Blogs Posted by Arsalan
In April 2024, cybersecurity researchers began tracking an unusually evasive malware strain spreading rapidly through phishing emails, fake software cracks, and malvertising campaigns. That malware was Lumma Stealer, a commercially sold infostealer designed to quietly extract sensitive data such as passwords, session tokens, crypto wallets, and authentication cookies from infected machines. Unlike viruses that cause […]
Have you ever considered that your choice of DNS server could influence your gaming? DNS is pivotal in reducing lag, improving connection speeds, and enhancing the gaming experience. Now, the question arises: What’s the best DNS for gaming? Follow this guide, and you’ll learn about the best gaming DNS servers in detail. What is DNS? […]
Cybersecurity services are essential for modern digital infrastructure as organizations increasingly adopt cloud environments and remote work, which expand their vulnerability to cyber threats like data breaches and ransomware. Without proper security measures, businesses face financial loss, legal issues, and reputational damage. These services protect networks, endpoints, applications, and data from unauthorized access and are […]
Roku is a widely used streaming device that allows users to access content from platforms like Netflix, Hulu, and YouTube. Like any internet-connected device, Roku relies on an IP address to communicate with your home network. Knowing your Roku IP address is essential if you set up a VPN on your router, troubleshoot connectivity issues, […]
If you’re using IPTV and experiencing buffering, freezing, or lag, especially during live streams or peak times, the issue is likely with your internet connection, not your IPTV service. Common problems include ISP throttling, poor routing, or regional restrictions. These factors affect how IPTV content reaches your device. You may have a fast internet plan, […]
With over a billion active users in more than 150 countries, TikTok has quickly become a cultural giant, changing the way people create and consume content. Its super-engaging short videos, powered by a really smart algorithm, have grabbed the attention of Gen Z, millennials, and brands. But as it keeps growing, privacy advocates, cybersecurity experts, […]
A watering hole attack is a cyberattack strategy in which the attacker targets a specific group of individuals by compromising a website or online service that they are known to frequent. The name “watering hole” is derived from the concept in nature, where predators wait at watering holes to catch their prey. Similarly, in a […]
Television has evolved beyond traditional broadcasts; it’s now a central platform for streaming global content. From Netflix and Disney+ to live sports and regional entertainment, Smart TVs give users access to a world of on-demand media. But with this convenience comes limitations: geo-blocks, throttled streaming speeds, and privacy risks. Using a VPN on your TV […]
Every interaction on the internet, whether sending an email, accessing a website, or making a digital transaction, leaves a traceable footprint. The IP address is one of the most fundamental identifiers behind all online activity. This unique string of numbers plays a critical role in how data is routed across networks, and it has become […]
Microsoft has issued an alert about a persistent malvertising campaign that leverages Node.js to deploy malware aimed at stealing sensitive data and exfiltrating system information. The campaign, which dates back to October 2024, primarily targets cryptocurrency enthusiasts. Attackers lure victims by promoting fake versions of popular trading platforms like Binance and TradingView, tricking them into […]
Cryptojacking is a type of cyberattack where hackers secretly use your device’s computing power to mine cryptocurrency. Unlike ransomware or data breaches, it doesn’t steal your data, instead, it slows down your system, drains battery life, and increases energy usage, often without you noticing. This threat has become increasingly common, especially as cryptocurrency values rise. […]
If AstrillVPN isn’t working as expected, don’t worry. Whether it’s a connection issue, an error code, or a slow speed complaint, VPNs can sometimes run into technical hiccups. But the good news is, that most of these issues can be resolved quickly with the right troubleshooting steps. This guide addresses the most common problems AstrillVPN […]
Transactions in a cashless environment can be completed quickly and easily with the help of contactless scanning. However, the widespread adoption of digital payment systems has prompted new concerns about fraudulent transactions. RFID protection solutions, such as RFID-blocking wallets and passport covers, provide solutions to these issues. However, the technology’s efficacy is crucial to assess. […]
Amazon’s Firestick has emerged as a revolutionary device, granting users access to various streaming content at their fingertips. As the boundaries of entertainment expand, so do concerns about online security and content accessibility. This is where the VPN becomes an integral tool for Firestick users. In this article, we’ll guide you about the best VPN […]
Industrial tech giant says data was stolen, operations disrupted, and investigations are still underway. Sensata Technologies has confirmed it was hit by a ransomware attack on April 6 that caused significant disruption to its operations and resulted in data exfiltration. The incident, which is still under investigation, prompted the company to file an 8-K disclosure […]
To think of a world without the Internet is to think of a world without information, community, commerce, and entertainment. However, it can also be a risky environment for kids to explore. Every parent wants to do what they can to protect their children from harm, whether from exposure to harmful material or undesired contact […]
Buffering issues can turn your streaming paradise into a buffering nightmare! Doesn’t matter if you’re a newbie with a Firestick or an experienced user, you’ll at some point in time face buffering issues with your Fire TV stick device. Nevertheless, in this comprehensive guide, we’ll discuss why Firestick keeps buffering and how can these issues […]
A serious security flaw in the OttoKit WordPress plugin, formerly known as SureTriggers, is being actively exploited, putting thousands of websites at risk of total compromise. Disclosed publicly just hours ago, the vulnerability, CVE-2025-3102 (CVSS 8.1), allows unauthorized attackers to bypass authentication and create admin-level user accounts on vulnerable websites. The flaw affects versions up […]
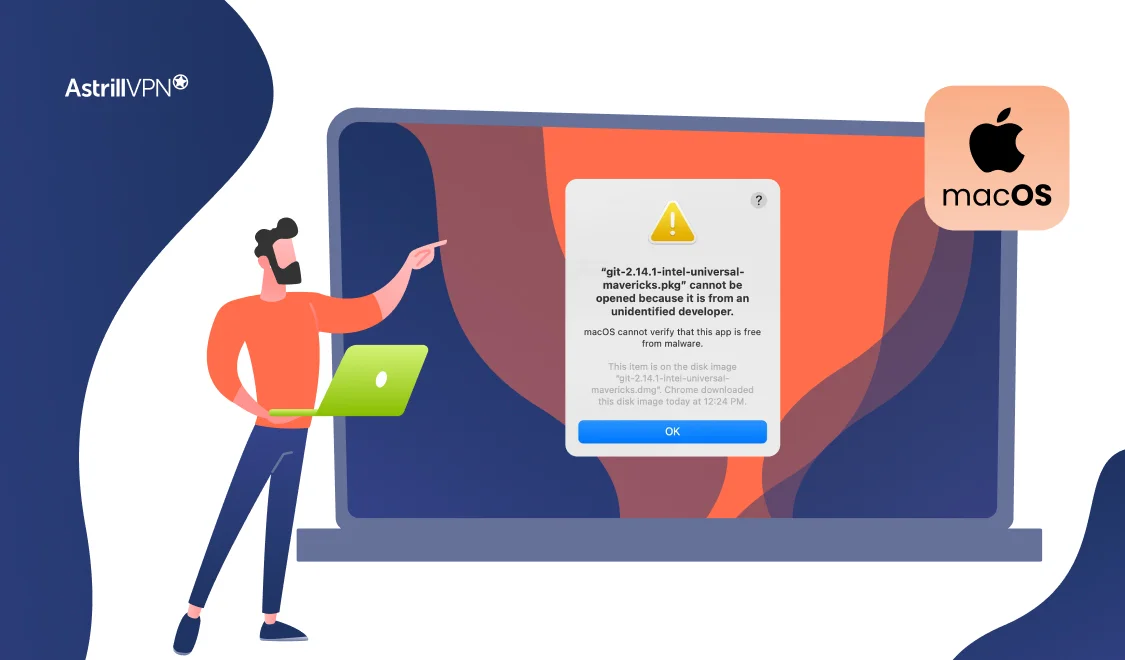
That moment when you try to open a new app and see the warning “macOS cannot verify that this app is free from malware” can be frustrating, but it’s also one of your Mac’s most important security features at work. This safeguard, powered by Apple’s Gatekeeper technology, isn’t just an arbitrary roadblock; it’s a critical […]
Users may show their support and acknowledge creators on TikTok with coins. Creators can rely on TikTok coins to generate money through virtual gifts they receive. Supporting creators financially and expressing gratitude for their work is as easy as buying coins and sending virtual gifts. So, how can you get cheap TikTok coins online? Follow […]
With a VPN, you can remain truly secure and protect your privacy whenever you’re online. Since digital security has become a growing concern, you may have questioned using a VPN. This article offers an explanation of VPNs and their benefits, as well as how to install one of the best VPN applications on the market. […]
Data breaches are no longer rare occurrences but frequent and unsettling events that impact millions of users worldwide. In 2024 alone, companies like T-Mobile, LastPass, and Uber have faced significant data breaches, compromising vast amounts of personal information. These incidents serve as stark reminders of the vulnerability of our digital lives. Maintaining the privacy of […]
Apple recently disclosed a security flaw in its Passwords app through its security content update that left users vulnerable to phishing attacks for three months before being addressed in the iOS 18.2 update. The issue, first spotted by security researchers at app developer Mysk, raised concerns about user data security, particularly for those accessing the […]
Nvidia has rolled out crucial security updates to address vulnerabilities in its Riva AI platform. If left unpatched, hackers could exploit its services for unauthorized access and potential financial damage. Riva, Nvidia’s GPU-accelerated speech and translation service, is widely used for real-time conversational AI applications, including large language models (LLMs) and retrieval-augmented generation (RAG). However, […]
A baiting attack is a form of social engineering where cybercriminals use enticing offers or items to manipulate victims into compromising their own security. These attacks exploit human curiosity, trust, or greed, often leading to malware infections, data theft, or unauthorized system access. Understanding baiting attacks is critical to staying safe in an increasingly connected […]
Internet Protocol Security (IPsec) VPN is one of the most robust solutions for ensuring secure, encrypted communication between devices over an IP network. For businesses, government agencies, or individual users, IPsec VPN is critical in safeguarding sensitive information from interception and tampering. In this guide, we will explain how IPsec VPN works, its key components, […]
If you’re looking for an alternative to VPNs, SOCKS5 proxies are an excellent option. Not all online privacy tools are created equal. While VPNs are great for encryption, SOCKS5 proxies offer a different set of benefits—like faster speeds and better performance for specific tasks. In this guide, we’ll explore the benefits of SOCKS5 proxies and […]
Mega cloud storage limits users from downloading or transferring 5GB of data daily. If you need more than that, you have to wait 24 hours for the limit to be reset. To get around this, Mega offers subscription plans at different prices, letting you transfer more data daily. Additionally, there are tricks available to bypass […]
If you are wondering how to bypass vpn blocks, then you have come to the right place. Over time, VPN blocks have become a serious thing, and many online streaming platforms as well as many websites have started implementing VPN blockers. Even though a good VPN usually helps you bypass all barriers, it’s frustrating when […]
Apple’s Safari focuses on keeping your privacy in check with features like Intelligent Tracking Prevention (ITP) and sandboxing to block annoying ads and cross-site tracking. However, you’re still not completely off the grid—your ISP can see your traffic, websites can find your real IP address, and geo-restrictions apply. That’s where a VPN for Safari comes […]
Kodi is a versatile, open-source media player that allows users to stream movies, TV shows, and live content seamlessly. While Kodi is available on various platforms, Roku does not natively support it. Unlike other streaming devices, Roku’s closed operating system prevents direct installation of third-party apps like Kodi. However, there are alternative methods to use […]
Have you ever tried accessing a website from home, realizing your IP address has changed since your last visit? Or why businesses and online services always seem to have a fixed digital identity while yours keeps shifting? That’s because not all IP addresses function the same way. While network devices like servers, routers, and switches […]
The 2025/26 season marks the 71st edition of Europe’s premier club football tournament and the 34th year since it adopted the name UEFA Champions League. The competition begins on July 8, 2025, and will culminate with the final in Budapest, Hungary, on Saturday, May 30, 2026. The Champions League isn’t just a European tournament, it’s […]
Streaming media to your TV has never been easier than with a Roku streaming player. When coupled with an internet-enabled device, this streaming stick makes it possible to watch live video from any location. This is why Roku surpassed the 85.5 million active users milestone last month (Q3 2024). In this guide, we have lined […]
LG Smart TVs have revolutionized how we consume entertainment, offering access to popular streaming platforms like Netflix, Hulu, Amazon Prime Video, and more, all from the comfort of your living room. However, much of the content on these platforms is geo-restricted, meaning you may not have access to certain shows, movies, or live broadcasts based […]
Traveling opens doors to new experiences and exposes you to significant cybersecurity risks. Nearly 20% of travelers fall victim to cybercrime abroad, often due to vulnerabilities like unsecured public Wi-Fi networks at airports, hotels, or cafés. These networks, while convenient, can quickly become a gateway for hackers to intercept sensitive information. Safeguarding your digital and […]
Most countries have a variety of internet service providers to choose from, each with its own set of pricing packages, download limits, access methods, and routing technology. How to Check Your ISP? If you are wondering, “Who is my internet service provider” then you can follow these steps: Who Can See Your ISP? If you […]
IPL, the action-packed T20 cricket league, is renowned worldwide for its exciting matches and fierce competitions between teams like Mumbai Indians and Chennai Super Kings. Every year, the IPL attracts an astonishing viewership of around 505 million on television. However, if you’re an IPL fan in the USA, you might face restrictions when watching the […]
When protecting your privacy online, understanding what your Internet Service Provider (ISP) can see and how they monitor your activities is crucial. Many users believe that browsing in incognito mode or using a basic privacy tool is enough to keep their data hidden from prying eyes, but the reality is far more complex. ISPs can […]
Are you a traveler wondering how to use a VPN for cheaper flights? Using vpn to get cheaper flights may seem mythical, but in reality, it does work. We’ve made this detailed guide in order to explain how a VPN helps travelers book cheaper flights. Go through the guide thoroughly to understand every aspect related […]
With an amazing user base of 35+ million, Cash App has undoubtedly transformed the world of mobile payments. But this transformation is limited to the people of the USA and the UK only! If you want to еxpеriеncе thе full potential of Cash App, thеn my friеnd, wе havе some good nеws for you. Today, […]
Phishing emails are a prevalent and dangerous cyber threat, designed to trick recipients into revealing sensitive information like passwords or credit card numbers. These fraudulent messages often mimic trusted sources, making them hard to identify. The goal of phishing is to steal personal or financial data, spread malware, or gain unauthorized access to systems. Cybercriminals […]
Cyber attacks have become increasingly prevalent in recent years, with attackers always looking for new and innovative ways to compromise systems and steal sensitive data. One such attack that has gained notoriety is the Evil Twin Attack, also known as the Evil Twin WiFi Attack. An Evil Twin Attack is a type of cyber attack […]
VPNs effectively protect your online presence by encrypting your internet traffic and keeping your activities private. However, the payment method you choose can impact your privacy. Traditional options like credit cards and PayPal can leave a digital trail that reveals your identity. Using Bitcoin to pay for a VPN offers a secure and anonymous alternative. […]
We often hear someone blaming the VPN provider for slow internet speed. But does a VPN slow down the internet? Well, if you are using a premium VPN with highly optimized servers like Astrill, then it seems this whole notion is a myth only. VPNs are supposed to encrypt your traffic and provide you secure […]
Note: In a dramatic turn of events, TikTok voluntarily suspended its services in the U.S. on January 19, 2025, following the Supreme Court’s approval of the “Protecting Americans from Foreign Adversary Controlled Applications Act.” This law mandated a halt on the app’s operations due to national security concerns over its Chinese ownership. However, just hours […]
If you’re a sports fan outside the UK, you’ve likely encountered the frustration of trying to watch BT Sport’s exclusive content only to be blocked by geo-restrictions. Whether in the US, Canada, or elsewhere, accessing BT Sport from abroad requires a solution to bypass these regional barriers. In this guide, we’ll show you how to […]
If you’re a Mac user wondering if you should use a free VPN. We get it; free stuff sounds great, but is a free VPN the best option for your Apple device? You want to protect your online privacy without breaking the bank. But free VPNs often have hidden costs that can leave your data […]
VPNs are the best tool for protecting your online privacy and digital freedom. Nevertheless, many people debate about the legality of a VPN and how safe it is to use. It is legal and safe to use a VPN in most countries like the USA, the UK, Canada, Australia, etc. However, there are certain regions […]
January 10, 2025 — AstrillVPN has released version 3.10.0.3066 of its desktop application, introducing a series of meaningful upgrades that strengthen security, improve device compatibility, and refine the overall user experience.This update focuses on real-world performance improvements that users will notice in daily use, especially across WireGuard connectivity, DNS handling, and cross-platform support. Broader Platform […]














![12 Fixes that Resolve Firestick Buffering Issues - Guaranteed [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/10/11-Fixes-that-Resolve-Firestick-Buffering-Issues.jpg)


![How to Use a VPN: IN-depth Analysis and Guide [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/05/How-to-use-VPN.jpg)
![A Detailed Online Privacy Guide for Staying Safe on the Web [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/10/online-privacy-guide.jpg)







![Install Kodi on Roku: Detailed Installation Guide [Updated]](https://www.astrill.com/blog/wp-content/uploads/2023/01/Feature-Banner-1.jpg)











![Does a VPN Slow Down the Internet? In-depth Analysis [Updated]](https://www.astrill.com/blog/wp-content/uploads/2022/06/Does-vpn-slow-down-your-speed.jpg)
![TikTok Faces Imminent U.S. Ban Amid Legal and Political Turmoil [Updated]](https://www.astrill.com/blog/wp-content/uploads/2025/01/USA-government-Banned-Tiktok.webp)