]
Have you ever wondered why the Wi-Fi on your phone automatically connects when you get home? It’s because network devices like routers use MAC addresses( unique identifiers hardwired onto network interface cards) to recognize trusted devices. But MAC addresses aren’t always permanent. According to latest report, as of 2025, almost all modern smartphones including every […]
A VPN authentication error occurs when the server cannot verify your login credentials or the connection parameters. This can happen for a variety of reasons, including incorrect usernames or passwords, outdated VPN clients, protocol mismatches, or network restrictions. Understanding why these errors occur is the first step toward resolving them quickly and effectively. In this […]
If you’re just minding your own business when an email pops into your inbox from Facebook and the subject line says your Facebook account’s recovery code is inside. Scammers are getting craftier with phony account recovery emails. If this sounds familiar, you’re not alone. Lots of folks are getting duped by fake Facebook account recovery […]
Have you noticed your internet speed slowing down recently, especially when streaming your favorite shows or gaming online? You start to wonder if your internet service provider, Spectrum, could be throttling your connection. Spectrum claims they don’t throttle internet speeds, but many customers report slower speeds during peak usage times. We’ve got some tips to […]




























![The Ultimate Guide to Best VPN for Gaming [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/08/Astrill-is-best-VPN-for-Gaming.jpg)