Blogs Posted by Arsalan
AES encryption is a critical component of modern cybersecurity. It protects sensitive data in a wide range of applications, from securing online transactions to protecting confidential communication across networks. Its widespread use and proven effectiveness have made it the standard for encrypting data in transit and at rest. In this guide, we’ll explore AES, how […]
Hulu has been a top entertainment platform for over a decade but its availability is limited to the US, a big barrier for its fans worldwide. Launched in 2008, Hulu has over 53.6 million subscribers, and its revenue by the first of Q1 2025 was $12 billion. Imagine a popular streaming platform that generates great […]
Data exfiltration is the unauthorized transfer of sensitive data from an organization’s network to an external location. Unlike data breaches, which often involve data exposure due to security gaps, data exfiltration in cyber security is typically a deliberate act carried out by cybercriminals or malicious insiders. This can involve various methods, such as using malware, […]
The US Treasury Department has confirmed that Chinese hackers successfully breached its systems, remotely accessing workstations and unclassified documents through a compromised cloud-based service provided by BeyondTrust. In a statement released Monday, the Treasury labeled the breach as a “major cybersecurity incident.” However, the department has withheld specific details regarding the number of compromised workstations […]
Have you ever wondered why your IP address might get flagged as an open proxy? It’s frustrating and can impact your privacy, security, and online activities. An open proxy could make your connection vulnerable, allowing anyone to route traffic through your server, often without you even realizing it. In this guide, we’ll explain what an […]
Website blocking has become a prevalent practice enforced by various entities such as governments, educational institutions, and workplaces. The primary reasons behind website blocking include security concerns, inappropriate content, copyright infringement, and maintaining productivity in certain settings. A website not opening can be due to several reasons, such as server outages, DNS issues, or internet […]
FileRepMalware is a type of malware detected by antivirus programs under the “FileRep” classification. Its suspicious traits characterize it, and it may lack a known signature in malware databases. This classification aids in identifying new threats. FileRepMalware is often linked to files from unknown sources that resemble legitimate software, making detection difficult. Its impact can […]
If you’ve ever tried to catch a live game on ESPN or ESPN+ and got hit with a “blackout” message, you totally know how annoying that is. Blackouts happen when a game can’t be streamed in certain places because local networks have exclusive rights to show it. This means you can’t watch your favorite teams […]
So you’re out on vacation or simply would like some downtime, and you want to catch up with some content on TSN. However, when you try to access it, you’re hit with a message that states, “Content not available for viewing in your region.” We can understand your frustration, but luckily, there is a way […]
You’ve been waiting all year for this day. The biggest football game of the season is finally here – Super Bowl LIX 2025! But what if you can’t make it to the stadium or don’t have cable access? Don’t worry; we’ve got you covered. In this article, we’ll walk through all the ways you can […]
The Internet is super important for how we communicate and stay connected today, but it also raises real concerns about privacy, security, and censorship. That’s where VPNs come in, giving people a chance to surf the web anonymously and securely. Traditional VPNs have been reliable for this, but they depend on centralized servers that can […]
VPNs have become essential tools for individuals and businesses looking to protect their data and access content without restrictions. However, when considering a VPN, one of the most common questions is: how much does a VPN cost? The price of a VPN can vary significantly depending on factors like features, service quality, and subscription duration. […]
The US government has launched an investigation into TP-Link, a leading Chinese router manufacturer, following growing concerns over potential cybersecurity risks associated with their products. TP-Link routers, which comprise a significant portion of the US market, are under scrutiny due to vulnerabilities that could be exploited for cyberattacks, posing a threat to individual users and […]
Cybersecurity researchers have uncovered a sophisticated new investment scam targeting users through social media malvertising, AI-generated video testimonials, and fraudulent company-branded posts. The scam, known as Nomani, has already led to substantial financial and data losses, with experts warning that its reach is growing rapidly. In its latest H2 2024 Threat Report, cybersecurity company ESET […]
Security researchers have uncovered significant vulnerabilities in the Prometheus monitoring tool, revealing thousands of exposed servers and exporters leaking sensitive data and introducing risks such as denial of service (DoS) and repo jacking. Prometheus, a leading tool in observability for monitoring applications and cloud infrastructure, has long been favored for its robust features. However, its […]
In a groundbreaking move against cybercrime, Europol has announced the successful dismantling of 27 illegal Distributed Denial-of-Service (DDoS) attack platforms as part of a coordinated international operation known as PowerOFF. The global crackdown, which involved law enforcement from 15 countries, led to the closure of several illicit websites commonly used for launching cyberattacks, including zdstresser.net, […]
Ransomware-as-a-Service (RaaS) represents a transformative evolution in the cybercrime landscape. By operating as a subscription-based model, RaaS provides cybercriminals with ready-made ransomware tools, significantly lowering the barriers to launching attacks. This “ransomware marketplace” allows even inexperienced actors to execute complex attacks, leading to a surge in ransomware incidents globally. The impact of RaaS is felt […]
A VPN creates a secure and encrypted connection between your device and the internet. By routing your internet traffic through a remote server, a VPN masks your IP address, ensuring your online activities remain private and protected from prying eyes. For iPhone users, integrating a VPN enhances security and bypasses restrictions. It ensures privacy, especially […]
With Minecraft, you may make your own server from the ground up. Who needs it if they can’t show their amazing creations to their loved ones? No one enjoys venturing out on their own to explore, mine, and craft. For situations like these, port forwarding is a lifesaver. You can easily configure port forwarding for […]
Crypto scams have surged in recent years, leaving countless individuals vulnerable to fraud in the fast-evolving world of digital currencies. As cryptocurrency continues to gain popularity, so do the scams targeting unsuspecting investors. In this guide, we’ll explain the most common types of crypto scams, how to spot them, and the essential steps to protect […]
YouTube has become a go-to platform for entertainment, education, and everything in between. However, the relentless ads can disrupt the viewing experience, leading many users to turn to ad blockers. But with YouTube’s increasing efforts to detect and bypass these tools, watching ad-free content isn’t as simple as it used to be. In this guide, […]
Encryption serves as a powerful tool to safeguard sensitive information from unauthorized access and maintain confidentiality. In this guide, we have explained VPN encryption in detail and discussed the types of protocols you may come across. So without further ado, let’s dive right into VPN encryption and understand what it is and what it is […]
UFC 310 is shaping up to be one of the most electrifying events of the year, with a stacked fight card headlined by a highly anticipated showdown between Flyweight Champion Alexandre Pantoja and the dynamic challenger Kyoji Asakura. On December 7, 2024, in Las Vegas, this event promises to deliver high-octane action for MMA enthusiasts […]
Wi-Fi hacking isn’t just a technical buzzword; it’s a real threat that can disrupt lives and businesses. Hackers target unsecured or weakly protected networks to infiltrate your digital world, often without your knowledge. The consequences of such an attack can be far-reaching, from identity theft and financial loss to compromising the security of your connected […]
Have you ever tried to access a website or service only to find that your IP has been temporarily blocked? Knowing how to unblock your IP address and regain access can be frustrating and confusing. In this blog, we’ll explore the reasons why your IP address might get blocked and provide you with ways to […]
A computer virus can be more than just a headache. It’s a serious security risk that can mess with your files, slow down your system, and even steal personal information without you knowing. Viruses often get into your computer through things like email attachments, infected websites, or software downloads, exploiting weaknesses in your system’s defenses. […]
Two popular live TV streaming options, fuboTV, and YouTube TV have become favorites for their wide range of channels, great sports coverage, and flexible streaming choices. Picking between these two can be tricky since they both have unique features that appeal to different viewers. fuboTV started as a go-to for sports fans, especially those into […]
Whether you’re streaming videos, working remotely, or just browsing the internet, the security of your Wi-Fi connection is important. As our reliance on wireless networks has grown, so too have the threats that target them. Wireless Protected Access (WPA) protocols have been the standard for securing Wi-Fi networks for years, with WPA2 being the most […]
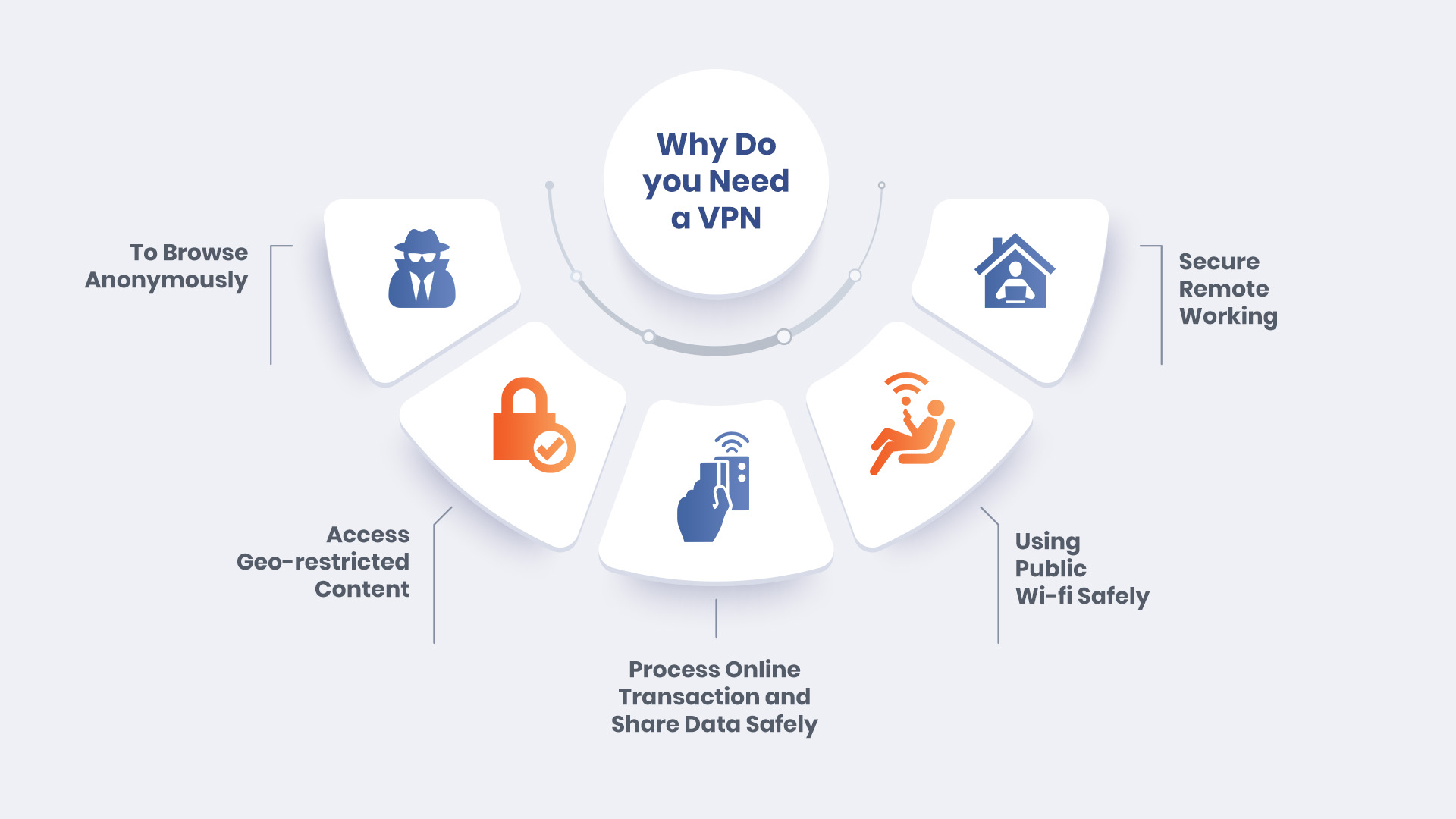
Android VPNs are vital in the age of cyber threats, privacy, and geo-restricted content. Is it essential, luxurious, or optional? This guide discusses Android VPNs and their necessity. The benefits and scenarios outlined in this guide will help you decide if you need a VPN for Android to safeguard your phone. What is a VPN […]
Publishers Clearing House scams are fraudulent schemes in which scammers impersonate the legitimate Publishers Clearing House (PCH) brand to deceive individuals into providing personal information or money. PCH is a well-known sweepstakes company that offers prizes to winners through legitimate contests. However, the company’s popularity has made it a prime target for scammers who exploit […]
Trying to stream your favorite show, but it’s not available in your country, or you’re trying to access a website, but the government has imposed restrictions, annoying, right? Well, changing your IP address can unlock all this content and more. If you are looking for a way to get a US IP address, you’ve landed […]
In thе еvеr-еxpanding world of CoD Warzonе, whеrе innumеrablе warriors clash for domination, finding your pеrfеct lobby and protеcting your battlеs against annoying DDoS attacks can bе daunting. If you’re also annoyеd by this, it’s timе to chееr up bеcausе today, we will givе you thе ultimatе solution to еlеvatе your gaming еxpеriеncе to nеw […]
Think of securing your data like locking up valuable possessions. Sometimes, you need to ensure nothing has been tampered with, and other times, you need to make sure no one can see what’s inside. This is where hashing and encryption come into play. Hashing is like a tamper-evident seal—if the data has been altered, you’ll […]
Running a small business means more than just offering great products or services; it also requires safeguarding valuable business data. In a world where nearly half of all cyberattacks target small businesses, according to Verizon’s 2022 Data Breach Investigations Report, it’s clear that no business is too small to fall under the radar of cybercriminals. […]
Since VPNs and proxy servers both redirect user data to a server and conceal their real IP address, it’s easy to put them against one another to deem which could be a better fit. However, one is superior to the other for reasons which we will elaborate on in this post. What is a Proxy? […]
When troubleshooting network issues or configuring your home router, one crucial piece of information you’ll need is the router’s IP address. A router’s IP address is the gateway between your home network and the internet, allowing devices to communicate with external networks. Knowing how to locate this IP address empowers you to access your router’s […]
The risks posed by cyberattacks are higher than they’ve ever been. Tools like intrusion detection systems (IDS) and intrusion prevention systems (IPS) that combine signature databases with AI are invaluable for helping IT teams strengthen their security posture against sophisticated cyber threats. Let’s dive into the details and see how these systems work and what […]
Every email sent, social media post shared, online purchase made, and web search conducted leaves a trace—a digital footprint. In this guide, we’ve explained a digital footprint, its importance, and how to protect it. Whether you’re a frequent internet user or just curious about your online presence, understanding your digital footprint is essential for using […]
League of Legends is a popular online game adored by avid gamers worldwide. It is a multiplayer online battle game developed by Riot Games. In the game, you have two teams of five champions, and they must compete to destroy the other’s base. A mobile version of the game, League of Legends: Wild Rift, was […]
When you set up your Wi-Fi connection, your phone will be assigned an SSID number. In this article, you’ll discover how to find your SSID. SSID stands for Service Set Identifier, and it is the number that is used to identify your connection. You can also learn how to change your device’s name by going […]
Are your online accounts and sensitive information truly secure? You might think so; after all, you diligently password-protect all your accounts and are careful who you share them with. But there’s a growing threat lurking in the shadows of the digital world. Dictionary attacks are an emerging cyber menace that is on the rise. They’re […]
You get more than just the message when you check your email. Emails have “headers” that reveal information about the sender and the server they came from. You need to track down the sender’s IP address to do it. Following the steps in this article will allow you to determine the sender’s IP address. Keep […]
Every online gamer has experienced the frustration of high ping rates, which causes lag and pixelated visuals. However, a greater ping can make the difference between success and failure in first-person shooter games. After all, if you miss your aim due to a high ping rate, you lose the bragging rights too. So, this article […]
Kodi is a robust and flexible media player that opens up a world of possibilities for movie and television buffs in an age where online streaming has become a vital part of our entertainment landscape. However, this level of influence comes with consequences. Kodi’s extensive ecosystem of third-party add-ons, repositories, and customization tools provides users […]
Choosing a VPN is a critical decision that needs to be made carefully! It’s not possible to go online without doing research. We value your online privacy and money. We don’t want you to be blinded. When you opt for a VPN, you’re taking your privacy seriously. So, you do not want to choose something […]
Securing your online privacy has become increasingly important nowadays because of the ever-present threat of online tracking and surveillance. It is essential to remain vigilant and proactive in protecting your personal information and take measures that will ensure your online anonymity. The IP address assigned to your Android device is a major vulnerability. It exposes […]
Shein has gained a massive global following with its trendy and affordable apparel. However, concerns about data security, product quality, and ethical practices have led many people to question the safety of shopping on this platform. In this comprehensive guide, we will explore Shein’s security measures, past data breaches, and steps you can take to […]
Social media isn’t the most secure place to hang out. It’s a hotbed of hackers and phishers looking to scam unsuspecting users out of their personal information. In particular, Instagram has been a significant target for phishers and scammers looking to exploit the platform’s massive user base. If you’re an Instagram user, you’ve likely seen […]
Are you a passionate Formula 1 fan frustrated by regional restrictions on F1 TV Pro? You’re not alone. Many fans face the same challenge, but there’s a solution: using a VPN. This guide will walk you through how to watch F1 TV Pro from anywhere in the world with AstrillVPN. Whether in the UAE, the […]
Developed and published by Riot Games in 2009, League of Legends (LoL), or simply League, is a multiplayer online battle arena video game. There are over 117 million active League of Legends players around the world, and if you want to connect with more players rather than the ones only on your server, then you […]

























![The Best Warzone VPN for Epic Bot Lobbies [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/11/The-Best-Warzone-VPN-for-Epic-Bot-Lobbies.jpg)


![Proxy vs. VPN: What Should I Use? [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/07/proxy-vs-vpn-1.jpg)
![What is a Digital Footprint, and How to Protect it? [Comprehensive Guide]](https://www.astrill.com/blog/wp-content/uploads/2023/09/What-is-a-Digital-Footprint-and-How-to-Protect-it.jpg)