How to Torrent Safely without Compromising Your Online Privacy

Arsalan Rathore

Unless you know what you’re doing, torrenting is hazardous. Putting legal considerations aside, you face many online threats when using BitTorrent to download and upload files.
The two most important factors in torrenting safety are anonymity and security, and if you ensure these, you can safely and securely use torrents.
Follow this guide to learn the ins and outs of using torrent safety. On top of that, we’ll give you the rundown on how to conceal your identity and prevent data breaches while torrenting.
Table of Contents
The Dangers of Torrenting
While torrenting is a common way to get files, there are a lot of dangers that users should be aware of to stay safe when using the internet. To be safe while torrenting, you need to know about these risks.
1. Malware and Viruses
One of the foremost dangers associated with torrents is the prevalence of malware and viruses embedded within files. Cybercriminals often exploit the decentralized nature of torrent networks to distribute malicious software disguised as popular movies, software, or other sought-after content. For instance, in 2017, the infamous “WannaCry” ransomware spread rapidly through torrenting, infecting systems worldwide by exploiting vulnerabilities, causing widespread chaos and financial losses.
2. Legal Risks and Copyright Trolls
Torrenting copyrighted material without proper authorization raises legal concerns and exposes users to potential legal actions. Copyright holders, often represented by copyright trolls or agencies, monitor torrent networks to identify and penalize individuals sharing or downloading copyrighted content illegally. High-profile cases, such as the crackdown on users sharing movies or music, have resulted in hefty fines and legal ramifications for individuals involved.
3. Hackers
Torrenting exposes users to potential threats from hackers attempting to exploit security vulnerabilities. Cyber attackers may employ various techniques, including man-in-the-middle attacks or injecting malicious code into torrent files, aiming to compromise users’ devices or steal sensitive information. For instance, in 2016, attackers targeted a popular BitTorrent client, compromising millions of users’ accounts and potentially accessing personal data.
4. ISP Throttling
Internet Service Providers (ISPs) often monitor and throttle internet speeds for users engaged in extensive torrenting activities. ISPs employ bandwidth throttling to regulate network traffic, reducing download speeds for torrent users to maintain network stability and compliance with regulations. This throttling can significantly impact the torrenting experience, resulting in slow download speeds and frustrating interruptions.
How to protect yourself when Torrenting
While torrenting makes it easy to access a lot of data, users still need to be careful to keep themselves secure. You may greatly improve your security while torrenting by using these measures:
Use a reliable VPN for safe torrenting
Utilizing a secure VPN is important when torrenting. AstrillVPN encrypts your internet connection, masking your IP address and online activities from prying eyes. AsrtrillVPN offers dedicated IPs as well, which are best for torrenting, ensuring faster and more secure connections.
Keep your VPN connected
Maintaining a consistent VPN connection throughout your torrenting session is essential for uninterrupted protection. Even brief disconnections could expose your real IP address and activities to potential monitoring entities. Configure the AstrillVPN client to automatically reconnect if the connection drops to ensure continuous anonymity.
Avoid suspicious torrenting clients and websites
Exercise caution when selecting torrenting clients and websites. Stick to well-known, trusted torrent clients like qBittorrent, Deluge, or Transmission, which prioritize user security and regularly update their software to address potential vulnerabilities. Additionally, opt for reputable torrent websites with a strong community base and verified torrents to reduce the risk of downloading compromised files.
Install an Antivirus program
An effective antivirus program that can analyze torrent files for malware and viruses should be part of your defense system. Make sure the antivirus program you use has the most recent virus definitions to detect and remove any malicious software or files that may be hiding in downloaded files.
How to Configure Your VPN for Safe Torrenting
Using AstrillVPN, you can safely and smoothly download torrents by following these steps:
- Download and install AstrillVPN on your device.
- Open the AstrillVPN app and login.
- Select any server from the list.
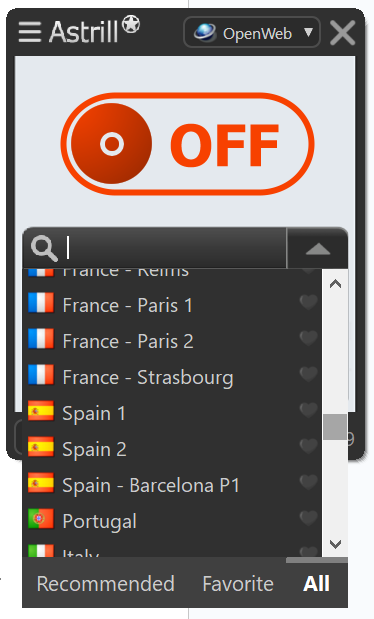
- Select the StealthVPN protocol from the drop-down list and establish the connection.
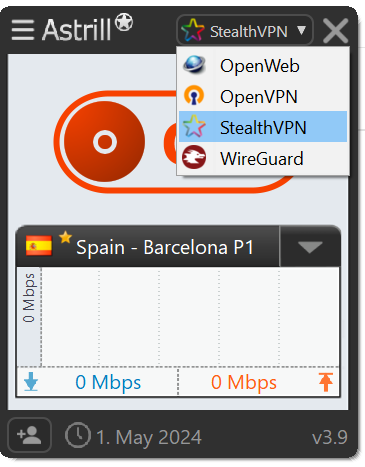
- Now Go to the settings menu and click on Privacy.
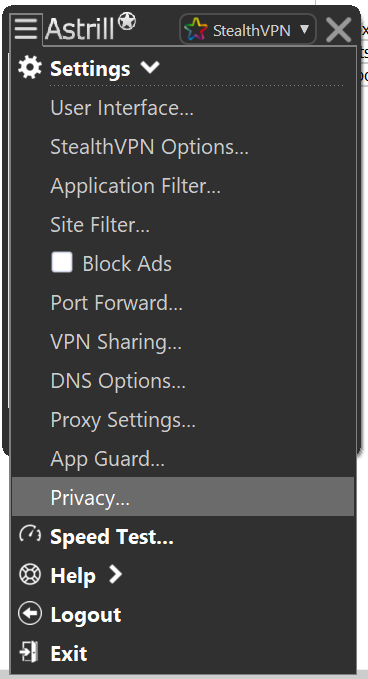
- Check mark the following options and Click OK:
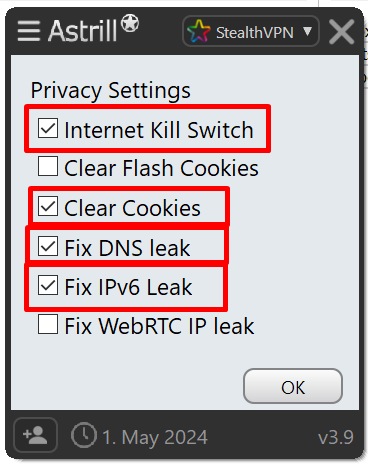
- Now click the Power button on the app to establish connection.
- Once connected, launch your torrent client and begin torrenting.
How to Safely Open .torrent Files
Downloading files from a torrent file does not include those files. Your torrent client will utilize it as a wayfinding tool to find other users who are willing to share the file you’re looking to download with you.
Grab a torrent program like qBittorrent or uTorrent, and you’ll be ready. To start torrenting after installation, open the.torrent file with your client and double-click it. During the whole process, you should be connected to a VPN server to do it all safely.
Recent Reported Malware Attack Through Torrent
The SOC of Positice Technologies discovered suspicious network behavior in August 2023 using MaxPatrol SIEM. The PT CSIRT incident response team was activated. A member of the X company’s staff fell victim to a relatively basic but previously undisclosed malware, according to the event analysis conducted by the PTSecurity task force. The individual only installed software from a pirate site; the examination found no signs of phishing or external perimeter breach.
Among the many disruptive behaviors displayed by the malware were collecting system information, installing remote management software (RMS) and the XMRig miner, and archiving the contents of the user’s Telegram folder (tdata). A Telegram bot served as the virus’s C2 server, receiving the data acquired by the malware.
An extensive investigation by the Positive Technologies Security team into the malware, infection chain, and Telegram bot led them to the discovery of numerous victims all over the globe and the identification of the “auto stealer” as the most probable originator of the malware.
Can I torrent safely with a free VPN?
Torrenting with a free VPN, while seemingly convenient, poses substantial risks and limitations that compromise user security and privacy. These free services often lack essential security features such as robust encryption protocols and kill switches, leaving users vulnerable to potential IP leaks and identity exposure during torrenting sessions.
Moreover, free VPNs frequently enforce strict bandwidth and speed limitations, disrupting efficient file downloads with slow speeds and data caps. Concerns about data privacy are heightened as many free VPN providers collect and log user data, potentially sharing this information with third parties and compromising user confidentiality.
Additionally, the presence of intrusive ads or, worse, embedded malware within free VPN software raises serious security concerns, potentially compromising device security and user privacy. The unreliable server infrastructure of free VPNs results in overcrowded servers and unreliable connections, leading to unexpected disconnections that could expose torrenting activities.
Therefore, investing in a reputable, paid VPN service is strongly advised, as it offers comprehensive security features, no data caps, a strict no-logs policy, and a reliable server network, ensuring a safer and more secure torrenting experience without compromising user privacy and safety.
FAQs
Torrenting itself isn’t inherently safe from viruses. Torrents can carry malware and viruses, posing risks to users who download or share files. Users must exercise caution, verify sources, and use reputable antivirus software to mitigate these risks.
Using uTorrent without a VPN can expose your IP address and torrenting activities to monitoring entities, potentially leading to privacy issues or legal repercussions, especially when downloading copyrighted content.
No, a VPN does not stop Torrenting. However, it encrypts your internet traffic, conceals your IP address, and enhances anonymity, making it more challenging for third parties to track or monitor your torrenting activities.
Seeding or sharing files within a torrent network isn’t inherently illegal. However, sharing copyrighted content without proper authorization constitutes piracy and is illegal in many jurisdictions.
qBittorrent is often considered a safer alternative to uTorrent. It’s an open-source torrent client with robust security features, no ads, and a focus on user privacy.
Yes, without the protection of a VPN, your IP address can be visible to other users in the torrent swarm and potentially tracked by copyright enforcement agencies monitoring torrent networks.
qBittorrent is favored for its open-source nature, absence of ads, active development, and a strong focus on user privacy and security. It also offers similar features to uTorrent without the bundled adware that uTorrent includes in its free version.
When using a VPN for torrenting, your ISP can’t directly monitor your torrenting activities. The VPN encrypts your traffic, preventing the ISP from seeing specific content or activities, though they can still observe that you’re using a VPN. You can even hide your VPN usage by using AstrillVPN’s StealthVPN protocol.

No comments were posted yet