Cyber threats have grown more sophisticated and damaging in today’s rapidly evolving digital landscape. One of the most dangerous categories is the Advanced Persistent Threat (APT), a stealthy, targeted, and highly destructive cyberattack. Unlike opportunistic hackers, APT attackers are methodical, patient, and often well-funded, making them a significant concern for governments, large corporations, and critical […]
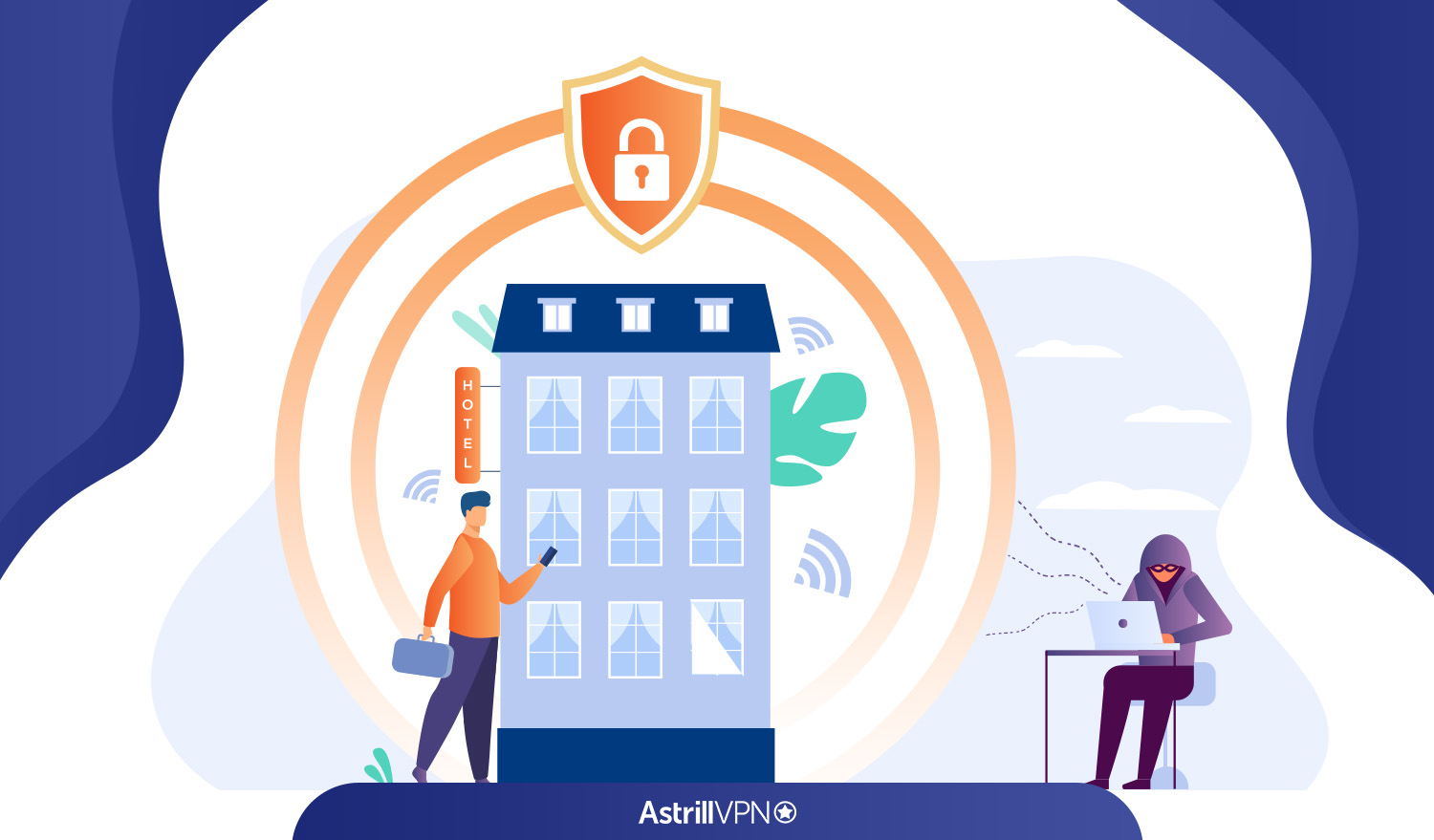
In the past, traveling safely meant safeguarding your passport, ensuring no one stole your wallet, and you didn’t misplace your credit cards. Of course, all of that is still significant. Today, however, safe travel also includes securing your digital assets while on public WiFi. Whether checking emails, accessing banking apps, or streaming entertainment, travelers rely […]
The Open Web Application Security Project (OWASP) is a globally recognized foundation that promotes secure software development. Its most referenced project, the OWASP Top 10, outlines the ten most critical web application security risks based on real-world data, research, and industry consensus. The OWASP Top 10 vulnerabilities serve as a practical framework for developers, security […]
What is a spam risk call and How to avoid it?
As our lives become more and more dependent on technology, protecting our devices from cyber threats is more critical than ever. One common annoyance that many of us face are spam phone calls, which can range from annoying telemarketers to dangerous scammers trying to steal our personal information. According to CBS News recent report: Americans […]
All of us know that the internet would not function without bots. From search engines indexing billions of web pages to chatbots providing instant customer support, bots automate tasks, improve efficiency, and enhance user experiences. However, not all bots serve beneficial purposes; malicious bots silently infiltrate systems, steal sensitive data, manipulate traffic, and even crash […]
Among the most concerning threats are spyware applications, which can infiltrate your device without your knowledge, compromising sensitive data such as messages, call logs, and banking information. Android smartphones have become prime targets for cybercriminals, with attacks on mobile devices increasing by 50% over the past year, as reported by the UK’s National Cyber Security […]
In our hyperconnected world, billions of devices access the Internet every second. The Domain Name System (DNS) is a silent yet crucial component often called the “phonebook of the Internet.” It translates human-readable domain names into machine-readable IP addresses. While this process seems simple on the surface, DNS is a high-value target for cybercriminals. This […]
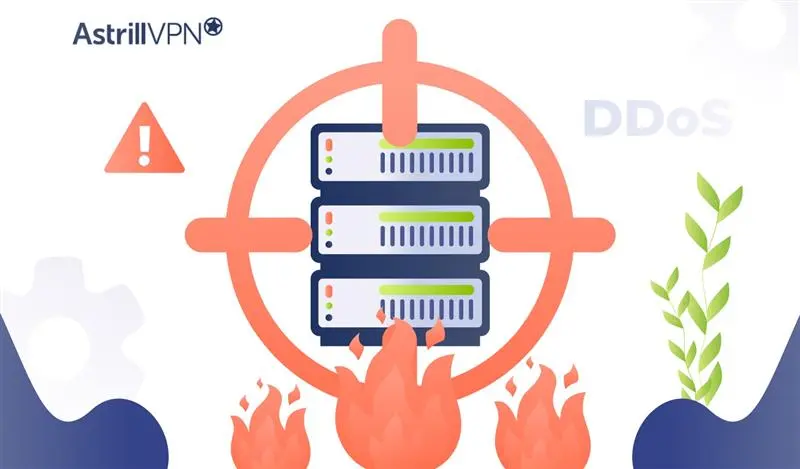
Distributed denial-of-service (DDoS) attacks remain one of the most common and disruptive cyber threats today. In 2024, industry telemetry shows that large-scale DDoS events continue to occur frequently and that peak attack volumes in recent years have reached hundreds of gigabits per second. Among DDoS techniques, the SYN flood (sometimes called SYN flooding) is a […]
Apple Pay is a super quick, secure, and easy way to manage your digital payments. Its transactions are protected by biometric authentication, tokenization, and encryption, keeping your information safe from prying eyes. However, the convenience of Apple Pay has also caught the attention of cybercriminals. Even though Apple Pay has solid security measures, it’s important […]
Imagine you’re just browsing the web like normal when suddenly a loud alert pops up claiming your device is infected. The message urges you to download a security tool or call a support number right away. It’s easy to feel a wave of panic, and that’s exactly what scareware wants to do. Scareware is a […]
The Norton PayPal email scam is a fraudulent email scam falsely claiming that you’ve renewed your Norton subscription. The scammers send these emails intending to steal your account and trick users into divulging sensitive data, such as their financial details. There are various effective ways to protect yourself from these online scams, including investing in […]
If you’re just minding your own business when an email pops into your inbox from Facebook and the subject line says your Facebook account’s recovery code is inside. Scammers are getting craftier with phony account recovery emails. If this sounds familiar, you’re not alone. Lots of folks are getting duped by fake Facebook account recovery […]
Fileless malware has emerged as one of the most serious challenges security teams face today. Such attacks move beyond dropping files to disk or installing traditional payloads. Instead, they exploit trusted tools already in the system memory, abuse legitimate features like Windows Management Instrumentation or scripting interfaces, execute code in memory, and avoid leaving evident […]
Ever gotten one of those sketchy emails claiming to be from Walmart? You know, the ones offering you a gift card or telling you that you won some big prize? Unfortunately, those are usually phishing scams trying to steal your personal information. As much as we all wish we’d won a $1000 Walmart gift card, […]
Just like how our security matters in the real world, our digital safety is of paramount importance. Cybersecurity is the practice of staying safe when connected to the internet and when protecting internet-reliant devices, such as databases, hardware, and even software. This protection is against hackers and malicious actors. In this day and age, we […]
Cross-site scripting (XSS) is a prevalent security vulnerability in web applications. It occurs when an attacker injects malicious scripts into otherwise benign and trusted websites. These scripts are executed in the victim’s browser, leading to potential security breaches, data theft, and unauthorized access. XSS typically exploits vulnerabilities in input validation and output encoding, making it […]
Organizations rely heavily on web applications, cloud services, and complex IT infrastructure. But amidst the growing sophistication of technology lies a silent yet devastating vulnerability: security misconfiguration. Often overlooked, this vulnerability allows attackers to exploit weak spots in systems that were improperly set up, inadequately maintained, or simply neglected. According to IBM’s 2025 Cost of […]
In today’s hyper-connected digital landscape, your devices face constant threats from malicious software. In fact, experts estimate there will be nearly 6.5 billion malware infections worldwide in 2025, with 300,000 new malware samples created every day. These digital threats can compromise your data, financial information, and overall cybersecurity, from viruses and worms to trojans and […]
Cyber threats are evolving faster than ever, and they’re targeting endpoints. In fact, according to a 2024 report by IDC, 70% of successful cyberattacks now begin at the endpoint. While still useful, traditional antivirus software is no longer enough to stop modern, sophisticated threats like ransomware, zero-day exploits, and fileless malware. As organizations adopt remote […]
A data or security breach occurs when private, sensitive, and confidential data is exposed to unauthorized personnel. Cybercriminals find a way to get past the security measures to steal your sensitive and confidential data for identity theft, fraud, and other malicious intent. Security breaches can have severe ramifications for companies and individuals. There are many […]
You’ve probably heard of mobile hotspots by now. They’re an amazing way to get online anywhere and can be life-saving when traveling. But what happens if someone gets their hands on your hotspot password? Now, you have to assess whether mobile hotspots are secure. They could potentially harm your privacy. Fortunately, there are several methods […]
Injection attacks are a big problem in cybersecurity. They exploit weak spots in how apps manage data, letting attackers slip in harmful commands. This can give them control over systems, steal personal info, and even mess things up. According to Aikido Security’s 2024 analysis, 6.7% of all vulnerabilities found in open-source projects are SQL injection attacks. […]
Cybercriminals increasingly employ spoofing to deceive targets and gain unauthorized access to systems. In 2025, researchers identified 3.7 billion URL-based threats in just six months. Attackers increasingly relied on AI-generated content, QR codes, and SMS for credential phishing. Phishing makes up 40% of spear-phishing attacks. Over 1 billion phishing emails are sent daily. These attacks exploit […]
The WannaCry ransomware outbreak in May 2017 was one of the biggest cyber disasters ever. In just a few hours, it infected over 200,000 computers in more than 150 countries, hitting both businesses and government offices hard. This major attack is estimated to have cost anywhere from 4 to 8 billion dollars, and it really […]
If you’ve had enough of the constant calls and text messages from an unknown number and you are ready to hit the block button but you’re unsure how that works on an iPhone, don’t panic. With U.S. consumers receiving nearly 5 billion robocalls monthly in 2025 and Americans losing $29.8 billion annually to phone scams, blocking unwanted numbers […]
Biggest Cyber Attacks Ever Made in History
You might not think about it often, but the internet is vulnerable. Hackers are always looking for new ways to break into our systems and steal our data. That’s when cyber attacks happen and happen all the time, but some stand out more than others. The biggest cyber attacks in history have affected everything from […]
Cyber extortion is becoming an increasingly common form of cybercrime. According to a report by Cybersecurity Ventures, global damages from ransomware attacks are expected to surpass $30 billion annually by the end of 2025. This highlights the growing threat that ransomware poses to businesses and individuals alike. Cyber extortion is a serious threat that impacts […]
Medical identity theft is becoming a huge problem and is one of the fastest-growing types of fraud. In 2024 alone, more than 276 million healthcare records were either exposed or stolen in the U.S., according to a report from HIPAA Journal. This means that every day, hundreds of thousands of people are at risk of […]
If you’ve decided to clear your router’s browsing history. Whether you share your network with others, want to free up space on the router, or value your privacy, deleting the router’s logs and history is essential. The good news is, clearing your router’s history is simple enough. The bad news is that the steps can […]
In today’s digital landscape, identity theft has become more sophisticated and dangerous. Among the many types of identity fraud, synthetic identity theft is emerging as the fastest-growing and hardest-to-detect form. Unlike traditional identity theft, synthetic identity fraud involves the creation of entirely new identities using a mix of real and fictitious data, making it incredibly […]
A rootkit is a sneaky piece of malicious software that burrows deep into a computer system, allowing cyber attackers to control it from afar without being easily spotted. It can mess with files, processes, and system settings without anyone noticing, so it’s considered one of the most dangerous cybersecurity threats. Recent studies suggest that around […]
In today’s tech ecosystem, if you’re unboxing a new smartphone, you’ll undoubtedly encounter pre-installed apps you never asked for. These apps are commonly called bloatware and are more than clutter. They can slow down your device, drain your battery, eat up storage, and sometimes even collect your data. A survey revealed that 76% of users […]
What Is Swatting and How Does It Work?
Swatting is a dangerous cybercrime that has gained notoriety in recent years. It is important to raise awareness about Swatting, its impact, and the steps that can be taken to prevent it. In this blog, we will explore what Swatting is, its dangers, why do people get swatted, and the efforts made to combat this […]
Cyber-enabled fraud continues to rise sharply. According to the FBI’s Internet Crime Complaint Center (IC3), reported losses from cybercrime reached 16.6 billion US dollars in 2024, a significant increase from 12.5 billion in 2023. This includes various forms of online fraud such as identity theft, investment scams, and business email compromise. Fraud prevention refers to […]
Pegasus spyware is nasty stuff that can sneak onto smartphones and steal people’s personal information. It’s a big deal for those who need to keep their data safe, like journalists and activists. This spyware can get into a phone without the owner’s knowledge. Once it’s in, it can access messages and photos, and even turn […]
A Guide to Data Security: Types & Best Practices
It doesn’t matter what your business’ size or industry is. If you handle personally identifiable data (PII), data security is a top priority. As cybercrime continues to thrive, businesses have no choice but to keep up the pace and continuously invest in data security. Why? Because poor data security practices have business-crippling consequences. According to […]
What is URL Phishing, and How to Prevent It
As the world continues to advance technologically, cyber threats also continue to evolve. One of the most common threats on the internet is phishing attacks, which often involve the use of phishing links or URLs. URL phishing attacks are a serious threat that can result in losing sensitive information and financial loss. By being aware […]
DDoS attacks have become one of the most disruptive weapons in cybercrime. What was once the domain of skilled attackers is now available to anyone with internet access and a small budget. This shift is mainly due to DDoS booters, online platforms allowing users to launch denial-of-service attacks without technical expertise. These services are marketed […]
Your device can join this criminal network without any visible signs. No pop-ups. No crashes. No obvious malware warnings. Botnets are designed to hide in plain sight, silently turning millions of innocent devices into weapons of mass digital destruction. According to Cloudflare, 71% of HTTP DDoS attacks in Q2 2025 were initiated by known botnets. Understanding […]
That innocent-looking device in your pocket? It’s recording your conversations, tracking your location, and sending your most private moments to complete strangers, all while you sleep peacefully, completely unaware. This is spyware and it’s already inside 1 billion devices worldwide. Right now, as you read this, advanced spyware is silently stealing data from phones, laptops, and […]
Privilege escalation is a critical security threat where attackers exploit system flaws to gain higher levels of access than originally authorized. Whether targeting a single device or an entire cloud infrastructure, such attacks can lead to full system compromise. In fact, according to IBM’s Cost of a Data Breach Report 2024, compromised credentials and privilege […]
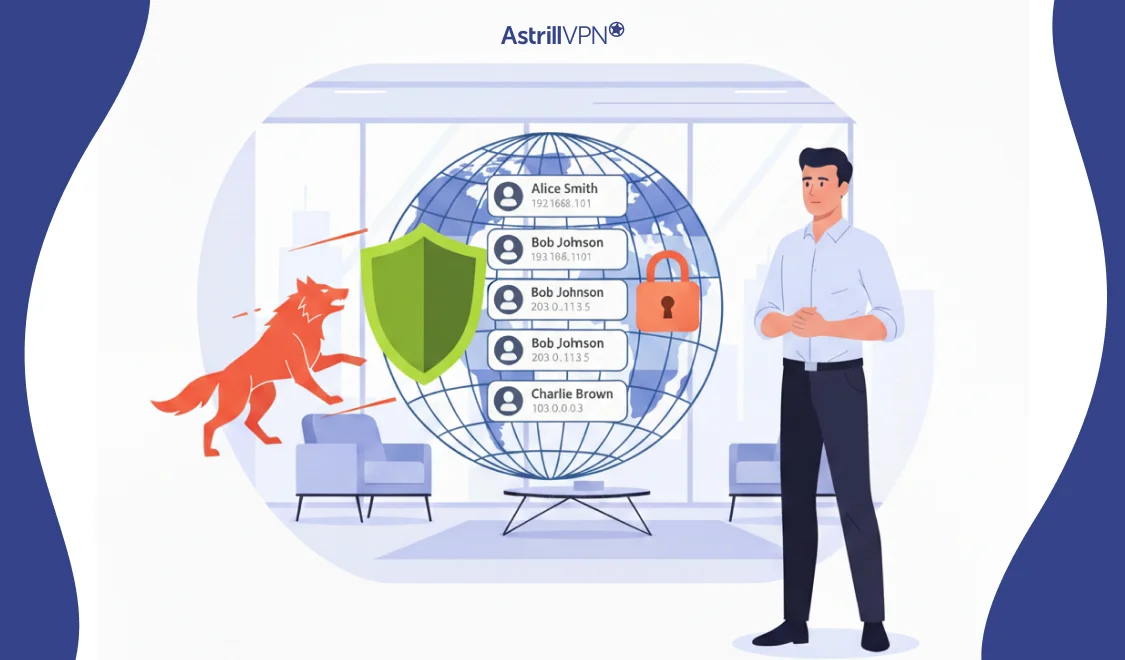
In the world of cybersecurity today, there are many different attack vectors to be aware of. One relatively common type is the replay attack. It sounds like something out of a sci-fi movie, but essentially, it’s when someone tries to “replay” a valid request or transaction on the web in order to gain access to […]
Zero day attacks are among the most critical threats in cybersecurity. These attacks occur when malicious actors exploit a software vulnerability unknown to the vendor or security community. Because no patch or fix is available during the exploit, the vulnerability is called a “zero-day,” indicating that developers have had zero days to address the flaw. […]
Have you ever received a suspicious phone call claiming to be from your bank or a government agency? Vishing, short for “voice phishing,” uses phone calls or voice messages to trick you into divulging sensitive information or taking harmful actions. As technology advances, these scams become increasingly sophisticated and challenging to detect. Understanding vishing and […]
The Internet of Things (IoT) has become deeply embedded in our daily lives, powering everything from smart homes and wearable health monitors to industrial automation and critical infrastructure. As of 2025, over 17 billion IoT devices are connected globally, which is expected to surpass 25 billion within just a few years. While this hyperconnectivity brings […]
Phishing is one of the most pervasive and dangerous threats in the digital world today. It refers to using deceptive tactics to trick individuals into revealing sensitive information such as login credentials, credit card details, or personal identification. Cybercriminals craft convincing emails, messages, or websites that appear legitimate, often mimicking well-known brands or trusted entities, […]
Ever get one of those tech support calls claiming to be from Geek Squad, offering to fix a problem with your computer? Yeah, those are scams. As much as we wish Best Buy’s tech support team made house calls, they don’t do unsolicited phone support. The truth is, there are shady characters out there trying […]
In cybersecurity, few threats are as deceptive and damaging as the Trojan horse virus. Named after the legendary Greek myth, this malware hides its true intent behind a seemingly legitimate facade. Once inside your system, it can steal data, monitor your activities, and even allow remote access to cybercriminals. In this article, we’ll explore everything […]
Staying secure online is not just about having the right tools. It is about understanding what you are up against. Every week, new vulnerabilities are discovered. Threat actors change their tactics. Attack campaigns adapt and grow more targeted. During this constant evolution, security teams are expected to defend systems, data, and users, often under pressure […]
In today’s increasingly connected world, cyber threats are growing in frequency and sophistication. Organizations of all sizes face constant risks of unauthorized access, data breaches, and malware infections. One of the most effective ways to detect these threats before they cause severe damage is by using an Intrusion Detection System (IDS). IDS tools serve as […]










![How to Spot a Walmart Phishing Email Scam? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/09/How-to-Spot-a-Walmart-Phishing-Email-Scam.jpg)









![What happens when you block a number on iPhone? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/03/Feature-Image-27.jpg)



















![The Truth About Geek Squad Scams: What You Need to Know? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/09/The-Truth-About-Geek-Squad-Scams.jpg)





