Free WiFi provides a cost-effective way to access the internet on the go. Whether you’re a student, a traveler, or simply someone who enjoys staying connected, learning how to get free WiFi can be a game-changer. This guide will explain various methods and tips to access free WiFi safely and conveniently, ensuring you stay connected […]
On June 18th, 2023, Governor Abbott passed the Texas Data Privacy and Security Act (TDPSA). Texas joins the ranks of other states like Montana, Tennessee, Indiana, Iowa, and many more regarding implementing Data Protection Laws. The TDPSA will come into effect from July 1st, 2024. It gives businesses time to prepare for the changes that […]
As reported by the Guardian, TikTok Faces Potential Multi-Million Pound Fine for Violating Children’s Privacy, EU Data Protection Regulator Rules. In a surprising turn of events, TikTok, the Chinese-owned video-sharing platform, is being slammed with a fine, possibly amounting to millions of pounds, for infringing on children’s privacy. The decision comes as a ruling from […]
If you decide which browser to use and wonder whether Microsoft Edge or Google Chrome is more secure and safe, it’s an important question since you want to protect your data and privacy online. They also have some key differences in handling your data and personal information that are worth considering. We’ll break down the […]
In the adrenaline-pumping world of Overwatch, victory depends on split-second reactions and flawless teamwork. Yet, the excitement can turn to frustration when lag spikes disrupt your every move. Whether you’re a seasoned player or a recruit, tackling lag spikes is vital to unlocking your full potential on the virtual battlefield. In this guide, we’ll equip […]
Artificial Intelligence (AI) has transformed numerous industries, revolutionizing how we work, communicate, and interact with technology. OpenAI, a leading research laboratory, has been at the forefront of AI innovation, developing state-of-the-art AI tools and models. However, one common obstacle that users encounter is the frustrating error message: “OpenAI services are not available in your country.” […]
Introduction You must know which browser is best, no matter what iOS device you use (macOS or iPhone). This in-depth guide brings you the ultimate battle of the browsers: Chrome vs. Safari. These two browsers have dominated the digital landscape, with millions of users worldwide. Whether you’re a tech geek, a casual browser, or someone […]
Internet Service Providers, or ISPs, provide internet access to homes, businesses, and other entities. They act as intermediaries, bridging the gap between users and the vast Internet infrastructure. Since ISPs provide internet service, it’s obvious that they have access to certain things we do over the internet. But the question is, what do ISPs see? […]
The Restrict Act (S.686) is a proposed bill introduced in the United States Senate on March 7th, 2023. Introduced by Senator Mark Warner, the Act proposes that the Secretary of Commerce be given the authority to review business transactions by foreign entities offering Information & Communications Technologies (ICTS) Products & Services, especially when these are […]
Just like how we need different hardware essentials to be able to play certain games, we also need different internet speeds. If you’re playing games with other players in a competitive environment, such as PlayerUnknown’s: BattleGrounds, or Valorant, you want high download and upload speeds to prevent delays or lags. If you prefer to game […]
Are you having trouble accessing the web interface of your Xfinity router because you can’t find the IP address? Don’t worry, we’re here to help! Most Xfinity routers come with a default IP address of 10.0.0.1. However, if you’ve made any changes to the default settings, locating the correct IP address becomes crucial for accessing […]
If you’ve ever wondered how to optimize your Mac’s performance, free up storage space, or resolve compatibility issues, clearing the cache is crucial. Cache files can accumulate over time, impacting your system’s speed and efficiency. In this guide, we will walk you through clearing different types of cache on a Mac, including browser cache, system […]
Pokémon Go has captured the hearts of millions of players worldwide, offering a unique augmented reality experience that combines the real world with the virtual world of Pokémon. The average number of active Pokemon Go players is 79,669,226, which proves its popularity well. While the game encourages exploration and adventure, there may be times when […]
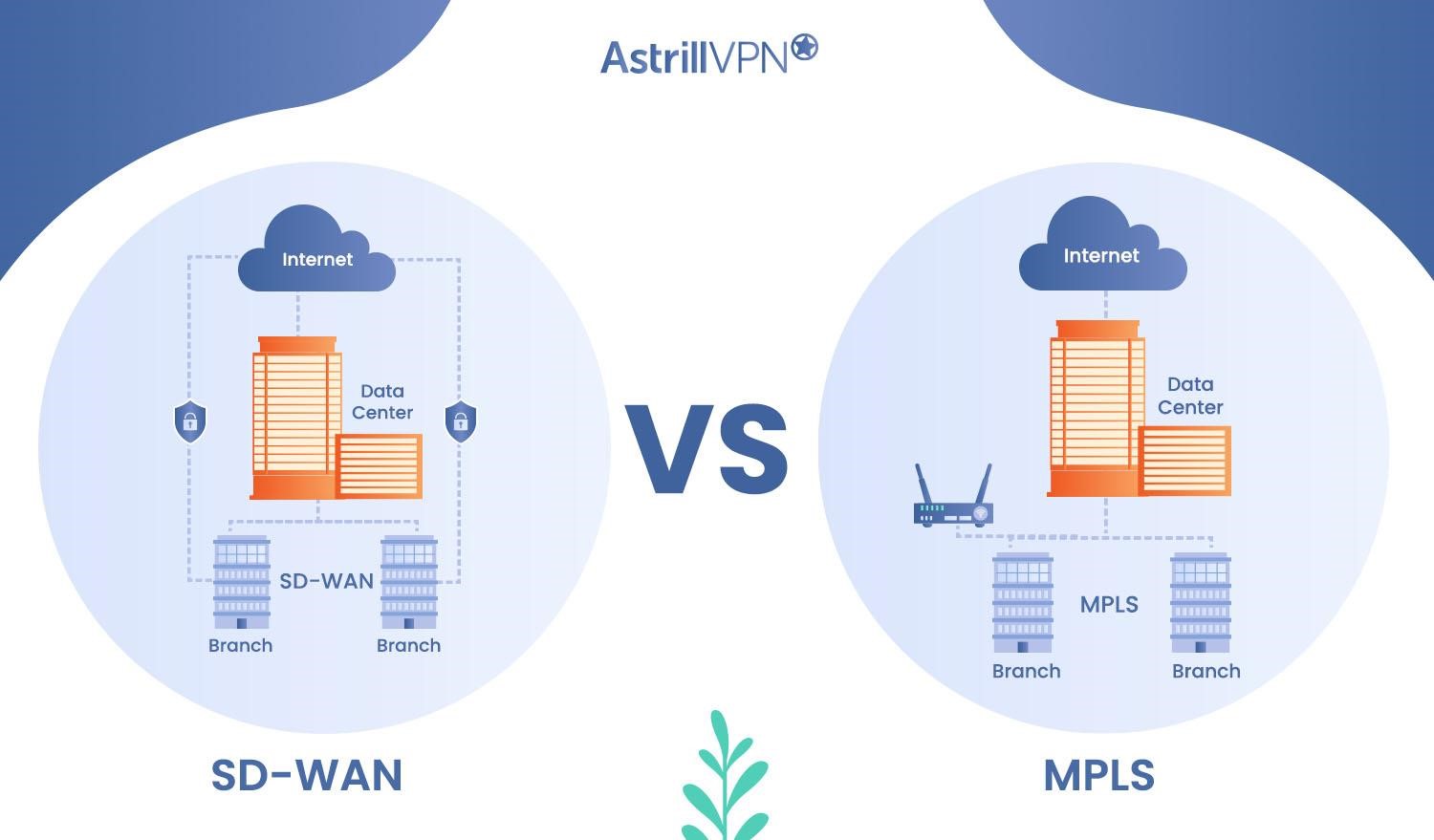
Wide area networks (WANs) connect geographically dispersed locations, enabling organizations to communicate and share data across different sites. As businesses expand and adopt cloud-based applications, the demand for efficient and reliable WAN technologies has increased significantly. Two prominent WAN technologies exist Software-Defined Wide Area Networking (SD-WAN) and Multi-Protocol Label Switching (MPLS). SD-WAN and MPLS have […]
YouTube has become a powerful platform offering vast educational content, revolutionizing how students learn and teachers instruct. However, accessing YouTube at school can be challenging due to blocking or restrictions imposed by educational institutions. By leveraging the potential of YouTube while maintaining a safe and controlled online space, schools can enhance learning experiences and provide […]
Hey there, ever had the feeling someone was looking over your shoulder while you entered your password or PIN? That uncomfortable sense of being watched can be a sign your personal information is at risk from shoulder surfing. Shoulder surfing definition is when someone spies on you to steal your data or account access. They […]
Hackers and cyber-criminals use password-cracking techniques to compromise users’ accounts and access sensitive data. Rainbow Table Attacks are one of the methods that they use. Unsure of what a Rainbow Table Attack is and how it can cause harm to organizations and individuals alike? Keep reading as we talk about Rainbow Table Attacks and what […]
T-Mobile, a leading mobile network provider, offers millions of users reliable coverage and seamless connectivity. Using T-Mobile’s network alone does not guarantee complete protection from cyber threats. Users are exposed to various risks when connecting to public Wi-Fi networks, such as those found in cafes, airports, or hotels. Why rely on T-Mobile for your privacy […]
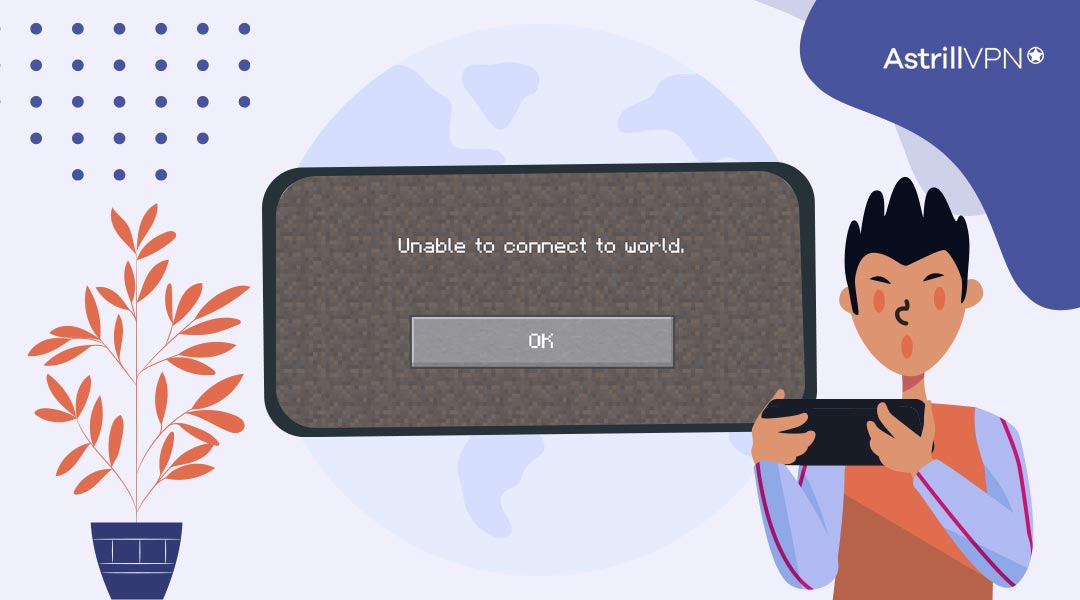
The “Unable to Connect to World” error in Minecraft can frustrate players eager to jump into their favorite multiplayer servers or play with friends. This error message typically appears when a problem establishes a connection between your Minecraft client and the server you’re trying to join. Resolving this issue is crucial to ensure a smooth […]
While iPhones and iPads come equipped with built-in ad blockers that can handle basic ads during online browsing, they often fall short when effectively blocking more sophisticated and potentially malicious ads. These ads can pose serious cybersecurity risks, making it essential to seek out dedicated ad blockers for comprehensive protection. An ad blocker specifically designed […]
In a recent development, Montana became the first state in the U.S. to officially ban TikTok, effective immediately from January 1st, 2024. Over 150 million American users use TikTok, and there have been growing concerns from U.S. lawmakers to ban the app altogether because of the potential influence of the Chinese government on TikTok. While […]
Welcome to the internet age, where your personal information, from your name and address to your social media posts, can be found with a quick Google search. We know there are precautions and tools you can use to protect yourself online, but it’s not always enough. If you’ve had enough of living in an era […]
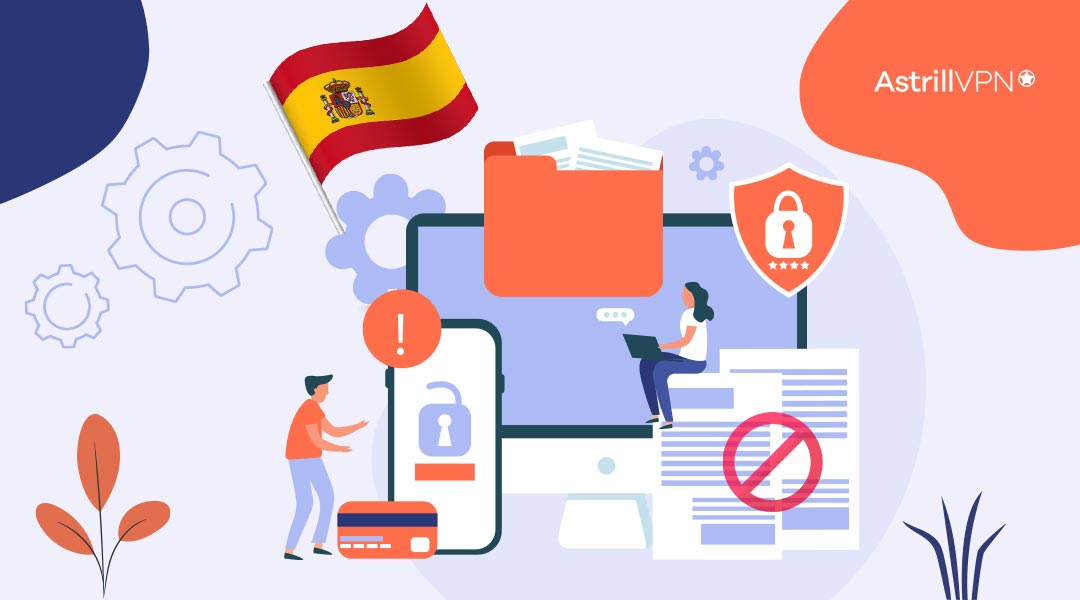
The document, which first got leaked to WIRED, revealed that many EU countries favor monitoring encrypted messages to help prevent the spreading of CSAM (Child Sexual Abuse Material.) Spain is proposing to ban end-to-end encryption altogether. The document states that EU countries (including Ireland) propose to create new rules and regulations to help combat this […]
Messenger, developed by Facebook, has become one of the most popular instant messaging platforms worldwide. With its extensive features and wide user base, Messenger allows individuals to connect seamlessly with friends, family, and colleagues. However, there are various reasons why someone might consider deactivating Messenger. In this article, we will explore the process of deactivating […]
What should you do with all the junk stored on your computer? Declutter it, of course! With all of the junk files clogged up on your computer, it’s the best course of action to start removing them, since it also affects the performance of your device. The best part is that decluttering all the junk […]
With the proliferation of smart devices and the Internet of Things (IoT), the need for seamless connectivity and communication between devices has become increasingly important. One of the technologies that facilitate this seamless connectivity is Universal Plug and Play (UPnP). UPnP is a set of networking protocols that enables devices to discover and communicate with […]
The social media blackout in Pakistan has reverberated across the nation, leaving citizens and international observers bewildered and concerned. Following the arrest of prominent political figure Imran Khan, the government has enforced sweeping restrictions on access to popular social media platforms, including Twitter, YouTube, Facebook, and Instagram. This unprecedented move has sparked controversy and political […]
Imagine settling down for a cozy night of Hulu binging, only to be met with the dreaded Hulu Proxy Error. It’s a major buzzkill that can occur when you’re trying to access Hulu from a location where it’s not available due to pesky geo-restrictions. The culprit? Using a proxy or VPN service to access the […]
With the growing popularity of VPNs, there is also a growing concern about the extent of the privacy offered. Unfortunately, many VPNs misrepresent themselves as having strong, secure no-logging policies. What’s worse is that it is becoming increasingly difficult to find a VPN that is actually secure and reliable. Many VPNs, still, silently collect data […]
If you’re an avid CSGO player, you know how frustrating it can be to experience high ping. A high ping can result in laggy gameplay, delayed responses, and inaccurate hit detection, which can significantly affect your gaming experience. However, the good news is that there are steps you can take to lower your ping and […]
Introduction It’s no secret that Reddit can be a wild and anonymous corner of the internet. But is Reddit safe for kids? As a parent, you want to ensure your child is safe online, but the answer can sometimes be complicated regarding Reddit. There’s no single answer here. It depends on your child and their […]
The need for data security has become more crucial than ever before. External hard drives are popular for storing large amounts of data due to their portability and convenience. However, with the increase in cyber threats and data breaches, protecting the sensitive data stored on these drives is essential. Encrypting an external hard drive is […]
Are you tired of being bombarded with endless ads while browsing the web? Do you value your online privacy and want to prevent intrusive tracking? Look no further than the world of ad-blocking Chrome extensions! With so many options to choose from, it can be overwhelming to find the best one for your needs. But […]
McDonald’s has been offering free WiFi to its customers for years, making it a convenient option for people on the go who need to stay connected. However, using public WiFi comes with risks, as cybercriminals can easily intercept your data and gain access to your personal information. So while you might be enjoying a double […]
We live in a world where internet connectivity is essential. However, the more devices connected to your WiFi network, the slower it becomes. You may experience slow internet speed or face security threats from strangers trying to access your network. In this blog, we will provide a complete guide on how to kick people off […]
Introduction Have you ever received a message via WhatsApp that seemed a bit off? In recent years, WhatsApp scams have become increasingly popular amongst scammers looking to exploit unsuspecting victims. These scams are becoming more and more prevalent. But there are still ways to protect yourself from becoming their next victim. In this article, we’ll […]
Introduction Have you ever been frustrated when your iPhone’s calendar notifications suddenly start appearing without you having made any changes? What may have started out as an innocent alert could soon be a source of anxiety and panic if you discover it’s a virus. In this article, we’ll discuss how to remove a virus from […]
Android is one of the most popular operating systems in the world, powering millions of smartphones and tablets. However, as with any popular technology, there are always those who seek to exploit it for their own gain. If you suspect your Android phone has been hacked, it’s important to take action as soon as possible […]
NAT (Network Address Translation) is a networking concept that allows devices on a private network to access the internet. NAT helps to hide the internal IP addresses of devices and presents a public IP address to the internet. In gaming, NAT type plays a crucial role in determining the smoothness of online gameplay. A strict […]
In recent years, issues relating to individuals’ right to privacy have become a focal point of increased public and governmental attention. After the Cambridge Analytica incident of 2018, the internet and social media have gained new significance. The digital billboards of the modern internet user are social networking sites like Twitter, Tumblr, Facebook, Pinterest, Instagram, […]
In February 2019, Astrill became one of the very few virtual private network (VPN) providers to offer WireGuard as part of its services. It is aimed at providing a fast connection, tighter security, and enhanced encryption with a much simpler architecture compared to IPSec and OpenVPN. Because the protocol uses cryptography and is easier to […]
Anyone who uses the internet leaves behind some sort of digital trail. All of our data, from the most basic to the most private, is accessible on the internet. The risk of data breaches grows larger and larger as time goes on, further eroding the concept of privacy. If our most private data were to […]
Taking measures to protect your online privacy is more important than ever in a world where organizations sell your personal information for profit and data breaches occur with alarming frequency. Using a VPN is the ultimate option for every netizen because it provides protection from every online threat and ensures privacy. Every person has different […]
Compared to its competitors, Binance has the highest daily trade volume. Because of this, it is now the largest cryptocurrency trading platform. Unfortunately, in 2019 it was banned in the United States due to some issues with regulations. In light of this restriction, Binance launched a new exchange that follows US regulations. Yet it provides […]
Managing a consumer-based business with easy payment methods is the gateway to offering a smooth user experience. As businesses are shifting to digital and mostly e-commerce or online vendors are taking its place, every organization tries to keep their transactions safe. With the online business demand, the threat of data and financial breaches is also […]
If you are planning to move to Qatar or visit there for watching the FIFA World Cup 2022, then you might be eager to know the must-have apps in Qatar. It’s always a good thing to plan your journey ahead. Here are some of the must-have apps that you should have on your mobile phone […]
Hey Astrill-ers, With the FIFA World Cup (Qatar) 2022 craze right around the corner, adrenaline is kicking in with a lot of excitement! To notch-up your excitement, we have an amazing offer for our loyal customers! We are super delighted to announce that any of existing Astrill customers can win a 90-day FREE extension of […]
Every four years, the entire world gathers for the world’s largest sporting event. Football. Or, if you’re in the US, you would call it soccer. This year’s 2022 World Cup is also shaping up to be one of the most unique competitions in history. The good news is it’s only a few months away. Due […]
If you’re more into online streaming than you are into cable streaming, DirecTV stream can be just the service you need to watch the 2022 FIFA World Cup online. Every single game, all 64, will be available to watch on that platform. Read on to learn how you can sign yourself up to view one […]