Compared to its competitors, Binance has the highest daily trade volume. Because of this, it is now the largest cryptocurrency trading platform. Unfortunately, in 2019 it was banned in the United States due to some issues with regulations. In light of this restriction, Binance launched a new exchange that follows US regulations. Yet it provides […]
Managing a consumer-based business with easy payment methods is the gateway to offering a smooth user experience. As businesses are shifting to digital and mostly e-commerce or online vendors are taking its place, every organization tries to keep their transactions safe. With the online business demand, the threat of data and financial breaches is also […]
If you are planning to move to Qatar or visit there for watching the FIFA World Cup 2022, then you might be eager to know the must-have apps in Qatar. It’s always a good thing to plan your journey ahead. Here are some of the must-have apps that you should have on your mobile phone […]
Hey Astrill-ers, With the FIFA World Cup (Qatar) 2022 craze right around the corner, adrenaline is kicking in with a lot of excitement! To notch-up your excitement, we have an amazing offer for our loyal customers! We are super delighted to announce that any of existing Astrill customers can win a 90-day FREE extension of […]
Every four years, the entire world gathers for the world’s largest sporting event. Football. Or, if you’re in the US, you would call it soccer. This year’s 2022 World Cup is also shaping up to be one of the most unique competitions in history. The good news is it’s only a few months away. Due […]
If you’re more into online streaming than you are into cable streaming, DirecTV stream can be just the service you need to watch the 2022 FIFA World Cup online. Every single game, all 64, will be available to watch on that platform. Read on to learn how you can sign yourself up to view one […]
Changing a private IP address into a public IP address is called Network Address Translation (NAT). This can be done to either one or multiple local IP addresses, and the conversion can be made directly into a global IP address. Through these IP addresses, local devices, hosts, and other such servers, can be made to […]
Your router, also known as the default gateway, has a unique, individual IP address whenever you connect to the internet. The default gateway receives and uploads traffic between you and the outside networks. This includes public and local networks, as well as the internet as a whole. By understanding how to access and configure your […]
It is ironic that some of the most popular websites on the planet that assure they do not collect data are seen to be violating privacy rules. The recent Facebook scandal is just one of the many news stories that have cropped up in the past few months that deal with the invasion of user […]
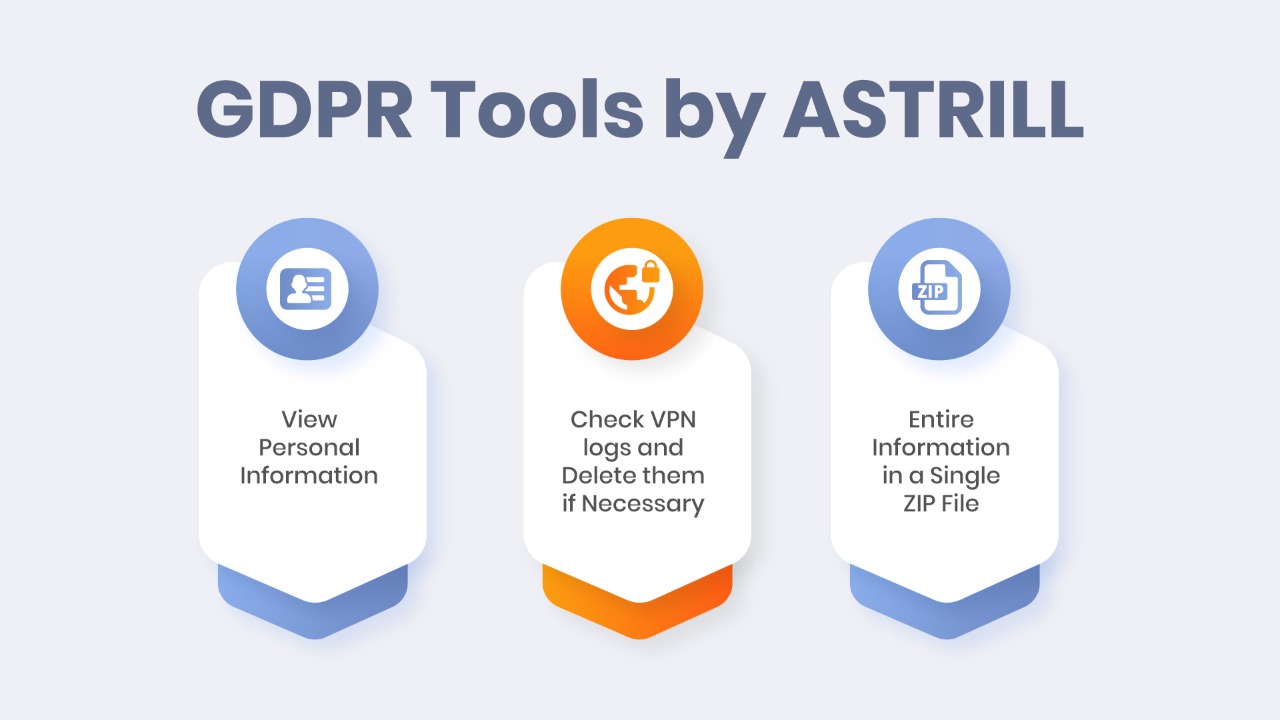
The General Data Protection Regulation (GDPR) is a regulation of the European Union (EU), providing EU residents control of their data. In other words, GDPR exists as a regulatory feature for citizens of all European Union members and safeguards their data handled by third-party websites and organizations. GDPR applies to all companies, whether they have […]
We would like to thank all applicants for submitting your work. We got over 50 designs ranging from minimalist to advanced UI. Because we were overwhelmed by the amount of work every single one of you put into the competition, we decided to award ALL participants with 1 month VPN membership and double the rewards […]
Do you feel like Astrill app UI is a bit dated? Would you like to give it a facelift? Are there things bothering you in the current layout? Do you have ideas for an amazing new UI that every Astrill user will fall in love with? Good news. We feel that our app needs some […]
At Astrill, we understand that our users’ browsing needs are diverse and often not limited to search indexes. Therefore, as part of our continuous efforts to push boundaries in online privacy and security technologies, we have extended the features of our core VPN product to enable secure access to deep web domains. Now you can […]
#DeleteFacebook! If you have come across this hashtag in the past week then you already know what’s brewing in the tech world. After Christopher Wylie, a Canadian whistleblower, revealed how his former analytics company exploited private data of over 50 million Facebook users to influence the 2016 US Presidential elections, the pressing question about individual […]
It’s almost like the tech bubble; maybe even bigger than that considering how many people are investing in it and how fast. Cryptocurrency has taken the world by storm, and it’s natural that you might feel like getting a slice of the pie. Since hitting the peak at the end of 2017, digital currencies like […]
We all know that the Internet is not the most private place on Earth. And there are enough hints that our everyday on-line activities throw at us that confirm that. Websites that track your on-line activities and re-target to show you suspiciously relevant ads, the need to fill in your mobile number when registering on […]