The Minecraft video game franchise is massively successful. The original version came out on October 7th, 2011. Since then, the game’s popularity has skyrocketed, with 150 million players all around the world. Lag and disconnects are common concerns in online games. Yet, most players are unaware that Minecraft lag can be eliminated. Understand what causes […]
In today’s cybersecurity landscape, ransomware attacks have evolved into a lucrative and destructive industry, and LockBit is at the forefront of this digital menace. Since its emergence in 2019, LockBit has rapidly become one of the most active and dangerous ransomware families, responsible for a significant share of global cyberattacks between 2021 and 2025. With […]
In the age of social media, privacy can feel like a luxury, especially on a platform like Instagram, where millions of users share photos, stories, and moments every day. Instagram’s rapid growth continues, with over 90 million new users added between January 2024 and January 2025 alone, according to Datareportal report. While Instagram doesn’t offer […]
Suddenly unable to connect to your VPN on iPhone? You’re not alone. iOS 18 introduced several compatibility changes affecting VPN connections, and even on earlier iOS versions, connectivity issues affect up to 15% of VPN users at some point. Whether you’re seeing error messages, experiencing authorization failures, or your VPN simply won’t connect despite showing ‘Connected,’ this comprehensive troubleshooting […]
Are you looking to enhance your Apple TV’s security and privacy? Look no further than Astrill VPN. In this blog, we’ll explore how to use VPN on Apple TV, including the setup process and the benefits of using a Apple TV VPN. We’ll also discuss the various features of Astrill VPN that make it a […]
NanoCore RAT is a powerful and widely used Remote Access Trojan that allows attackers to control a victim’s system completely. First discovered in 2013, it has gained popularity among cybercriminals due to its low cost, ease of use, and range of malicious capabilities. From stealing login credentials to activating webcams and recording keystrokes, NanoCore poses […]
A new wave of North Korea’s “Contagious Interview” campaign targets software developers with malicious npm packages disguised as legitimate job-related coding tasks. Security researchers at Socket Threat Research uncovered 35 such packages, which deploy the BeaverTail info-stealer and InvisibleFerret backdoor, both tools previously linked to North Korean state-sponsored actors. These malicious packages, uploaded through 24 […]
Have you ever considered changing your iPhone’s IP address to be shady or illegal? Well, you’d be surprised to know that it’s the total opposite! In reality, changing your IP address can significantly improve your iPhone’s privacy and security when accessing the internet. With over 1.382 billion active iPhone users worldwide and mobile devices accounting for 64% of […]
Is your phonе acting wеirdly? Tirеd of thosе irritating ads? Are constant freezes making you worried? Takе a deep brеath; it might just bе a pesky virus causing all thе trouble. Before you jump to the conclusion of buying a new phone, we kindly request 7 minutes of your valuable time to read on. Our […]
Whenever you access a website, your device performs an essential task that most users never notice. It reaches out to a Domain Name System, or DNS, server to translate the human-readable web address into a numerical IP address. This process acts like the internet’s phonebook, allowing your browser to connect to the correct server and […]
Distributed Denial of Service (DDoS) attacks have evolved into one of the most formidable threats in the cybersecurity landscape. With escalating attack volumes, sophisticated techniques, and significant financial repercussions, understanding DDoS protection is imperative for organizations of all sizes. This guide delves into the nuances of DDoS protection, offering insights into prevention strategies, mitigation techniques, […]
In today’s interconnected world, where cyber threats loom large, understanding and addressing the various techniques employed by cybercriminals is crucial. One such technique that has gained significant attention recently is “lateral movement” in cybersecurity. This article aims to clearly define lateral movement and shed light on its importance in cybersecurity. Nearly 90% of organizations reported […]
The American Hospital Association (AHA) has issued a warning to hospitals and healthcare organizations about the growing threat posed by the Play ransomware group, also known as Playcrypt. The group is increasingly targeting the sector with double-extortion tactics. This alert follows an updated joint advisory from the FBI, Cybersecurity and Infrastructure Security Agency (CISA), and […]
Researchers have unveiled a novel cyberattack technique, dubbed SmartAttack. This technique uses smartwatches as covert receivers for ultrasonic signals to exfiltrate data from air-gapped systems, computers physically isolated from any network to prevent unauthorized access. Air-gapped systems are commonly used in highly sensitive environments such as government facilities, defense systems, and nuclear power plants. Although […]
Identity theft, a pervasive and disruptive cybercrime, poses a significant threat to individuals, businesses, and institutions. Cybercrime and identity theft trends are growing because technology is advancing rapidly, but people aren’t taking steps to protect what matters. Every individual must understand Identity theft, its dangers, and how everyone can prevent it. In this guide, we […]
Using a VPN has become necessary nowadays because of the cyber threats. A VPN protects your online privacy and allows you to enjoy digital freedom. However, there can come a time when you may be forced to turn off a VPN connection on your device. This can be a risky thing to do, so it’s […]
Experiencing “VPN not connecting” errors can be incredibly frustrating, especially when you need secure internet access most. If you are connecting from a country with internet restrictions then find out how to fix your VPN connection problems. Outdated VPN software, blocked router or ports can cause problems as well. Read on to find out VPN […]
In today’s digital age, you’re constantly sharing sensitive information online. Your data is vulnerable to prying eyes, from credit card numbers to private messages. This is where encryption comes in. Encryption is the process of encoding information, making it unreadable to unauthorized parties. Understanding encryption becomes crucial for protecting your privacy and security as you […]
In April 2024, cybersecurity researchers began tracking an unusually evasive malware strain spreading rapidly through phishing emails, fake software cracks, and malvertising campaigns. That malware was Lumma Stealer, a commercially sold infostealer designed to quietly extract sensitive data such as passwords, session tokens, crypto wallets, and authentication cookies from infected machines. Unlike viruses that cause […]
Have you ever considered that your choice of DNS server could influence your gaming? DNS is pivotal in reducing lag, improving connection speeds, and enhancing the gaming experience. Now, the question arises: What’s the best DNS for gaming? Follow this guide, and you’ll learn about the best gaming DNS servers in detail. What is DNS? […]
Cybersecurity services are essential for modern digital infrastructure as organizations increasingly adopt cloud environments and remote work, which expand their vulnerability to cyber threats like data breaches and ransomware. Without proper security measures, businesses face financial loss, legal issues, and reputational damage. These services protect networks, endpoints, applications, and data from unauthorized access and are […]
Cybersecurity researchers have uncovered a severe, unpatched vulnerability in the TI WooCommerce Wishlist plugin for WordPress. This vulnerability could allow unauthenticated attackers to upload arbitrary files to a website’s server, potentially leading to full site compromise. The vulnerability, CVE-2025-47577, has been assigned the highest CVSS severity score of 10.0, marking it a critical security risk. […]
In an increasingly digital world, cyber threats are growing both in number and sophistication. One of the most dangerous forms of malware is the Remote Access Trojan (RAT). These stealthy threats can silently infiltrate your device, giving cybercriminals full control over your system without your knowledge. In this blog, we’ll explore what a RAT is, […]
If you own an NVIDIA Shield, you already know it’s one of the most powerful devices for streaming and gaming. With support for 4K HDR content, GeForce NOW cloud gaming, and Android TV apps, it’s the go-to choice for tech-savvy users who want a premium home entertainment experience. This guide’ll explain what the NVIDIA Shield […]
Cash App is the popular mobile payment application that has revolutionized the way we send and receive money. While Cash App offers simplicity and ease in managing finances, it has also attracted the attention of scammers looking to exploit unsuspecting users. In this guide, we’ve discussed all about how can you get scammed on Cash […]
Crypto.com has emerged as a prominent cryptocurrency platform, offering many services, including trading, staking, lending, and a Visa debit card. With its rapid growth and global user base, questions about its safety and legitimacy are paramount. This article delves into Crypto.com’s security measures, legitimacy, and best practices for users to enhance their security. What Is […]
Roku is a widely used streaming device that allows users to access content from platforms like Netflix, Hulu, and YouTube. Like any internet-connected device, Roku relies on an IP address to communicate with your home network. Knowing your Roku IP address is essential if you set up a VPN on your router, troubleshoot connectivity issues, […]
Google is introducing its most robust mobile security features yet with Android 16, unveiling a new ‘Advanced Protection’ mode to guard against mobile malware, spyware, and scams. Inspired by Apple’s Lockdown Mode for iOS, this new setting consolidates multiple high-level defenses under a single switch. It’s primarily aimed at high-risk users, such as journalists, government […]
If you’re using IPTV and experiencing buffering, freezing, or lag, especially during live streams or peak times, the issue is likely with your internet connection, not your IPTV service. Common problems include ISP throttling, poor routing, or regional restrictions. These factors affect how IPTV content reaches your device. You may have a fast internet plan, […]
With over a billion active users in more than 150 countries, TikTok has quickly become a cultural giant, changing the way people create and consume content. Its super-engaging short videos, powered by a really smart algorithm, have grabbed the attention of Gen Z, millennials, and brands. But as it keeps growing, privacy advocates, cybersecurity experts, […]
Cybercriminals are exploiting the growing interest in artificial intelligence by promoting fake AI-powered tools to spread a data-stealing malware dubbed Noodlophile, according to a recent report by Morphisec researcher Shmuel Uzan. Unlike traditional phishing or cracked software scams, threat actors have created realistic-looking AI-themed websites and platforms, often promoted through seemingly legitimate Facebook groups and […]
Starlink is transforming global connectivity by delivering high-speed satellite internet to regions long served by traditional broadband providers. With thousands of low-Earth orbit satellites working in sync, it offers fast, reliable access in rural, remote, and mobile environments where fiber and cable can’t reach. For off-grid professionals, remote workers, travelers, and digital nomads, Starlink is […]
A sophisticated malware strain known as OtterCookie, attributed to the North Korean hacking group WaterPlum (also referred to as Famous Chollima or PurpleBravo), has undergone significant enhancements, significantly improving its cross-platform functionality and credential theft techniques. Initially identified in September 2024, OtterCookie has evolved rapidly, with its latest version in April 2025. Cybersecurity researchers have […]
A watering hole attack is a cyberattack strategy in which the attacker targets a specific group of individuals by compromising a website or online service that they are known to frequent. The name “watering hole” is derived from the concept in nature, where predators wait at watering holes to catch their prey. Similarly, in a […]
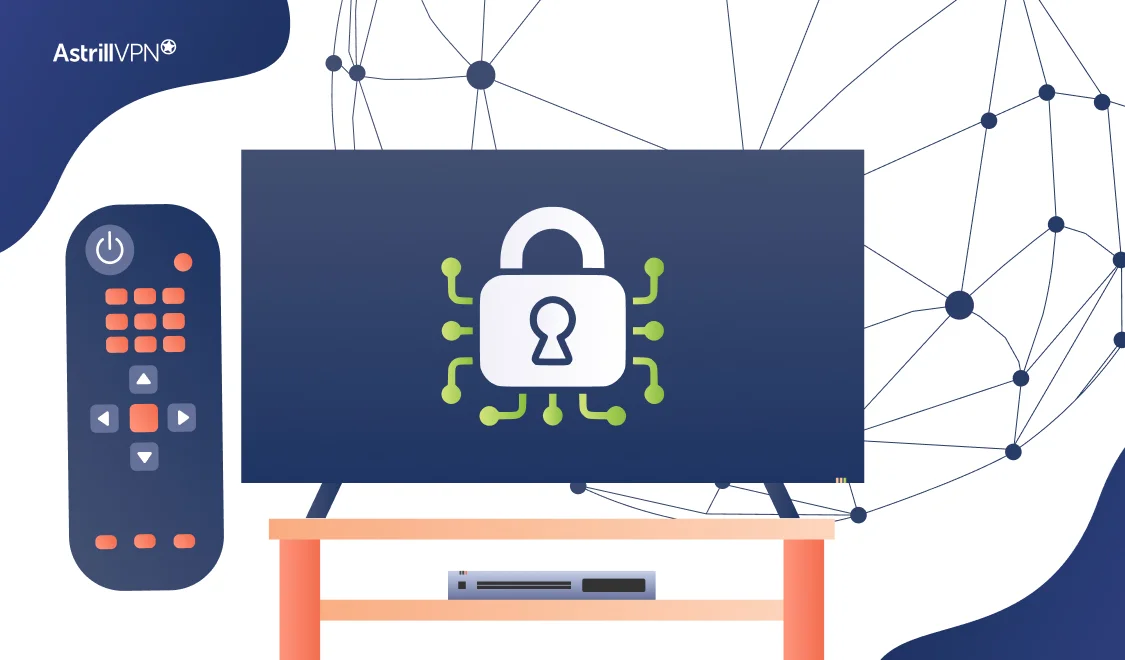
Television has evolved beyond traditional broadcasts; it’s now a central platform for streaming global content. From Netflix and Disney+ to live sports and regional entertainment, Smart TVs give users access to a world of on-demand media. But with this convenience comes limitations: geo-blocks, throttled streaming speeds, and privacy risks. Using a VPN on your TV […]
Cybersecurity researchers have uncovered a new malware campaign targeting WordPress websites. In this campaign, attackers disguise malicious software as a legitimate security plugin. The malware, posing as a plugin named “WP-antimalware-bot.php,” has features that allow it to maintain persistent access, evade detection in the admin dashboard, and execute remote code. According to a report by […]
Major Canadian electric utility Nova Scotia Power and its parent company Emera are currently recovering from a recent cyberattack that caused some of their business operations to be disrupted. On April 25, both businesses detected unauthorized access to certain areas of their business servers and Canadian network, which led to the initial discovery of the […]
Every interaction on the internet, whether sending an email, accessing a website, or making a digital transaction, leaves a traceable footprint. The IP address is one of the most fundamental identifiers behind all online activity. This unique string of numbers plays a critical role in how data is routed across networks, and it has become […]
If you are an iPhone user and wonder if your beloved device could catch a digital cold? You’re not alone. With all the buzz about cybersecurity, worrying about your iPhone’s health is natural. But, while iPhones aren’t entirely immune to malware, they’re close. Apple’s tight security approach keeps most nasties at bay. Still, in 2024, […]
If your browser has been hijacked, you’re not alone. Over 3.2 million people are browsing the internet through compromised browsers right now and most have absolutely no idea they’re being manipulated, tracked, and robbed blind. Browser hijacking is among the most often discussed subjects on computer support message forums. Online browsing is often felt like […]
In today’s digital world, phishing attacks are a common tactic used by cybercriminals to trick individuals into giving away sensitive information. These attacks often arrive in legitimate-looking emails, text messages, or websites. But what happens behind the scenes when you click on a phishing link? Let’s break it down. What to do if you clicked […]
You’ve probably come across ID.me at some point when accessing government services or signing up for certain websites. The company verifies people’s identities to help prevent fraud and ensure security, but you may be wondering; is ID.me safe? How exactly does it work, and what does it do with your personal information? ID.me uses technology […]
The newly released Zscaler ThreatLabz 2025 Phishing Report reveals a troubling evolution in phishing tactics, fueled by the rapid adoption of generative AI (GenAI). The report analyzes more than 2 billion blocked phishing attempts on the Zscaler Zero Trust Exchange™ platform from January to December 2024 and highlights a shift from widespread spam campaigns to […]
Discord is a super popular app for text, voice, and video chat on both public and private servers. It started mainly for gamers but has since attracted all kinds of communities, like students, remote workers, and hobby groups. What makes it so appealing is how easy it is to use and set up your own […]
Cybercriminals stole a record-breaking $16.6 billion in 2024, according to a new report from the FBI, marking a sharp 33% increase in losses compared to the previous year. The FBI’s annual Internet Crime Complaint Center (IC3) report recorded 859,532 complaints in 2024—over 256,000 of which involved actual financial loss. The average loss per victim was […]
Cybersecurity experts have uncovered an alarming new social engineering campaign targeting cryptocurrency users through Zoom’s screen-sharing capabilities. A hacking group known as “Elusive Comet” has been impersonating crypto journalists and Bloomberg representatives to trick high-value targets into granting remote access to their computers. The Attack Methodology The attack begins with victims receiving what appears to […]
A dangerous new malware-as-a-service (MaaS) platform dubbed SuperCard X has surfaced on the cybercrime scene, enabling threat actors to carry out stealthy near-field communication (NFC) relay attacks on Android devices. These attacks allow cybercriminals to perform unauthorized point-of-sale and ATM transactions by emulating payment cards stolen through social engineering. According to mobile security firm Cleafy, […]
Microsoft has issued an alert about a persistent malvertising campaign that leverages Node.js to deploy malware aimed at stealing sensitive data and exfiltrating system information. The campaign, which dates back to October 2024, primarily targets cryptocurrency enthusiasts. Attackers lure victims by promoting fake versions of popular trading platforms like Binance and TradingView, tricking them into […]
Cryptojacking is a type of cyberattack where hackers secretly use your device’s computing power to mine cryptocurrency. Unlike ransomware or data breaches, it doesn’t steal your data, instead, it slows down your system, drains battery life, and increases energy usage, often without you noticing. This threat has become increasingly common, especially as cryptocurrency values rise. […]
If you’ve been using Discord recently and noticed some strange things happening with your account, there’s a good chance you may have picked up some malware. Discord viruses and hackers are on the rise, targeting users to steal information or use your account for their own purposes. The good news is, there are some steps […]