How do you know if your phone is hacked [Updated]

Arsalan Rathore
![How do you know if your phone is hacked [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/07/How-to-know-if-your-phone-is-hacked-1-800x470.jpg)
If something feels ‘off’ with your phone, it most likely is a warning sign for something more sinister. You might’ve noticed that your phone has started having minor glitches. Perhaps it may restart itself throughout the day without any prompt. It may also constantly be warm to the touch, even when you haven’t used it excessively.
You may even see that your GPS has enabled or disabled yourself, and your call log or messages inbox is filled with data you haven’t typed out. This is typically paired with greater data and internet consumption beyond your typical usage.
These odd snags are not glitches. They are the most common signs reported by users with compromised device security. One other evident and frightening sign is that you may simply lose access to all of your device’s features.
Table of Contents
Is it possible that someone can hack my phone?
Yes, it is indeed possible for someone to hack your phone. Mobile devices are increasingly becoming targets for cybercriminals due to the vast amount of personal information they store. Hackers employ various methods to gain unauthorized access to your phone, including:
Phishing Attacks
Cybercriminals often use deceptive emails, text messages, or websites to trick you into revealing your personal information. These phishing attempts can look very convincing, often mimicking legitimate companies or contacts. Once you enter your details, the hacker gains access to your accounts and personal information, and you won’t notice any phone hacking symptoms.
Malware and Spyware
Malicious software can be installed on your phone by downloading fake apps, clicking on suspicious links, or even opening infected email attachments. Malware can steal your data, monitor your activity, and even control your device remotely. Spyware, however, specifically tracks your activities, such as text messages, call logs, and browsing history, without your consent.
Public Wi-Fi Networks
Unsecured public Wi-Fi networks are a common hunting ground for hackers. When you connect to these networks, hackers can intercept the data transmitted between your phone and the network. This can include sensitive information like login credentials, emails, and financial details. Sometimes, hackers set up fake Wi-Fi hotspots that appear legitimate, tricking you into connecting.
SIM Swapping
This method involves tricking your mobile carrier into transferring your phone number to a new SIM card owned by the hacker. The hacker achieves this by impersonating you and providing enough personal information to convince the carrier to make the switch. Once the hacker controls your phone number, they can receive your calls and messages, including verification codes for your online accounts, effectively taking over your identity.
Bluetooth and NFC Vulnerabilities
Hackers can exploit Bluetooth and Near Field Communication (NFC) protocol weaknesses to access your phone without your knowledge. For instance, Bluejacking and Bluesnarfing are techniques where hackers send unsolicited messages or steal information from your device via Bluetooth. If your phone’s Bluetooth or NFC features are left on in public places, it increases the risk of such attacks.
Outdated Software
Using outdated software on your phone can leave it vulnerable to hacking. Software updates often include patches for security vulnerabilities that have been discovered. If you do not keep your phone’s operating system and apps up to date, hackers may exploit known weaknesses.
Physical Access
Sometimes, all a hacker needs is physical access to your phone. If someone temporarily gets hold of your device, they can install malicious apps or tamper with your settings to gain ongoing access.
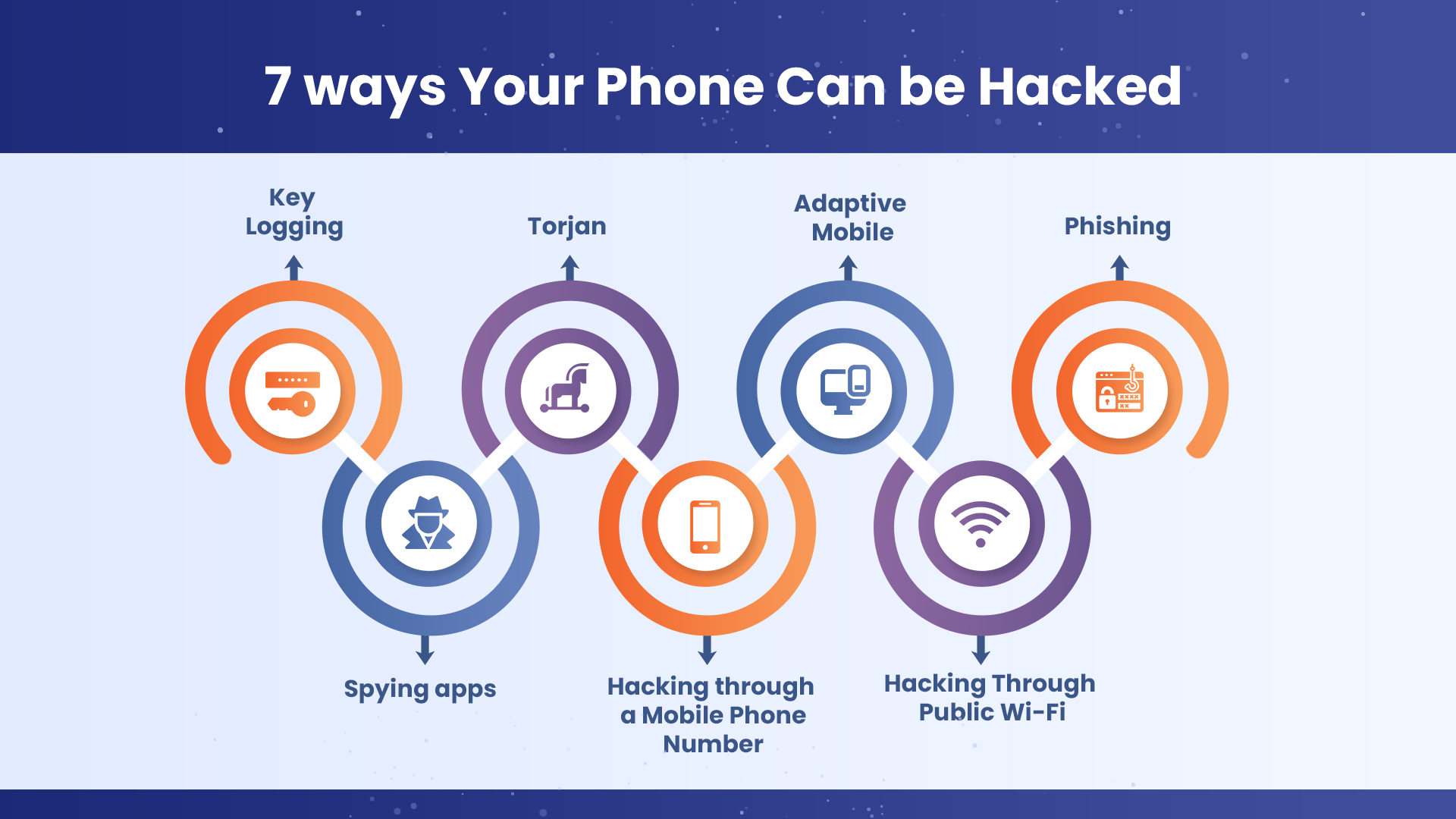
7 ways Your Phone Can be Hacked
Now, it’s easier than ever to become a cybercrime victim. Since the industry is so fast-paced and dynamic, there are new advancements on a daily basis. This, unfortunately, means that hackers have an ever-growing arsenal of tools at their disposal. Here are the five most typical methods by which cybercriminals hack phones:
Keylogging
This is a type of software that works in the background of all of your applications. It tracks all of the keys pressed on your phone, which includes the information you type in, the applications you utilize, and more. Most often, this method is employed by hackers to collect users’ private information, such as their passwords or banking information.
Trojan
These are some of the most dangerous methods of hacking. Trojans appear to be ordinary, unsuspecting applications on your phone. But, in truth, they are a type of malware virus that can collect, store, and extract your private data from your phone. This is especially sinister because of how hard it is for the average user to notice.
Adaptive Mobile
This method is unique as it targets a SIM card by transmitting a symbol to the victim’s device. When the message is received, hackers can spy on the device if the user clicks on the message. This method is more complex than most, and it runs in a very sophisticated manner as it can be used by cybercriminals to directly source information from your device.
Phishing
Phishing is when cyber criminals impersonate a trustworthy source to gather information from unsuspecting victims. This can come through emails, messages, or even perceivably secure requests for personal data, such as passwords. When these requests are responded to, the hackers gain access to their victim’s device, allowing them to monitor, collect, or sell data as they wish to.
Spying apps
These apps mostly track their user’s location, call logs, and messages. They are helpful for parents who want to keep an eye on younger children using their devices, but they can easily be hacked by cybercriminals who can use that information for malicious purposes. There are many cases where hackers have utilized these apps to collect emails and sensitive data.
Hacking through a Mobile Phone Number
This is a more complex means of hacking, but it can be done. Through SS7 system signaling, hackers can record calls, forward calls, and even find out your location.
Hacking Through Public Wi-Fi
By creating a hotspot that looks like a Public Wi-Fi or by hacking into an unsecured public network, a hacker can intercept traffic. This is known as a Man-In-The-Middle attack.
Symptoms that your phone is Hacked
Most of the tell-tale signs of your phone being hacked appear like glitches. But the fact is, these problems may just be the result of a serious problem. Some malware can deplete all of the resources of your device, limit the functioning of other apps, or even lock you out of your device entirely.
Performance Issues
If you’ve noticed that your device is sluggish out of nowhere, you could have a virus. Ask yourself if your battery doesn’t last as long as it usually does or if simple applications are taking longer to load. If your device is not behaving as it did before, you may have malware.
Your Phone Feels like it’s Running Hot
Performance issues are also linked with your phone being very hot to the touch. If your phone is hot even when it’s not being used, some sort of malware or mining app is likely being run in the background. This can also explain sudden battery losses or spikes in data use.
Mystery Apps or Data
One of the most obvious signs of being hacked is finding data that you haven’t acted upon. If you come across an application you didn’t download, texts you didn’t write, or calls you didn’t make, it is likely that you’ve been hacked. If you notice anything you don’t recognize on your phone, it’s time to take action.
Pop-ups or Changes to Your Screen
Sudden pop-ups are never a good sign when it comes unprompted. Any changes to your home screen or in your configuration can be a big hint that your device has been compromised.
How to Recover Your Phone After Being Hacked
Most of the time, booting your phone up in Safe Mode to delete the malicious app is the perfect fit. But there are many times when we don’t know what app is causing the problem. Here are some other tips for recovering your phone.

Change Your Password
Make sure you don’t use the same password for different websites. Always try to incorporate special characters into longer passwords to make them over ten characters. Also, put a reminder in your calendar that tells you to change your password every 6 to 8 months, just to fully secure your device.
Install and Run an Anti-malware Software
An anti-malware software does everything you need it to do. It can not only identify the source of the problem but also get rid of it entirely. The most effective results come from preventative measures, so make sure to run this software regularly.
Turn Off Your Mobile Data and Wifi
It’s never a good idea to connect to a public Wi-Fi or to have your phone automatically connect to one, especially without a VPN. AstrillVPN is one of the best and most complete security solutions that are available on the market. It can protect your identity and encrypt your data so that there can be no access point for hackers to infect your device.
Remove all Third-party and Suspicious Apps
If you are unsure about where you’ve downloaded an application form, you should delete it. Any application that hasn’t been downloaded from the Google Play Store is dangerous to have on your phone. Ensure you also check all the privacy settings and application permissions for any suspicious behavior.
Restore Your Phone to Factory Settings
Resetting your phone to factory settings erases all of the data stored on your device. This reboot allows your phone to go back to its bare essentials, which means that anyone who has access to your device can no longer reach it. This is a relatively simple process and is one of the most effective options.
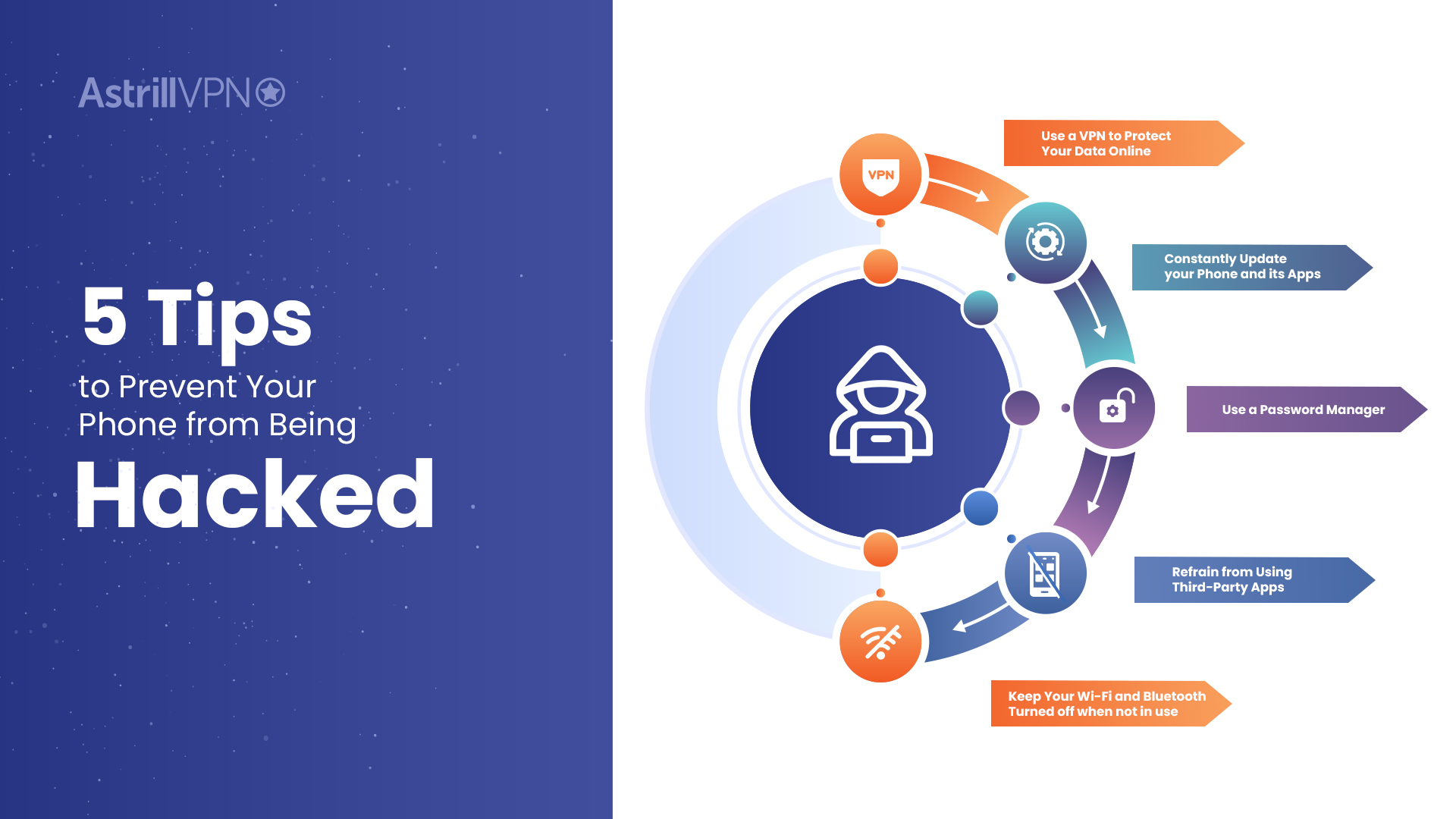
5 Tips to Prevent Your Phone from Being Hacked
Although there are multiple ways for a hacker to gain access to your phone to steal private and sensitive data, here are several preventative measures to consider taking:
Use a VPN to Protect Your Data Online
VPNs work in a way where that connects your device to a VPN server. AstrillVPN, for example, has hundreds of servers in over fifty countries. This means that whenever you connect to a VPN, you will be totally anonymous and untraceable. All of your data will also be encrypted, whether incoming or outgoing.
Any hackers trying to hijack your device will ultimately fail. AstrillVPN will change your IP address, protect your data, and give you an incomparable experience of privacy when online.
If you are using an iPhone, then you can check out our Astrill VPN on iPhone guide.
Moreover, you are android user then you can check our VPN guide on Android
Constantly Update your Phone and its Apps
Prevention is definitely better than a last-minute solution. Other than keeping your bases covered with anti-malware software, staying updated with your phone’s own security updates is essential. Make sure you keep all apps and services active with regular updates, as that keeps everything running smoothly and securely.
Use a Password Manager
A complicated password is one of the best defenses against hacking attacks. However, it can get troublesome to remember a variety of passwords. Using a password manager can fix this because you can use it to not only keep your passwords in a safe place but can also use it to create top-notch passwords for total security.
Refrain from Using Third-Party Apps
Third-party applications from the internet do not go through the stringent checks that Google Play has in place for applications on their platform. Many third-party applications often demand unnecessary permissions that grant them greater access to your phone than needed. Google Play also has security protocols in place that immediately delete any malicious app, which further protects your safety.
Keep Your Wi-Fi and Bluetooth Turned off when not in use
Whenever you turn your Wi-Fi or Bluetooth off during inactivity, you are effectively shutting the door to any unwanted parties from entering your device. Prevention is absolutely key, so whenever you are traveling and don’t need to be connected to the internet, just turn the connectivity options off.
Examples of real-life hacks and how they were detected and addressed
Here are some examples of real-life hacks and how they were detected and addressed:
1. Pegasus Spyware
In 2021, the Pegasus spyware was discovered to be infecting the phones of journalists, activists, and government officials worldwide. The spyware could secretly collect data from the phone’s microphone, camera, and other apps and send it back to its operators. The hack was detected by cybersecurity researchers who were analyzing a phone belonging to a Saudi activist, and the issue was addressed by companies releasing security updates to fix the vulnerabilities that the spyware exploited.
2. iPhone Phishing Attack
In 2019, a group of hackers used a sophisticated phishing attack to gain access to the iPhones of several prominent Twitter users, including Elon Musk and Barack Obama. The hackers sent messages that appeared to be from the victims’ IT departments, asking them to enter their login information on a fake website. Once the hackers had access to the victims’ phones, they could post tweets from their accounts. The hack was detected when the fake website was reported to the authorities, and the issue was addressed by Twitter, strengthening its security measures.
3. Android Malware
Researchers discovered “Android.Banker.A9480” in 2018, a malware that targeted banking apps on Android phones in India, stealing sensitive information and login credentials that were transferred to the hacker’s server. The cybersecurity experts identified the hack through suspicious activity on the victim’s phone. The affected banks addressed the issue by releasing security updates to their apps.
4. WhatsApp Spyware
In 2019, WhatsApp revealed that spyware known as “Pegasus” had been used to target the phones of human rights activists and journalists. The spyware could infect the phone via a missed voice call on WhatsApp and then access sensitive information such as location data and messages. The hack was detected when a cybersecurity company discovered the vulnerability and reported it to WhatsApp. The issue was addressed by WhatsApp releasing an update to fix the vulnerability and urging users to update their apps.
5. iOS Malware
Researchers identified “iOS14-JB,” a new iOS malware in 2020 that could jailbreak iPhones and install malicious apps. The malware spread via a fake website that offered iPhone jailbreak software. Upon analyzing the malware, the researchers reported their findings to Apple, which addressed the issue by releasing a security update to patch the exploited vulnerability.
6. SIM Swap Attacks
Several high-profile Twitter accounts were hacked in 2018 in a SIM swap attack, where hackers were able to take control of the victim’s phone numbers and access their accounts. The hack was detected when the victims noticed unusual activity on their accounts and reported it to Twitter. The issue was addressed by Twitter strengthening its security measures and urging users to enable two-factor authentication to protect their accounts.
Why do Hackers Hack your Phone?
Nowadays, our phones are basically our lives. These devices include our private data and have logs of our personal moments. This information can be useful to anyone who has malicious motives, such as:
- Identity theft, which can be done by stealing baking information
- Selling personal data to advertisers or companies
- Using your data for illegal purposes
- Using your device for mining cryptocurrency
- Making your device a third-party in cyber or botnet attacks
Conclusion
With all of the sensitive data that we carry along with us in our devices, knowing how to identify any warning signs could make a world of difference. Being aware of how to recognize any red flags and learning how to recover your data if you suffer any losses can help you through an otherwise problematic situation.
FAQs
Can I Run a Test to See If My Phone Is Hacked?
Yes, you can run tests to see if your phone is hacked. Various security apps and antivirus programs can scan your phone for malware, spyware, and other malicious activities. Monitoring unusual behavior such as unexpected data usage, battery drain, and strange pop-ups can also help identify if your phone is compromised.
Will You Know Immediately If Your Phone Is Hacked?
Not necessarily. Some hacks are designed to be stealthy and may not show immediate signs. However, unusual behavior such as sudden battery drain, increased data usage, apps crashing, or unfamiliar apps appearing on your phone can be indicators of a potential hack.
Can You Tell If Your Phone Is Being Monitored?
Yes, some signs can indicate if your phone is being monitored. These include:
- Unusual battery drain
- Increased data usage
- Slow performance
- Strange background noises during calls
- Unexpected reboots
- Presence of unfamiliar apps
Can hackers see you through your iPhone?
It is highly unlikely that a hacker can see you through your iPhone’s camera without your knowledge. However, a hacker can gain access to your iPhone’s camera and microphone through a malware attack or by exploiting a vulnerability in your device’s operating system or apps.
How do I run a security check on my iPhone?
To run a security check on your iPhone, you can follow these steps:
- Go to Settings > General > Software Update and make sure your iPhone is running the latest version of iOS.
- Go to Settings > Privacy and review the permissions for each app to ensure they only have access to the data they need.
- Go to Settings > Safari and turn on “Block Pop-ups” and “Fraudulent Website Warning” to protect against malicious websites.
- Install and run a reputable antivirus app from the App Store, such as Norton Mobile Security or McAfee Mobile Security.
What is the first thing you do when you get hacked?
If you believe you have been hacked, the first thing to do is to disconnect your device from the internet to prevent further unauthorized access. Change all of your passwords, including email, social media, and financial accounts, using a different, strong password for each account.
Can someone hack my bank account with my phone number?
It is not possible for someone to hack your bank account using just your phone number. However, hackers can use social engineering tactics, such as phishing or pretexting, to trick you into providing sensitive information or transferring money.

No comments were posted yet