Blogs Posted by Bisma
If you’re a Roku user, you know how frustrating it can be when you cannot access certain content due to geo-restrictions or censorship. That’s where a VPN comes in – encrypting your internet traffic and masking your IP address, you can bypass these restrictions and stream content from around the world. In this blog, we’ll […]
Did you ever have one of those annoying Facebook messenger bugs that spreads itself to all your friends? You know the ones – they look like a normal message from a friend, tempting you to click a link or watch a video. But then suddenly your Messenger starts spontaneously sending the same message to people […]
If you’re just trying to chill and watch the latest episodes of your favorite Netflix shows, but no matter what you try, you keep getting that annoying proxy error. It’s frustrating to experience it. But don’t flip the coffee table in rage just yet. With a few simple tweaks, you can get past that error […]
iPhone Data Leak
If you love baseball but hate the blackout restrictions on MLB TV then you’re not alone. Nothing’s more frustrating than not being able to watch your favorite team just because of where you live. But don’t worry, there’s an easy fix. Using a VPN, or virtual private network, you can bypass the blackouts and stream […]
HP CEO Enrique Lores defended the company’s practice of disabling certain printers when users install third-party ink cartridges, saying it’s necessary to protect customers from security risks. In an interview with CNBC Television last week, Lores said HP printers are designed to work only with HP cartridges to guard against “embedded viruses” that could spread […]
Every online action you take today puts your personal information in danger, including simple web searches. Your IP address and browsing history will be recorded every time you utilize search browsing. Various businesses can benefit from this data. Users are identified so that advertisements can be tailored to each individual. Displaying personalized advertisements is how […]
HAK5 developed the Wi-Fi Pineapple, which is a private company. Now you may be wondering, how do fruit and WiFi go hand in hand? Well, there’s a story behind its name. The WiFi Pineapple gets its name from its appearance. It’s a small, black device with multiple antennas at the top that stem outwards in […]
Ever find yourself in need of Internet access while out and about, so you hop on the nearest public Wi-Fi network? It’s convenient, but is that free Wi-Fi ever really safe? Think about it – that network is open to anyone nearby, and there are hackers who know how to snoop on what people do […]
PDFs have long been a vehicle for malware and viruses. But can a PDF have a virus? The short answer is no, PDFs are simply a file format and are not inherently malicious. However, that doesn’t mean you should let your guard down when dealing with PDFs from untrusted sources. While PDFs may be a […]
With our fast-paced life, we are all hurrying to do daily chores. So when it comes to downloading files, the faster, the better. Right? Well, why are my downloads so slow? Sure, download speed is important, but it’s not the only factor determining how long a file takes to download. You can do several things […]
Suppose you get a call from someone claiming to be from Xfinity, and you start thinking about Xfinity will call me? Saying there’s an issue with your internet service or cable package that needs to be addressed immediately. They insist you provide personal information like your account number, social security number, or credit card details […]
When discussing dark web browsing, Tor is the first browser that springs to mind. Tor is growing in popularity among millions of people worldwide with the passing years. It has been synonymous with anonymous browsing during the last few years. As people’s concerns about online privacy rise, questions like is tor browser legal? What can […]
With the advent of cryptocurrency, the cyber risk landscape has grown increasingly complicated. Crypto-jacking and other crypto-focused malware are on the rise, and protecting your data is essential. Thankfully, it’s possible to mitigate the risk posed by cryptocurrency malware. In this article, we’ll uncover some of the latest insights on crypto malware and provide tips […]
As an emulator, Bluestacks is adored by the majority of its gamers. It claims to be magic for them. With this emulator, you can use any mobile app on Android as this emulator is specially designed for better performance, better speed, and more accurate control changes. Due to its popularity and demand to turn off […]
ESO Solutions, a leading provider of data and software for emergency responders and healthcare organizations, announced today that it suffered a ransomware attack impacting the sensitive data of up to 2.7 million individuals. In an incident notice published on its website, the Austin, Texas-based company stated that an unauthorized third party deployed ransomware to encrypt […]
So you’re in India and want to protect your privacy and security online? With increased government monitoring and censorship, using a VPN is crucial. But with so many VPN services out there, how do you choose? As India’s leading VPN provider, AstrillVPN is the obvious choice for privacy, security and bypassing geo-restrictions. With servers optimized […]
Have you ever been in the middle of an intense team fight in Dota 2, your fingers flying across the keyboard as you dodge spells and land perfect combos, only to have your screen freeze for a few seconds? Lag spikes and high ping in Dota 2 can ruin the experience and cost you the […]
Ever get one of those virus alerts on your computer claiming you’ve been looking at pornography? Yeah, it’s annoying and embarrassing even though you know you haven’t looked at anything inappropriate. The good news is those virus alerts are scams trying to trick you into calling a fake support number or downloading software that will […]
Have you ever struggled with bad credit? Maybe you’ve made a few mistakes in the past that hurt your credit score, and now you have a hard time qualifying for loans, credit cards, apartments, or jobs. It happens to the best of us. But what if there was a way to establish a new credit […]
In recent years, smart home devices like Ring cameras have revolutionized the way we protect our homes. With their ability to provide real-time video feed and instant alerts on our mobile devices, they have offered an added layer of convenience and security. But like any technology connected to the internet, they are not immune to […]
Google Chat, an important component of Google’s business-focused software suites, has become a popular mode of communication for individuals and organizations. This tool, however, raises certain privacy concerns, especially as increasing numbers of scammers find means to misuse it. As a user, it’s imperative to recognize the potential vulnerabilities and learn how to navigate safely […]
If you’ve got your hands on Sony’s new PlayStation 5 console then it’s time to get that optimized for the best online gaming experience. One of the most important things you can do is make sure you’ve got an Open NAT type. NAT type refers to how well your PS5 can connect to other players […]
If you’re one of the millions of cord-cutters out there looking for free TV shows and movies online, there’s a good chance Putlocker has popped up on your radar. But before you dive in and start binge-watching your favorite series, you’re probably wondering is Putlocker safe? As with any free streaming site, there are some […]
Have you been using uTorrent for years to download your favorite movies, TV shows, music, books, and software? It’s time to ditch that outdated torrent client and upgrade to something better. uTorrent used to be great, but now it’s riddled with ads and bloatware that slow down your downloads and invade your privacy. You deserve […]
You’ve probably heard of sting operations where undercover agents set up scenarios to catch criminals. Well, honeypots are kind of like cyber sting operations. They lure in hackers to secretly gather information about their methods and motives.Ever wonder how cybersecurity experts try to outsmart hackers? One of their clever techniques is using decoy systems called […]
As more and more workplaces adopt hybrid work setups, the need for secure remote data access has become evident. Companies and employees need to be able to access resources from home and portable devices, without risking data breaches or compromised security. Virtual private networks are already in use by many businesses worldwide, allowing secure, anonymous […]
Maybe you have a website or app and need to ramp up security or want access to servers that give you more control. Or perhaps you just want to stream your favorite shows while traveling abroad. Either way, you’ve come to the right place. If you’ve heard about VPS and VPN services, you must want […]
Wave Browser appears to be a regular browser on the surface, but it’s a type of software you might not want on your computer. This misleading browser can collect your data without your knowledge, bombard you with intrusive advertisements, and be quite challenging to uninstall. In this guide, we’ve discussed everything related to the Wave […]
Ever run into that annoying “Ethernet doesn’t have a valid IP configuration” error on your Windows PC? Don’t worry, we’ve got you covered. In just a few easy steps, you’ll be back online in no time. Believe it or not, this frustrating message usually means something went a little haywire with your network settings, but […]
You’ve just set up your shiny new Raspberry Pi and are eager to get started with some projects. But there’s a catch – your Pi is behind your wireless router’s NAT firewall. But what exactly is a NAT Firewall? Don’t worry , with a little networking know-how you’ll be accessing your Pi in no time. […]
Omegle is the site for you if you enjoy chatting and entertaining with random people. This platform gives many people a way to have fun conversations. The app is getting popular because of social media videos. People connect, talk, and post their recordings on other media platforms for entertainment. Undoubtedly, it’s a terrific way to […]
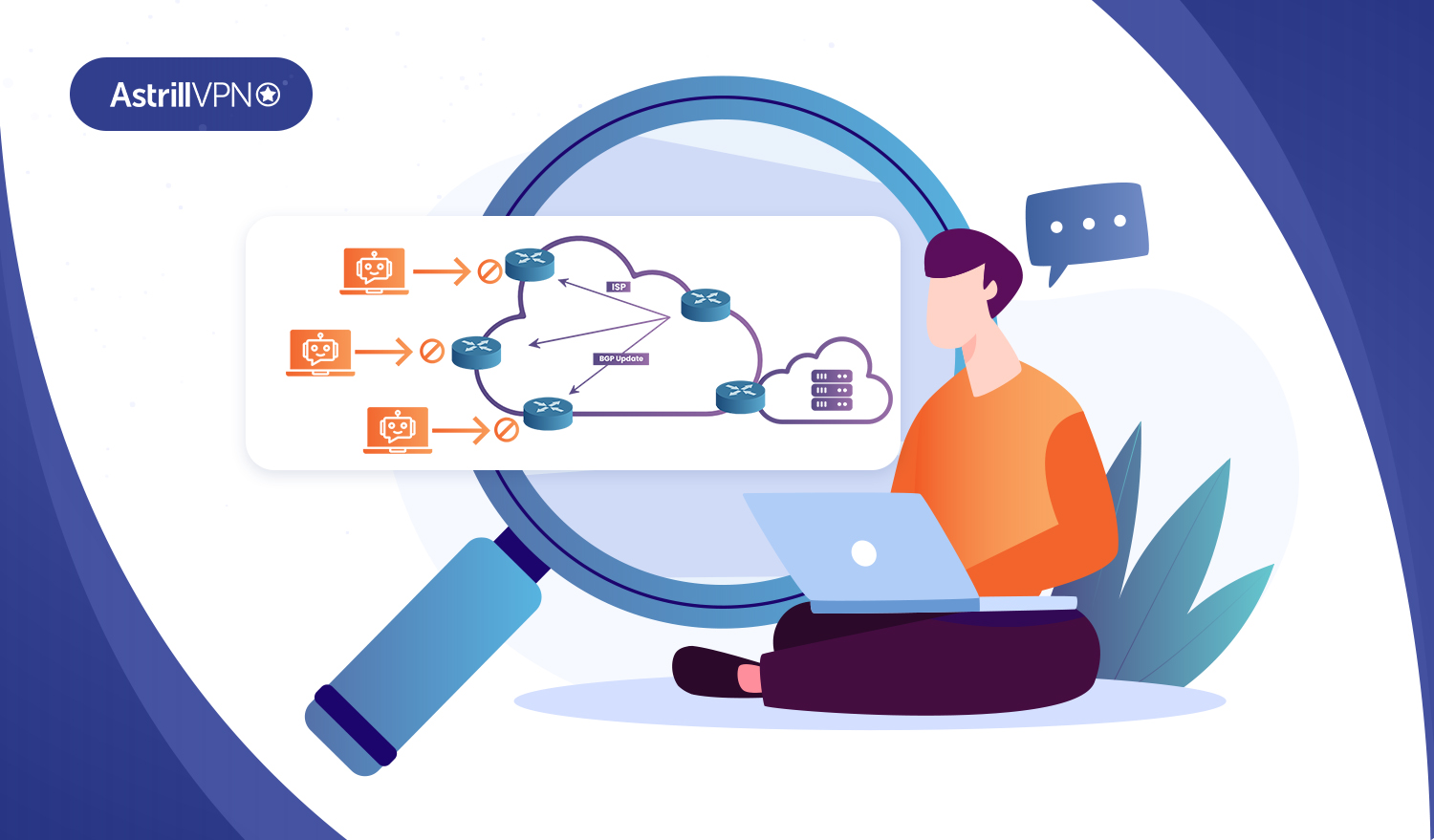
Blackhole routing is a type of internet routing that can both benefit and hurt an ISP’s network. The term derives from a 1979 film. A black hole route is a place where things aren’t able to escape, and it has negative connotations in IP routing. Nevertheless, DDoS blackhole routing can be a helpful solution when […]
If you gave your kid an iPhone or iPad for their birthday, and are having second thoughts about it, don’t worry because you’re not alone. As tech-savvy as kids are, some parental oversight is still a good idea. The good news is iOS, the operating system that powers iPhones and iPads, has some built-in features […]
Social media has really made our lives transparent due to a lot of information we expose on it. Geo-tagging, sharing photos on social media and other digital footprints can leave you vulnerable to your service provider and several other data collecting websites. This can also lead to you being doxxed. If you are concerned about […]
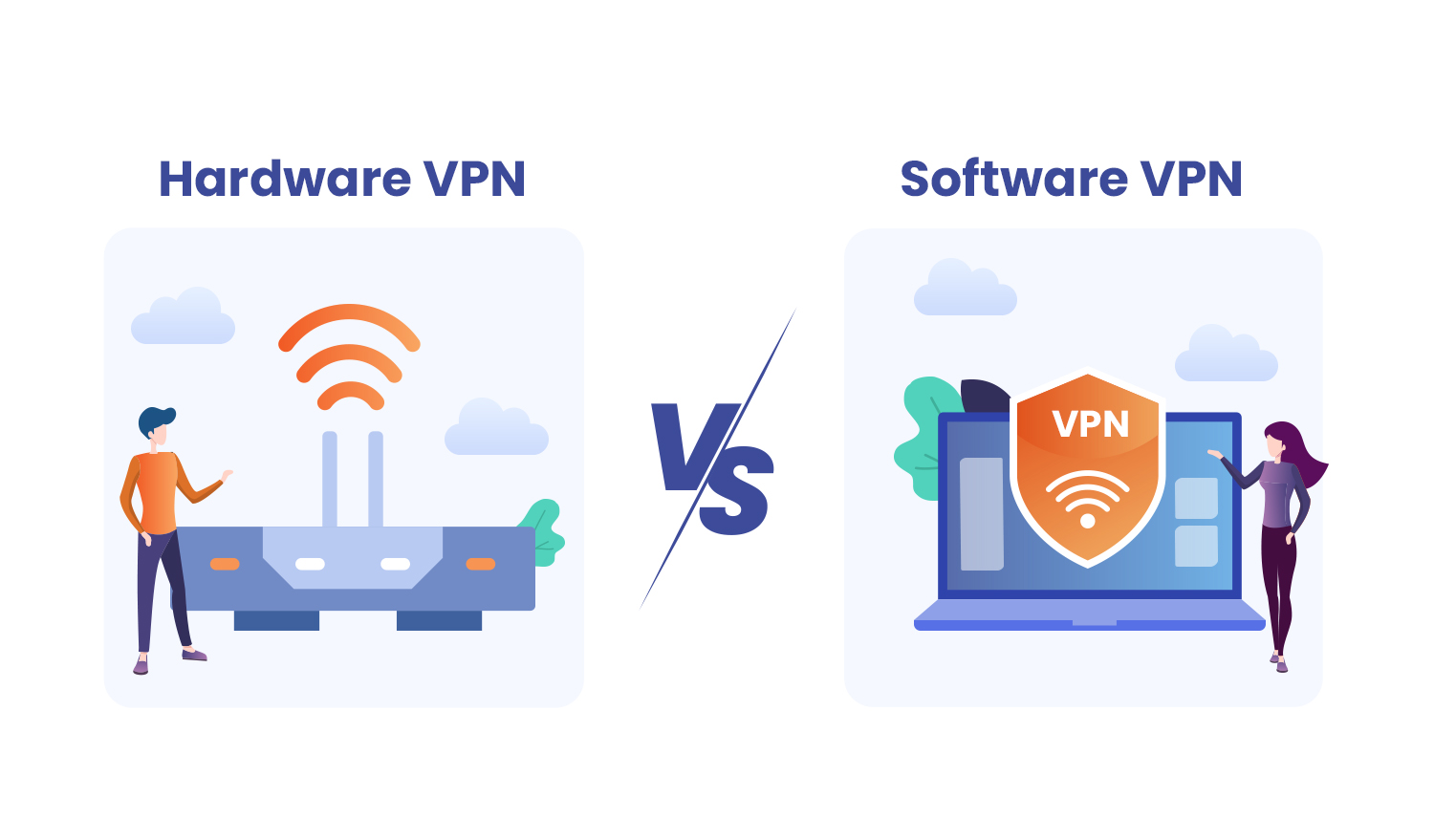
When it comes to security, there are two main types of VPN: software and hardware. Both provide different levels of protection and are capable of securing your online activities. The main difference between these two is the level of security they offer. However, both have pros and cons. So, let’s dig more in detail. What […]
If you decide which browser to use and wonder whether Microsoft Edge or Google Chrome is more secure and safe, it’s an important question since you want to protect your data and privacy online. They also have some key differences in handling your data and personal information that are worth considering. We’ll break down the […]
Are you having trouble accessing the web interface of your Xfinity router because you can’t find the IP address? Don’t worry, we’re here to help! Most Xfinity routers come with a default IP address of 10.0.0.1. However, if you’ve made any changes to the default settings, locating the correct IP address becomes crucial for accessing […]
Hey there, ever had the feeling someone was looking over your shoulder while you entered your password or PIN? That uncomfortable sense of being watched can be a sign your personal information is at risk from shoulder surfing. Shoulder surfing definition is when someone spies on you to steal your data or account access. They […]
Welcome to the internet age, where your personal information, from your name and address to your social media posts, can be found with a quick Google search. We know there are precautions and tools you can use to protect yourself online, but it’s not always enough. If you’ve had enough of living in an era […]
What should you do with all the junk stored on your computer? Declutter it, of course! With all of the junk files clogged up on your computer, it’s the best course of action to start removing them, since it also affects the performance of your device. The best part is that decluttering all the junk […]
With the proliferation of smart devices and the Internet of Things (IoT), the need for seamless connectivity and communication between devices has become increasingly important. One of the technologies that facilitate this seamless connectivity is Universal Plug and Play (UPnP). UPnP is a set of networking protocols that enables devices to discover and communicate with […]
Managing a consumer-based business with easy payment methods is the gateway to offering a smooth user experience. As businesses are shifting to digital and mostly e-commerce or online vendors are taking its place, every organization tries to keep their transactions safe. With the online business demand, the threat of data and financial breaches is also […]
It is ironic that some of the most popular websites on the planet that assure they do not collect data are seen to be violating privacy rules. The recent Facebook scandal is just one of the many news stories that have cropped up in the past few months that deal with the invasion of user […]