How to Safely Remove Chromium Virus: Step-by-Step Guide

Google Chrome is one of the most popular browsers in the world, yet you may not have ever heard of another one of Google’s web browsers known as “Chromium.” While the names are similar and related, they represent two different web browsers. Chromium is an open-source project that forms the foundation of several popular web browsers, including Google Chrome. While it doesn’t have the spotlight Chrome does, it still holds on its own as it has been innovative for the digital landscape.
So what exactly is the Chromium Browser, and what happens when you experience a Chromium Virus on your device? This in-depth guide will answer all of these questions and give you the ins and outs of Chromium Malware and all the practical steps you can take to remove it from your devices instantly. So, with that out of the way, let’s get started.
Table of Contents
ToggleWhat Is The Chromium Browser?

Chromium is a free, open-source web browser project developed and maintained primarily by Google. It aims to build a faster and stable way for users to experience the web. It generates the source code used by Chrome, Edge, and other browsers. When Google Chrome was introduced in 2008, the Chromium source code also became available. Other people can contribute to the project since it is open source.
To create Chrome, Google incorporates its propriety features, branding, and other services on top of the Chromium code. Since it is an open-source project, Chromium has a robust set of developer tools known as DevTools, meaning developers can contribute by debugging and optimizing websites and web applications. The Chromium project is frequently updated and improved by a community of developers and other contributors.
The name “Chromium” originates from the fact that Chromium provides the major source code for Google Chrome; hence, the term “Chromium” was chosen by Google since chromium metal is used for chrome plating. Here’s how Chromium differs from Google Chrome:
- Chromium does not have automatic browser updates.
- Chromium does not have the API keys for some Google services, including browser syncing.
- It does not have proprietary multimedia codecs (like H.264 media support and AAC audio formats).
- It does not have tracking mechanisms for usage and crash reports.
- New features and updates get integrated into Chrome quickly and may require less extensive testing than Chrome.
- Some users think Chromium has more privacy benefits as it doesn’t collect the same level of data or integrate with most Google services the way Google Chrome does.
How Can You Detect Chromium Virus On Your Device?
Although the Chromium browser is as safe as Google Chrome when downloaded from a trusted source, hackers use it to spread Malware since it’s an open-source code. Unfortunately, fake versions of Chromium on the internet are created specifically to steal your data and install Malware on your devices.
A fake version of Chromium can infect your device with viruses and Malware and redirect you to sites hosting malicious software or Phishing sites that compromise your private and confidential data. Detecting a Chromium Virus will help you remove Chromium Malware instantly before the damage is done. You should know the exact signs and symptoms to remove them from your devices promptly. Here are some of the significant signs your device is infected with Chromium Malware:
- If you notice that the Chromium icon (the same as the Google Chrome icon but with different colors) suddenly appears on your desktop even though you never downloaded it or installed it from the Chromium website.
- Your CPU usage becomes high, and your device starts performing much slower.
- You get random pop-ups and advertisements even when you’re not using the internet.
- You may notice unwanted browser extensions and add-ons without your consent.
- Your browser crashing frequently and getting unexpected error messages may indicate problems with the browser or Malware on your device.
- Your homepage has changed, or the homepage on your Chromium browser isn’t automatically set to Google.
How Can You Remove Chromium Virus From Your Computer?
So you’ve detected a Chromium Virus on your device, and you’re asking yourself, “How can I remove Chromium Malware from my device?”. Well, you’re in good hands as we’ll walk you through the exact steps you need to take to remove Chromium Virus from your device, depending on the operating system you’re using. We’ll also discuss how you can remove it from the different browsers. So, without any further ado, let’s begin.
How To Remove Chromium Virus From Windows
- Open the Window’s Start button, which you can find on the bottom left, and type “Control Panel.” Open Control Panel.
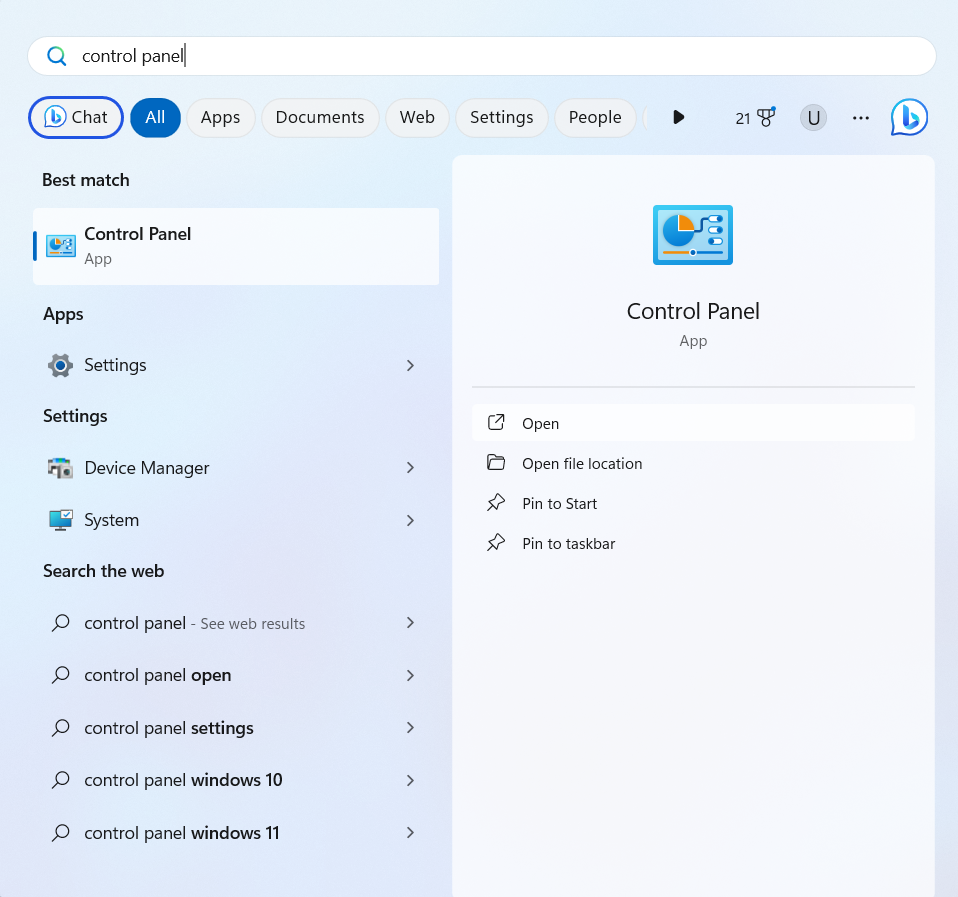
- Once you’ve entered the Control Panel, click on “Programs.”
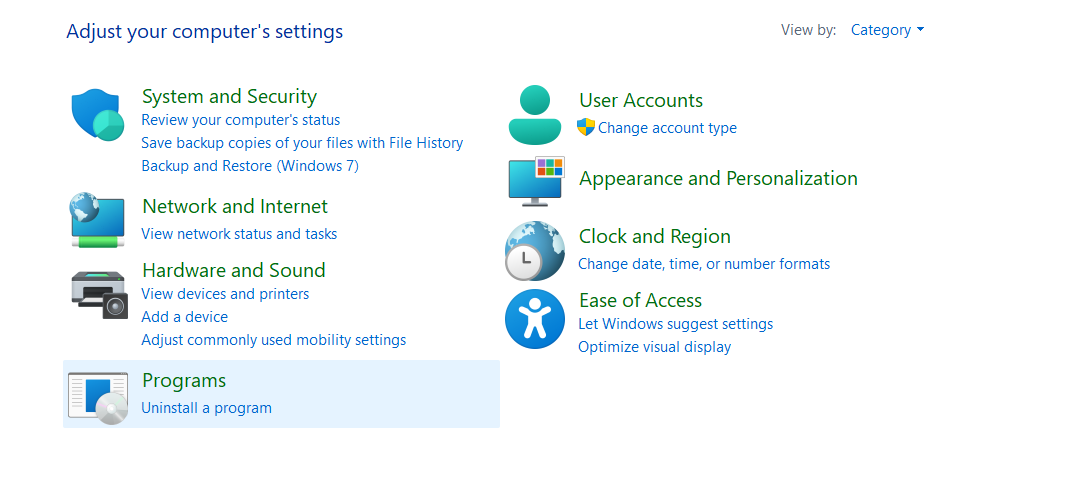
- You will then see a list of applications installed on your device. You can click on the “Installed On” section, which will list the applications in the order in which they were installed. You can use it to uninstall any recent applications you’re unfamiliar with.
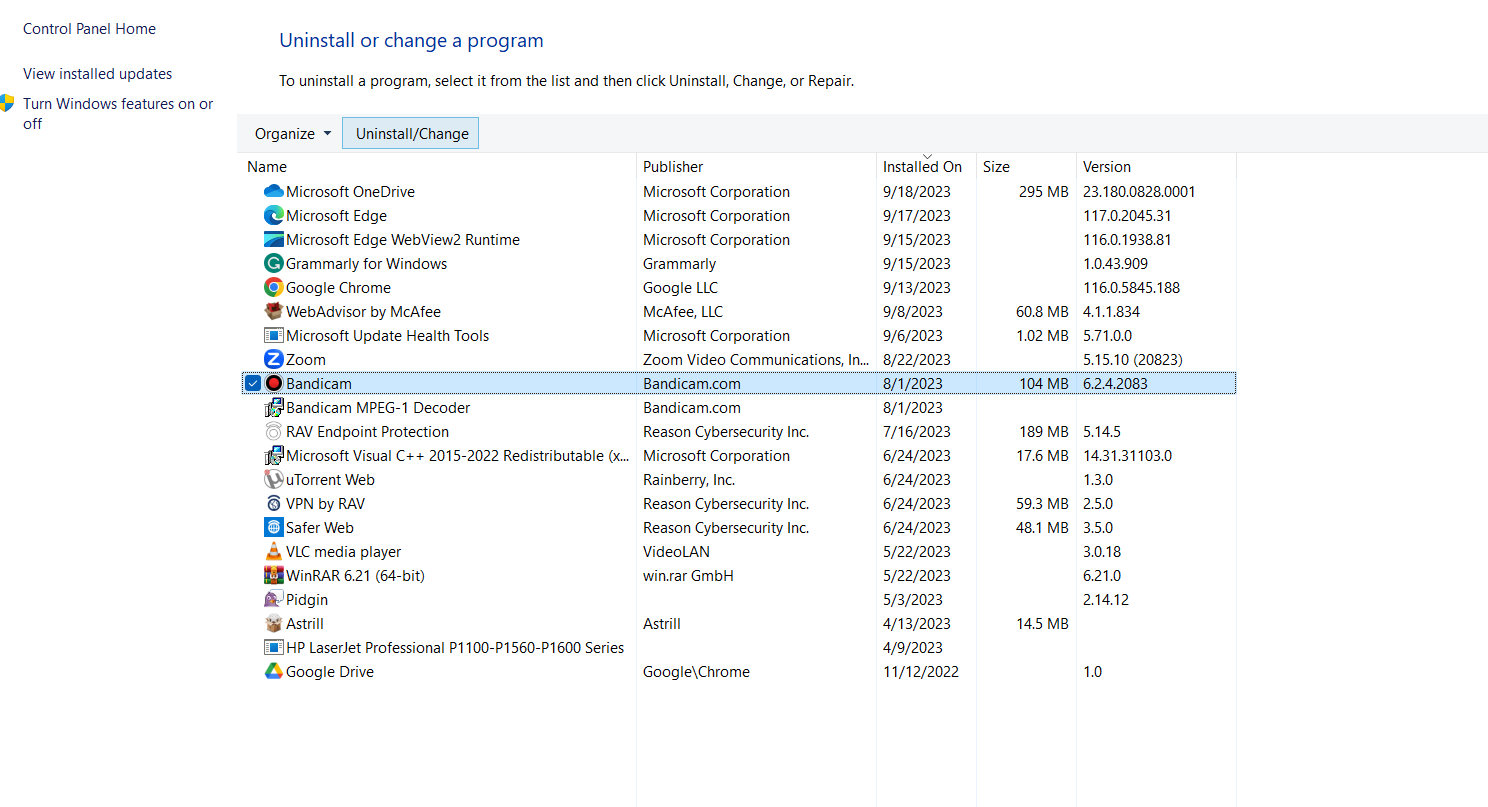
- Click Uninstall, and Windows will remove the selected applications from your device.
How To Remove Chromium Virus On Windows Manually
You can also get rid of Chromium browser manually from your device.
- Go to the Windows icon at the bottom left and search “Task Manager.”
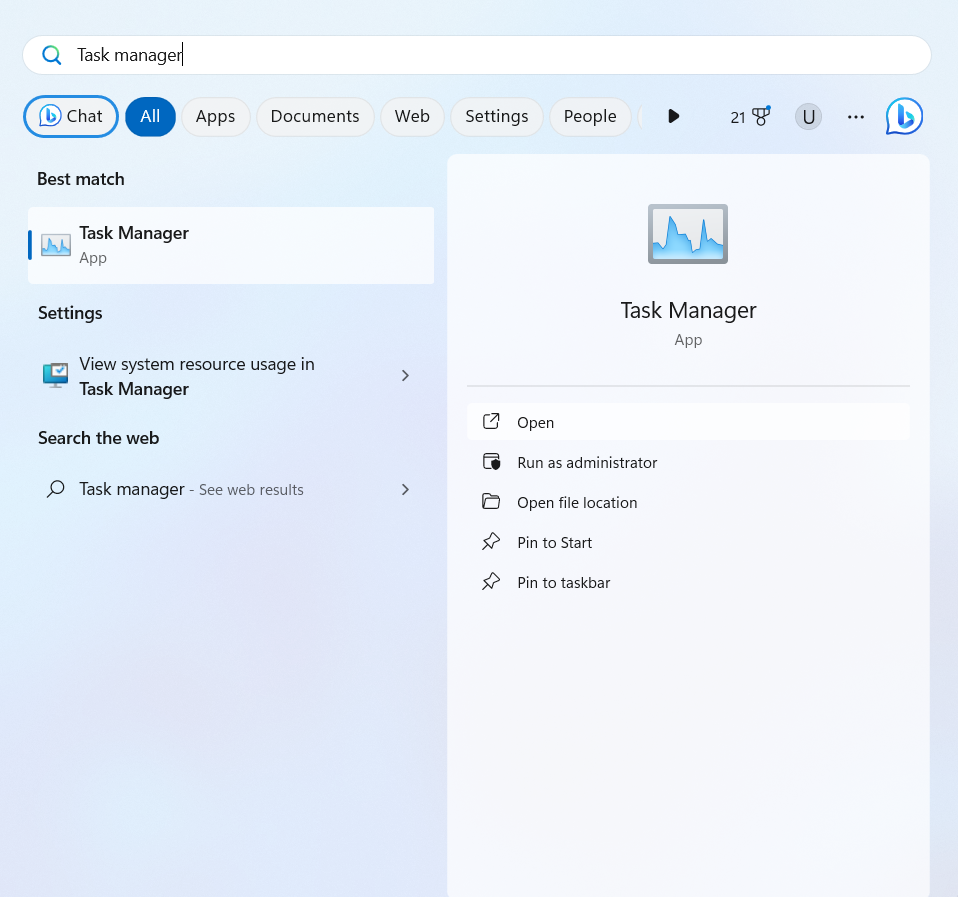
- Open the Task Manager, select Chromium, and right-click “Open file location.”
- Select all the files and then click “Delete.“
- After that, go back to “Task Manager,” select Chromium, and click “End task.” Empty the Recycle bin afterwards, and Chromium will be removed permanently.
How To Remove Chromium Virus From macOS
- Click on the “Finder” icon in the left corner of the Dock.
- Click “Applications,” which you’ll find on the left side.
- Use the Search Bar on the top right corner of the screen and type “Chromium” to find the infected application or other applications that you find suspicious.
- Drag the infected application to the “Trash” bin icon. Click and hold the Trash Bin icon until “Empty Trash” appears. Click on it to remove it from your device.
How To Remove Chromium Virus Manually From macOS
If you cannot find the virus files in your apps or the places we’ve mentioned above, there’s a way for you to remove them manually instead. However, make sure you know the name of the virus file because if you accidentally delete something else, Here’s how:
- Click “Go” and select “Go to folder” from the drop-down menu.
- Type “/Library/LauchAgents/” and press “Go.”
- Delete all virus files that have a similar name or the same name as Chromium.
- If you don’t find any such files, then don’t delete anything. You can also repeat the same process by typing in other library directories like “/Library/LaunchAgents” and “/Library/LaunchDaemons.”
How To Remove Chromium Virus From Web Browsers
Here’s how you can remove Chromium Malware from your web browsers:
Google Chrome
- Open Google Chrome and click the three-dotted menu in the top left corner.
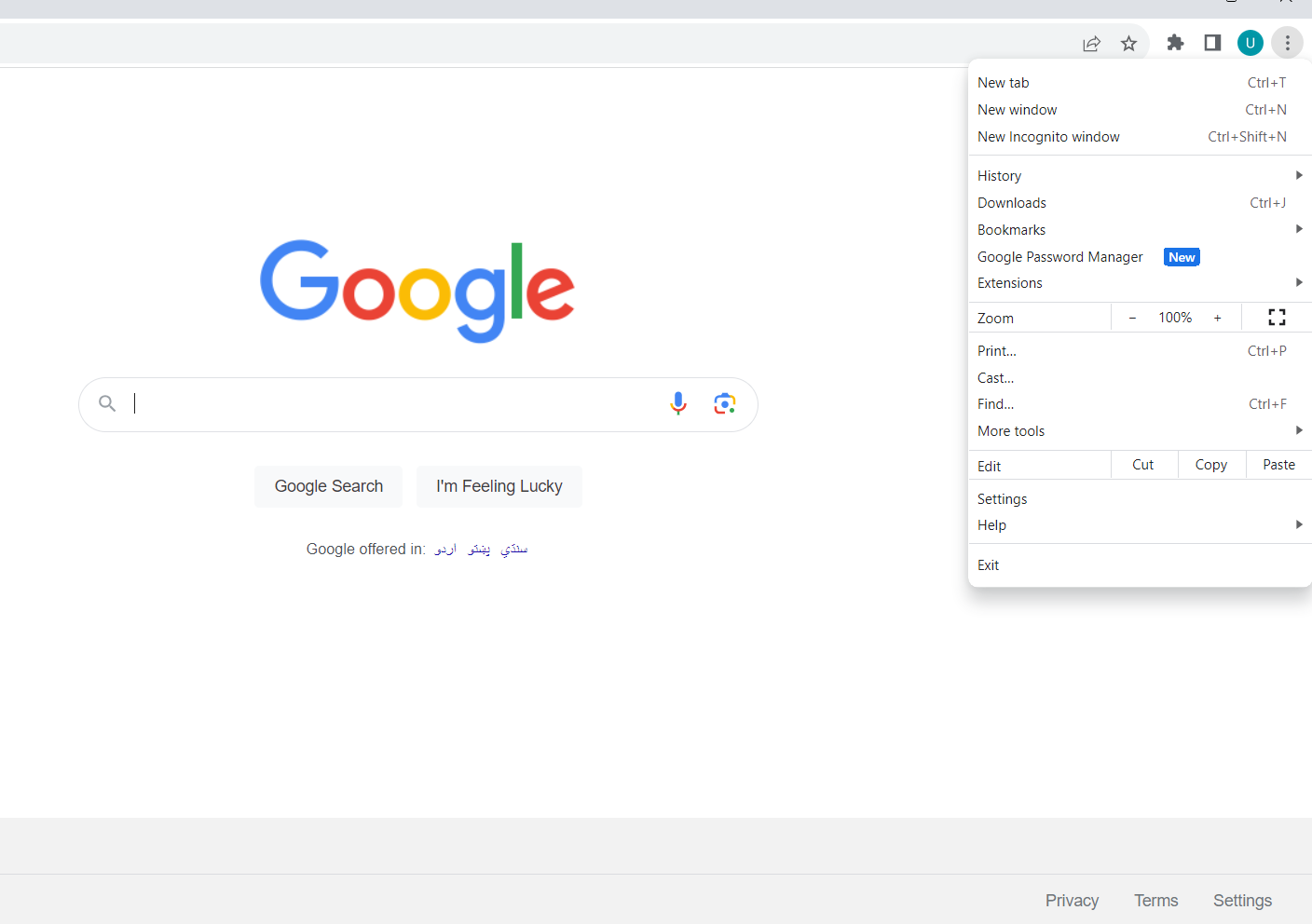
- When you’ve opened the menu, click on “Extensions” and then click on “Manage Extensions.”
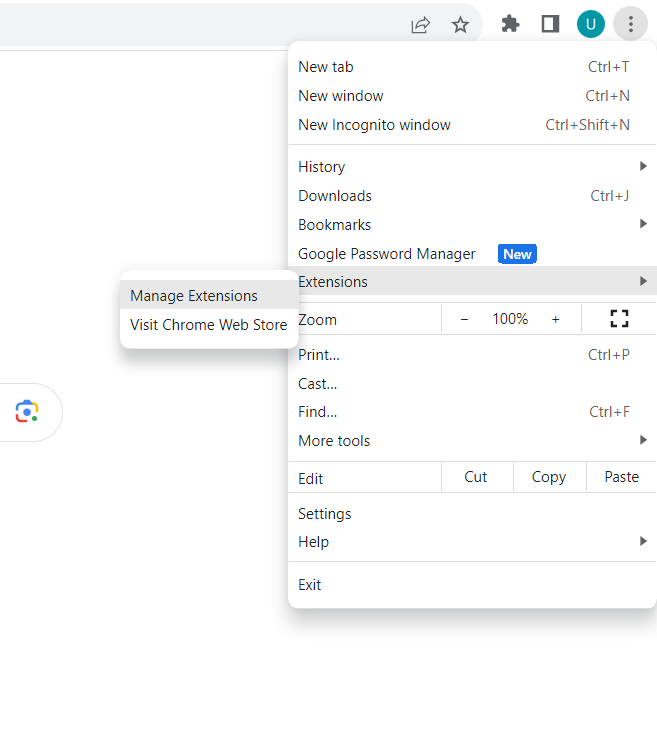
- If you find suspicious extensions or don’t recall installing them, click “Remove” to wipe them from your device.
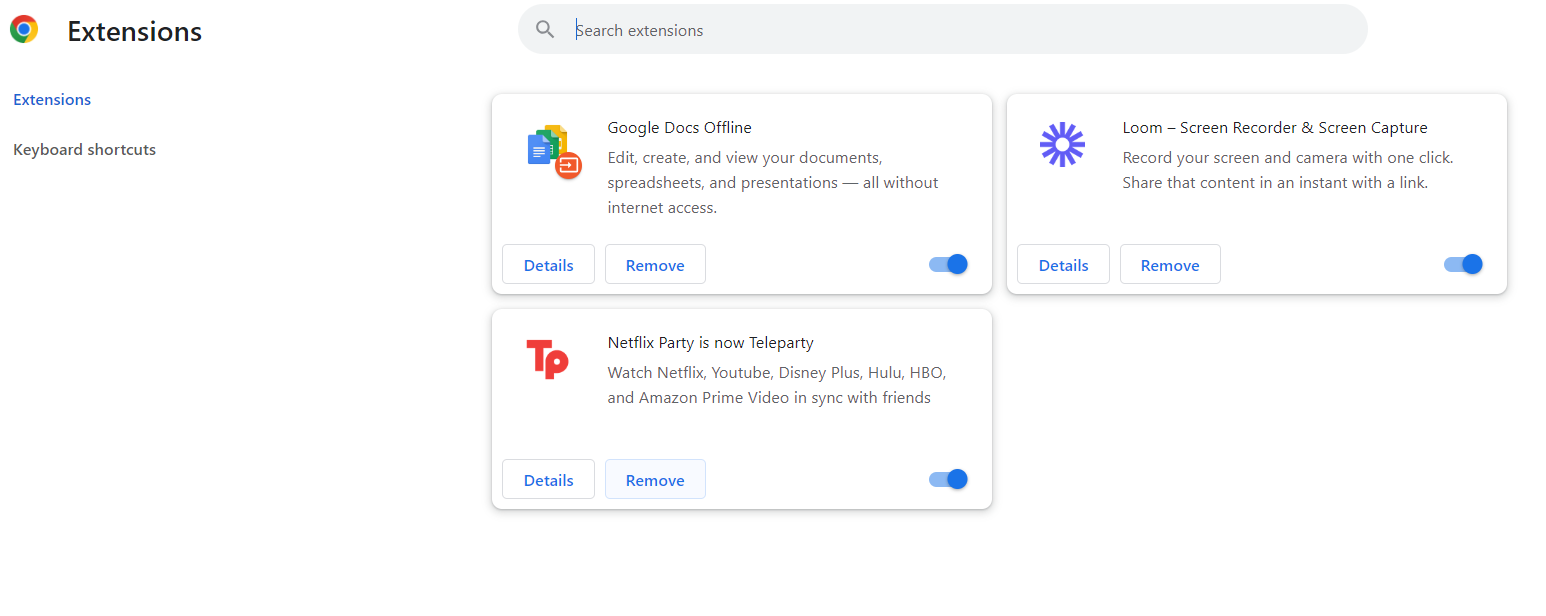
- Once you’ve removed the extension, you can close Google Chrome and reopen it to see the changes.
Safari
- On the top left corner of your screen, open Safari.
- From the drop-down menu, click on “Preferences.”
- Choose “Extensions” and “Uninstall” from there to remove any suspicious add-ons.
- A pop-up Window will appear asking you to confirm if you want to uninstall the extension. Select “Uninstall” again to remove the infected application from your device.
Mozilla Firefox
- Open Mozilla Firefox and click on the burger menu in the top right corner of the screen.
- Select the “Add-ons” option from the menu.
- Open and select all the extensions you want to remove.
- Click the “Remove” button on the suspicious extensions you want wiped from your device, and you’re all set.
Microsoft Edge
- Open the Edge Browser.
- Open the three-dotted menu by clicking on the top right corner of the page.
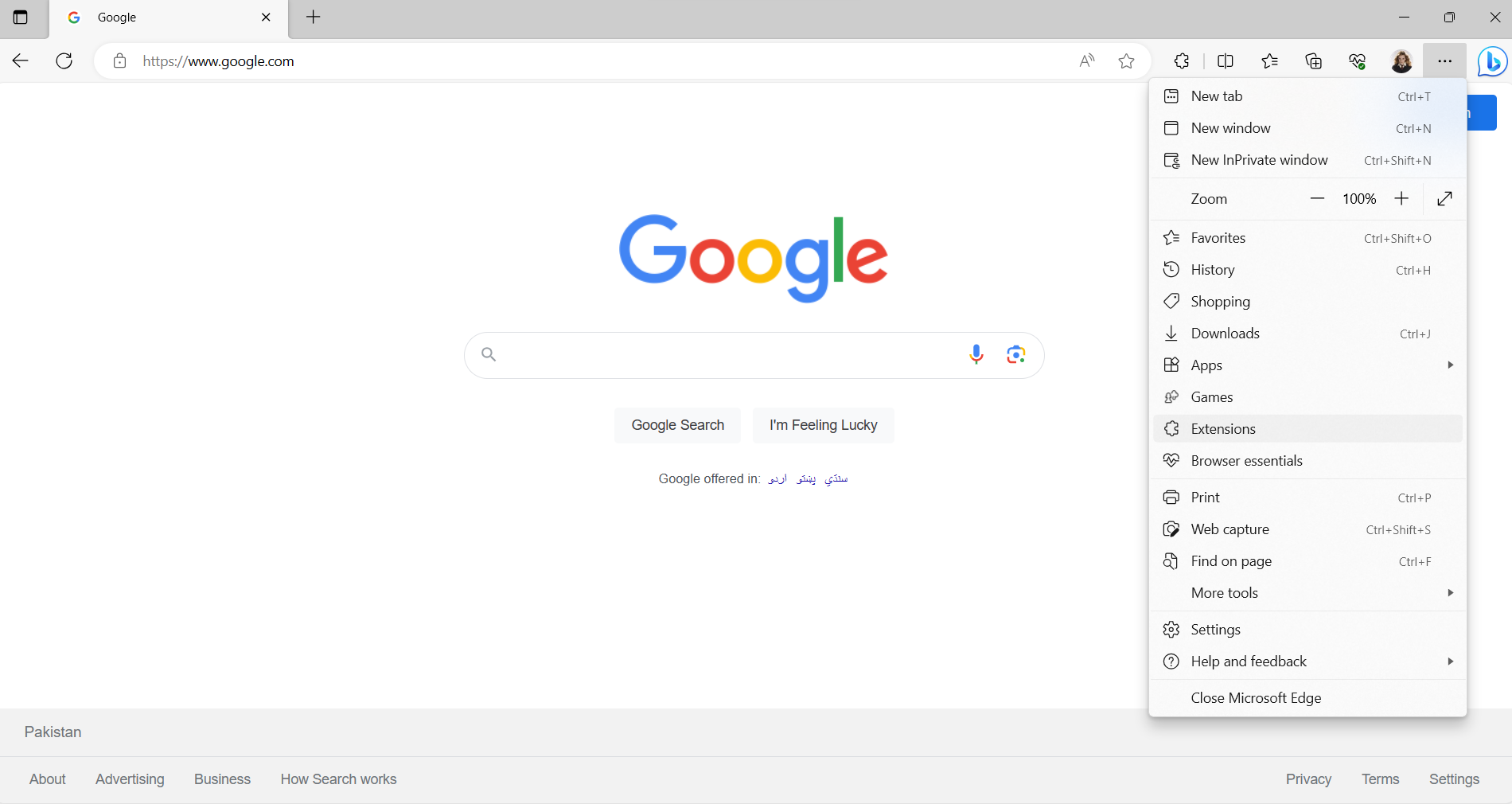
- From the drop-down menu, select “Extensions”.
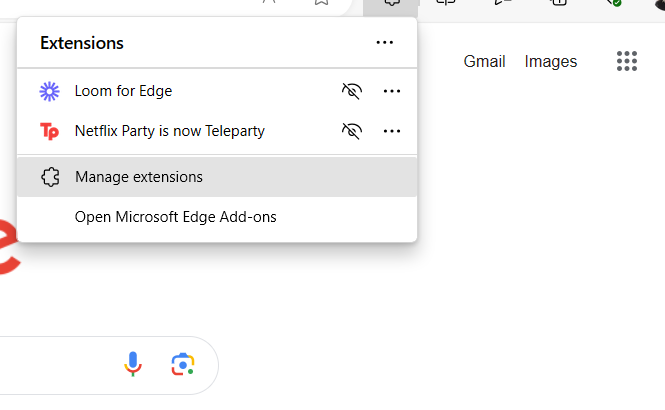
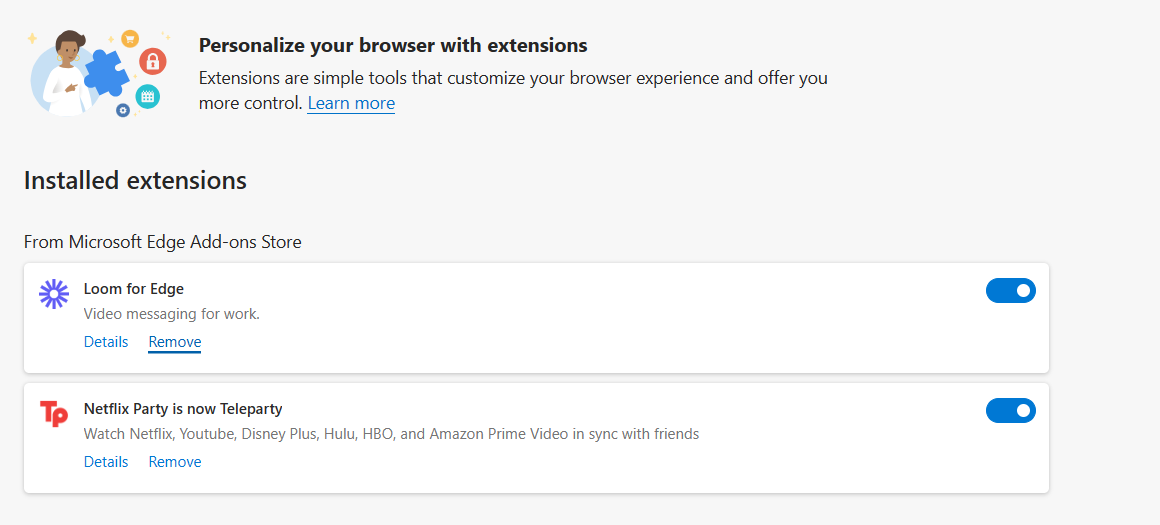
- After that, select “Manage Extensions” and then select Remove at the bottom of the suspicious extension you want to remove.
How To Protect Yourself Against Chromium Virus?

There are various ways through which you can protect yourself against Chromium Malware. Here’s what you can do:
1) Keep Software Updated
Outdated software, drivers, and operating systems are the perfect targets for Malware attacks since attackers exploit this vulnerability. Hackers exploit these vulnerabilities to deliver Malware to your system. You must ensure that your operating system, web browsers (including Google Chrome and Chromium), and other software on your device are up-to-date and have all the latest security patches and updates.
Software updates enable fixing bugs and security enhancements to protect your device against malicious software. Also, allow the auto-update option so that applications can update as soon as you start using them. Go to Application Settings if you weren’t automatically asked to enable this feature as soon as you installed the application.
2) Use Reputable Links & Sources
Always make sure that you’re clicking a reliable link. If you feel a slight hint of suspicion, there’s something wrong. Only click legitimate links; always download and install programs from official sources. Download software and browser extensions from reputable sources like the Chrome Web Store for Chromium and Chrome Extensions. Avoid downloading software from third parties that you don’t trust or don’t have that much information about.
Web attacks like drive-by-download are prevalent, where you automatically download Malware into your system when you click on a suspicious link. Also, never open email attachments you think are suspicious or not coming from a reliable source or someone you trust.
3) Use A Reliable Antivirus Software
Installing reliable Antivirus software will enable you to detect Malware and viruses before any damage is done. Sometimes, it’s hard to track what gets into your device, so installing quality Antivirus software will tell you if it detects a virus or if you’re about to access a harmful website with malicious links.
Excellent and reliable Antivirus software will keep your online experience safe by intercepting malicious downloads and websites before you can access them. It will also help you mitigate the risk of, let’s say, Ransomware attacks by automatically creating backups of all your important files and data. It should also offer real-time scanning of files and internet traffic to detect and remove threats immediately as they occur. These are essential factors you must look into when investing in Antivirus software.
4) Use A VPN
It is always risky when you’re using a public network. You have no idea what kinds of people are connecting to public WiFi, and public networks give hackers an easy way to not only distribute Malware to your device but also look at your online activities. To avoid your data getting into the wrong hands when you’re using a public network, a VPN (Virtual Private Network) comes into the picture.
A VPN encrypts your internet traffic and masks your IP address, protecting your data from getting intercepted by malicious actors and other third parties. AstrillVPN has a range of security features, including a Kill Switch, robust VPN Protocols, a Split Tunneling feature, and a strong No-Logs Policy, ensuring that your online activities remain anonymous and that no cybercriminals can infiltrate your data. Here’s how you can use AstrillVPN:
- Sign Up for AstrillVPN or Log In using your credentials. You can download AstrillVPN directly from their website or go to the App Stores and install it from there.
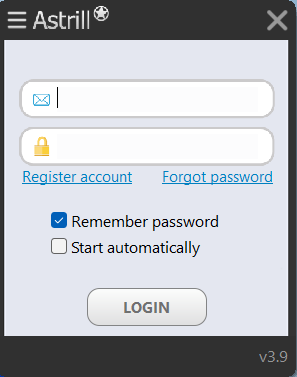
- Log In To AstrillVPN with your credentials.
- Once you’ve logged in, you must choose a server location you wish to connect to.
- Once you’ve chosen a server, you can click the toggle switch to turn the VPN connection on, and you’re all set!
5) Using Strong Passwords and enabling Two Factor Authentication
Creating strong and unique passwords would be best to prevent your online accounts from getting compromised. It would be best to have passwords with uppercase lowercase letters, numbers, and special characters. Having unique passwords for your browser and email accounts would be best. It would be best if you used a reliable Password Manager to enable you to manage all your passwords securely.
You should also opt for Two Factor Authentication. 2FA adds an extra layer of security by requiring additional authentication before you can access your online accounts. So, if you’re logging into your accounts, you must provide biometric verification or an OTP (one-time password), which will be sent to you on your phone number or email address.
Final Thoughts
Although Chromium browsers themselves are safe, malicious actors create fake Chromium browsers to infect users’ devices with Malware and compromise their confidential data. By detecting the signs of Chromium Malware early on and taking the appropriate preventative measures, you’ll get rid of Chromium Malware in no time.
FAQs (Frequently Asked Questions)
The Chromium virus is a malicious web browser created using Chromium’s code. Chromium itself is not a malware or virus. Malicious actors can sometimes create fake versions of Chromium or combine them with potentially unwanted software to deceive users. The unwanted programs can exhibit virus-like behaviors, tracking a user’s online activities and displaying excessive ads.
If Chromium has installed itself on your computer, it means you’ve downloaded potentially unwanted software with a malicious version of Chromium. Your computer has likely been infected with the Chromium virus and Malware.
The Chromium browser is an open-source project, and developers are constantly contributing to the project. Chromium is as safe as Chrome if you download it from a reliable source.
Chromium is safe to use and is considered better for user privacy when compared to Chrome. Chromium itself is not Malware, so there’s no cause for concern. However, you should check your Chromium folder and look for red flags pointing to a malware attack.
The Chromium browser will cause no harm to your device and is safe to use if downloaded from a trusted source. There’s no harm in using the Chromium browser, and it is as safe as Chrome.
Fake Chromium browsers are spread through software bundles, distributed through software bundles, and sneak into a user’s device without their knowledge. Ads support these fake browsers and come with several suspicious browser extensions constantly delivering third-party ads to the victim.


No comments were posted yet