Google Chrome is one of the world’s most widely used web browsers. According to StatCounter, Google Chrome accounts for 62.85% of the global browser market share. As you can see, Google Chrome has a large user base, with billions of people using it as their default web browser.
And while Google Chrome is safe to use, it has its fair share of vulnerabilities.
A significant reason for these vulnerabilities is due to many factors, including the size of its codebase, the number of people using the browser, and the attraction of the target.
So, the larger the codebase, the more vulnerabilities there are. The more an application gets used, the greater the number of attackers that want to attack and are sneakily looking for ways to do so. Unfortunately, as popular as Chrome is, it is susceptible to online threats and Malware.
You may notice strange and subtle signs of something wrong with your browser.
You may be seeing unfamiliar browser extensions on Chrome or dozens of ads popping up, and you’re not quite sure how this is happening—all these point toward the sign that your Chrome browser is infected with malware.
If you’re concerned that your browser is hijacked and that your sensitive data might get compromised, then you’ve come to the right place, as we’ll address all of your concerns in this guide. We’ll walk you through all the steps you need to take to remove malware from Chrome and suggest the most effective ways to protect your device from future viruses and malware. So, if you’re ready, let’s get started.
Table of Contents
What Can I Do To Remove Viruses and Malware From Google Chrome?
One of the most effective ways to answer the pressing question of how to remove Malware from Chrome is to invest in reliable Antivirus software. Here’s how you can use an Antivirus software to clean malware from Chrome:
1) Use A Reliable Antivirus Software
The first step to remove malware and viruses from Google Chrome is to invest in reliable antivirus software. There are so many good antivirus software in the market, but essentially, excellent antivirus software meets the following criteria:
- It effectively detects and removes a wide range of malware, from trojans, viruses, and spyware to ransomware.
- It offers real-time protection and frequently monitors your system for threats to prevent malware from infecting your computer.
- It has an intuitive and user-friendly interface, making it easy to perform scans, navigate settings, and understand security alerts.
- The antivirus software is compatible with your operating system and any other software that you frequently use.
- It includes additional features like a firewall, email protection, secure browsing, and anti-phishing. Some antivirus programs also have tools to optimize system performance.
- A great antivirus program should run in the background without slowing down your system’s performance. Look for antivirus software optimized to have minimal impact on the computer’s resources.
2) Run An Antivirus Scan
Once you’ve chosen an Antivirus software that meets the above mentioned requirements and installed the program on your device, running a full system scan is time. Open the program’s dashboard or main window. Look for the system scan, click Start Scan, and once the antivirus software completes the scan, you can check and see if there are any threats on your device and then take steps to remove them immediately.
How Can I Remove Adware From Google Chrome?
So you’ve detected that there’s malware on Google Chrome, and you’ve invested in an antivirus program to remove the malware from your device. It’s now time to scan Chrome for adware and actively take steps to remove it from your device. Here are your top-notch solutions to remove adware from Google Chrome:
1) Reset Browser Settings
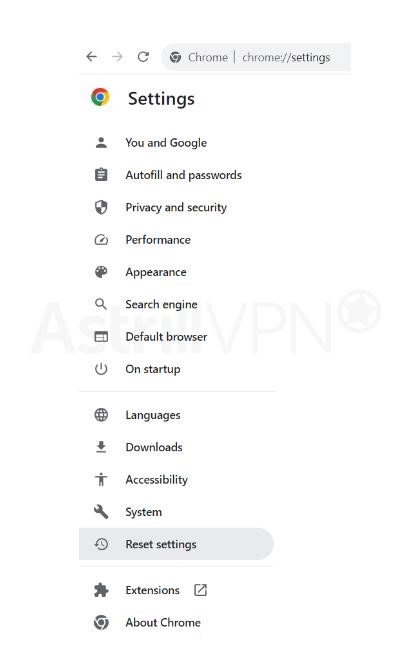
You will have to reset your browser settings to get rid of malware from Google Chrome. Here’s how you can do it:
- Open Google Chrome, click the three-dotted menu at the top-right corner of the screen, and then click on Settings.
- From there, click on Reset Settings.
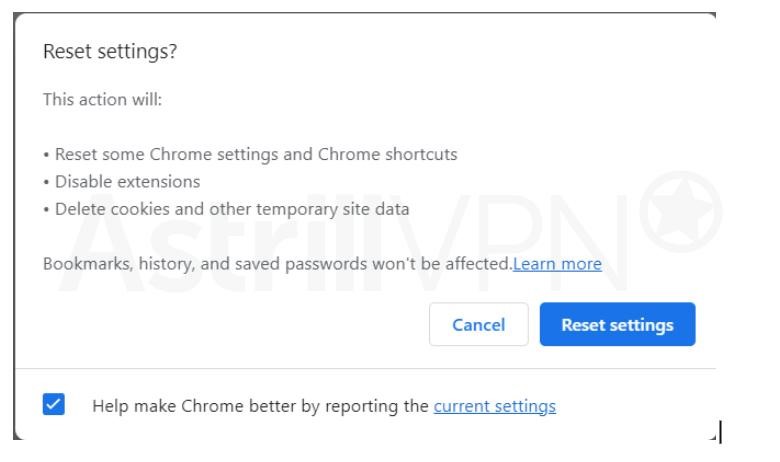
- Once you’ve entered, select Restore settings to their original defaults.

- You will then be shown a Reset verification screen to inform you what happens when you reset browser settings. Click the Reset settings button, and then you’re all set.
2) Remove Unwanted Browser Extensions
When there’s Malware on your browser, you will notice suspicious-looking browser extensions you don’t remember installing. Here’s how to remove sketchy browser extensions from Chrome:
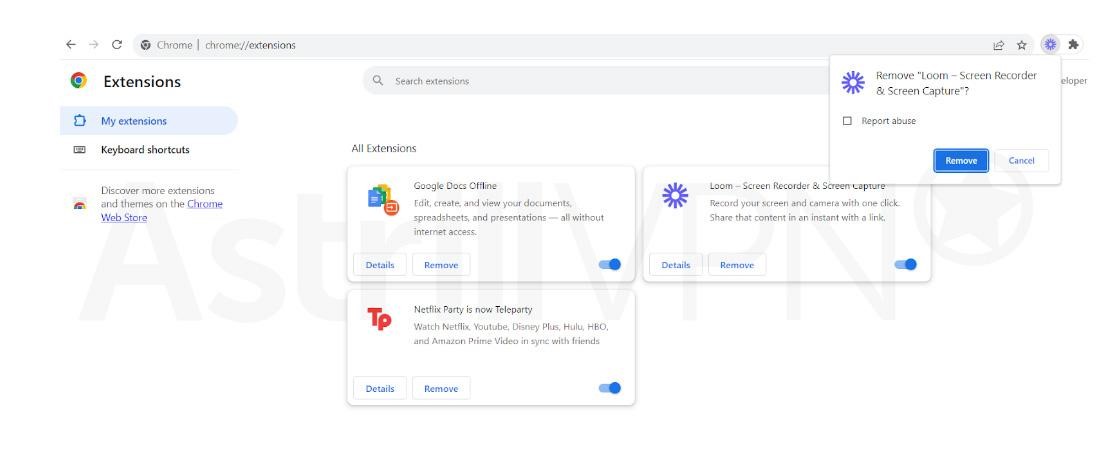
- Go to the Chrome browser, and once you enter, go to the address bar, type chrome://extensions, and then press Enter. You can also click the Puzzle icon on the top-right corner of the screen, and it will take you directly to the Extensions page.
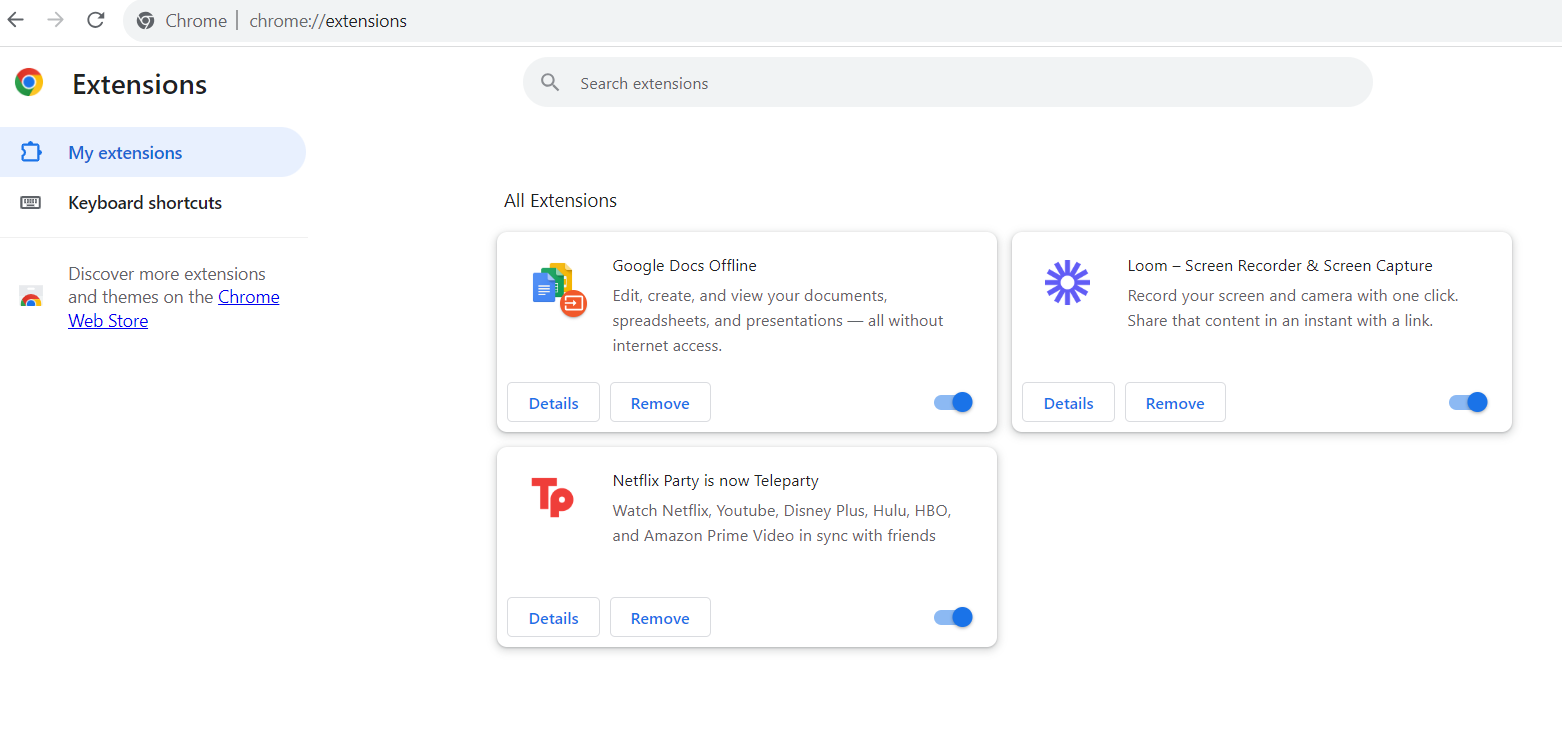
- Go to the Extensions menu. You can do this by toggling the sliders next to extensions you aren’t using. This will disable the extensions.
- The better step is to delete these extensions, which will cause more long-term harm and compromise your data. You can uninstall the extensions by clicking Remove and then Remove again.
3) Change Default Ads Permission
To prevent intrusive and misleading ads, you should change your default ad permissions on Chrome. Here’s how to do it:
- Go to Chrome, and at the top-right, click the three-dotted menu, click Settings, and then head to Privacy & Security.
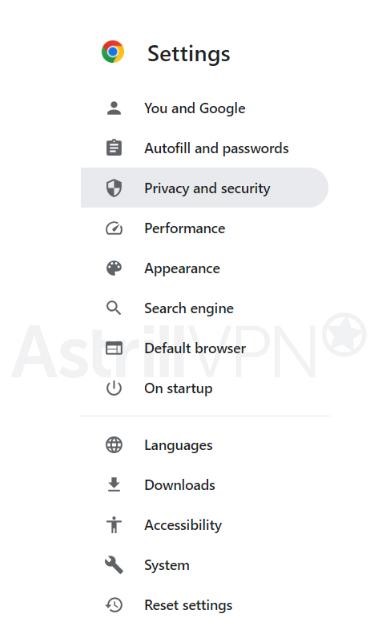
- From there, click Site Settings > Additional content settings > Intrusive ads.
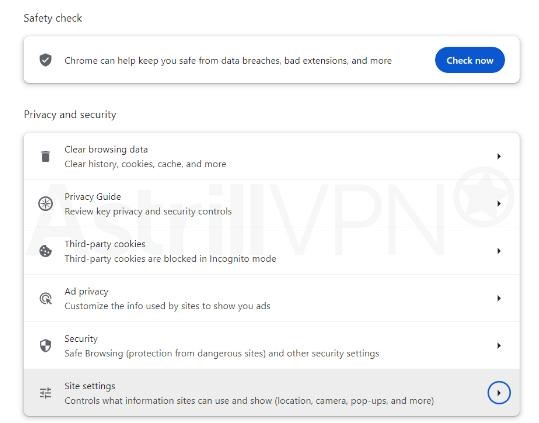
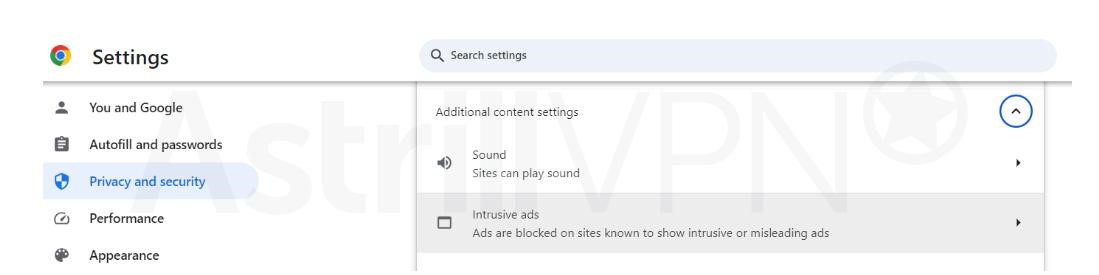
- You can then select the option you want as your default setting.
4) Use Safe Browsing In Chrome
You can protect yourself against Malware and other online threats by getting alerts about Malware, any fishy extensions, phishing, or any websites on Google’s list of potentially unsafe websites. Here’s how you can change your Safe Browsing settings on both Chrome and Android:
- Open Google Chrome on your device.
- Click the three-dotted menu and then click Settings.
- Click Privacy & Security and then select Safe Browsing.
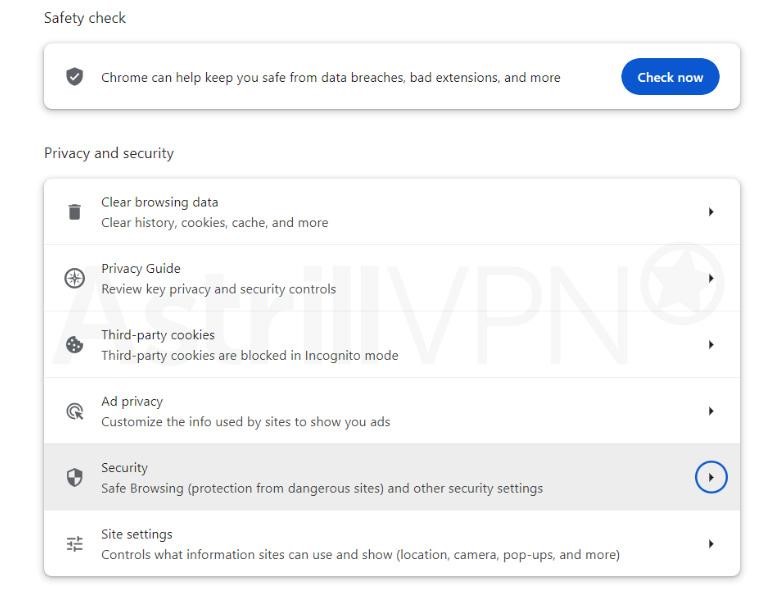
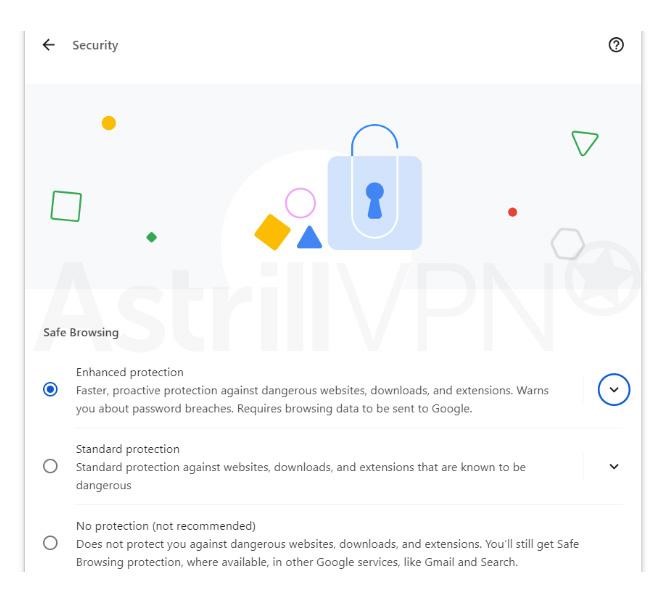
- Select the level of Safe Browsing that you want to use. You can choose between Enhanced protection, Standard protection, and No protection.
5) Block Pop-Ups & Notifications On Chrome
Google Chrome blocks pop-ups from automatically showing up on your screen by default, but if you’re still getting pop-ups after disabling them, it’s a sign that your mobile or computer is infected with Malware. To block pop-ups and redirects from a website:
- Open Chrome on your computer.
- At the top-right corner of the screen, click the three-dotted icon and then Settings.
- Click Privacy and Security and then go to Site Settings.
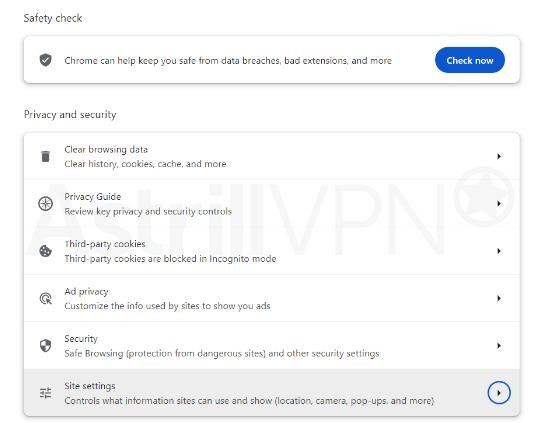
- Under “Allowed to send pop-ups and use redirects.”, find the website.
- To the right of the website, click the three-dotted icon > Block. If you can’t find the website listed next to “Allowed to send pop-ups and use redirects.”, click Add. Enter the site’s web address and then click Add.
You could be subscribed to notifications if you’re still getting notifications from a website after disabling pop-ups. You can turn off the notifications for the site by:
- Open Chrome and then go to the site you’re getting notifications from.
- Click View site information.
- Next to “Notifications,”select Block from the drop-down menu.
- You can also block the notifications from your site settings.
What Are Other Precautionary Steps I Can Take To Remove Malware From My Device?
In order to protect your device from Malware attacks and keep your data safe and secure from getting compromised by malicious actors, there are additional security measures that you can start implementing today. These include:
1) Remove Unwanted Applications From Your Device
You can easily remove adware and suspicious applications from your device by following these quick and easy steps.
Remove Unwanted Programs On Your PC
You must invest in a reliable antivirus for Windows, as it can scan Chrome for adware. You can also remove unwanted applications from Windows manually by following these steps:
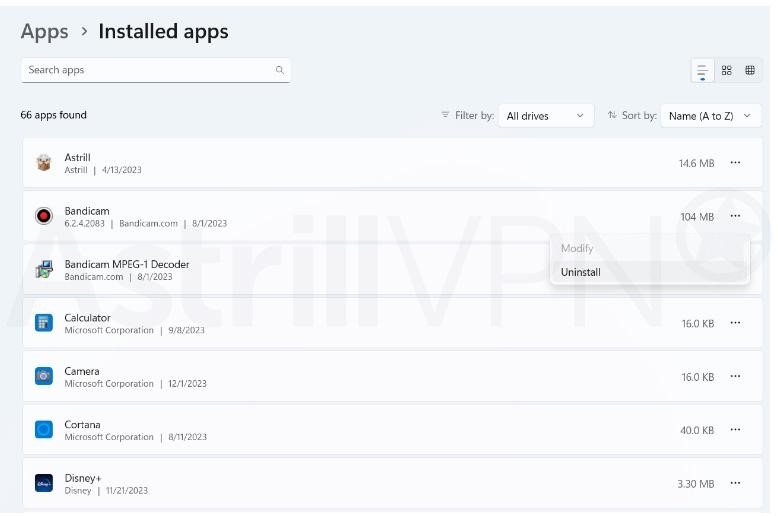
- Select Start and then select Settings.
- From there, go to Apps > Installed apps.
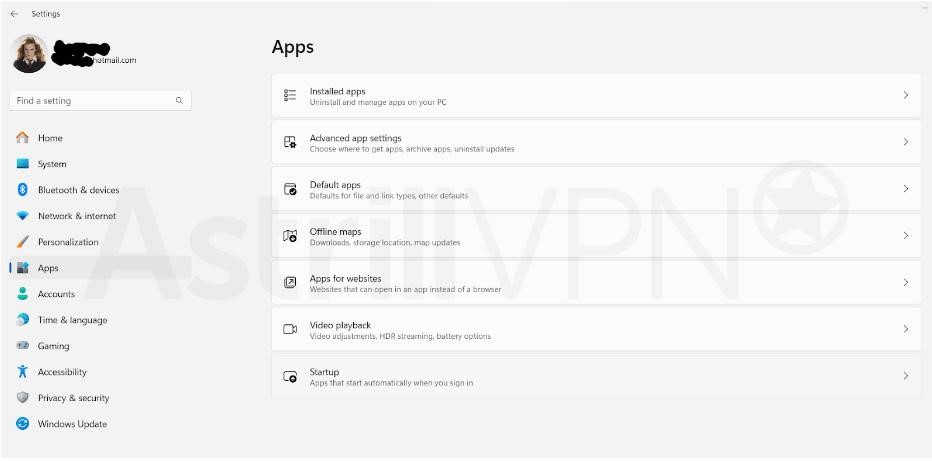
- Select the app you’d like to remove, and then click on the three-dotted line and click Uninstall.
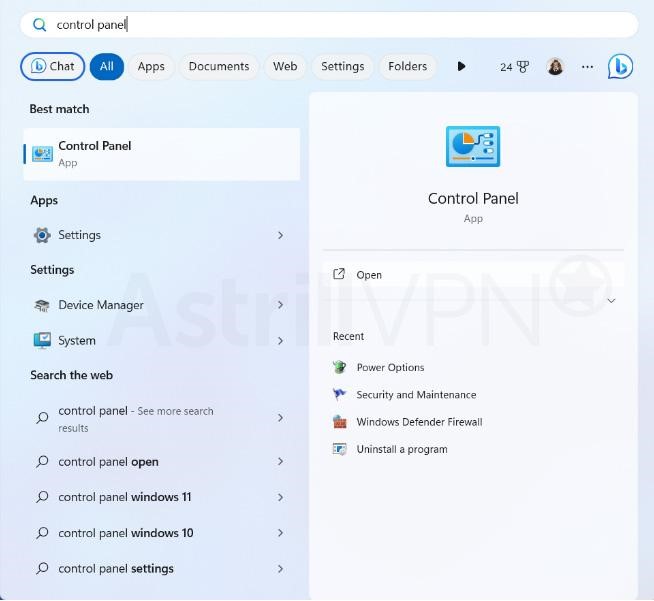
- You can also uninstall it from the Control Panel. Search for the Control Panel on the search bar and then open it.
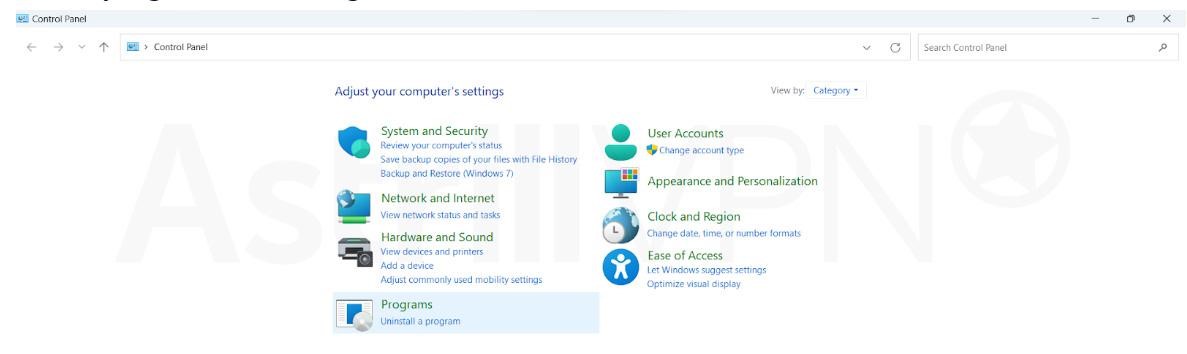
- Select Programs and then Programs and Features, or directly click on Uninstall a program under Programs.
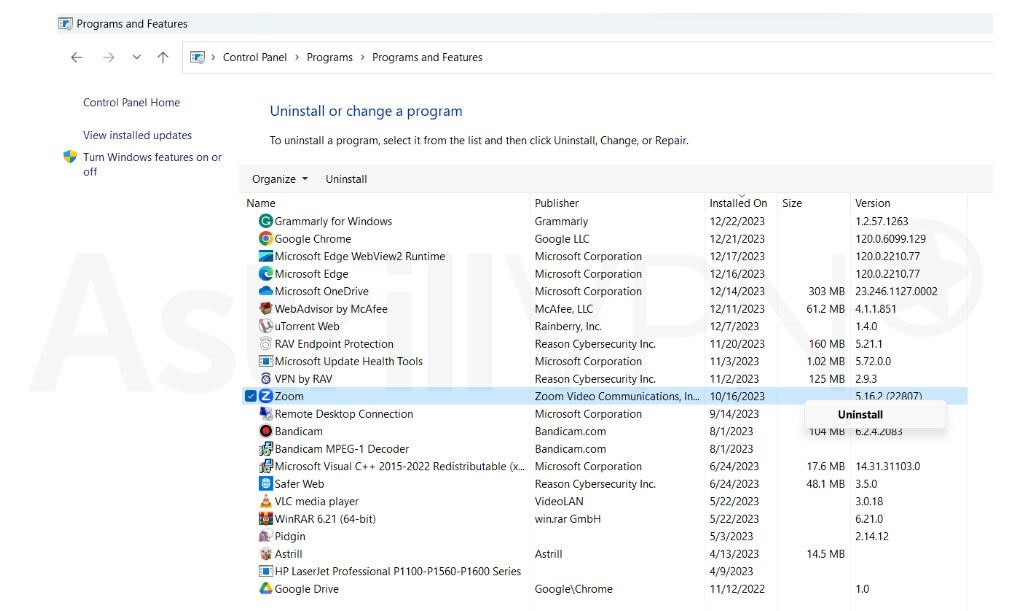
- Select the program/programs you’d like to uninstall, then right-click and select Uninstall. The program will then be removed from your PC.
Remove Unwanted Programs On Your Mac
You can also remove malicious applications from your Mac device manually. Here’s how you can do it:
- Open Finder.
- On the left side, click Applications.
- Search for any applications that you don’t recognize.
- Right-click the name of any suspicious and unwanted programs.
- Click Move To Trash.
- When you’re done with this, right-click Trash at the bottom.
- Click Empty Trash.
2) Invest In AstrillVPN
Although VPNs don’t necessarily help protect against Malware attacks and viruses, they do add an extra layer of protection and security by encrypting your internet traffic and masking your IP address, keeping your sensitive and confidential safe and secure from cybercriminals, malicious actors, and other third parties.
AstrillVPN comes loaded with a bunch of cool features that will take your privacy and security to the next level. It has a Kill Switch feature, Split Tunneling, and robust and state-of-the-art Encryption protocols from Wireguard to OpenWeb. It also adheres to a strict No-Logs Policy, meaning it will not store or record your online activities when using the VPN. Here’s how you can start using AstrillVPN:
- Download AstrillVPN directly from their website. They have download links for all the operating systems.
- Once you’ve downloaded and installed AstrillVPN, it’s time to Sign Up. You can Log In with your existing login credentials, or if you’re just joining, you can register for the app and then begin using it.
- Choose a preferred server location and change the protocols according to your needs and preferences.
- You can now turn the VPN connection on and leave the worries of malicious actors intercepting your data being a thing of the past.
What Are The Most Common Signs Google Chrome Is Infected With Malware?

So you have a sneaking suspicion your browser is infected with Malware, but you want to know for sure. Here are the telltale signs that Chrome has Malware:
- You see an unusual amount of unnecessary pop-ups and ads, and most of these ads and pop-ups are unrelated to the websites you’re visiting.
- The Malware on the Chrome browser can redirect you to unfamiliar websites, especially when you’re trying to visit trusted and popular websites.
- If you’re seeing unfamiliar browser extensions, and you don’t remember installing them, then that’s a sign the Chrome browser is infected with Malware.
- The Malware can change and alter your browser’s homepage settings, like changing your homepage and default search engine without your permission.
- Since Malware consumes system resources, it can lead to a decreased performance of your computer as well as a slow browsing experience.
- If your browser is experiencing more frequent crashes than usual, this could also be a sign of Malware interference, so it’s best to look into it immediately.
What Is The Google Chrome Virus?

Although there isn’t a specific Google Chrome virus, users might refer to various types of Malware or malicious software that can affect the Google Chrome browser or get distributed through it. These include browser hijackers, malicious extensions, adware, and other forms of Malware.
- Browser hijackers are programs that change the browser settings without the user’s consent. They can alter the homepage or the default search engine.
- Some extensions in Chrome are used for malicious intent. They can compromise your privacy, bombard you with unwanted ads, and engage in other harmful activities that can compromise your privacy.
- Other threats that can impact Google Chrome include adware software that displays unwanted advertisements in pop-ups or banners. They can be installed on your computer.
Recent Incidents Of Google Chrome Viruses
While Google Chrome is considered a safe browser, it is not immune to viruses and malware. There have been reports of Google Chrome viruses and malware in recent years. Let’s look at some of the recent ones:
1) ChromeLoader Malware
ChromeLoader is a persistent kind of Google Chrome browser hijacker discovered in 2022. ChromeLoader is a trojan that’s downloaded through drive-by-downloads or unofficial websites. Once installed on a user’s computer, ChromeLoader can steal their personal and confidential information and install other Malware on their device. By the middle of 2022, cybersecurity experts had uncovered new variants of this information-stealing malware, highlighting its feature set in a short period.
2) ClearFake Attacks
Security experts have also recently warned of increased fake browser update attacks, where users get tricked into downloading malicious software. Proofpoint, a security firm, has warned that they have observed increased dangerous activities using fake browser updates to deliver Malware. One of these attacks has been dubbed ClearFake, and these are found on infected websites.
When a user tries to access content on these sites, a pop-up appears, urging the user to update their browser to the latest version before they can access the content on the site. When users click the fake update button, it automatically installs malware designed to steal their personal and confidential details.
3) Rilide Stealer Chrome Browser Extension
The malicious Rilide Stealer Chrome browser extension has returned in new campaigns by targeting crypto users and enterprise employees to steal crypto wallets and credentials. Rilide is a malicious browser extension for Chromium-based browsers, which includes Chrome, Edge, Brave, and Opera, discovered by Trustwave SpiderLabs in April 2023. The Rilide browser extension impersonated the authentic Google Drive extensions to hijack the browser, monitor user activities, take screenshots, and steal information like email account credentials and crypto assets.
How Can I Avoid Malware In The Future?
To ensure that you don’t become a victim of Malware in the future, here are the most effective tips and tricks to help you avoid them in the long run:
- To avoid Malware in the future, be cautious of websites that may cause you to download unwanted software. For example, you’re able to get copyrighted content at no charge.
- Beware of warnings regarding viruses or infected devices, mainly if you haven’t used a virus scanner.
- Be on the lookout for encrypted archives, like .zip files, that require passwords and may bypass antivirus detection scans.
- Avoid insecure connections when visiting websites, and don’t download files from sites that don’t start with HTTPS. HTTPS websites are secure and encrypt your data.
- If a pop-up about a download or program update seems suspicious, don’t click on it. Instead, it would help if you went to the program’s official website to download it.
- Do pay attention to the Safe Browsing’s download warnings. Cybercriminals may ask you to turn off or ignore the warnings to avoid antivirus detections.
Final Thoughts
Having your Chrome browser get infected with malware can be scary, and you might not know how to tackle this issue, but this guide provides you with all the tools you need to get rid of malware from Chrome for good. You can protect your devices and sensitive and confidential data by removing suspicious and unwanted programs from your device, resetting your browser, investing in reliable antivirus software, and using a VPN as an additional security measure. The first key to protecting yourself is to identify the signs of Malware early on so that you can take quick action. Once you do that, you’re all set.
Frequently Asked Questions (FAQs)
Although Google doesn’t provide any programs to remove Malware, Google Chrome offers Safe Browsing, allowing applications to check URLs against Google’s updated list of suspected phishing and malware pages.
Google checks websites to see whether they host software or downloadable executables that can negatively impact the user experience. The Security Issues report shows you a list of suspected files hosted on your site.
Reinstalling Chrome can remove Malware, especially if the Malware is specific to the Chrome browser.
There are good tools in the market that can help you remove Malware for free, but investing in a premium service for additional features and more security against viruses and malware is good.
Although many types of Malware are out there that are difficult to remove, a rootkit has proved to be quite challenging to remove because it gains root-level access to a system while trying to ensure it stays undetected.


No comments were posted yet