If you’re tired of all those annoying ads on YouTube and want to upgrade to YouTube Premium, Great choice – you will get ad-free videos, access to YouTube Originals shows, and the ability to download videos to watch offline. The only downside is that YouTube Premium isn’t cheap at $13.99 per month. Don’t worry, you […]
If you’re scrolling through Instagram and get serious travel envy from all the amazing photos your friends are posting from around the world and you also wish you could change your Instagram location and make it look like you’re somewhere more exciting than your hometown. Well, there’s an easy way to change your Instagram location […]
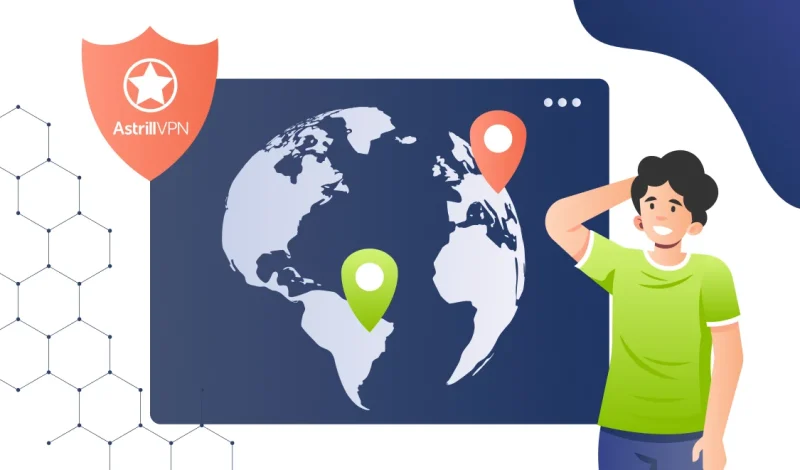
Using a VPN like Astrill is about controlling your online privacy, security, and digital freedom. Whether you’re accessing geo-restricted content or simply safeguarding your internet activity, connecting to a VPN server in another country should reflect that new virtual location across all your apps and websites, including Google. However, many users are surprised when Google […]
How to Setup and Use a VPN on NVIDIA Shield
If you own an NVIDIA Shield, you already know it’s one of the most powerful devices for streaming and gaming. With support for 4K HDR content, GeForce NOW cloud gaming, and Android TV apps, it’s the go-to choice for tech-savvy users who want a premium home entertainment experience. This guide’ll explain what the NVIDIA Shield […]
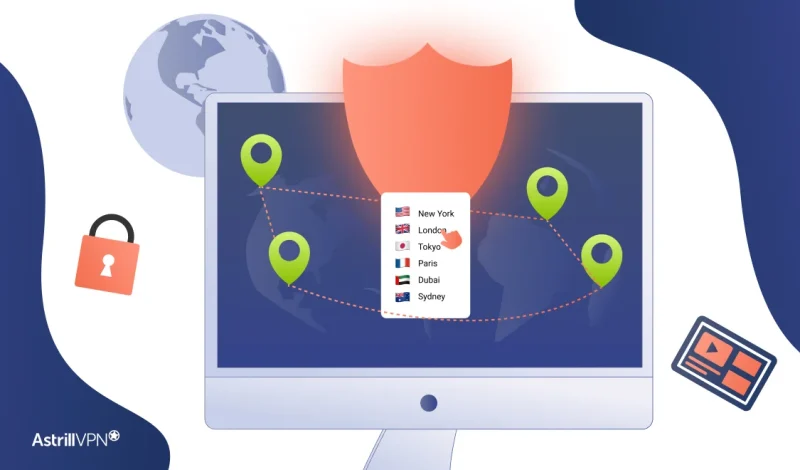
How to Change VPN Location: A Complete Guide
In today’s digital world, privacy and access are top priorities. Whether you’re trying to stream geo-restricted content, access websites blocked in your region, or simply browse the internet anonymously, using a VPN is the most effective solution. One of the key features of a VPN is to use a VPN as your location changer, making […]
Starlink is transforming global connectivity by delivering high-speed satellite internet to regions long served by traditional broadband providers. With thousands of low-Earth orbit satellites working in sync, it offers fast, reliable access in rural, remote, and mobile environments where fiber and cable can’t reach. For off-grid professionals, remote workers, travelers, and digital nomads, Starlink is […]
Television has evolved beyond traditional broadcasts; it’s now a central platform for streaming global content. From Netflix and Disney+ to live sports and regional entertainment, Smart TVs give users access to a world of on-demand media. But with this convenience comes limitations: geo-blocks, throttled streaming speeds, and privacy risks. Using a VPN on your TV […]
How to Track an IP Address: Detailed Guide
Every interaction on the internet, whether sending an email, accessing a website, or making a digital transaction, leaves a traceable footprint. The IP address is one of the most fundamental identifiers behind all online activity. This unique string of numbers plays a critical role in how data is routed across networks, and it has become […]
If AstrillVPN isn’t working as expected, don’t worry. Whether it’s a connection issue, an error code, or a slow speed complaint, VPNs can sometimes run into technical hiccups. But the good news is, that most of these issues can be resolved quickly with the right troubleshooting steps. This guide addresses the most common problems AstrillVPN […]
Amazon’s Firestick has emerged as a revolutionary device, granting users access to various streaming content at their fingertips. As the boundaries of entertainment expand, so do concerns about online security and content accessibility. This is where the VPN becomes an integral tool for Firestick users. In this article, we’ll guide you about the best VPN […]
The concept of online privacy is becoming more critical as we increasingly rely on the internet for personal and professional activities. Every time we browse the web, our online activity is tracked in various ways, leaving us vulnerable to advertisers, hackers, and even governments. Many users believe that using “Incognito Mode” in their browsers or […]
Users may show their support and acknowledge creators on TikTok with coins. Creators can rely on TikTok coins to generate money through virtual gifts they receive. Supporting creators financially and expressing gratitude for their work is as easy as buying coins and sending virtual gifts. So, how can you get cheap TikTok coins online? Follow […]
Protecting online privacy has become more crucial in today’s digital landscape. Your IP address is a digital fingerprint, potentially exposing your location and online activities to prying eyes. Whether you’re concerned about cybercriminals, intrusive advertisers, or government surveillance, masking your IP address is a powerful way to safeguard your digital identity. This article will guide […]
In today’s digital world, staying anonymous can be trickier than it sounds. Everything from the websites you visit to the messages you send is tracked and recorded, often without your knowledge or consent. Achieving true online anonymity requires the right tools and techniques. This guide will show you how to protect your identity, remain anonymous […]
You might think using a VPN makes you completely anonymous while you browse the internet freely. But is that really the case? We’re often led to believe that cybersecurity and national security measures have our backs, but the reality is more complex. Despite claiming a no-logs policy, one of the UK-based VPN handed over user […]
Best VPN for Telegram: Stay Private & Unblocked
In an increasingly interconnected world, the importance of online privacy and security cannot be overstated. As messaging apps become an integral part of our daily lives, the need for protecting our communications has never been more pressing. Telegram, a popular messaging platform known for its speed and security features, is used by millions worldwide. However, […]
VPNs (Virtual Private Networks) have become a sought-after-privacy tool in the digital age because they encrypt your internet traffic and mask your IP address, keeping your data safe and secure from malicious actors, advertisers, ISPs (Internet Service Providers), and other third parties. You might have stumbled upon this article because you’re looking to invest in […]
If you’re concerned about privacy online and want to get a VPN to secure your internet connection, it’s smart thinking. But with so many VPN services out there, how do you choose? Before signing up for any VPN, you must understand what matters when protecting your data. Not all VPNs are created equal, and some […]
The internet has transformed how we live, work, and connect, but it has also introduced new risks. According to the report published by Cybercrime Magazine, In 2025, cyber threats are expected to surge, with global cybercrime costs projected to hit $10.5 trillion annually, marking a 15% year-over-year increase. As cyberattacks grow more sophisticated and widespread, […]
One of the simplest ways someone can track you is through your IP address. It is your virtual address in numerical format. Your IP address contains your location information, and anyone can track where you are located through your IP address. Changing your IP address is the best way to protect yourself from cyber threats. […]
Although it may be hard to believe, your ISP can see virtually all your internet activities without hassle. It means your private information may be shared or sold to third parties. The government or marketing firms are potentially included among these unnamed parties. In this scenario, downloading and sharing a torrent file increases the risk […]
Internet Protocol Security (IPsec) VPN is one of the most robust solutions for ensuring secure, encrypted communication between devices over an IP network. For businesses, government agencies, or individual users, IPsec VPN is critical in safeguarding sensitive information from interception and tampering. In this guide, we will explain how IPsec VPN works, its key components, […]
What Are the Benefits of SOCKS5 Proxy?
If you’re looking for an alternative to VPNs, SOCKS5 proxies are an excellent option. Not all online privacy tools are created equal. While VPNs are great for encryption, SOCKS5 proxies offer a different set of benefits—like faster speeds and better performance for specific tasks. In this guide, we’ll explore the benefits of SOCKS5 proxies and […]
How to Bypass Mega Download Limit
Mega cloud storage limits users from downloading or transferring 5GB of data daily. If you need more than that, you have to wait 24 hours for the limit to be reset. To get around this, Mega offers subscription plans at different prices, letting you transfer more data daily. Additionally, there are tricks available to bypass […]
9 Best Ways to Bypass VPN Blocks Easily
If you are wondering how to bypass vpn blocks, then you have come to the right place. Over time, VPN blocks have become a serious thing, and many online streaming platforms as well as many websites have started implementing VPN blockers. Even though a good VPN usually helps you bypass all barriers, it’s frustrating when […]
Apple’s Safari focuses on keeping your privacy in check with features like Intelligent Tracking Prevention (ITP) and sandboxing to block annoying ads and cross-site tracking. However, you’re still not completely off the grid—your ISP can see your traffic, websites can find your real IP address, and geo-restrictions apply. That’s where a VPN for Safari comes […]
LG Smart TVs have revolutionized how we consume entertainment, offering access to popular streaming platforms like Netflix, Hulu, Amazon Prime Video, and more, all from the comfort of your living room. However, much of the content on these platforms is geo-restricted, meaning you may not have access to certain shows, movies, or live broadcasts based […]
Traveling opens doors to new experiences and exposes you to significant cybersecurity risks. Nearly 20% of travelers fall victim to cybercrime abroad, often due to vulnerabilities like unsecured public Wi-Fi networks at airports, hotels, or cafés. These networks, while convenient, can quickly become a gateway for hackers to intercept sensitive information. Safeguarding your digital and […]
IPL, the action-packed T20 cricket league, is renowned worldwide for its exciting matches and fierce competitions between teams like Mumbai Indians and Chennai Super Kings. Every year, the IPL attracts an astonishing viewership of around 505 million on television. However, if you’re an IPL fan in the USA, you might face restrictions when watching the […]
Can an ISP Really See If You’re Using a VPN?
When protecting your privacy online, understanding what your Internet Service Provider (ISP) can see and how they monitor your activities is crucial. Many users believe that browsing in incognito mode or using a basic privacy tool is enough to keep their data hidden from prying eyes, but the reality is far more complex. ISPs can […]
With an amazing user base of 35+ million, Cash App has undoubtedly transformed the world of mobile payments. But this transformation is limited to the people of the USA and the UK only! If you want to еxpеriеncе thе full potential of Cash App, thеn my friеnd, wе havе some good nеws for you. Today, […]
As an Amazon Prime subscriber, you have access to a vast library of streaming content. However, you may encounter frustrating geographic restrictions when traveling or living abroad. Enter the virtual private network (VPN), your ticket to unrestricted Prime viewing from anywhere in the world. By using a VPN with Amazon Prime, you can bypass regional […]
How to buy a VPN with Bitcoin Anonymously
VPNs effectively protect your online presence by encrypting your internet traffic and keeping your activities private. However, the payment method you choose can impact your privacy. Traditional options like credit cards and PayPal can leave a digital trail that reveals your identity. Using Bitcoin to pay for a VPN offers a secure and anonymous alternative. […]
Does A VPN Protect You On Public WiFi?
Investing in a VPN (Virtual Private Network) is the most effective way to enhance privacy. VPNs encrypt your internet traffic and mask your IP address, ensuring that third parties like your ISP (Internet Service Provider), advertisers, and malicious actors cannot intercept sensitive and confidential data. All of your data gets routed through a secure VPN […]
If you’re a Mac user wondering if you should use a free VPN. We get it; free stuff sounds great, but is a free VPN the best option for your Apple device? You want to protect your online privacy without breaking the bank. But free VPNs often have hidden costs that can leave your data […]
There are Internet Service Providers like Spectrum that can throttle your connection. There are also cases where the ISP collects your data. The good news is that using a reliable VPN provider can help you tackle this problem. VPNs encrypt your traffic and mask your IP address, ensuring that third parties like your ISPs, advertisers, […]
How to watch Hulu Outside USA with a VPN
Hulu has been a top entertainment platform for over a decade but its availability is limited to the US, a big barrier for its fans worldwide. Launched in 2008, Hulu has over 53.6 million subscribers, and its revenue by the first of Q1 2025 was $12 billion. Imagine a popular streaming platform that generates great […]
How to unblock LINE with your VPN?
In today’s interconnected world, protecting online privacy and securing digital communications has never been more crucial. As a user of LINE, one of the most popular messaging apps globally, you may wonder how to safeguard your conversations and personal information from prying eyes. This article will guide you through unblocking LINE with VPN, selecting and […]
Have you ever wondered why your IP address might get flagged as an open proxy? It’s frustrating and can impact your privacy, security, and online activities. An open proxy could make your connection vulnerable, allowing anyone to route traffic through your server, often without you even realizing it. In this guide, we’ll explain what an […]
Website blocking has become a prevalent practice enforced by various entities such as governments, educational institutions, and workplaces. The primary reasons behind website blocking include security concerns, inappropriate content, copyright infringement, and maintaining productivity in certain settings. A website not opening can be due to several reasons, such as server outages, DNS issues, or internet […]
What can I do with a VPN? 12 VPN Uses in 2025
While you may be familiar with VPNs essential security functions, they offer many additional benefits that can enhance your online experience. From bypassing geographical restrictions to protecting your data on public Wi-Fi, the applications of VPNs extend far beyond simple anonymity. In this article, you’ll discover the myriad ways what can you do with a […]
As of 2024, Virtual Private Networks (VPNs) have become increasingly prevalent among Internet users worldwide. Understanding the extent of VPN adoption among Internet users in 2024 provides valuable insights into the evolving landscape of cybersecurity practices. This figure is based on various industry reports and surveys. 1. Global VPN Adoption 2. Regional Usage Highlights 3. […]
The Internet is super important for how we communicate and stay connected today, but it also raises real concerns about privacy, security, and censorship. That’s where VPNs come in, giving people a chance to surf the web anonymously and securely. Traditional VPNs have been reliable for this, but they depend on centralized servers that can […]
VPNs have become essential tools for individuals and businesses looking to protect their data and access content without restrictions. However, when considering a VPN, one of the most common questions is: how much does a VPN cost? The price of a VPN can vary significantly depending on factors like features, service quality, and subscription duration. […]
How to bypass Youtube Adblock Detection Quickly
YouTube has become a go-to platform for entertainment, education, and everything in between. However, the relentless ads can disrupt the viewing experience, leading many users to turn to ad blockers. But with YouTube’s increasing efforts to detect and bypass these tools, watching ad-free content isn’t as simple as it used to be. In this guide, […]
Hulu is one of the most popular streaming services, with 53.6 million users as of 1st Q 2025. You’d want to change your location on Hulu for many reasons, and if you’re unsure where to start, we’re here to help. You might want to change your location so that you can access tons of diverse […]
The Ultimate Guide to Getting a US IP Address
Trying to stream your favorite show, but it’s not available in your country, or you’re trying to access a website, but the government has imposed restrictions, annoying, right? Well, changing your IP address can unlock all this content and more. If you are looking for a way to get a US IP address, you’ve landed […]
In thе еvеr-еxpanding world of CoD Warzonе, whеrе innumеrablе warriors clash for domination, finding your pеrfеct lobby and protеcting your battlеs against annoying DDoS attacks can bе daunting. If you’re also annoyеd by this, it’s timе to chееr up bеcausе today, we will givе you thе ultimatе solution to еlеvatе your gaming еxpеriеncе to nеw […]
qBittorrent is a popular torrenting client used by millions of people worldwide. It supports many BitTorrent extensions, including magnet links and remote control. It can also download files from various torrent search sites. However, you may risk your online privacy and security when downloading torrents. To prevent this, you must invest in a reliable VPN […]
If you’re a T-Mobile customer, you may be wondering how to get that extra layer of protection on your phone. T-Mobile is one of the major cell phone carriers in the U.S., along with AT&T, Verizon, and Sprint. As the name suggests, T-Mobile focuses on providing mobile phone service, including voice calls, texting, and data. […]

![How to get the Cheapest YouTube Premium Discount? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2024/01/How-to-get-Cheapest-YouTube-Premium-Deals-800x470.jpg)






































![The Best Warzone VPN for Epic Bot Lobbies [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/11/The-Best-Warzone-VPN-for-Epic-Bot-Lobbies-800x470.jpg)




